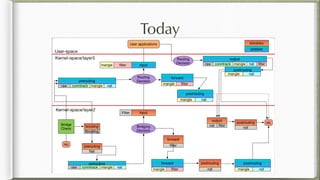
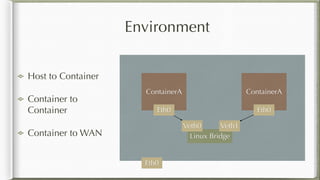
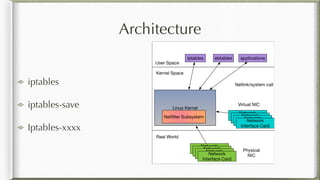
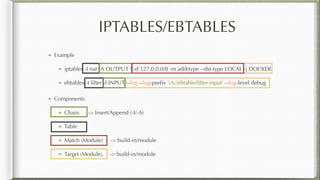
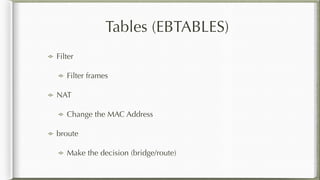
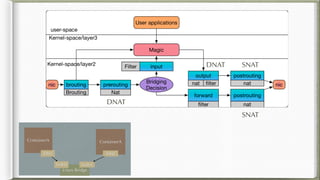
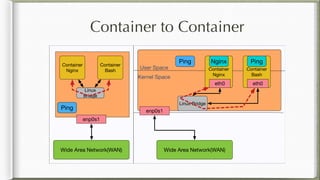
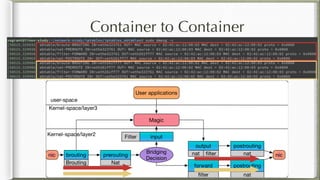
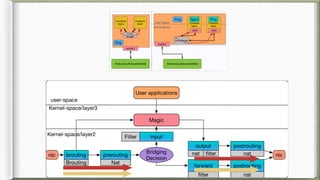
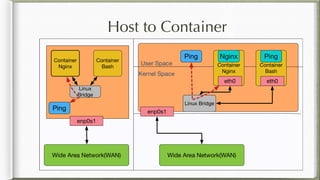
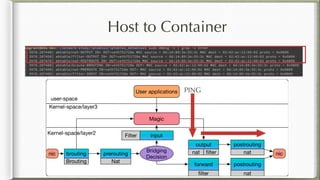
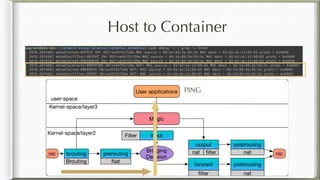
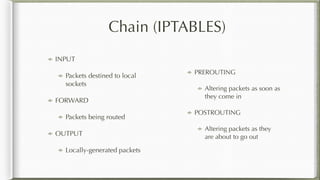
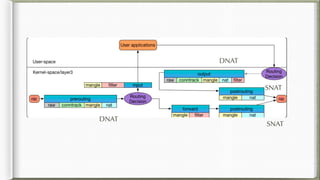
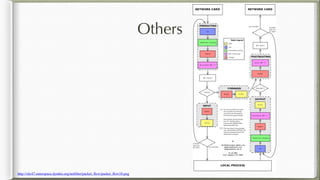
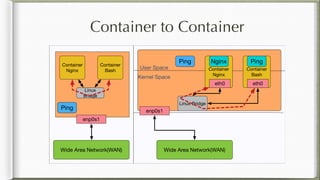
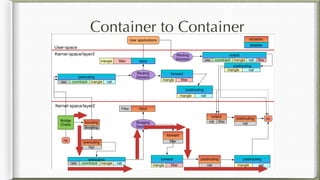
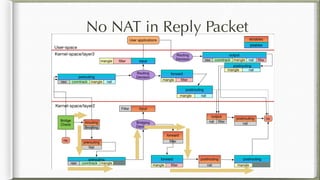
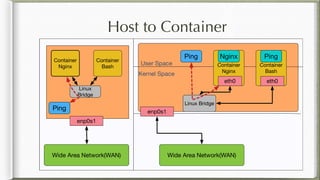
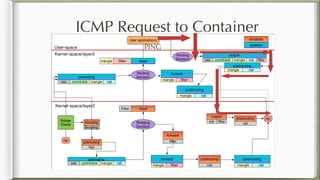
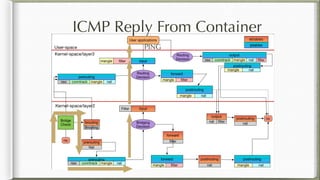
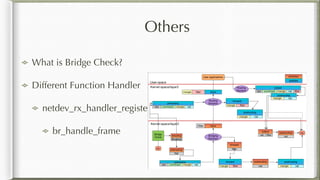
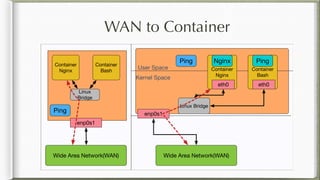
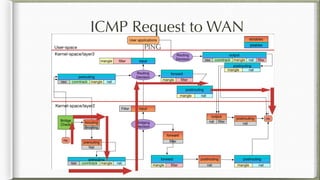
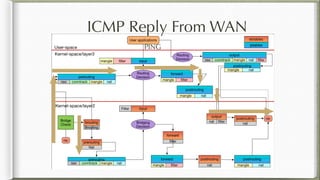
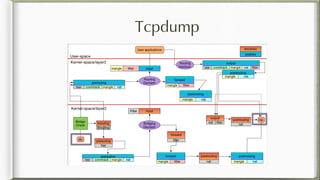
The document discusses iptables and its implementation in networking, particularly within containerized environments using Docker and Kubernetes. It covers various aspects like ebtables, connection tracking, and the modification of kernel modules to manage packet flow between hosts and containers. The document also includes practical examples of setting up rules, generating traffic, and debugging network connections.