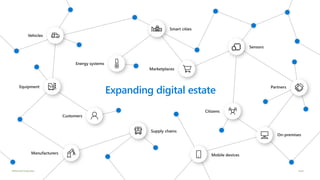
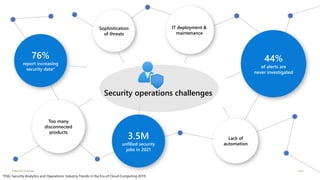
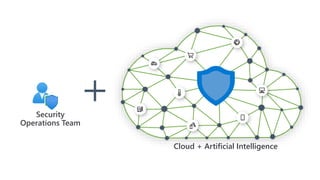
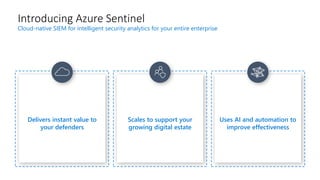
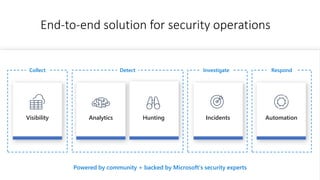
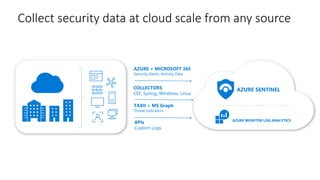
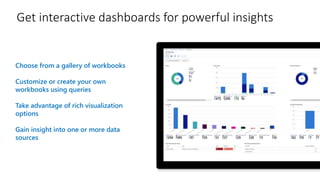
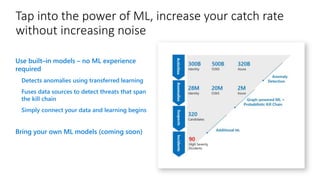
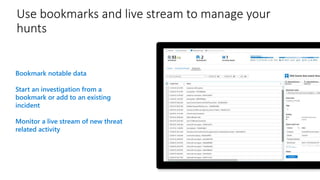
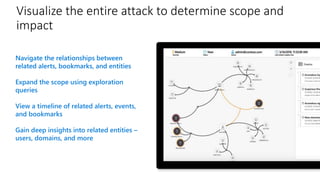
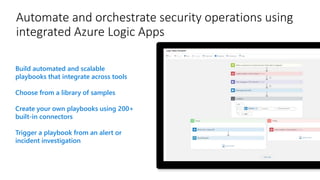
Modernize your security operations with Azure Sentinel. Azure Sentinel is a cloud-native security information and event management (SIEM) solution that uses artificial intelligence and automation to help detect threats across your entire enterprise. It collects security data from any source, uses built-in analytics and AI to detect threats, enables hunting of security data through queries, and allows you to start investigations from prioritized incidents. Azure Sentinel also provides automation capabilities through integrated logic apps to automate security operations.