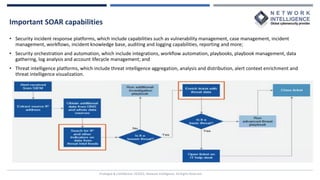
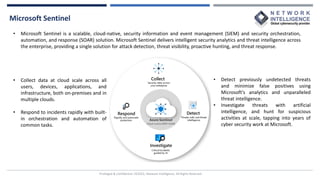
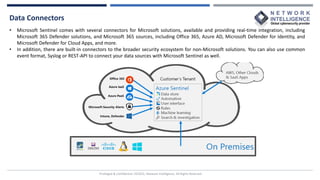
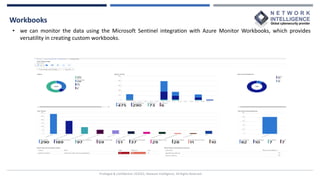
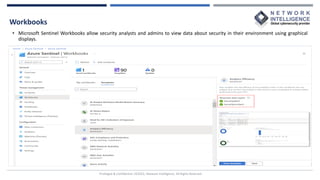
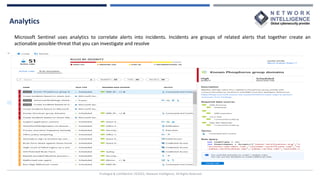
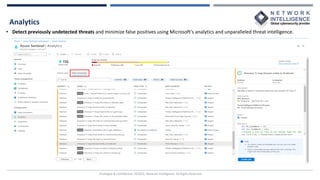
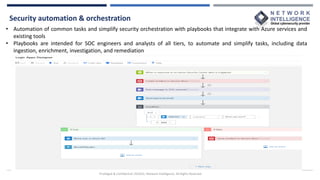
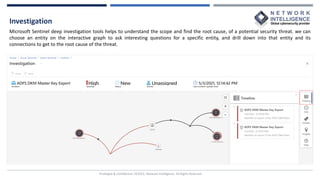
This document provides an overview of Microsoft Sentinel, a cloud-native SIEM and SOAR solution. It discusses what SOAR is, important SOAR capabilities like security orchestration and automation. It also covers the benefits of SOAR like faster incident detection and boosting analyst productivity. The document then explains how Microsoft Sentinel collects data at cloud scale, responds to incidents with automation, and detects threats using analytics. It describes features like data connectors, workbooks, hunting, notebooks and certifications related to Microsoft Sentinel.