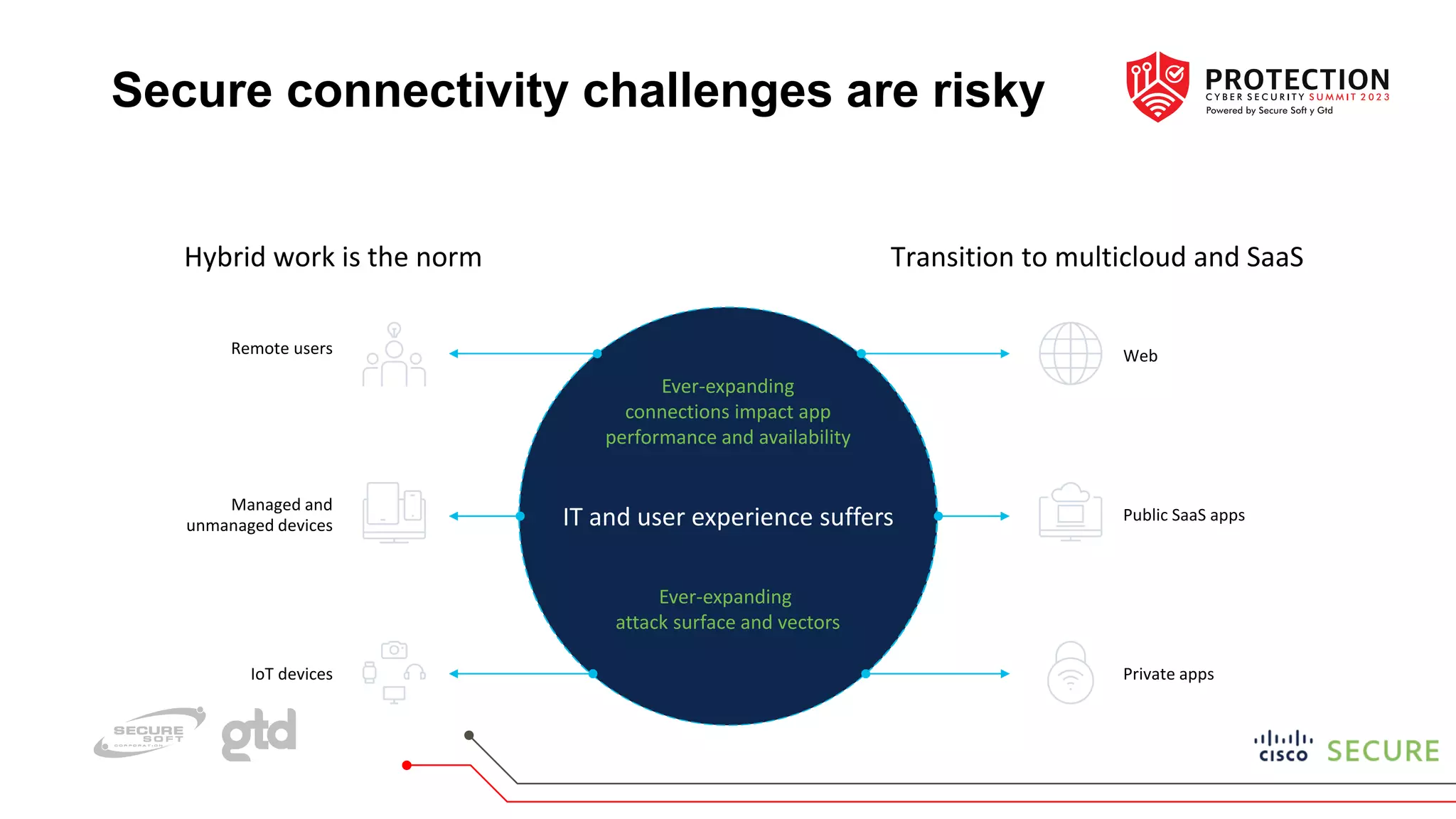
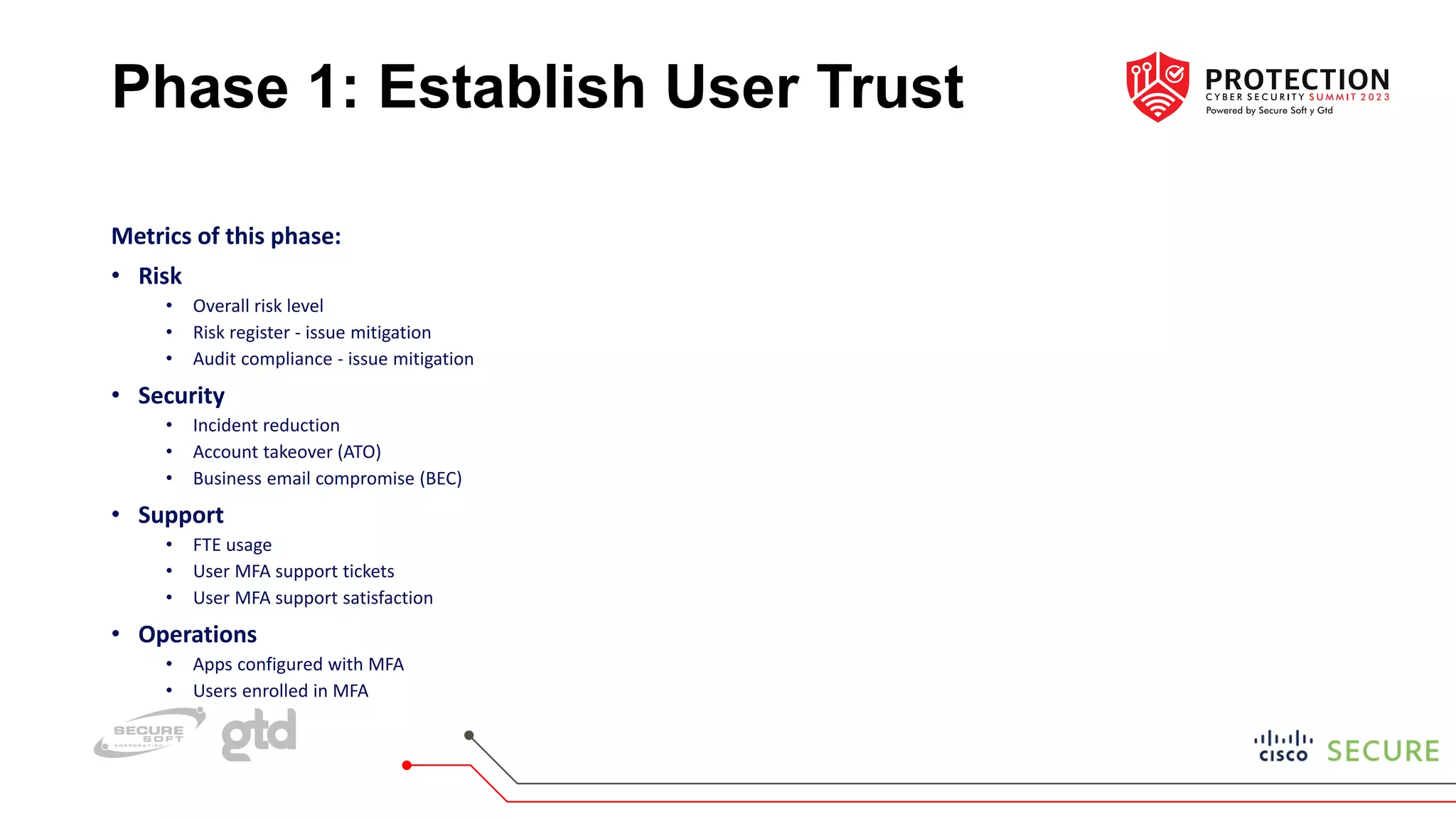
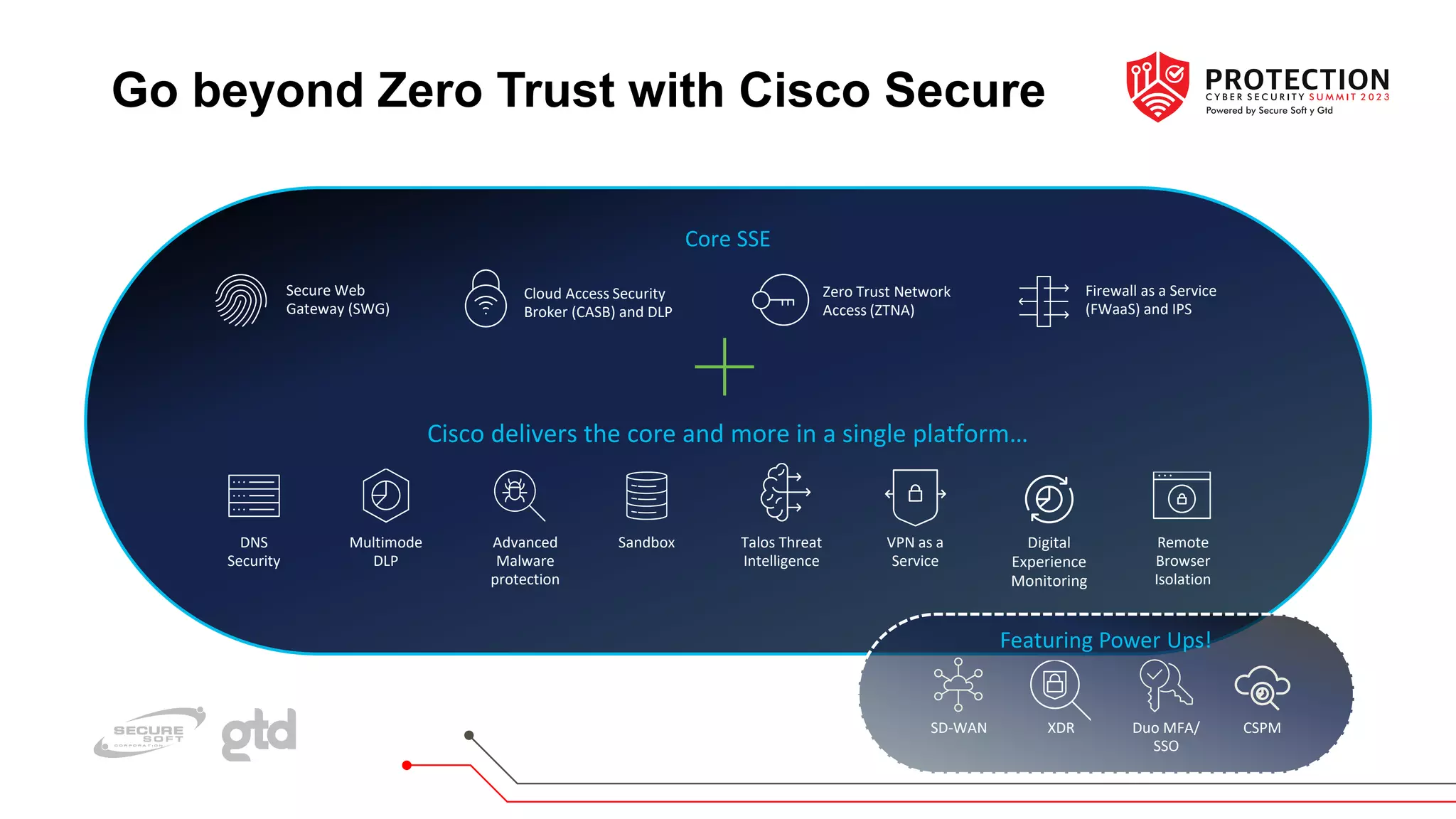
The document outlines a practical approach to implementing zero trust in hybrid work environments, addressing challenges from an ever-expanding attack surface and the complexity of securing various devices and applications. Cisco's zero trust framework emphasizes continuous visibility, adaptive trust assessments, and granular access controls based on user, device, and application status. The approach is structured into phases that include establishing user trust, device visibility, device trust, adaptive policies, and optimizing the workforce experience for improved security and operational efficiency.