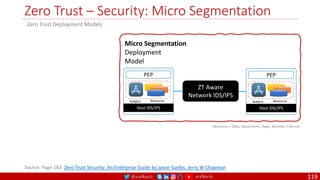
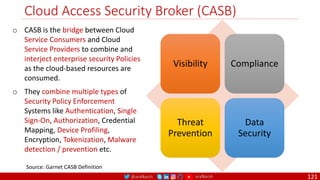
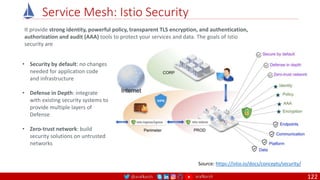
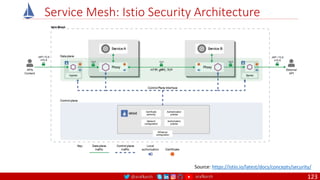
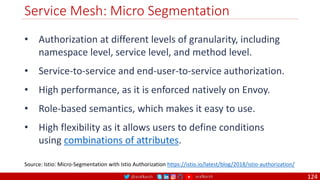
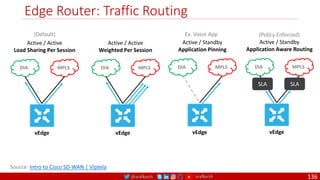
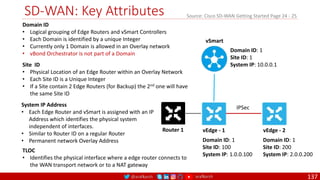
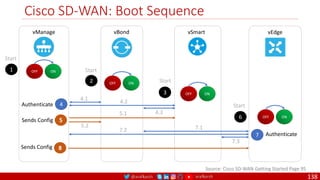
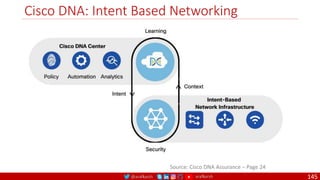
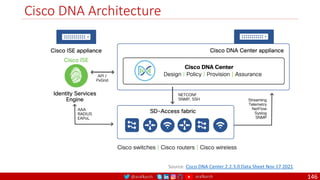
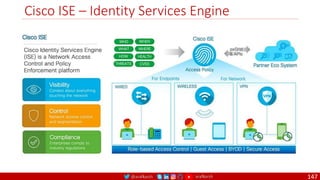
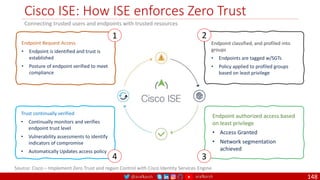
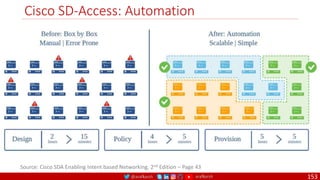
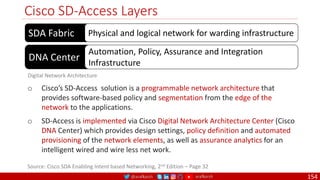
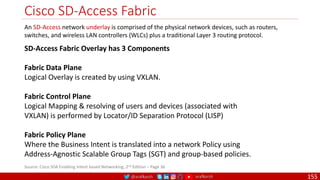
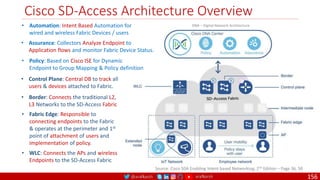
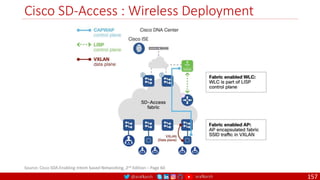
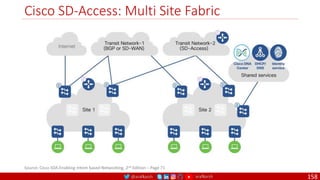
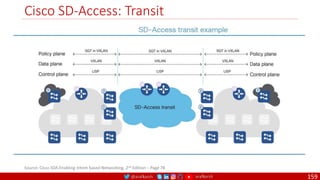
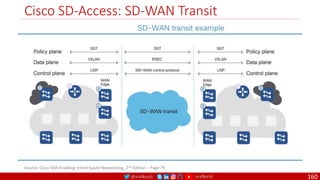
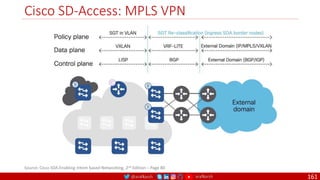
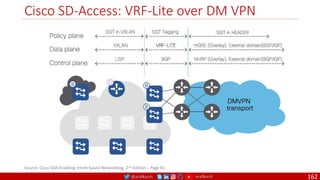
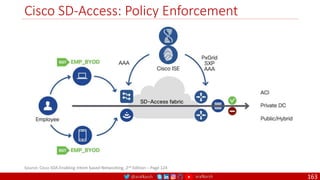
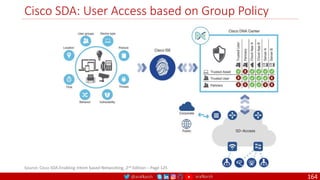
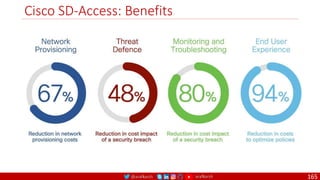
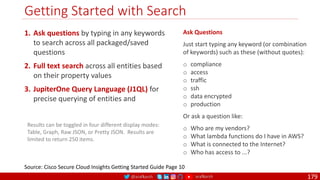
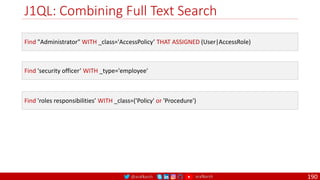
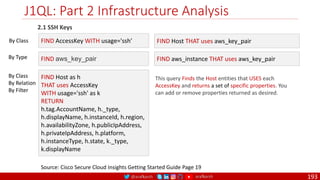
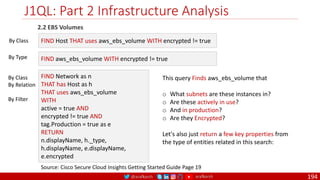
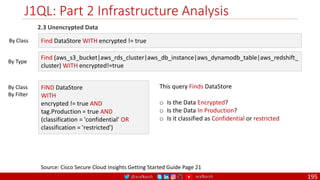
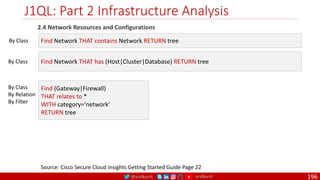
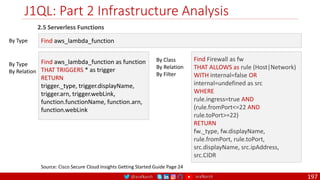
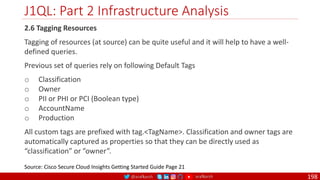
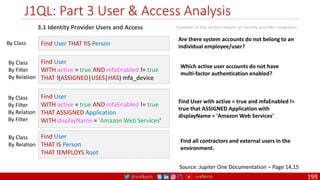
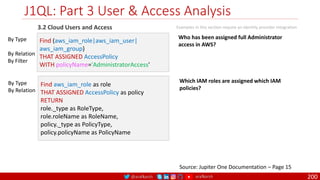
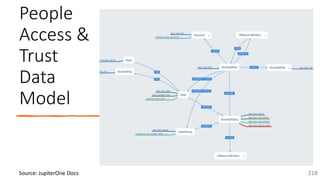
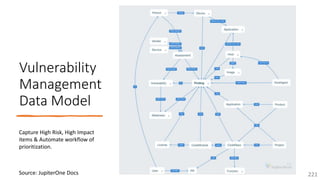
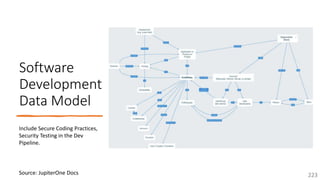
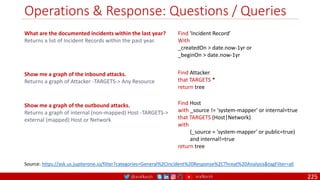
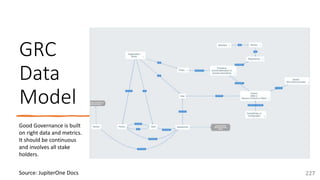
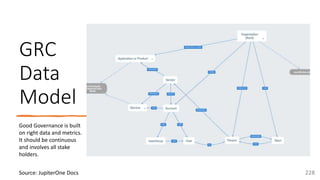
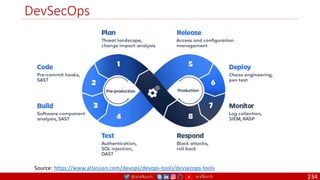
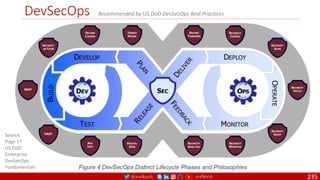
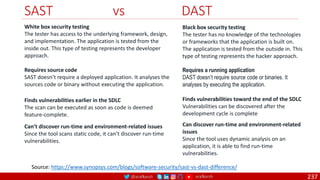
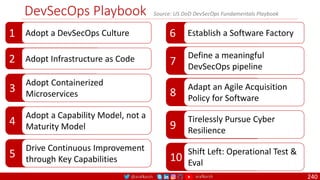
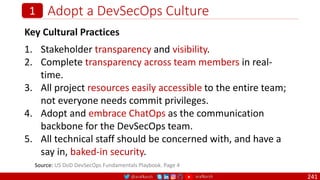
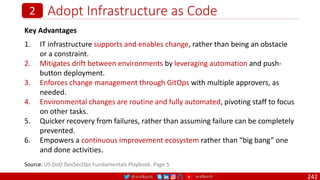
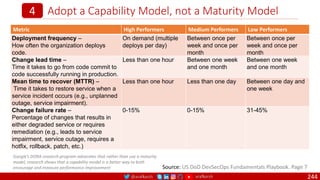
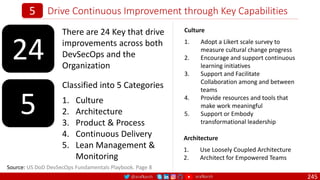
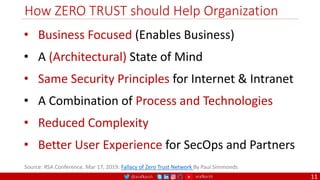
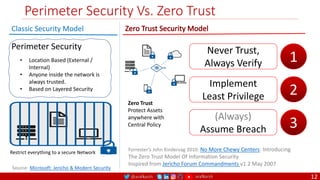
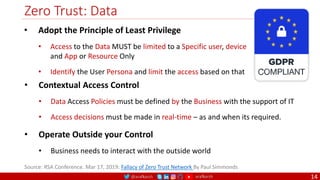
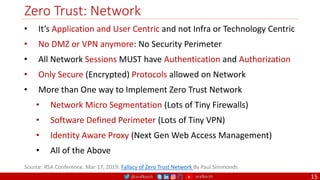
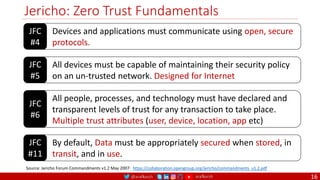
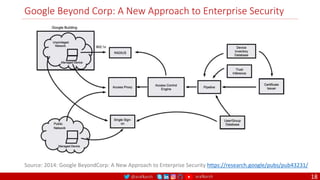
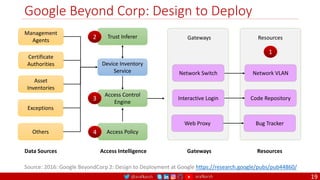
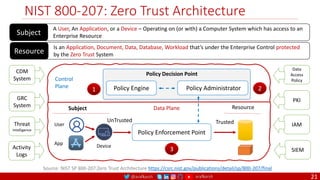
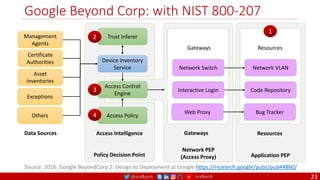
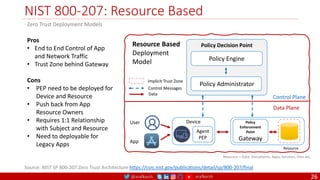
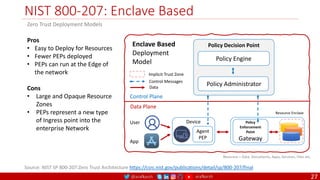
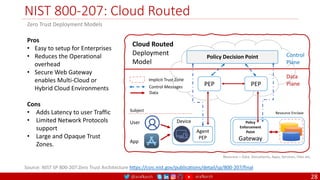
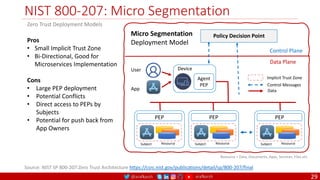
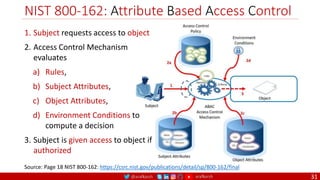
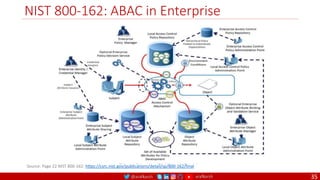
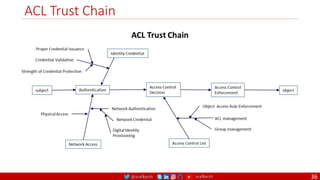
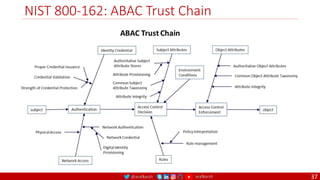
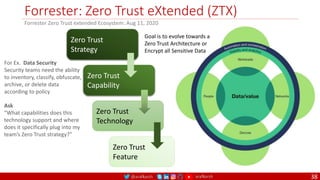
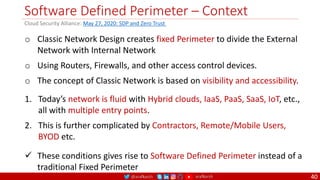
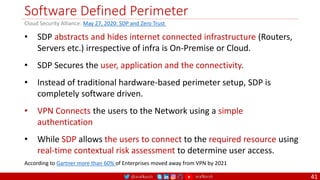
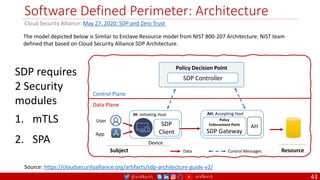
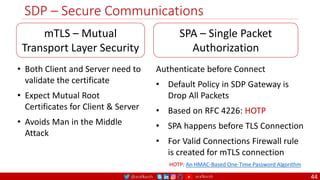
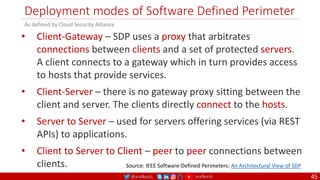
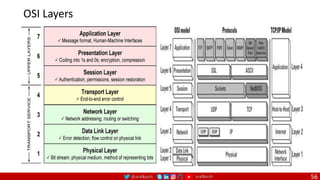
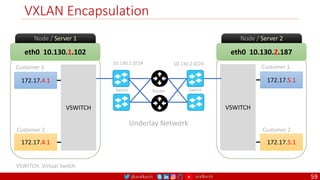
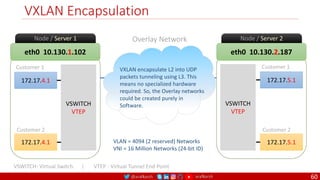
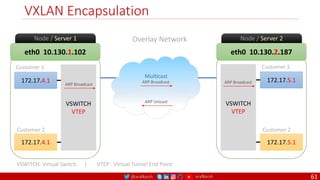
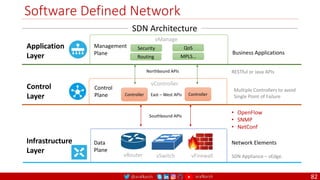
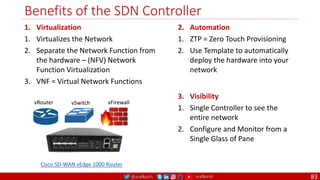
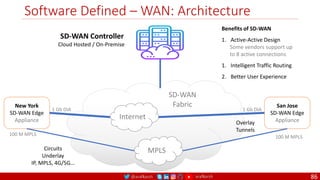
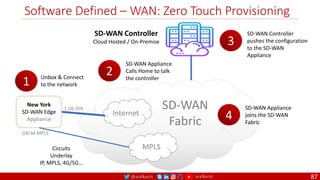
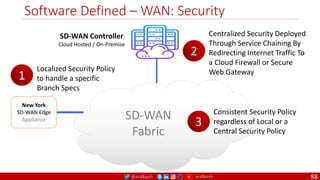
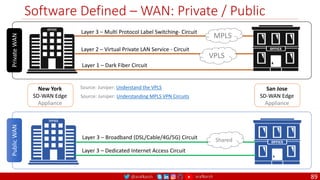
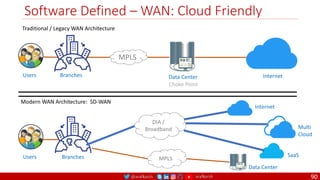
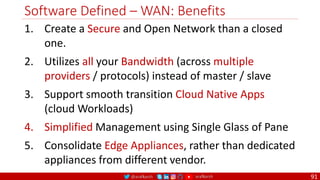
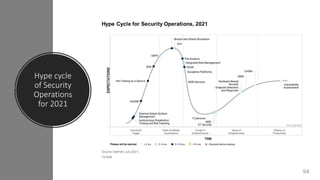
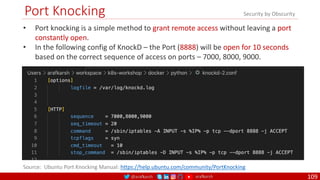
The document is a comprehensive overview of networking and security practices relevant to software developers, particularly focusing on Zero Trust architecture and DevSecOps. It outlines the evolution of security models, the importance of continuous integration and delivery (CI/CD), and discusses various deployment models of Zero Trust as proposed by NIST. This final part of a series aims to inform developers about their role in enhancing security measures within their applications and services.



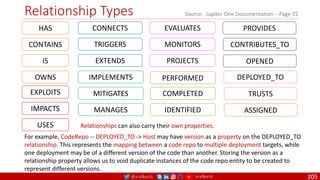
![@arafkarsh arafkarsh
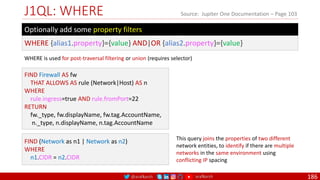
Agile
Scrum (4-6 Weeks)
Developer Journey
Monolithic
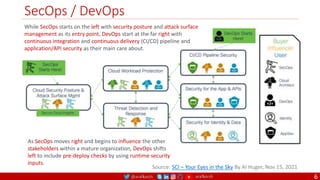
Domain Driven Design
Event Sourcing and CQRS
Waterfall
Optional
Design
Patterns
Continuous Integration (CI)
6/12 Months
Enterprise Service Bus
Relational Database [SQL] / NoSQL
Development QA / QC Ops
4
Microservices
Domain Driven Design
Event Sourcing and CQRS
Scrum / Kanban (1-5 Days)
Mandatory
Design
Patterns
Infrastructure Design Patterns
CI
DevOps
Event Streaming / Replicated Logs
SQL NoSQL
CD
Container Orchestrator Service Mesh](https://image.slidesharecdn.com/ms-12-zero-trust-sase-devsecops-v04-220407081302/85/Zero-Trust-SASE-DevSecOps-4-320.jpg)
























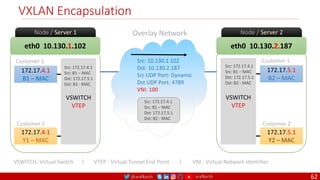
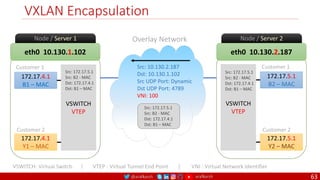
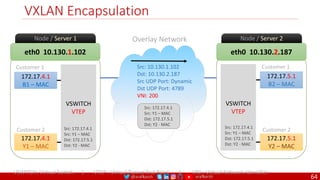
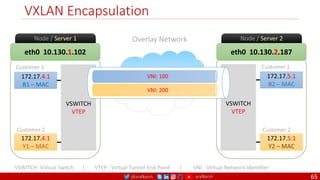




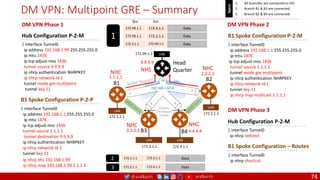
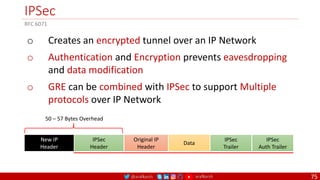
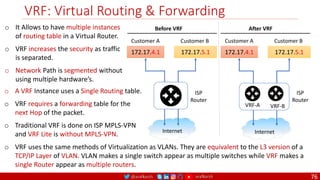
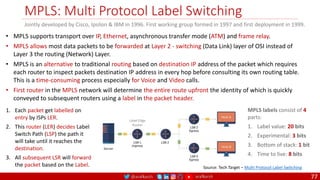











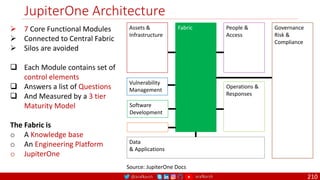
![@arafkarsh arafkarsh
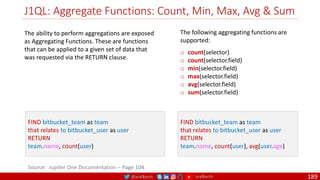
32 Bit
64 Bit
32 Bit
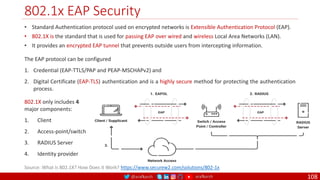
Single Packet Authorization
110
UID OTP
Counter GMAC
128 Bit
SPA = UID, CTR OTP, GMAC
UID Universal ID of SDP Client
CTR Hashed with seed to Create OTP
OTP One Time Password: HTOP
GMAC Signature of UID, CTR, OTP
Seed Shared Secret for OTP
Encryption
Key
Shared Key for GMAC
(AES-256)
OTP HMAC [Seed + CTR]
GMAC E-Key [UID + OTP + CTR]
CTR
Is incremented to mitigate
playback attacks
= 256
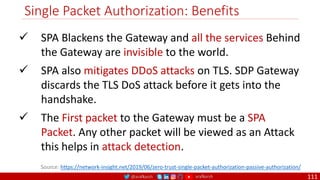
SPA addresses all the limitations of Port Knocking
By Default, SPA Gateway Drops All the Packets
1. Client Sends a SPA Packet
2. Gateway Receives the Packet and Decrypts Packet
3. Validates the Credentials based on protocol / port
4. If Valid, then Adds a Firewall rule to open an mTLS
Connection
5. Once the Connection is established the Gateway
removes the firewall rule making the service go Dark
Again.
o The established mTLS session will not be affected by
removing the firewall rule.](https://image.slidesharecdn.com/ms-12-zero-trust-sase-devsecops-v04-220407081302/85/Zero-Trust-SASE-DevSecOps-110-320.jpg)