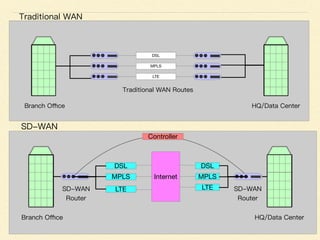
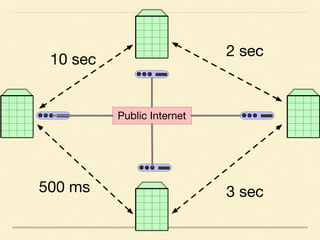
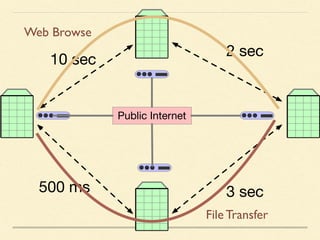
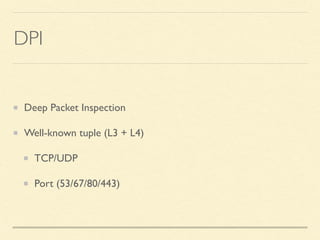
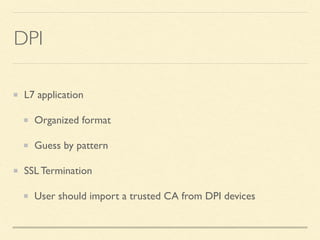
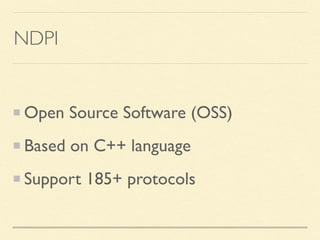
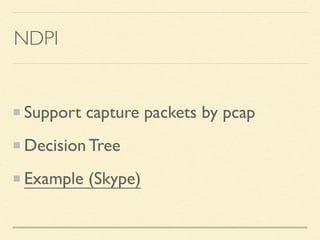
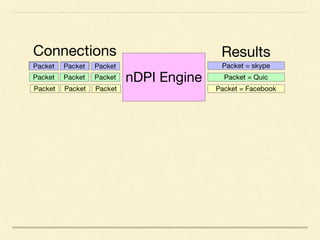
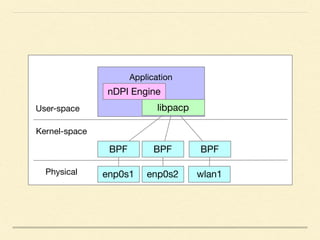
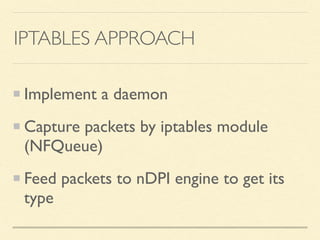
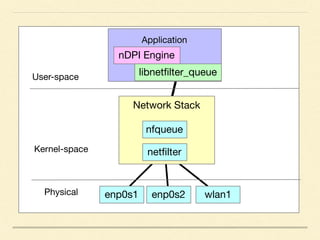
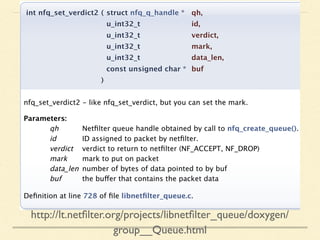
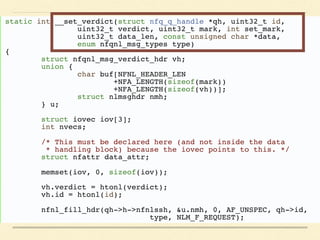
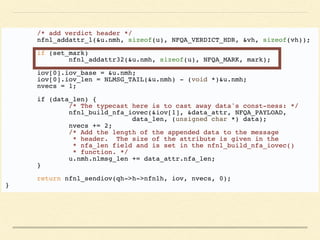
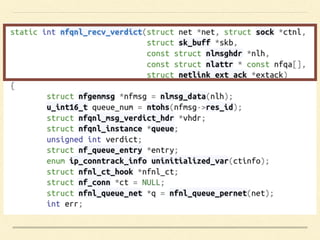
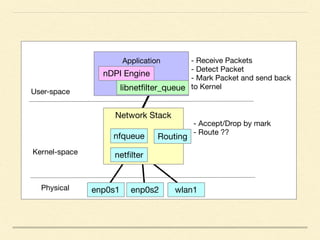
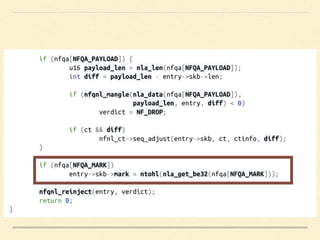
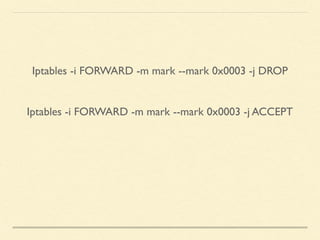
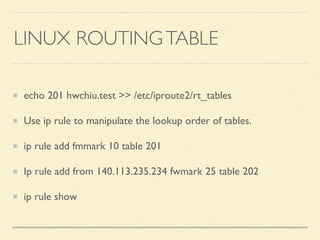
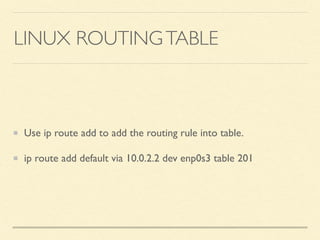
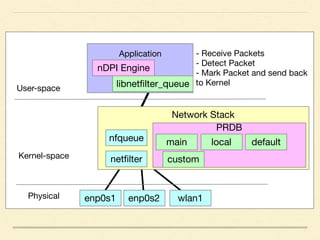
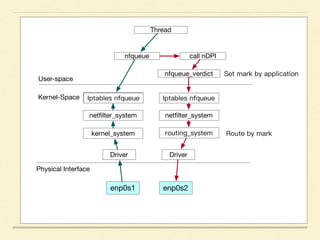
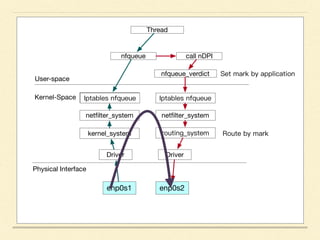
The document discusses application-based routing in Software Defined Wide Area Network (SD-WAN) environments, detailing how to optimize traffic routes based on application priority using various Linux kernel techniques. It explains the challenges of implementing deep packet inspection (DPI) and routing decisions through methods like netfilter and iptables. The presentation emphasizes performance improvements by leveraging connection tracking and reducing the need for excessive packet inspections.