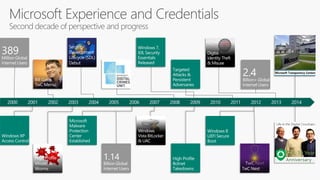
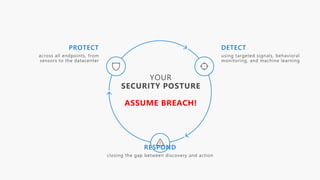
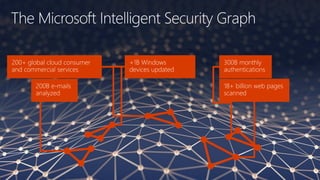
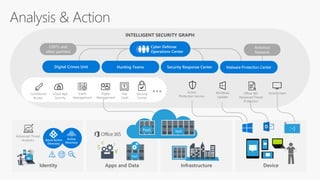
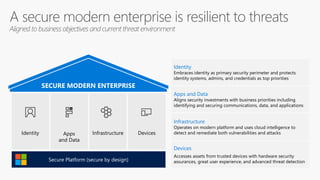
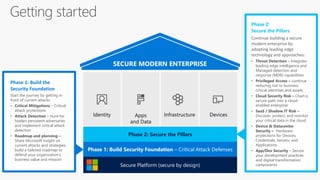
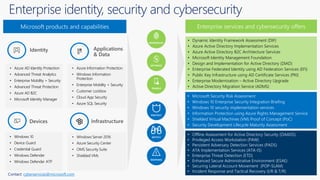
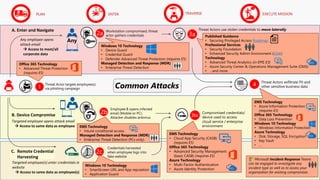
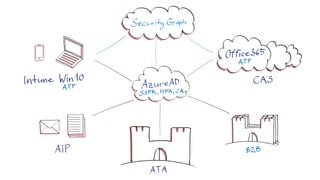
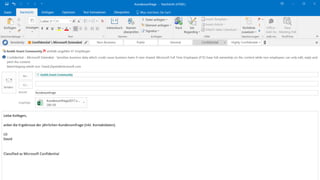
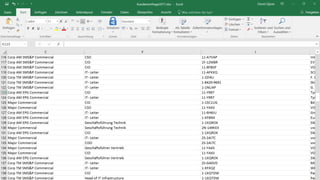
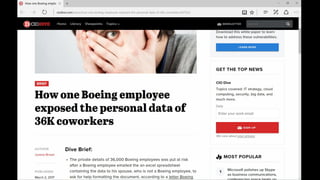
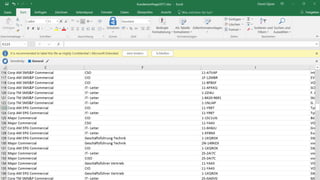
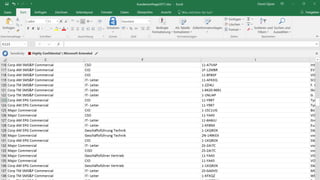
The document discusses cybersecurity and protecting information. It provides statistics on why organizations want to protect information, such as to reduce data leakage, meet compliance requirements, and partition sensitive data from unauthorized users. It then lists some of Microsoft's security capabilities for protecting devices, customer data in the cloud, on-premises environments, and customer data both in the cloud and on-premises.