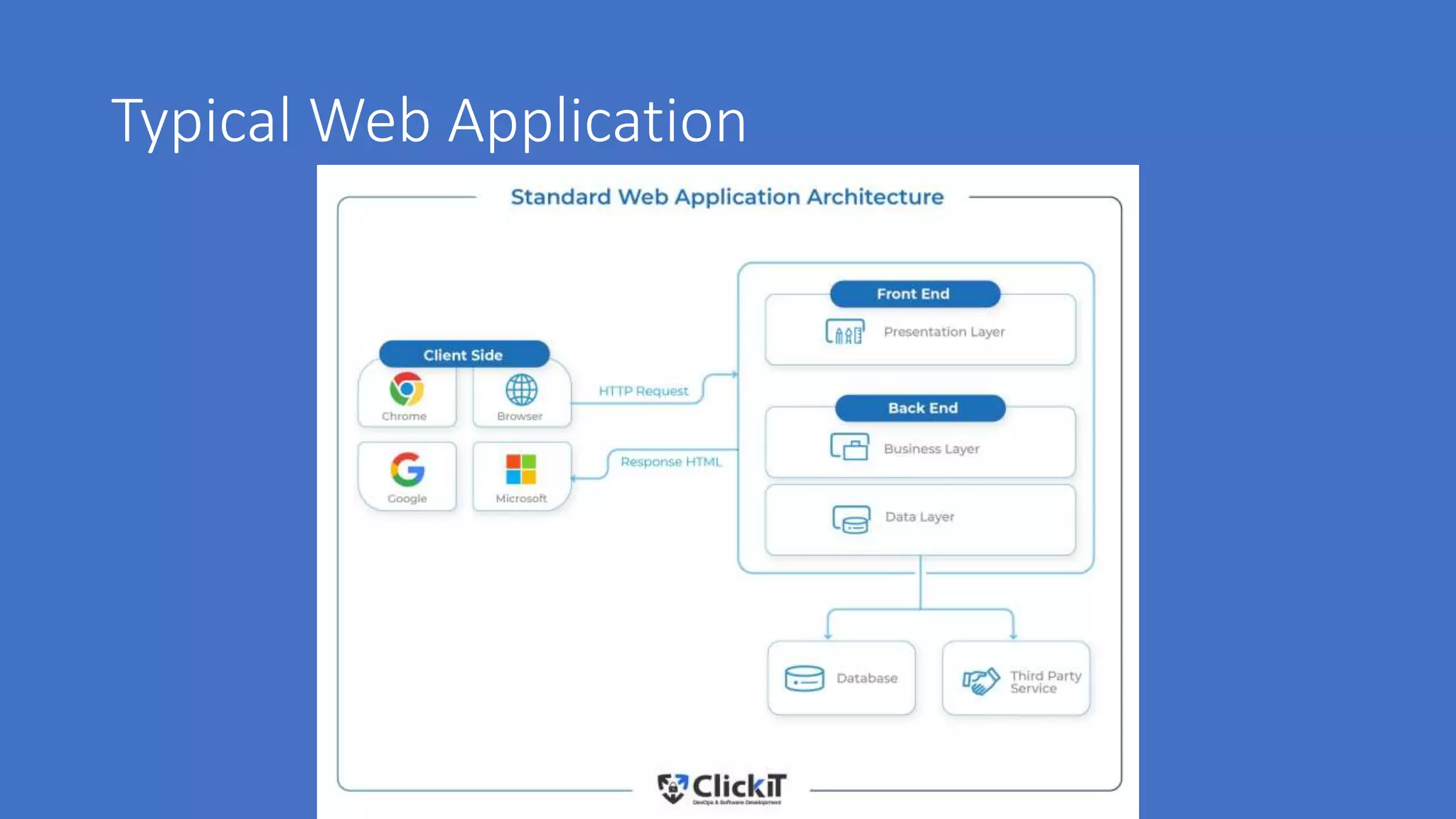
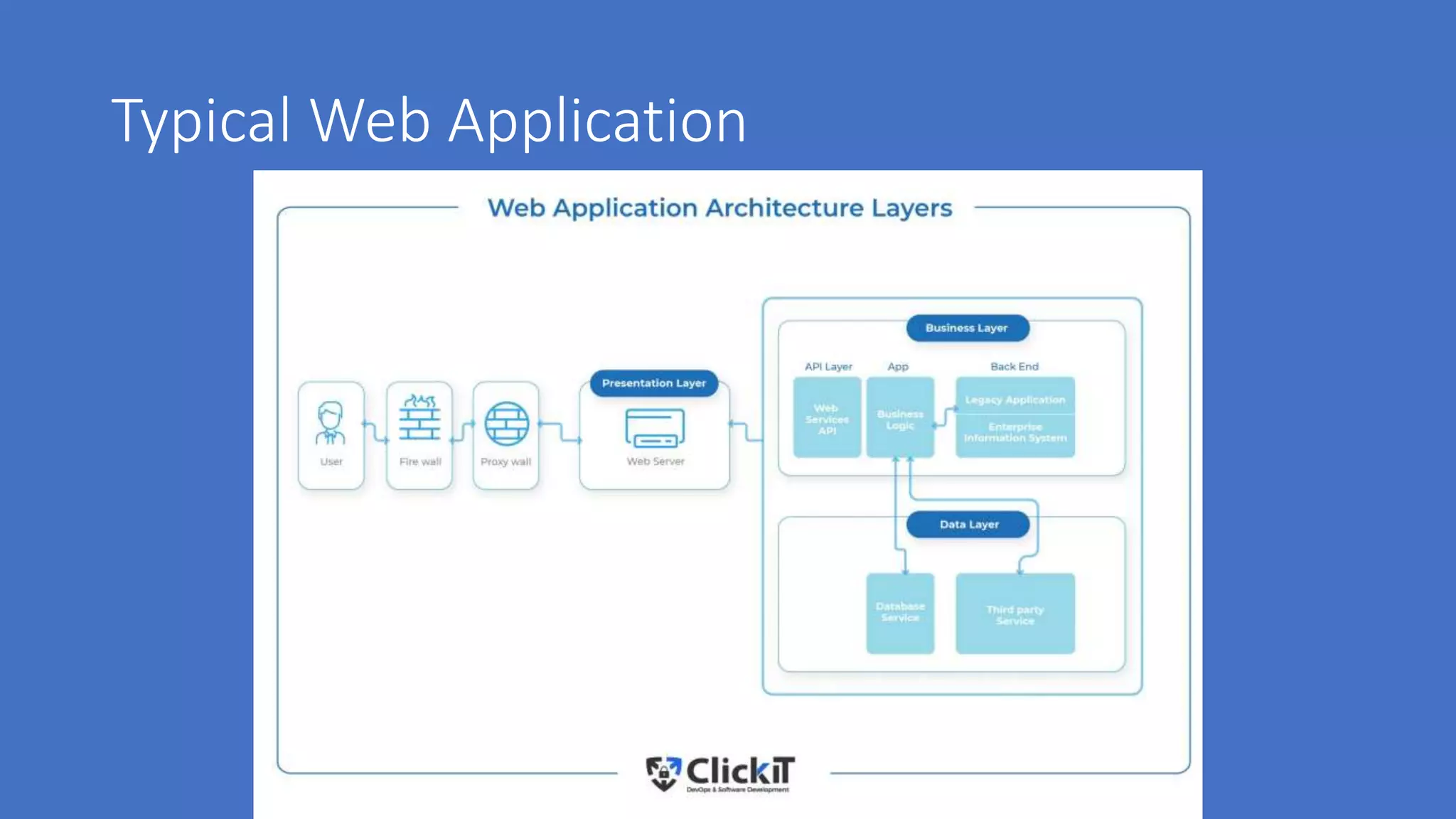
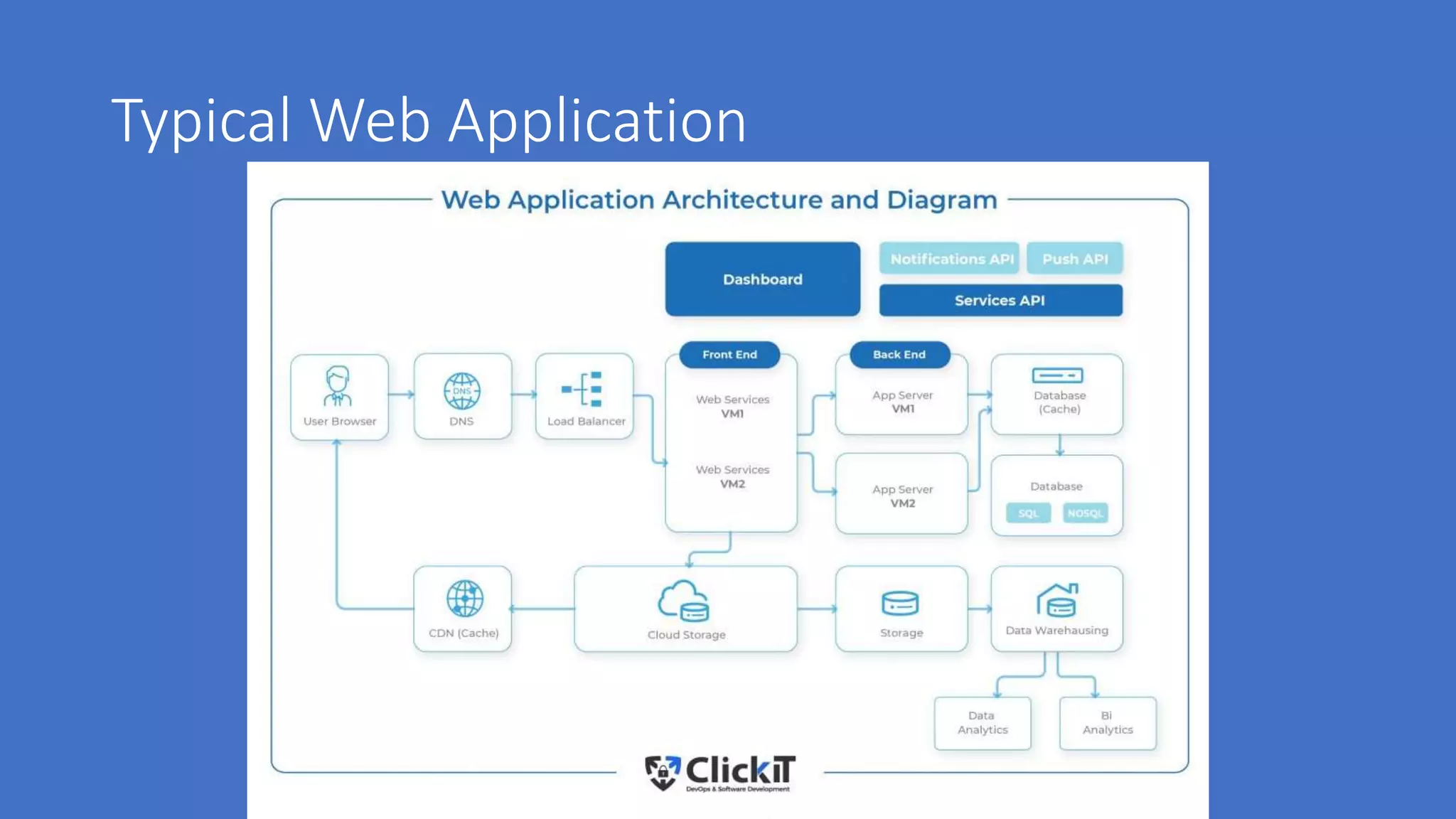
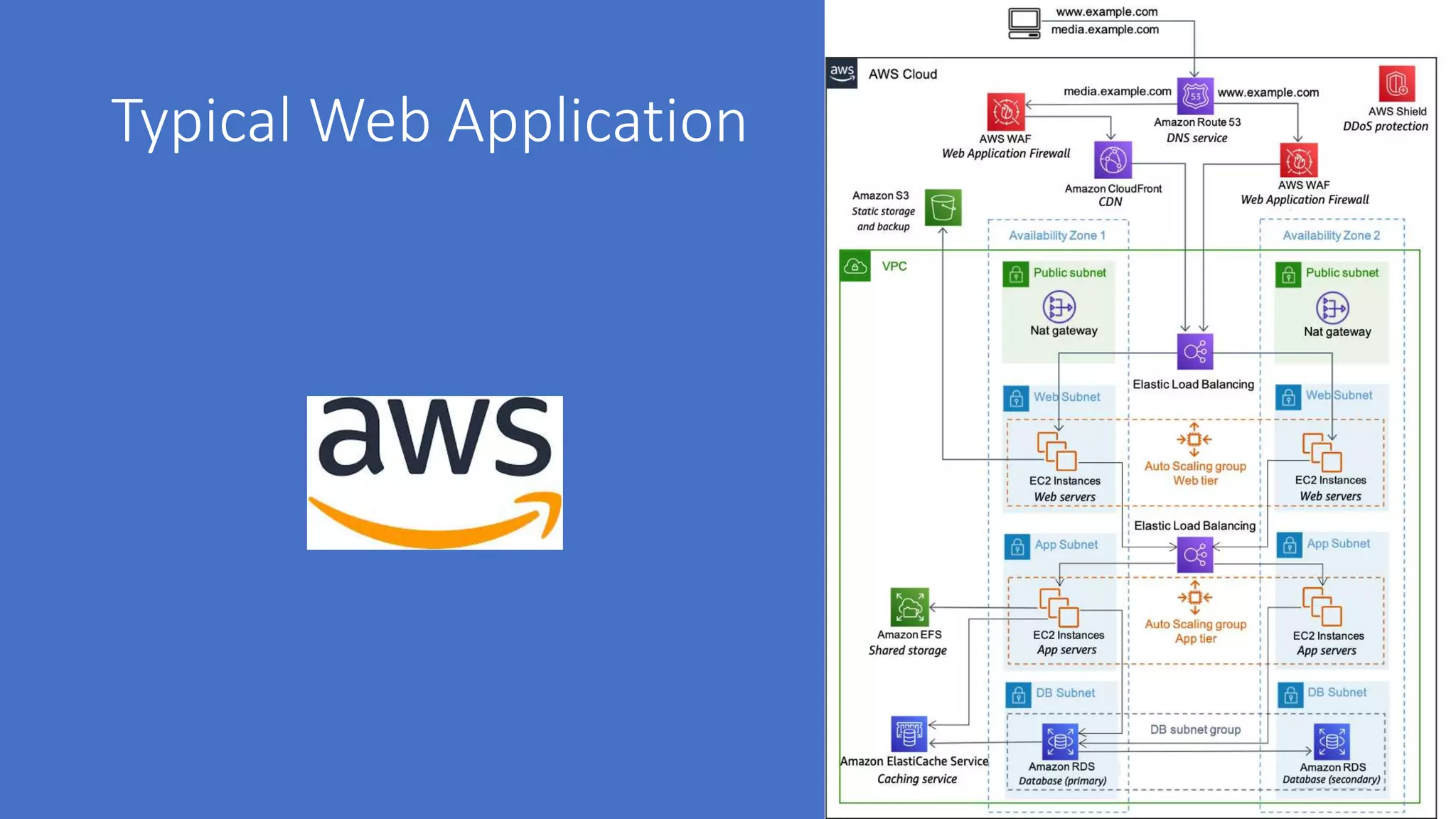
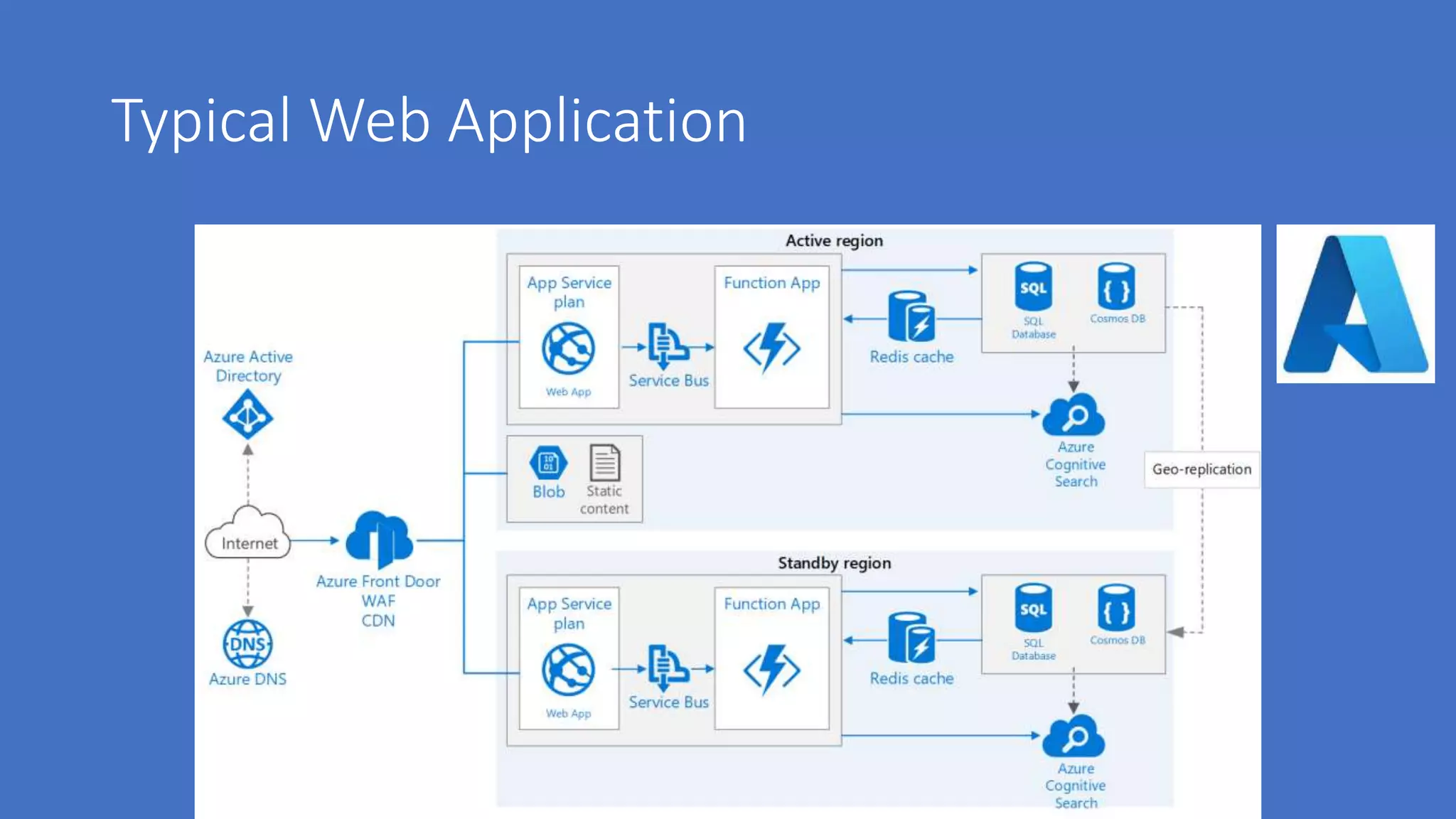
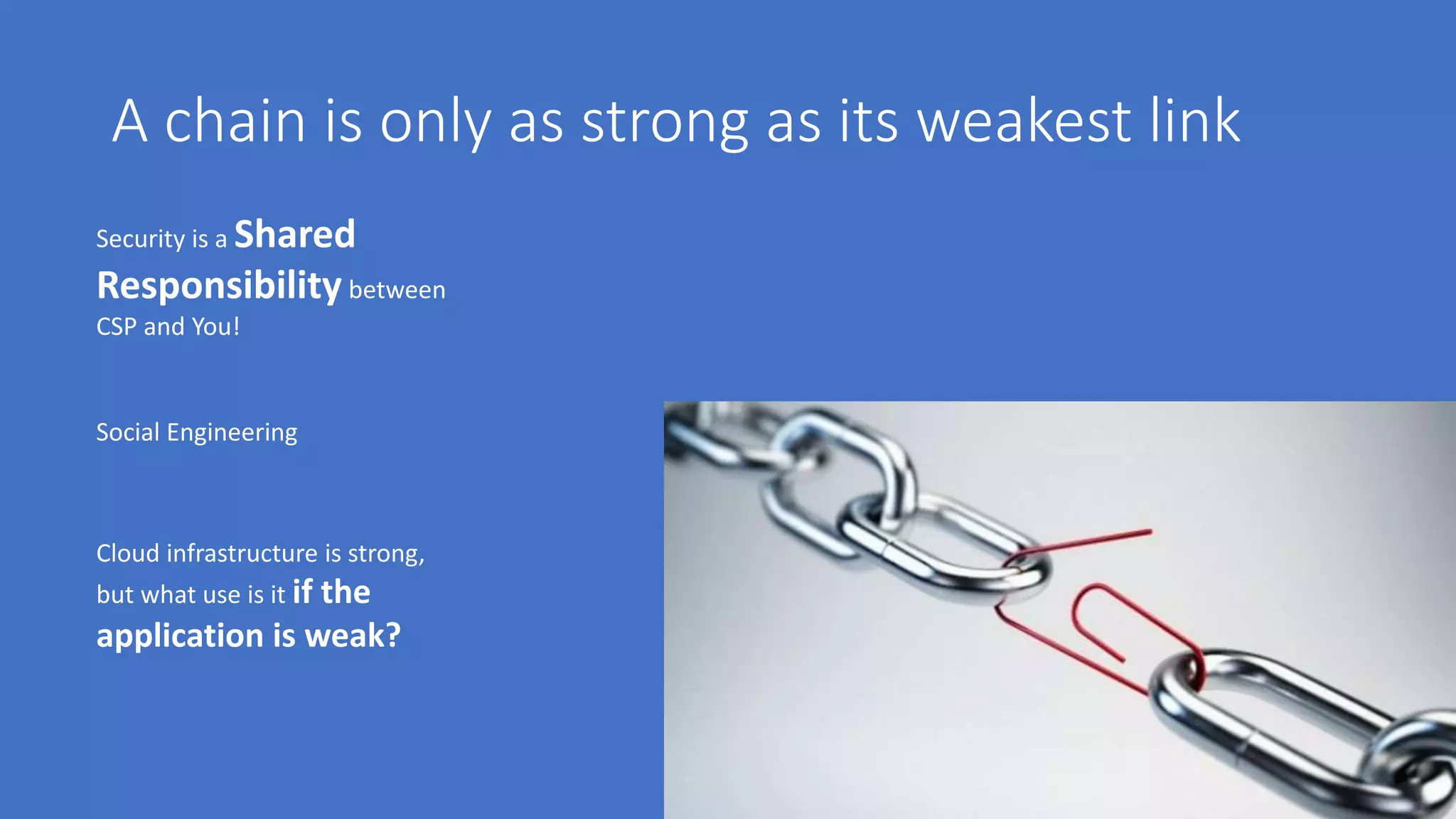
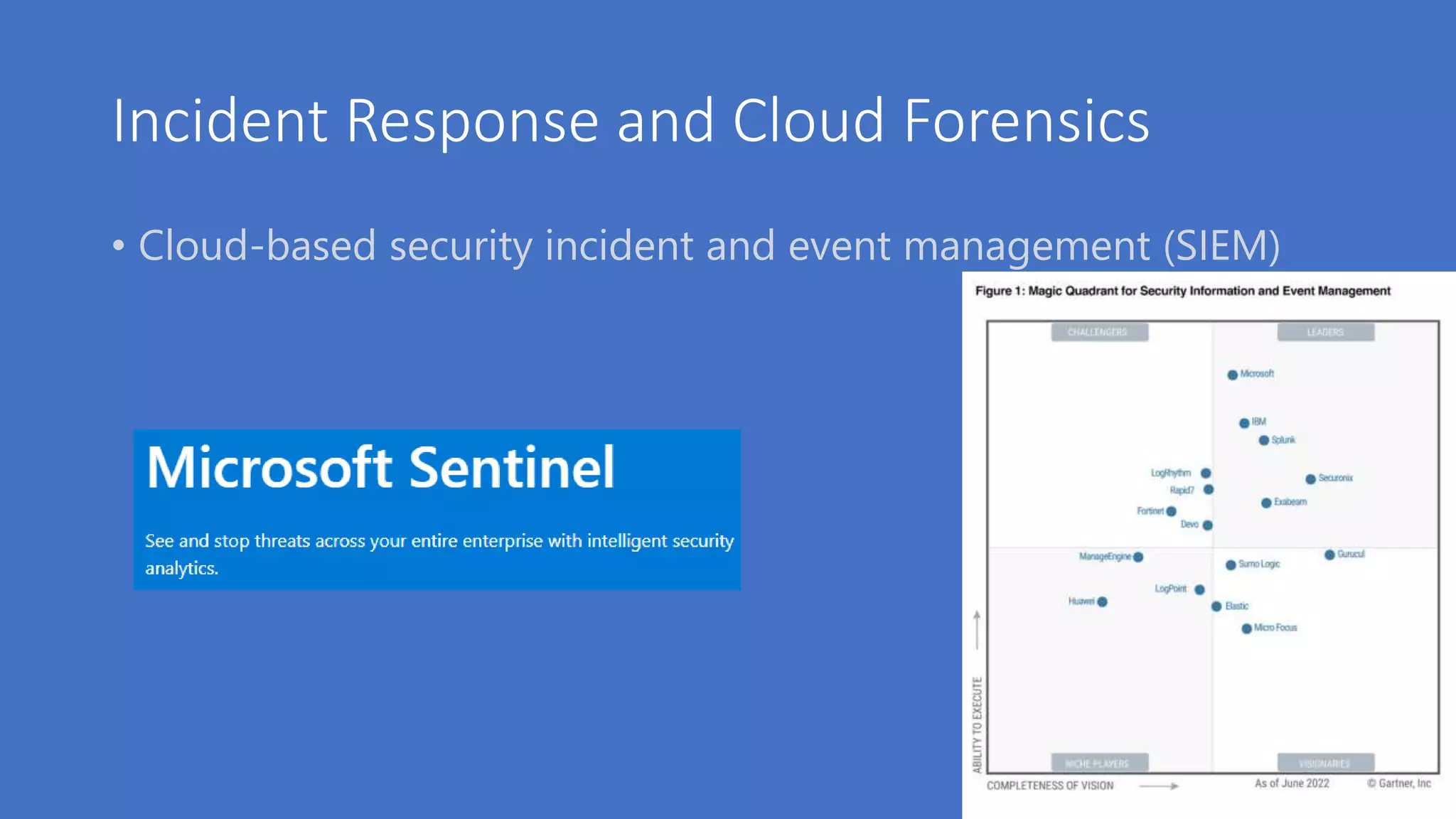
The document discusses various aspects of cloud security, highlighting numerous data breaches from notable companies and the evolving threat landscape. It emphasizes the shared responsibility of security between cloud service providers and users, along with best practices for secure application development and compliance. Key topics include access control, data security, network security, and incident response strategies.