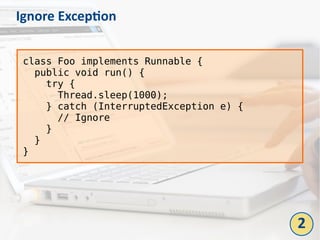
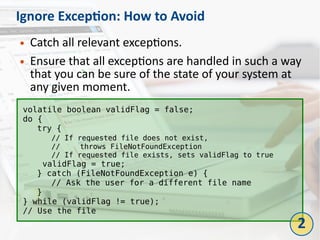
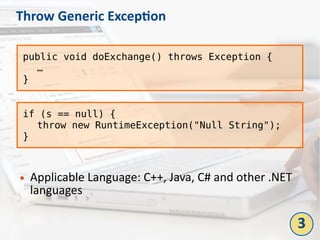
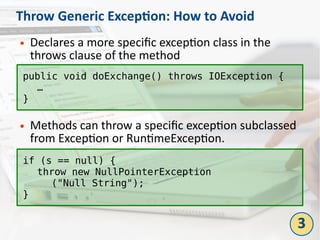
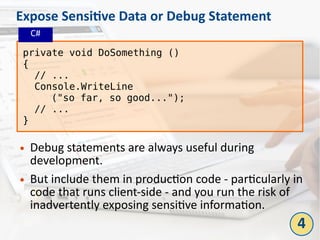
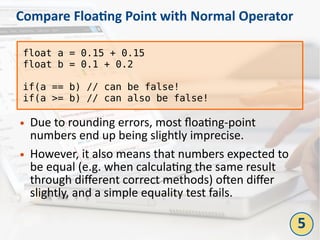
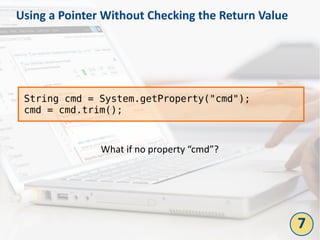
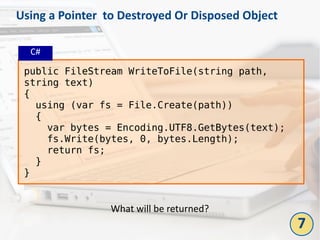
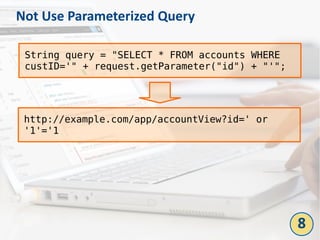
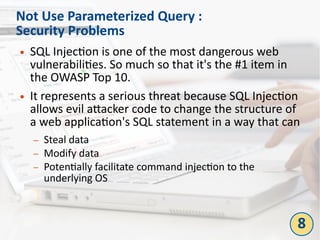
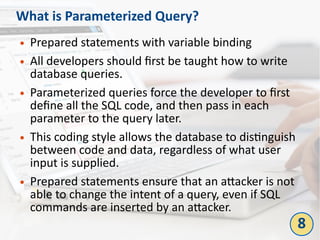
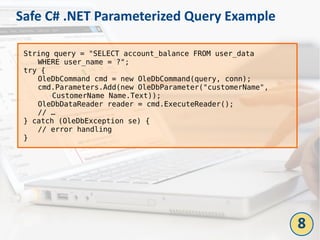
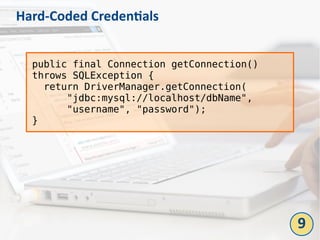
The document outlines the top 10 bad coding practices that can lead to significant security issues within applications, such as the misuse of the 'eval' function, ignoring exceptions, and hard-coded credentials. Each practice is accompanied by potential security problems, prevention strategies, and references to relevant guidelines. By adhering to these practices, developers can enhance the security and robustness of their code.