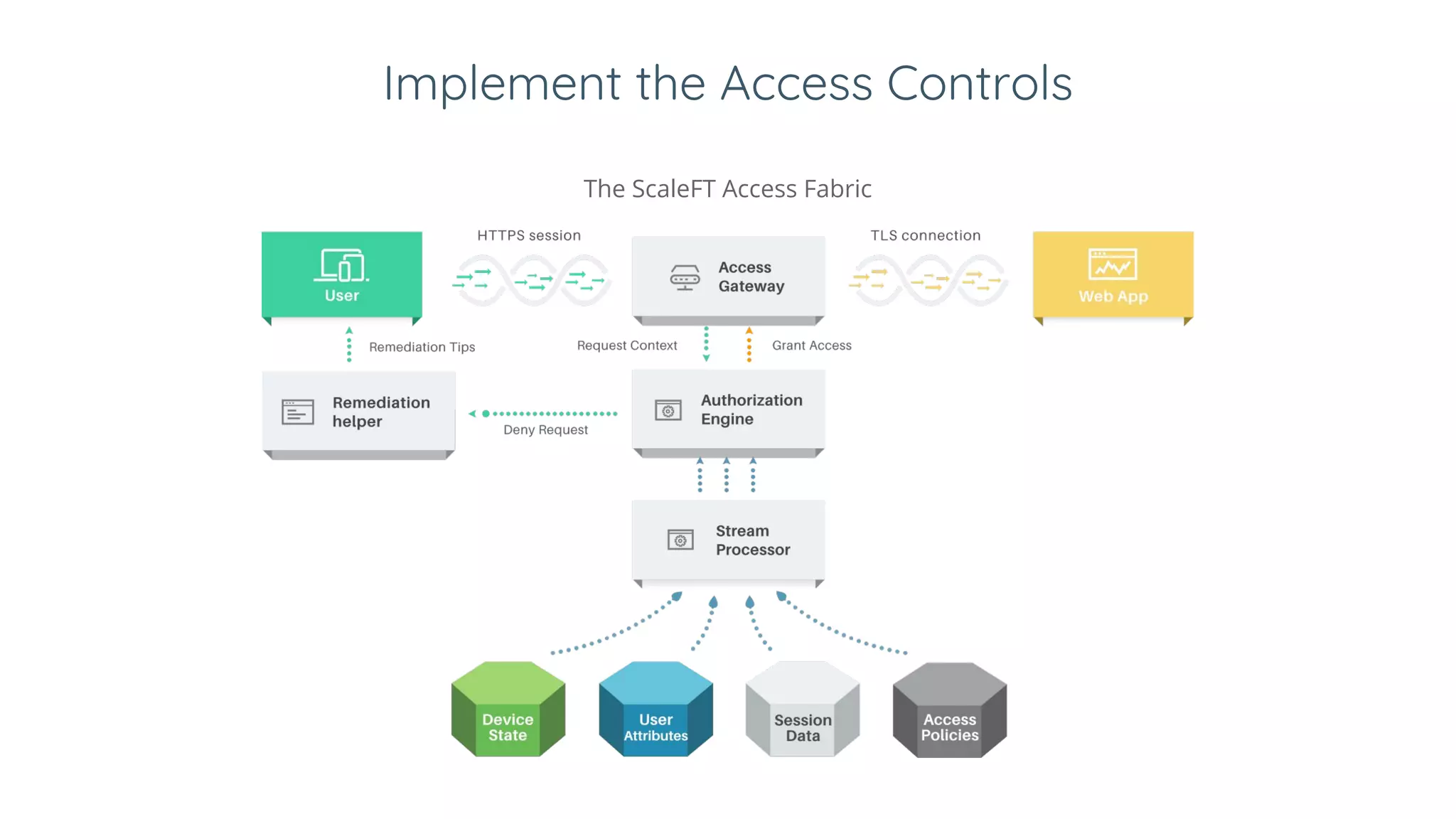
1. Google implemented a zero trust architecture called BeyondCorp to allow employees to work from untrusted networks without using a VPN. It granted access based on identity and device attributes rather than network location.
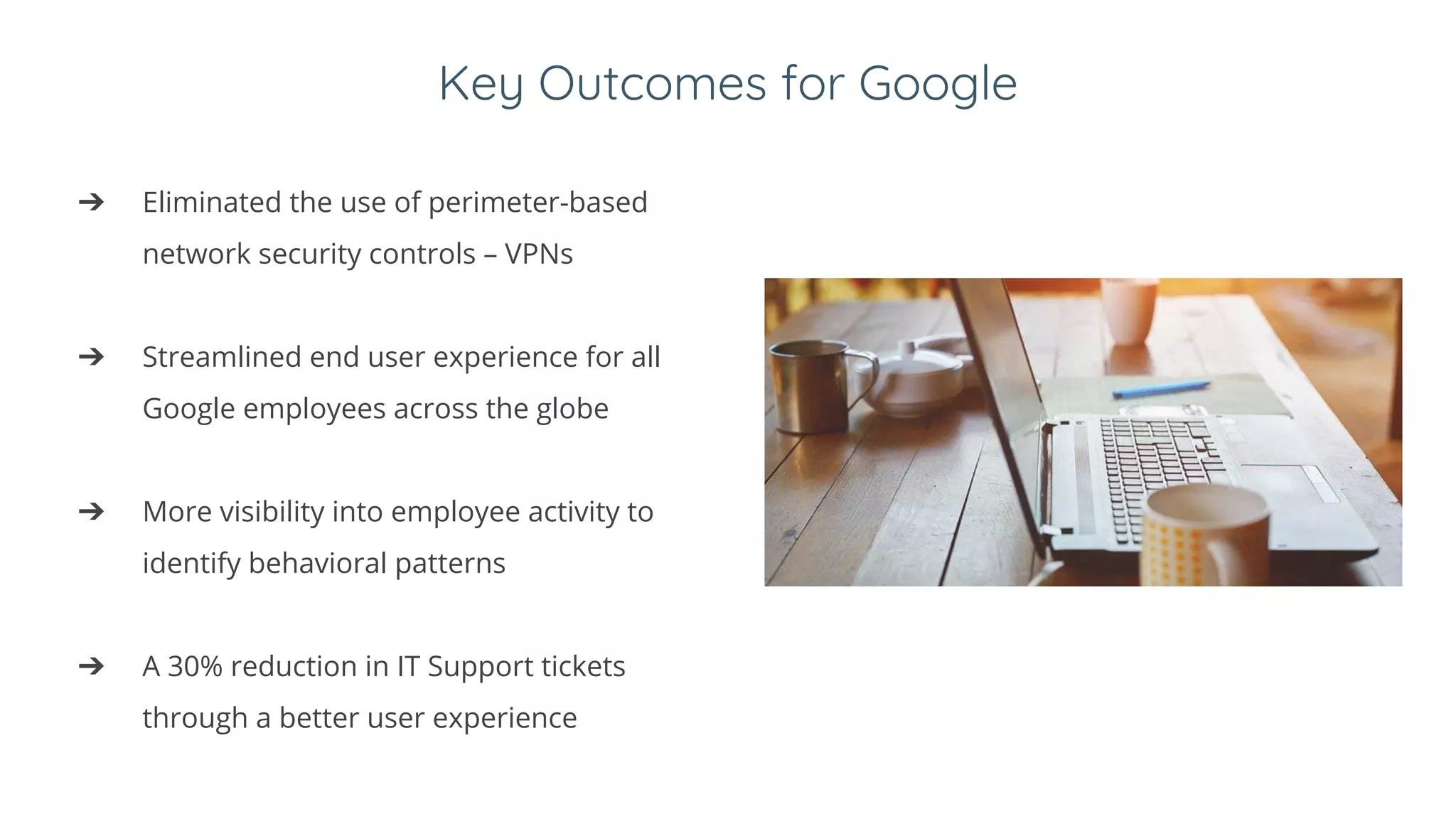
2. BeyondCorp has several components including an identity provider, device inventory, trust inferer, access policies, access proxy, and access control engine. It eliminated VPNs, streamlined the user experience, and reduced IT support tickets.
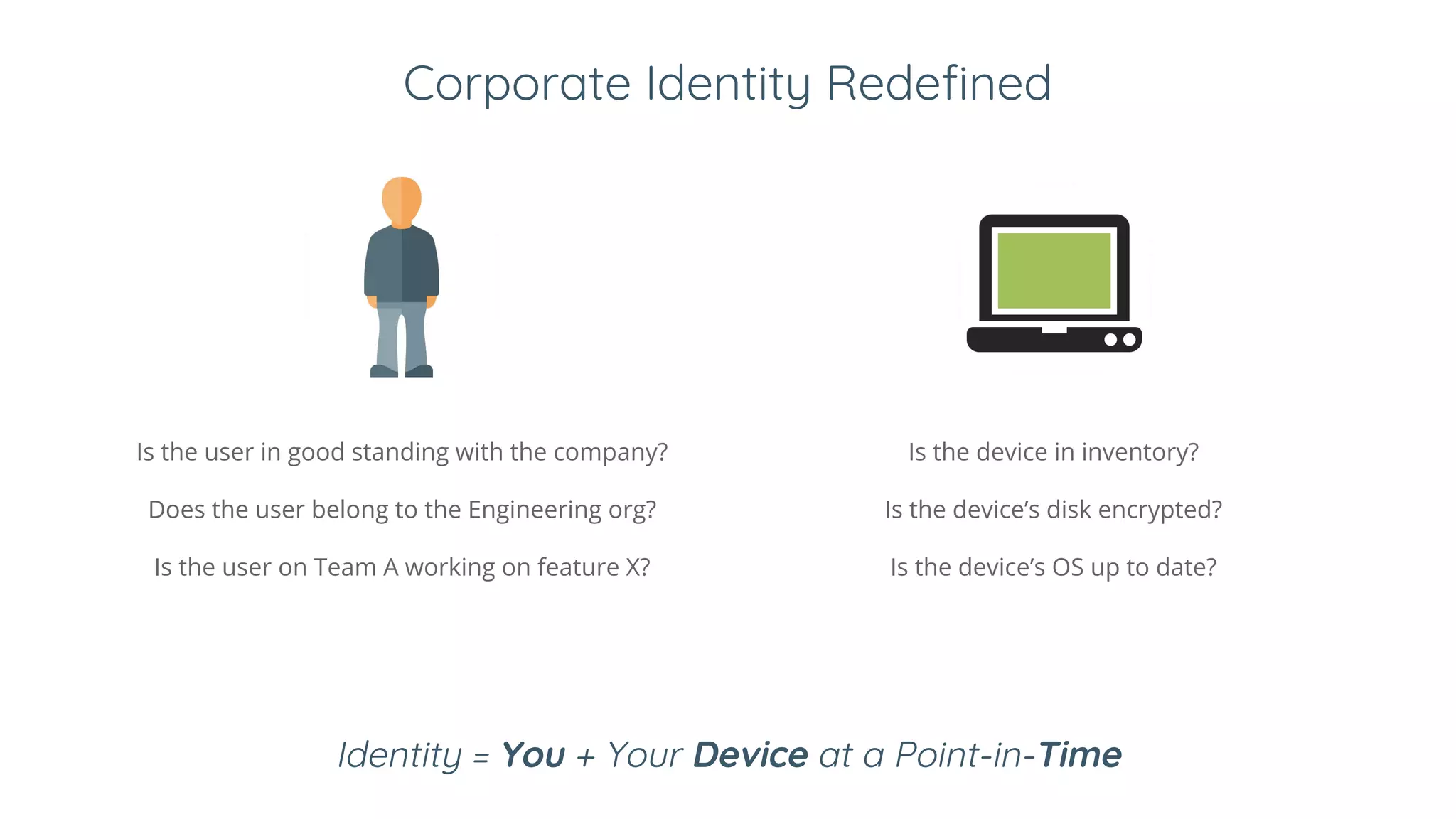
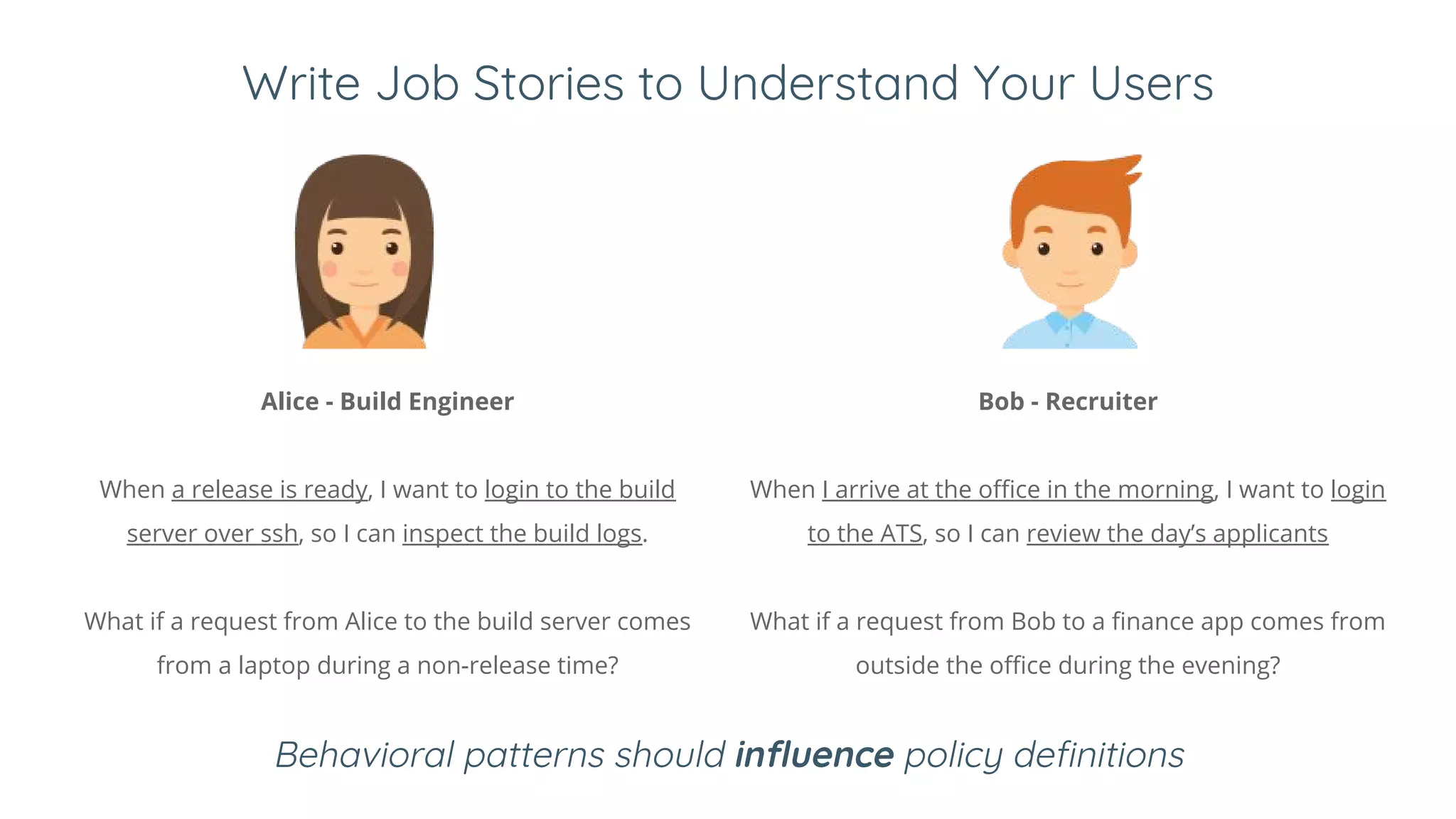
3. Zero trust is applying BeyondCorp principles to other organizations. It redefines identity as the user and device attributes. Access decisions are made in real time based on those attributes and dynamic conditions like being on an up-to-date device. This improves security by enforcing encryption and