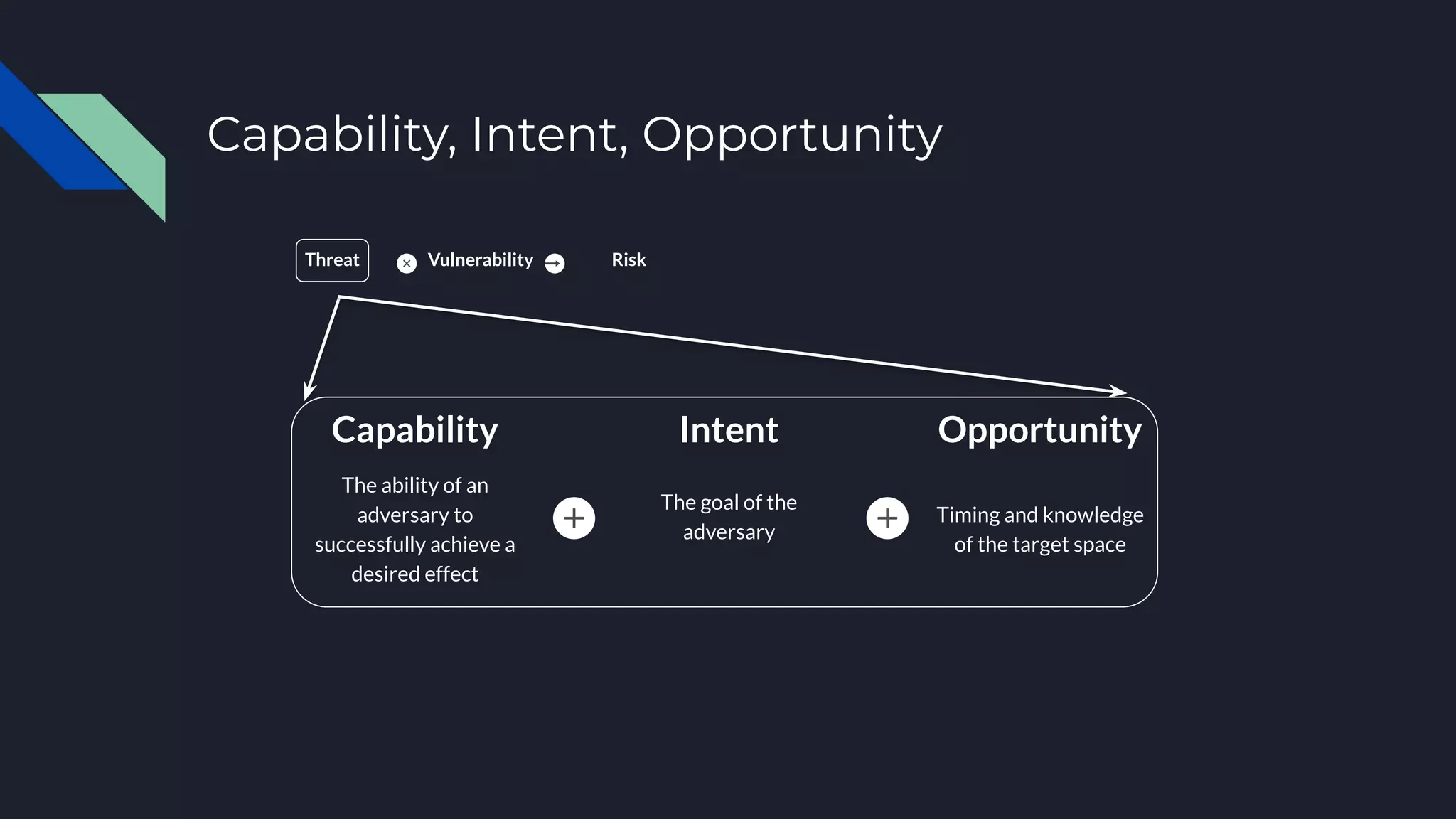
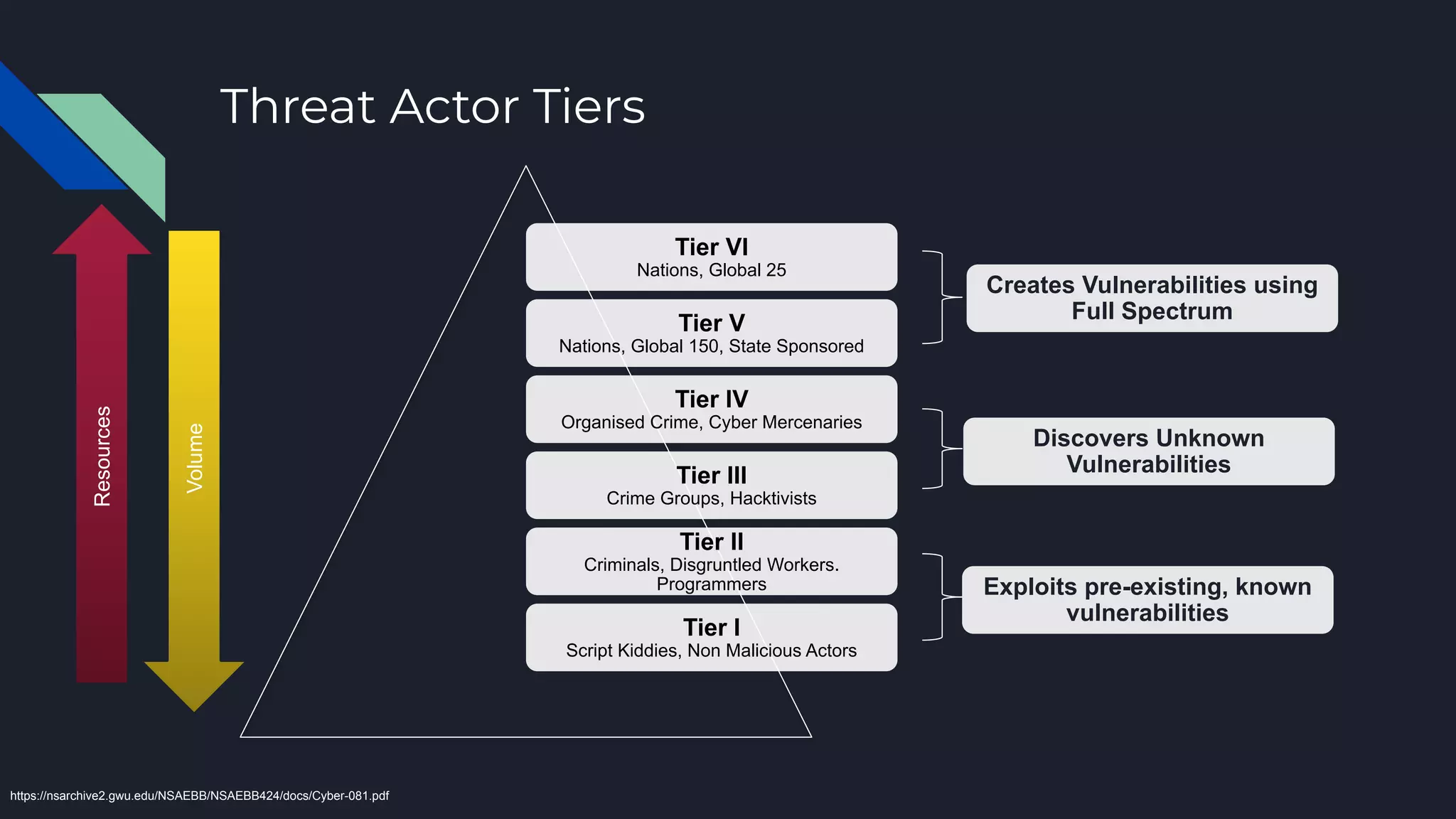
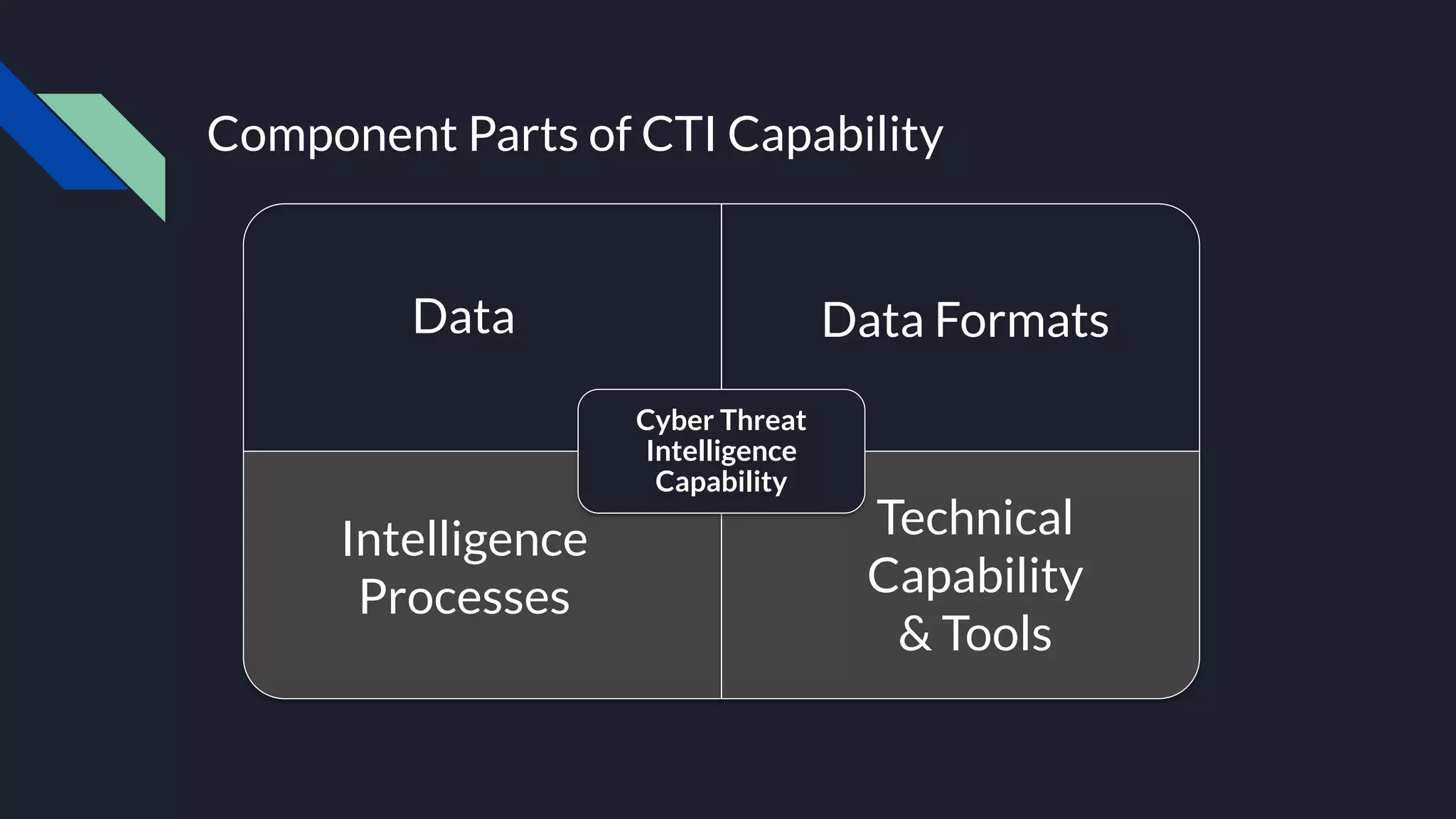
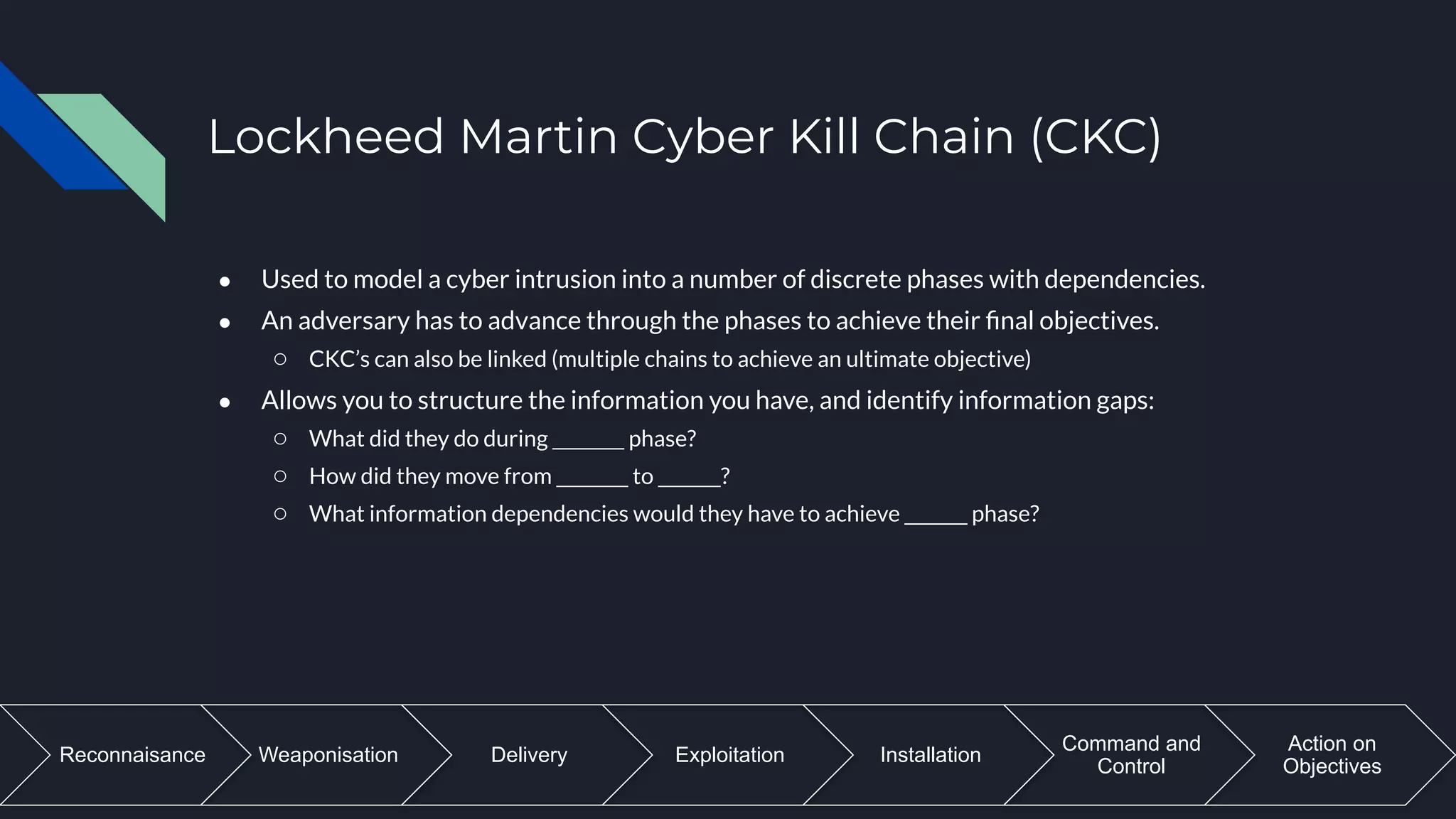
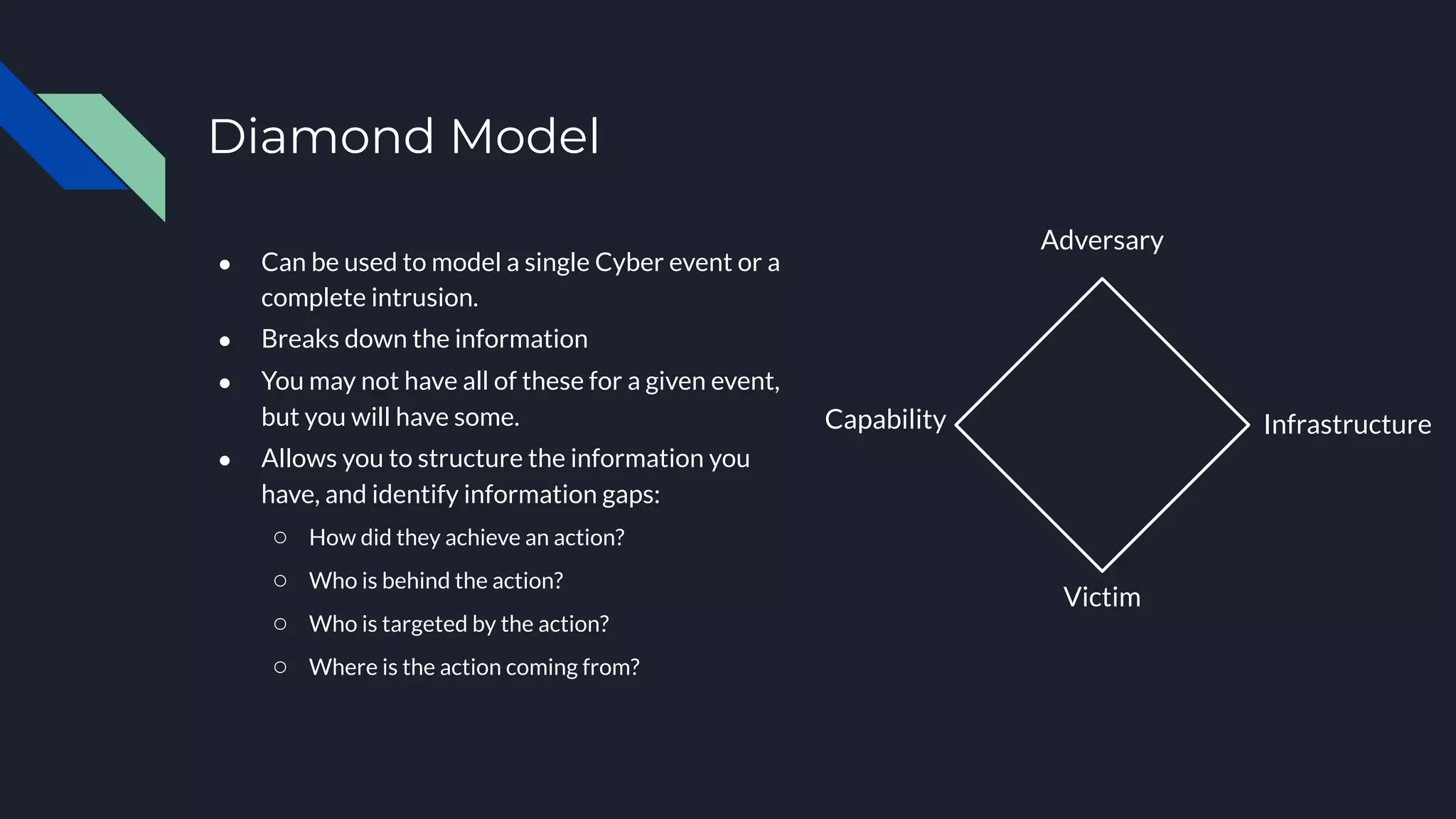
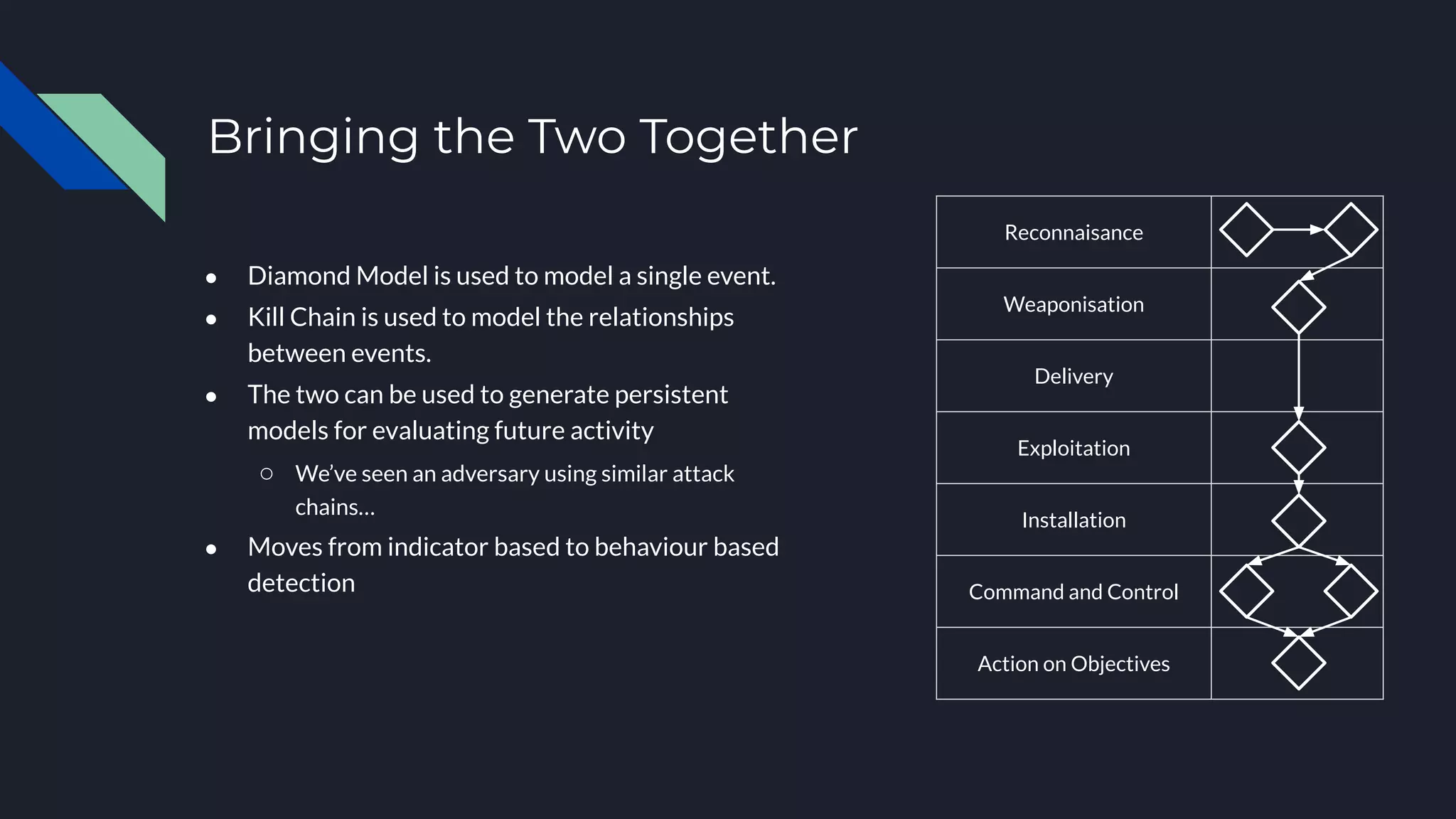
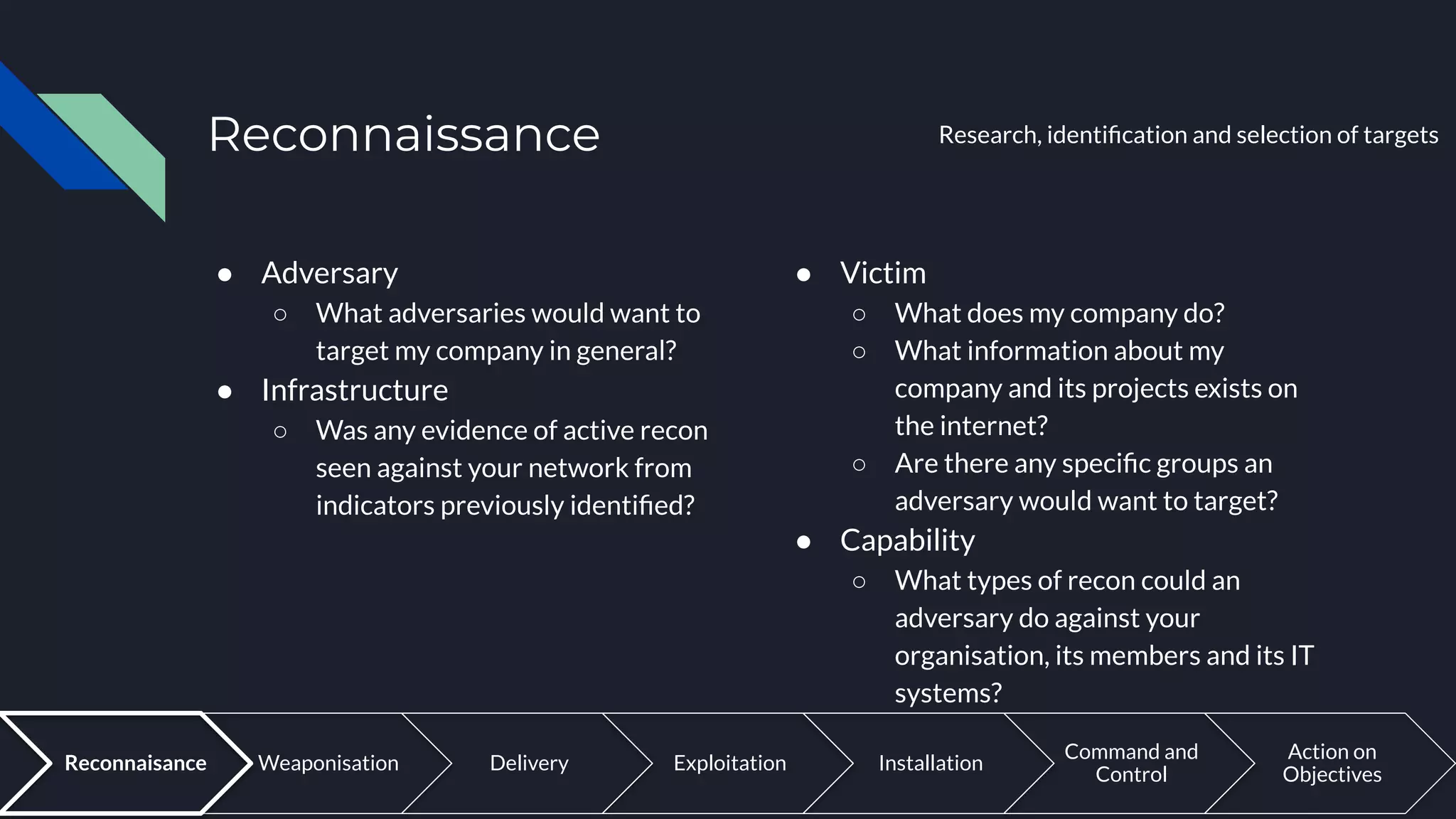
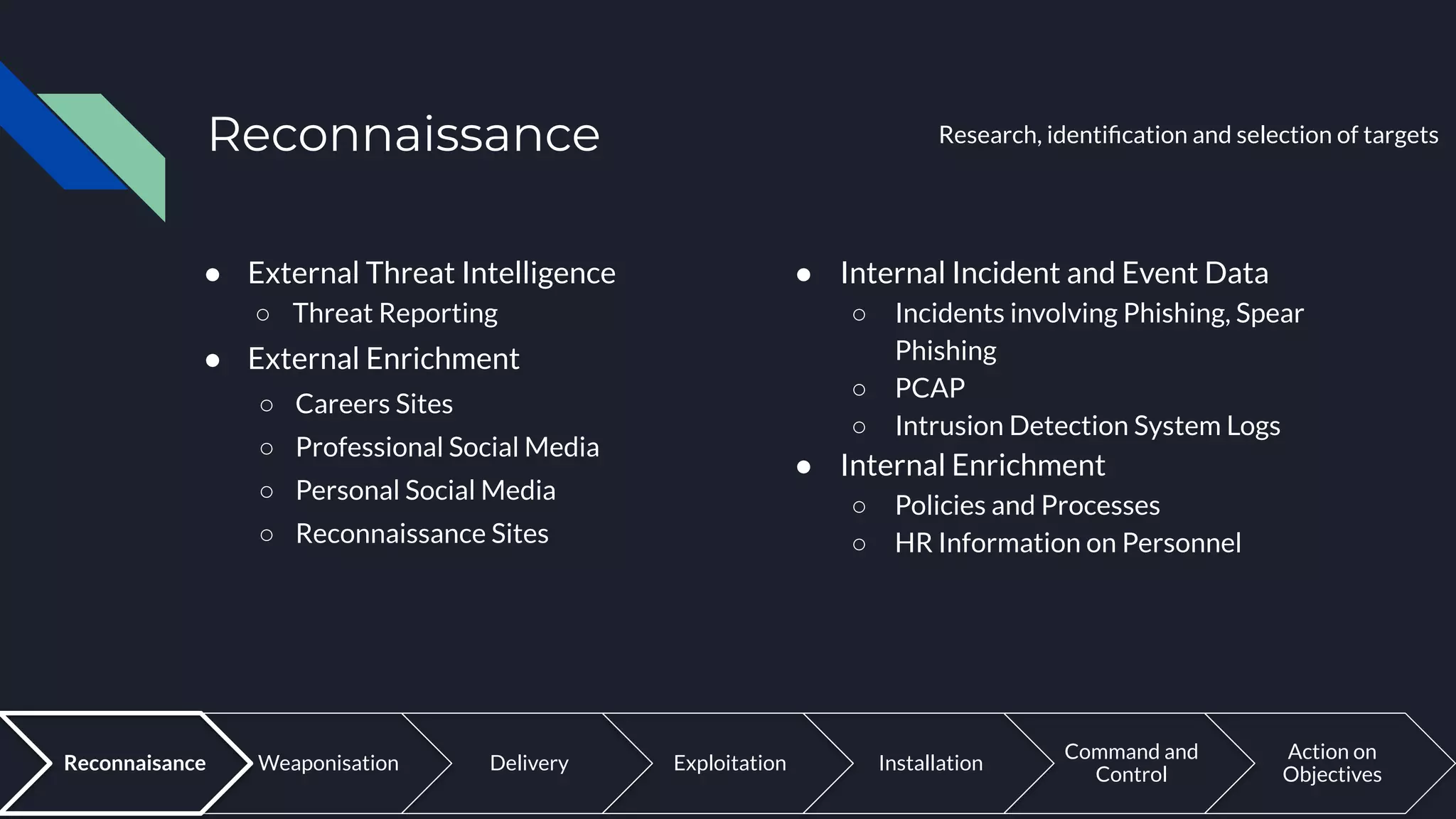
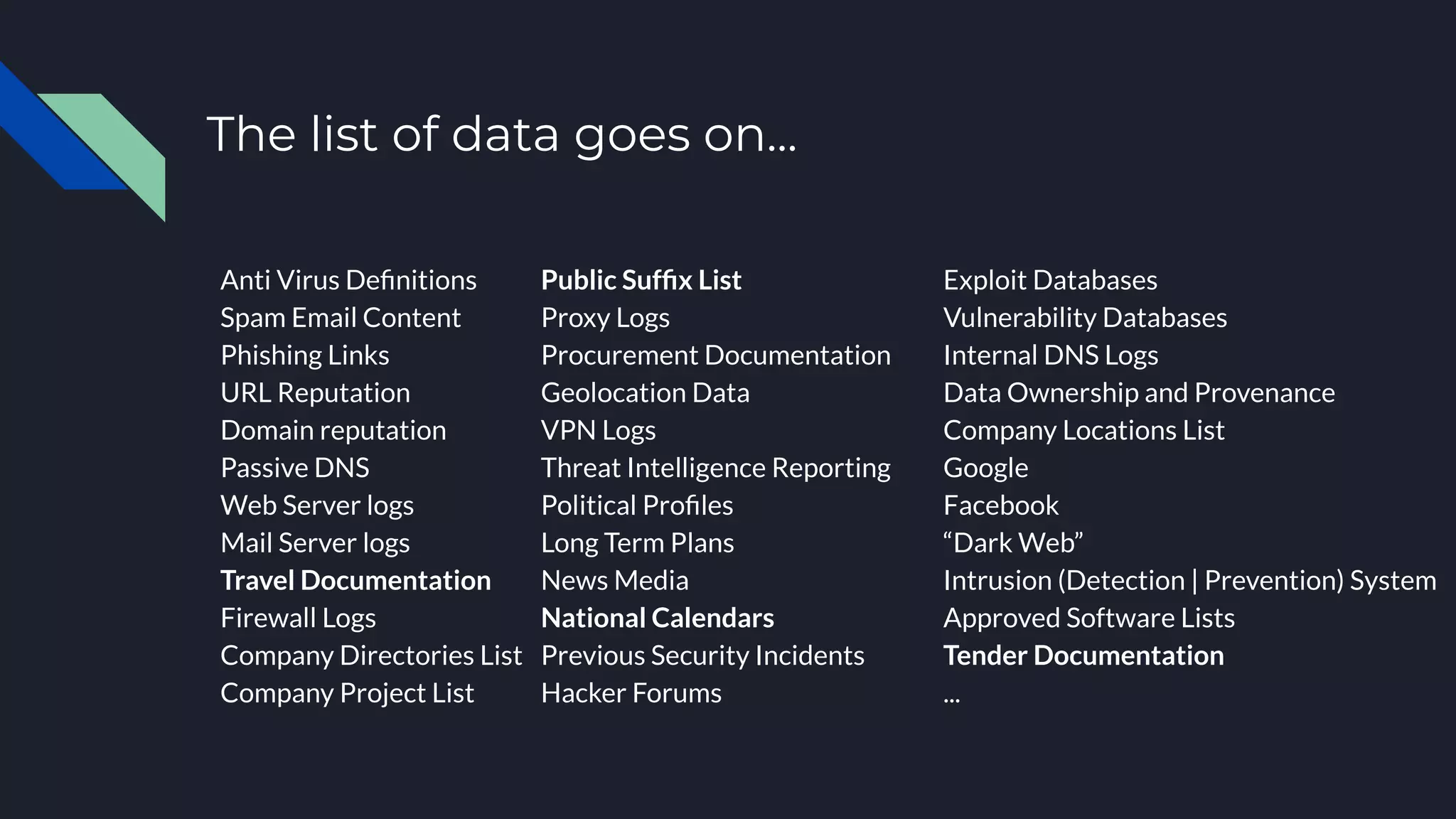
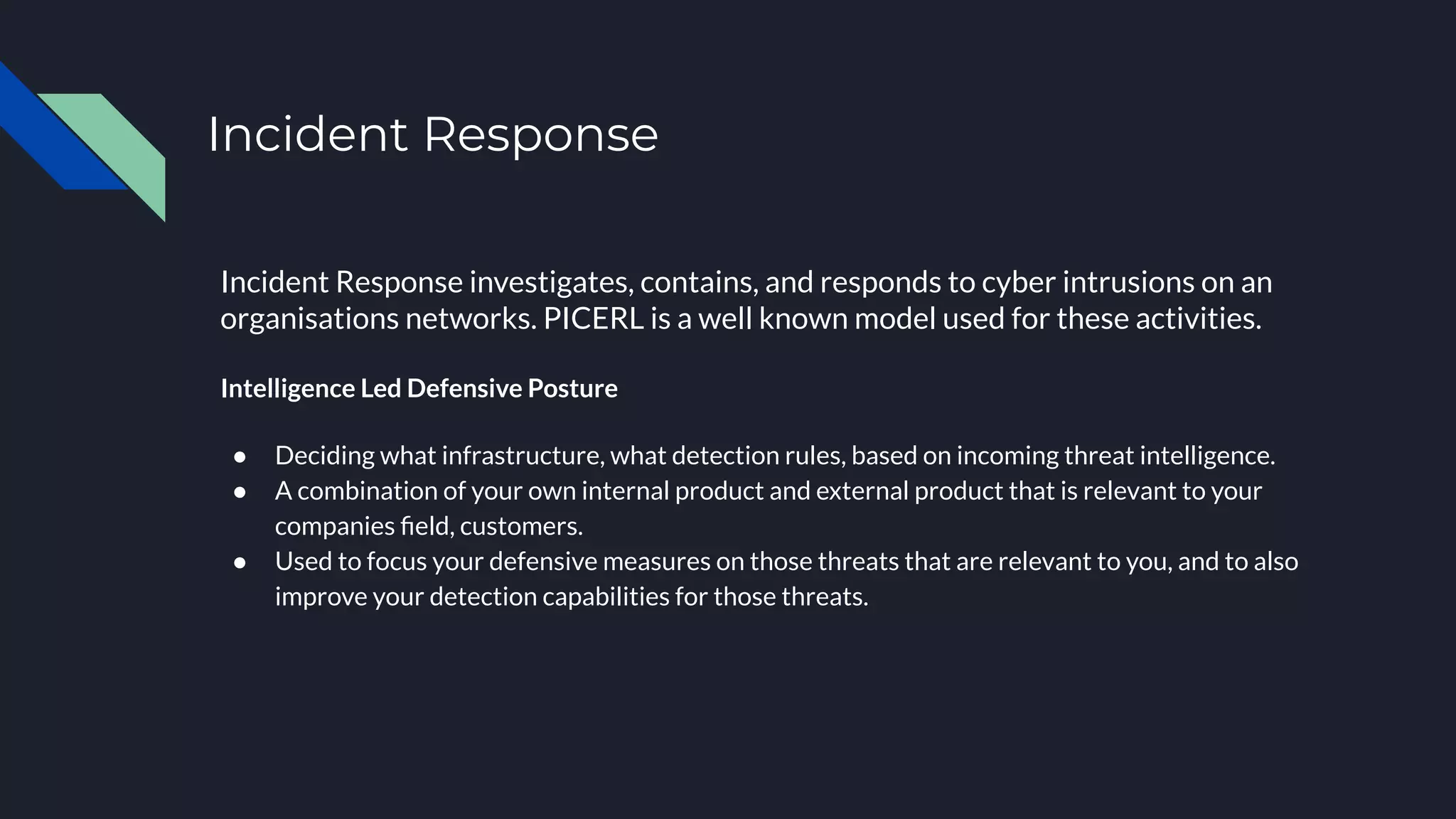
The document discusses cyber threat intelligence and how it can support defensive cyber operations. It defines cyber threat intelligence and outlines different data source types that can be used, including internal incident data and external threat intelligence. It describes the Lockheed Martin Cyber Kill Chain and Diamond Models for structuring threat information and identifying gaps. Actionable threat intelligence requires both internal and external data across the cyber kill chain phases to generate useful context. Threat intelligence can help with incident response, penetration testing, and establishing an intelligence-led defensive posture focused on the most relevant threats.