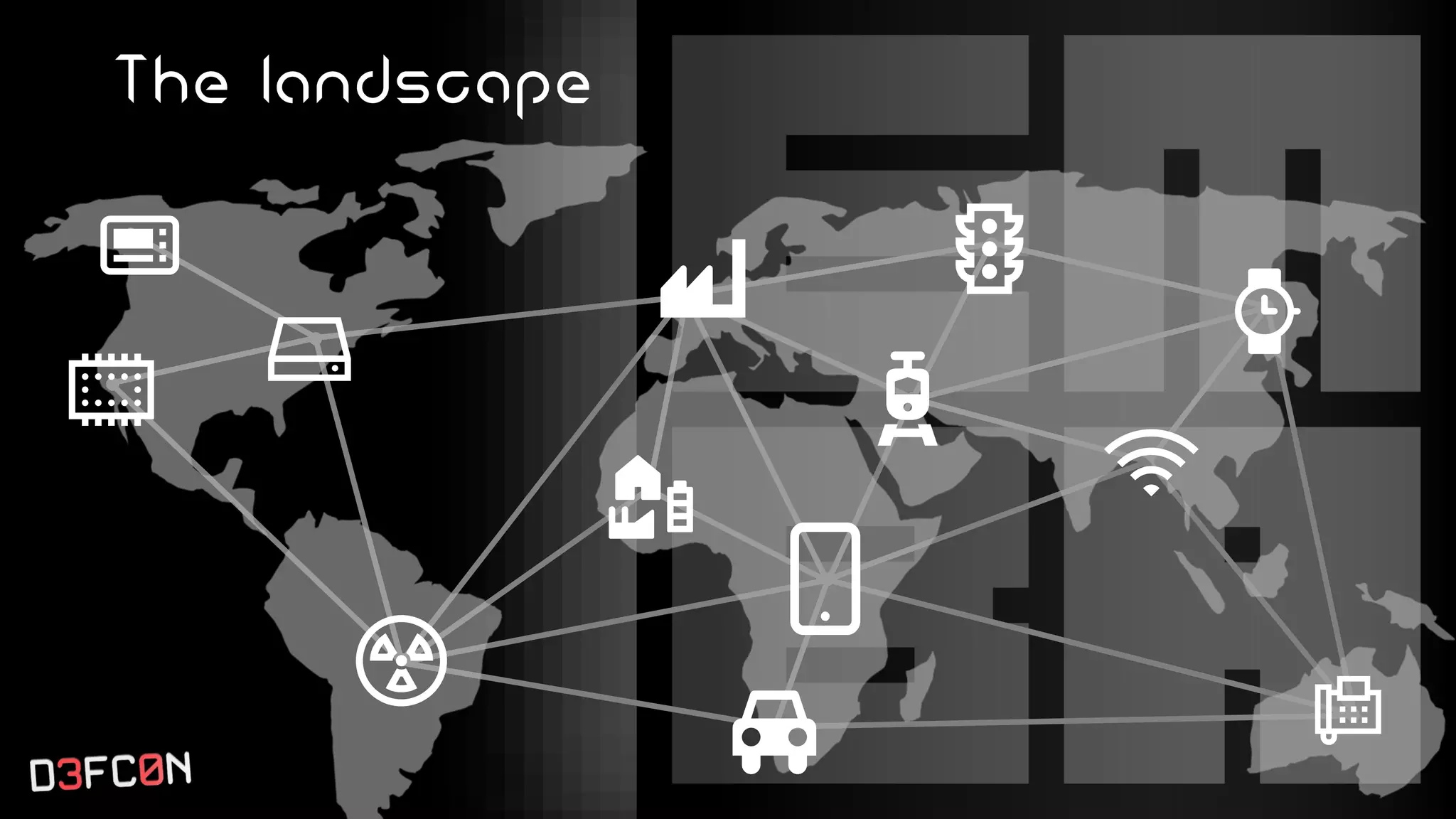
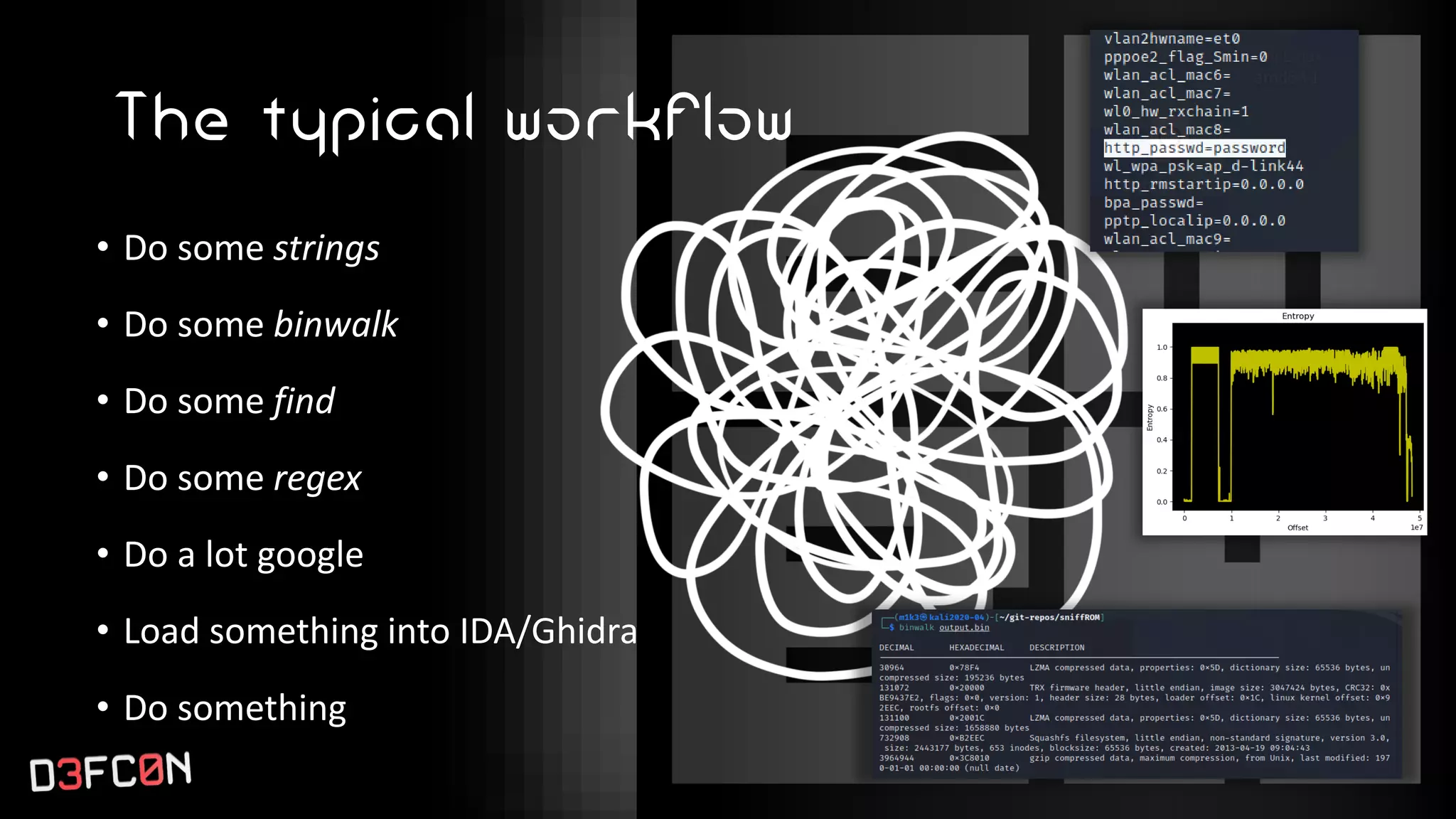
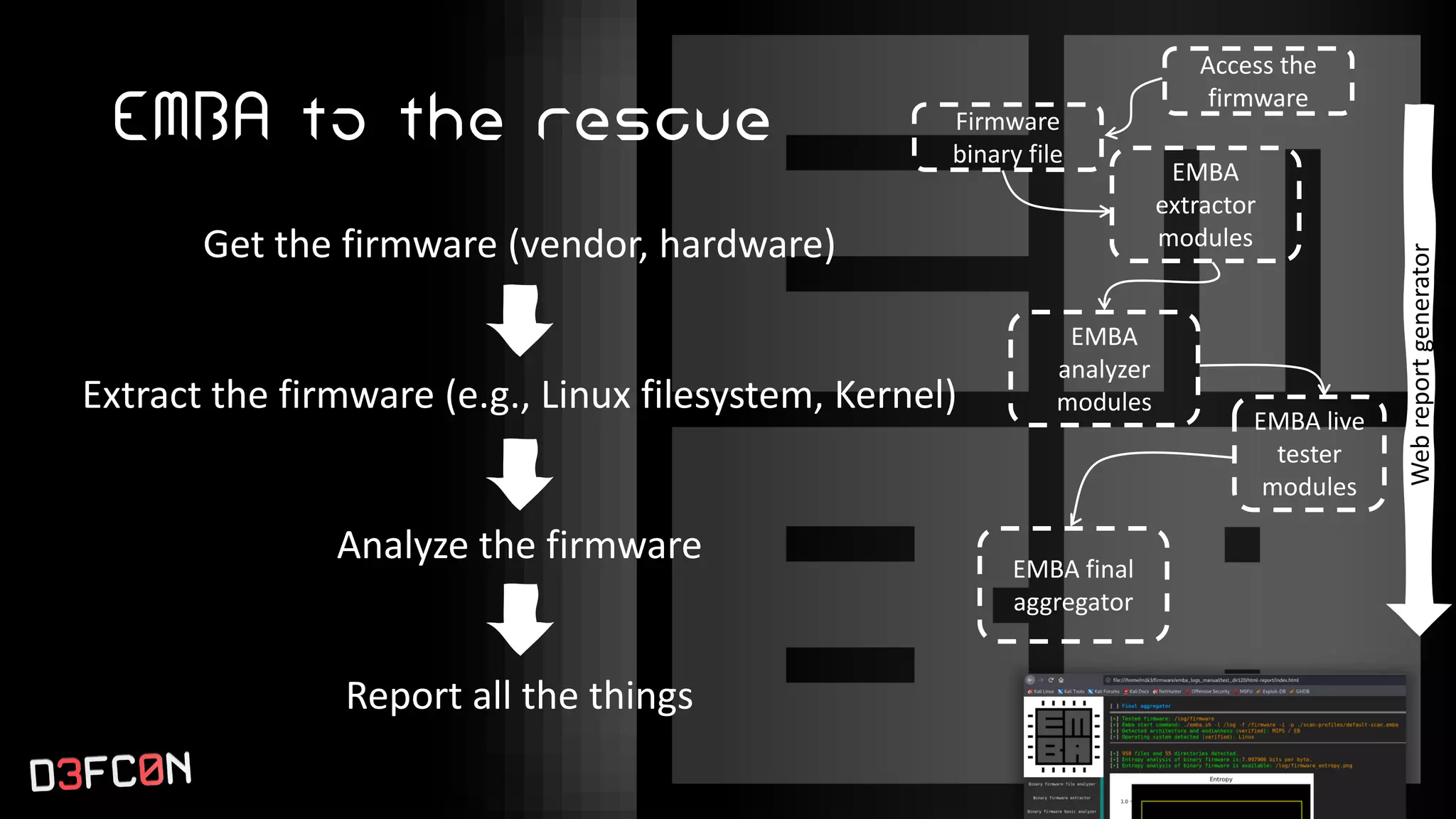
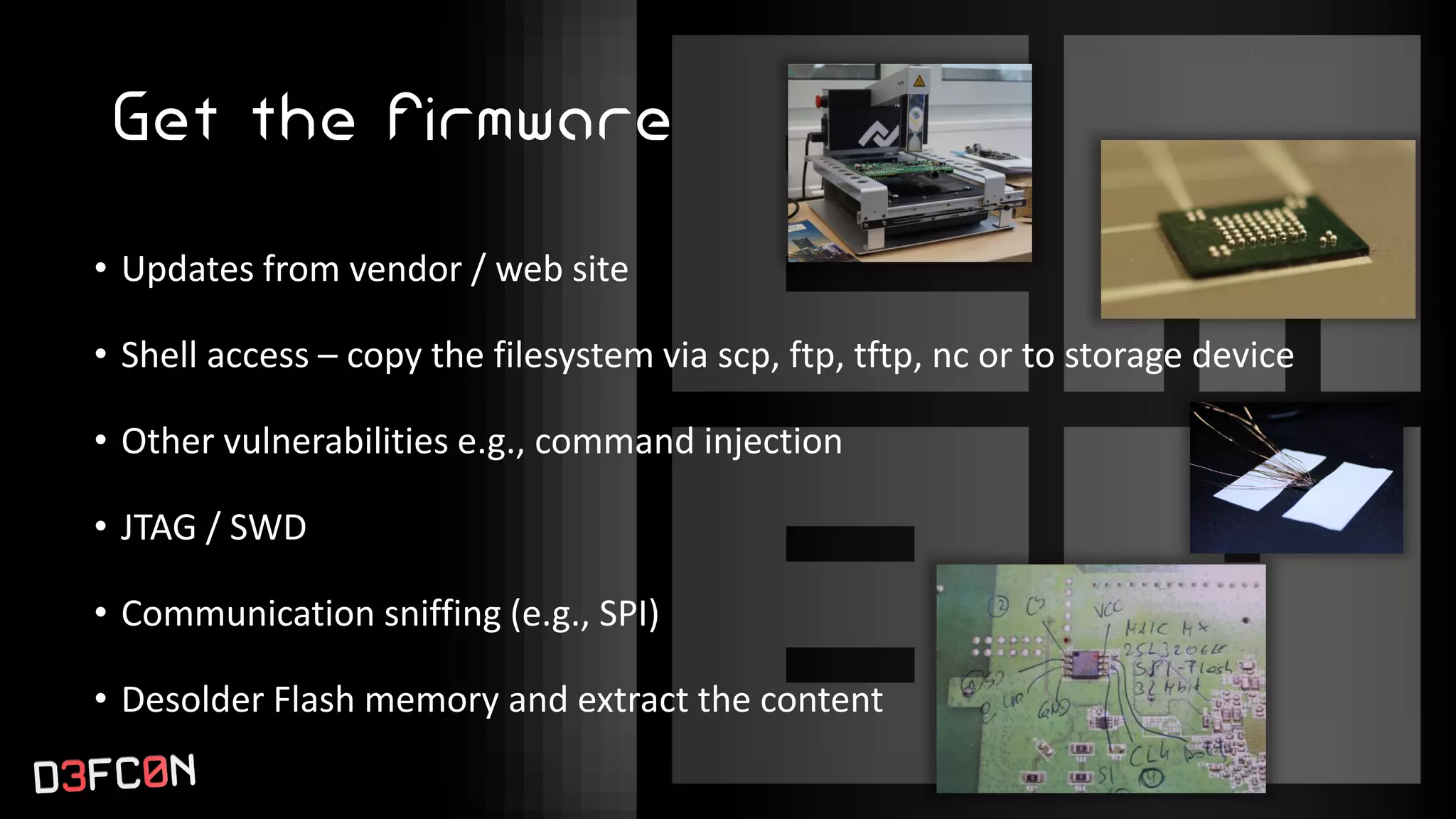
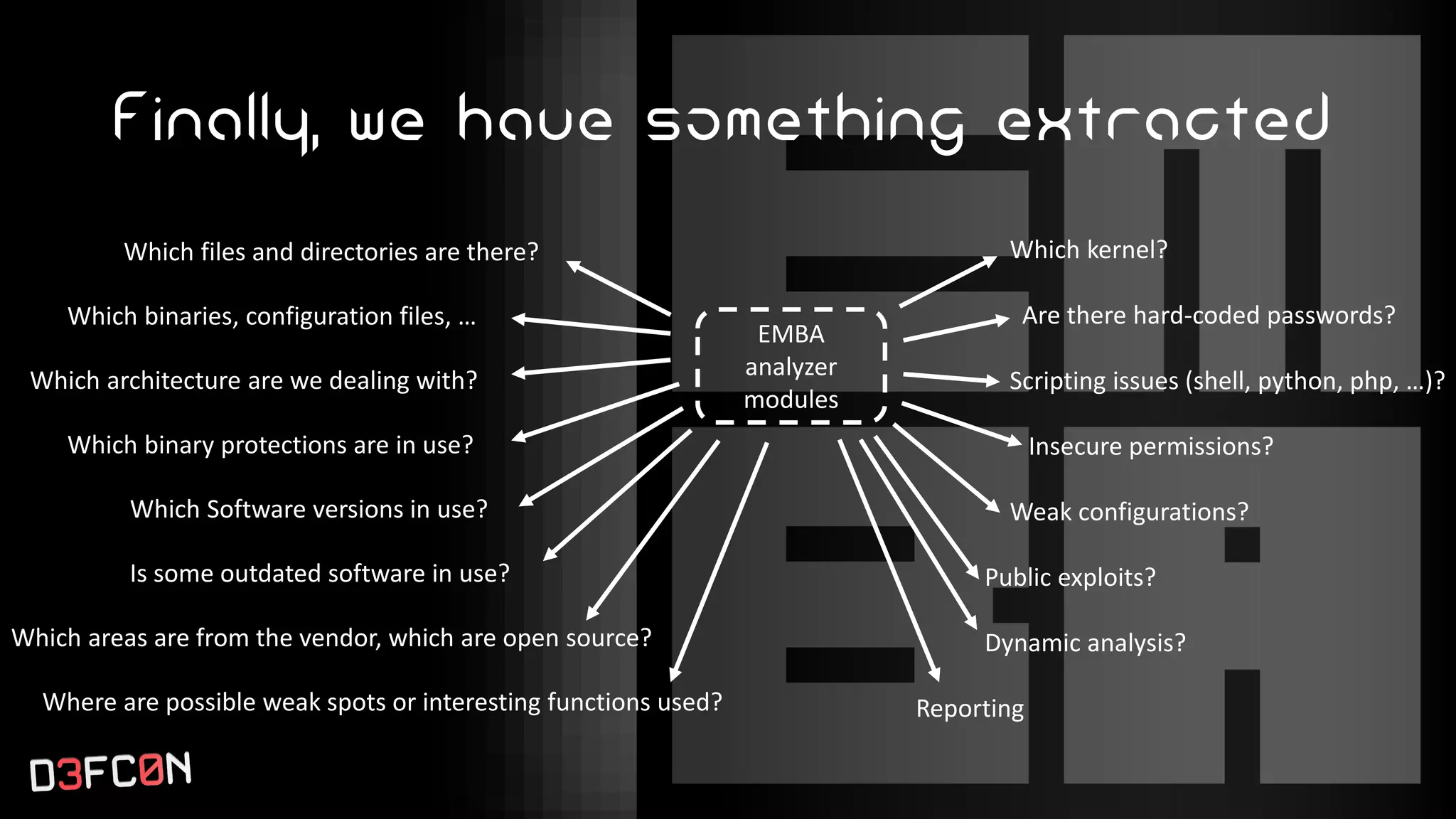
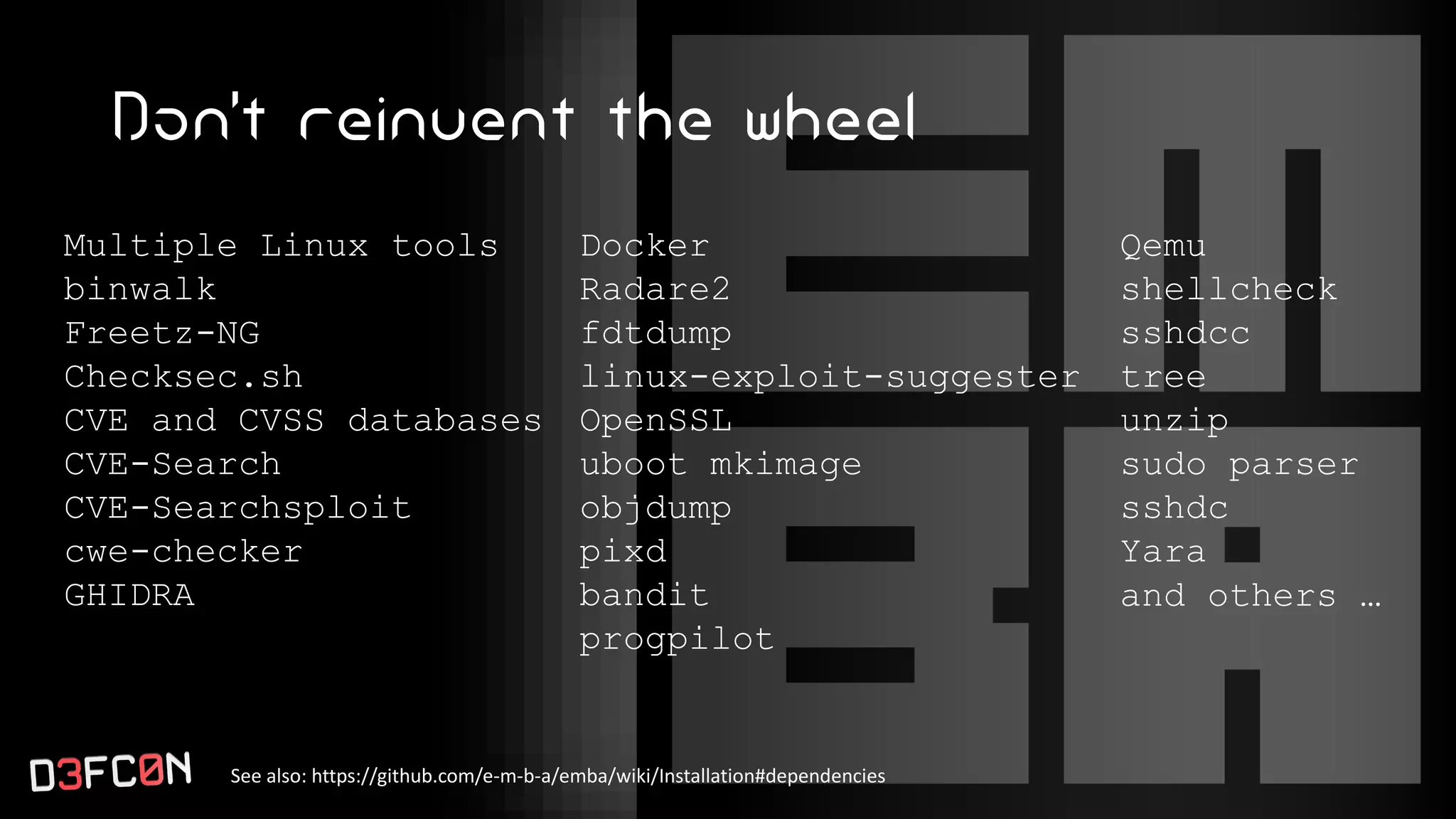
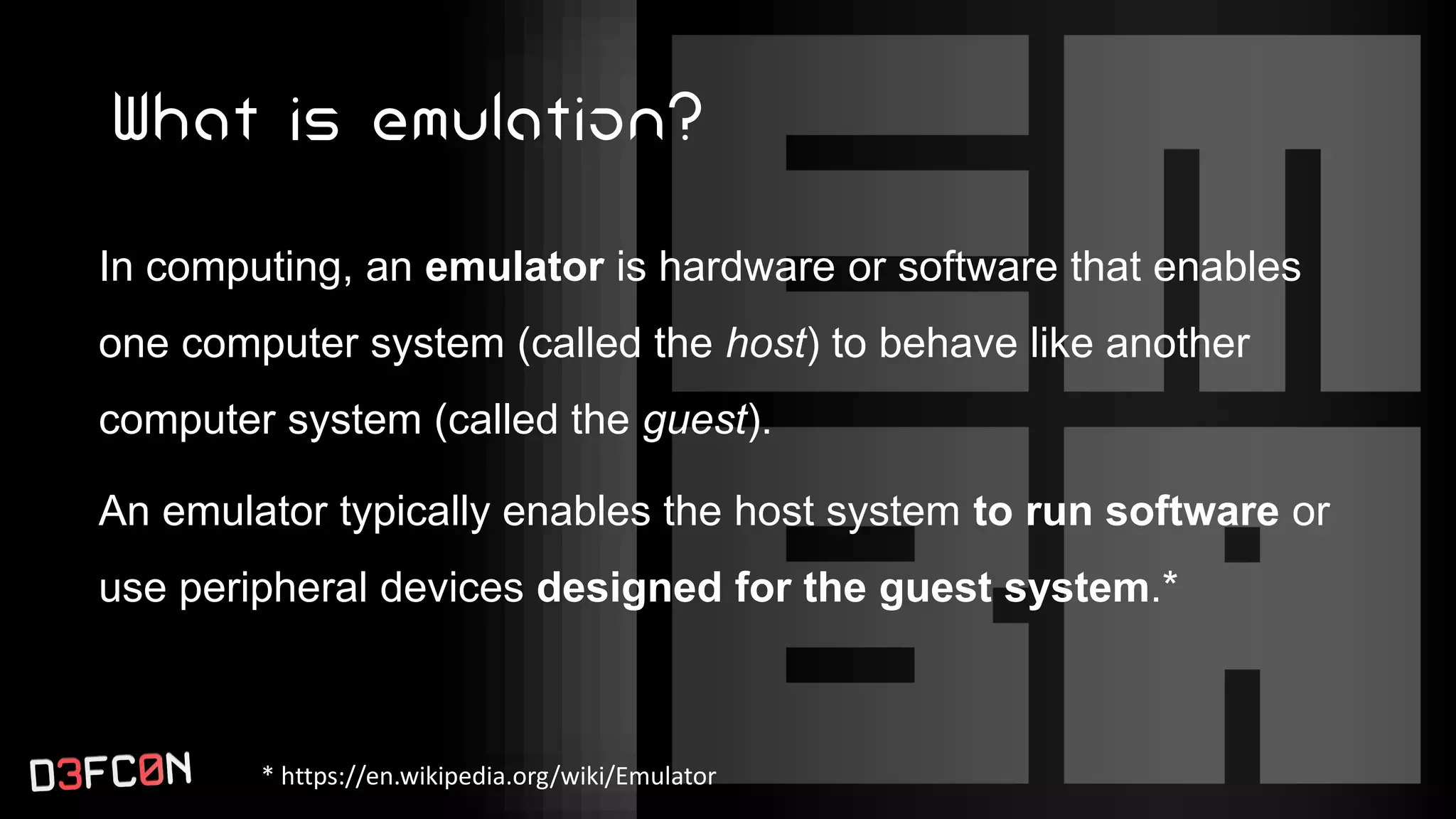
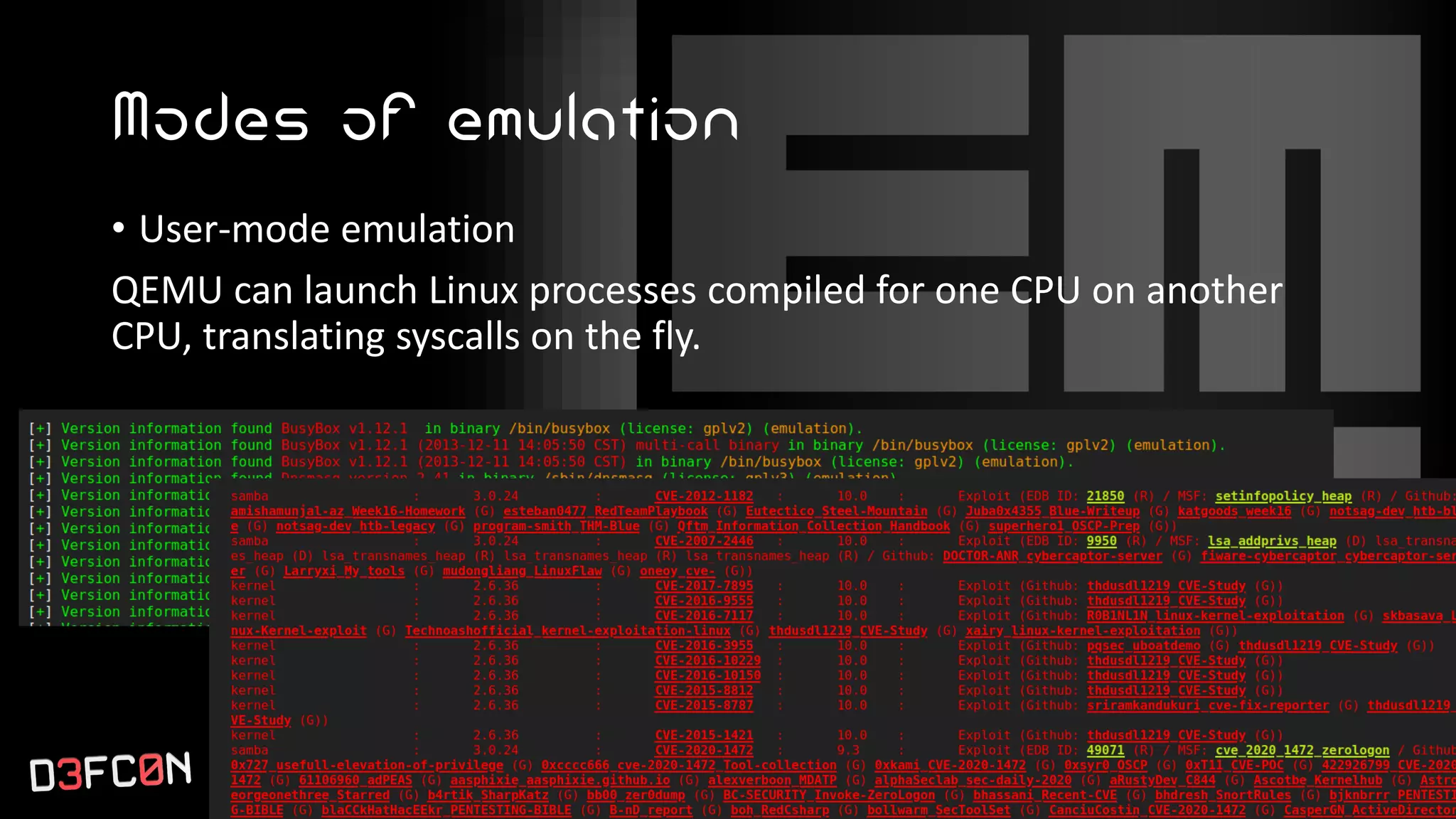
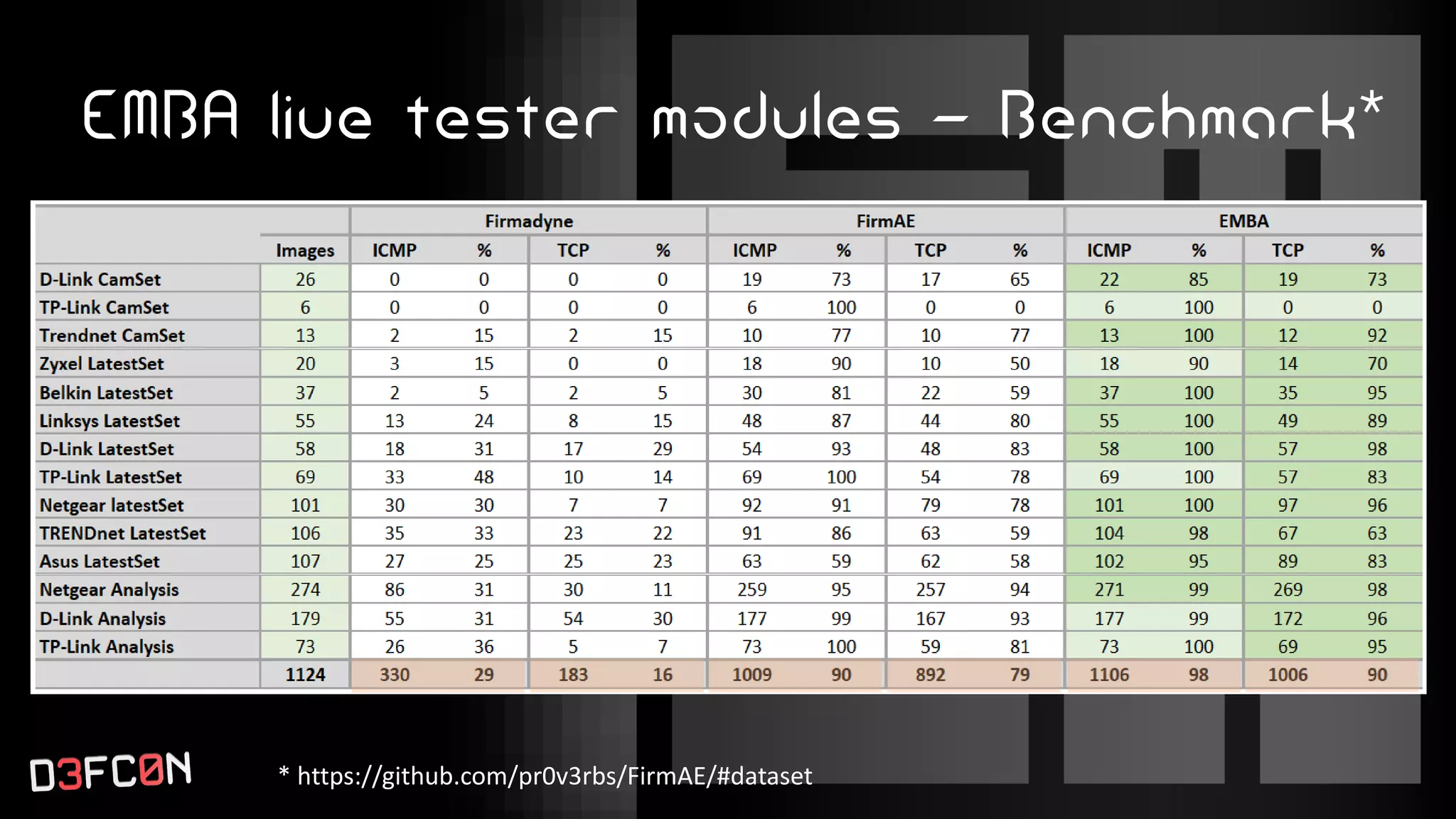
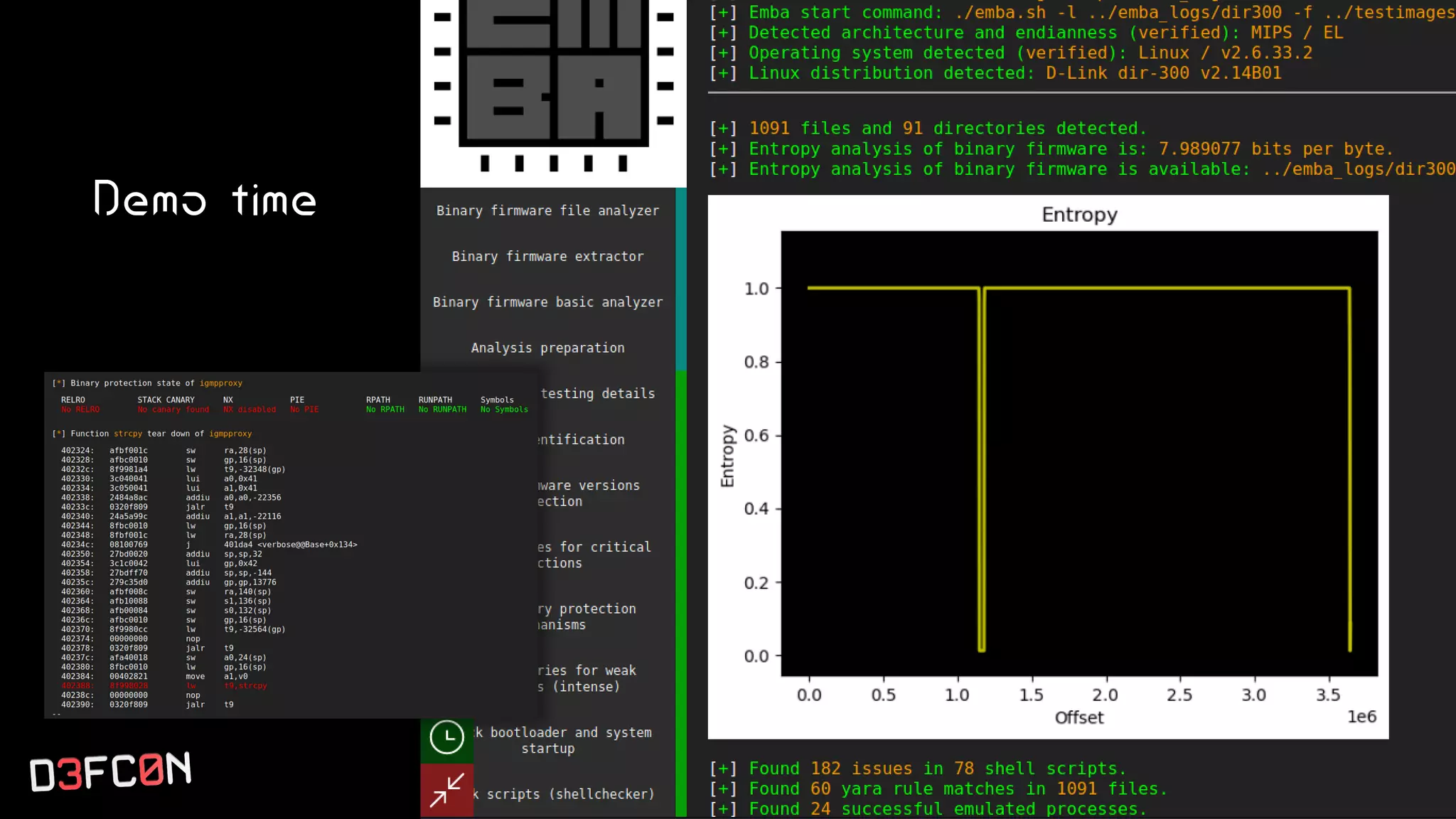
The EMBA Firmware Security Analyzer is a comprehensive tool for analyzing and extracting firmware, designed by Michael Messner and Pascal Eckmann from Siemens. It simplifies the firmware analysis process by integrating multiple workflows and tools, allowing for deep extraction, analysis, and reporting of vulnerabilities found in firmware. EMBA utilizes various methods, including user-mode and system-mode emulation, to enhance automated analysis capabilities and highlight potential security weaknesses in embedded systems.