This document provides an overview of nftables, the new packet filtering framework that replaces iptables in the Linux kernel. It discusses the history and predecessors to nftables, how nftables works, key differences from iptables like its more flexible table and chain configuration, and examples of basic nftables rulesets. It also covers topics like matches, jumps, load balancing performance, and kernel configuration options for nftables.



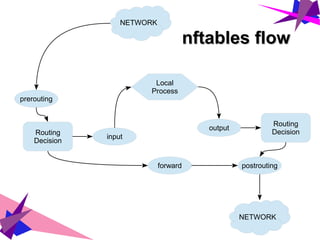
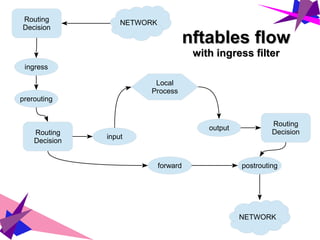
![nftables vs. iptablesnftables vs. iptables
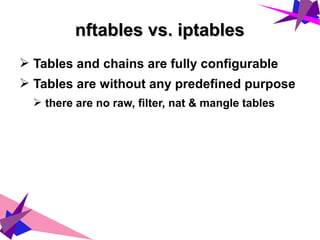
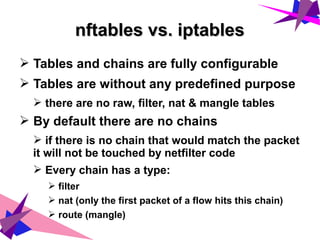
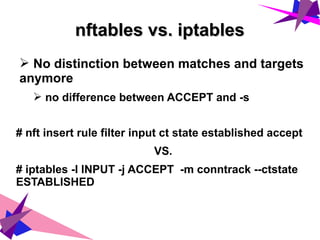
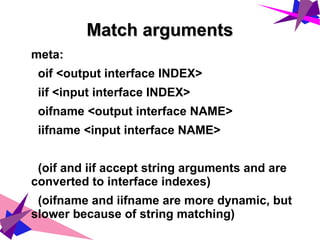
➢ Tables and chains are fully configurable
list
tables [family]
table [family] <name>
chain [family] <table> <name>
add
table [family] <name>
chain [family] <table> <name> [chain definitions]
rule [family] <table> <chain> <rule definition>
table [family] <name> (shortcut for `add table`)
Families:
ip - IPv4
ip6 - IPv6
inet - IPv4 or v6
arp - arp
bridge - linux bridge](https://image.slidesharecdn.com/nftables-170114202255/85/nftables-the-evolution-of-Linux-Firewall-10-320.jpg)


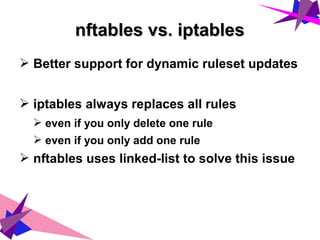





![Kernel configurationKernel configuration
[*] Networking support --->
Networking options --->
[*] Network packet filtering framework (Netfilter) --->
Core Netfilter Configuration --->
<M> Netfilter nf_tables support
<M> Netfilter nf_tables conntrack module
<M> Netfilter nf_tables counter module
<M> Netfilter nf_tables log module
<M> Netfilter nf_tables limit module
<M> Netfilter nf_tables masquerade support
<M> Netfilter nf_tables nat module
IP: Netfilter Configuration --->
<M> IPv4 nf_tables support
<M> IPv4 nf_tables route chain support
<M> IPv4 packet rejection
<M> IPv4 NAT
<M> IPv4 nf_tables nat chain support
<M> IPv4 masquerade support
<M> IPv4 masquerading support for nf_tables](https://image.slidesharecdn.com/nftables-170114202255/85/nftables-the-evolution-of-Linux-Firewall-28-320.jpg)

