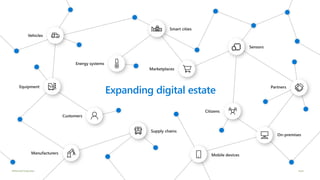
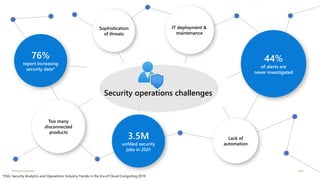
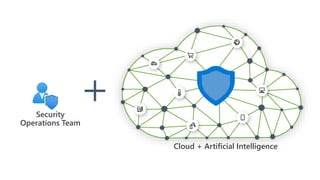
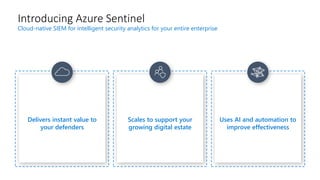
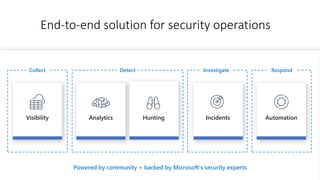
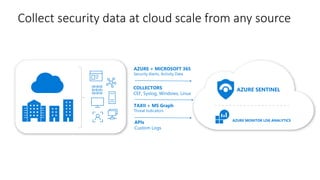
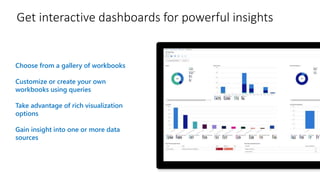
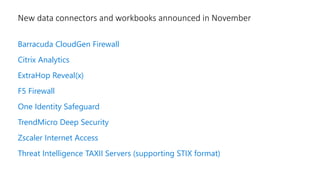
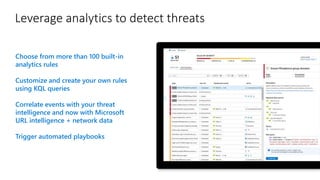
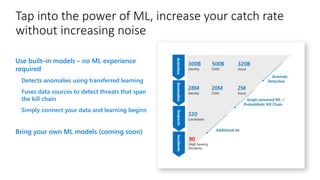
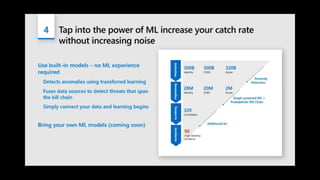
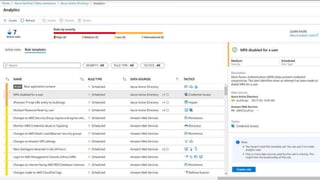
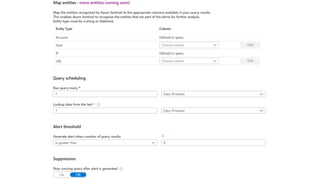
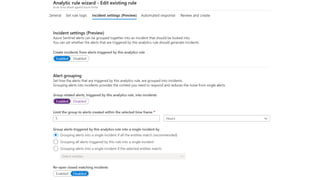
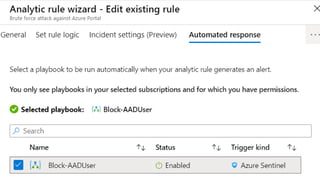
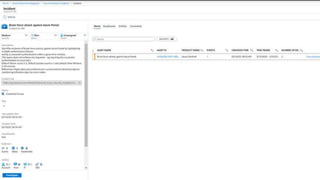
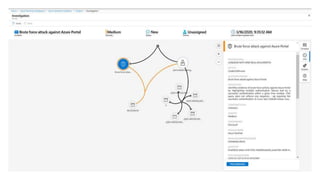
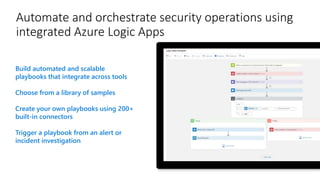
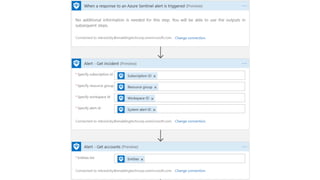
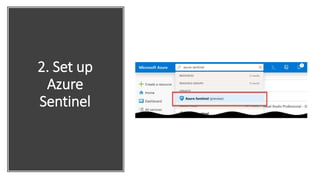
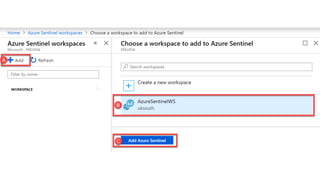
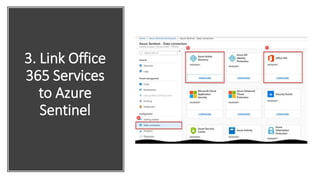
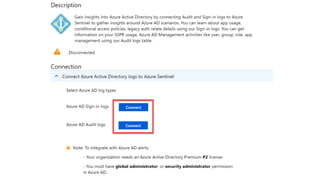
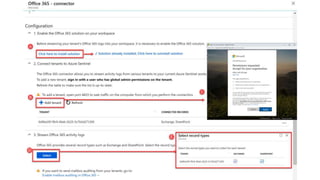
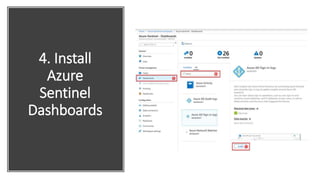
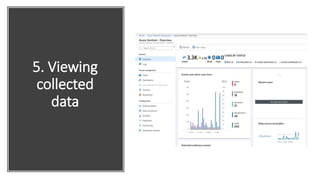
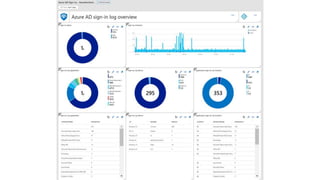
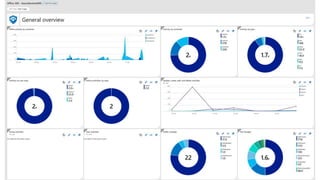
This document provides an overview of Azure Sentinel and how it can be used with Office 365. It discusses the challenges of security operations and how Azure Sentinel uses AI and automation to help. It then summarizes Azure Sentinel's key capabilities including visibility, analytics, hunting, incidents, and automation. It also includes demonstrations of these capabilities and steps to set up Azure Sentinel with an Office 365 connection.