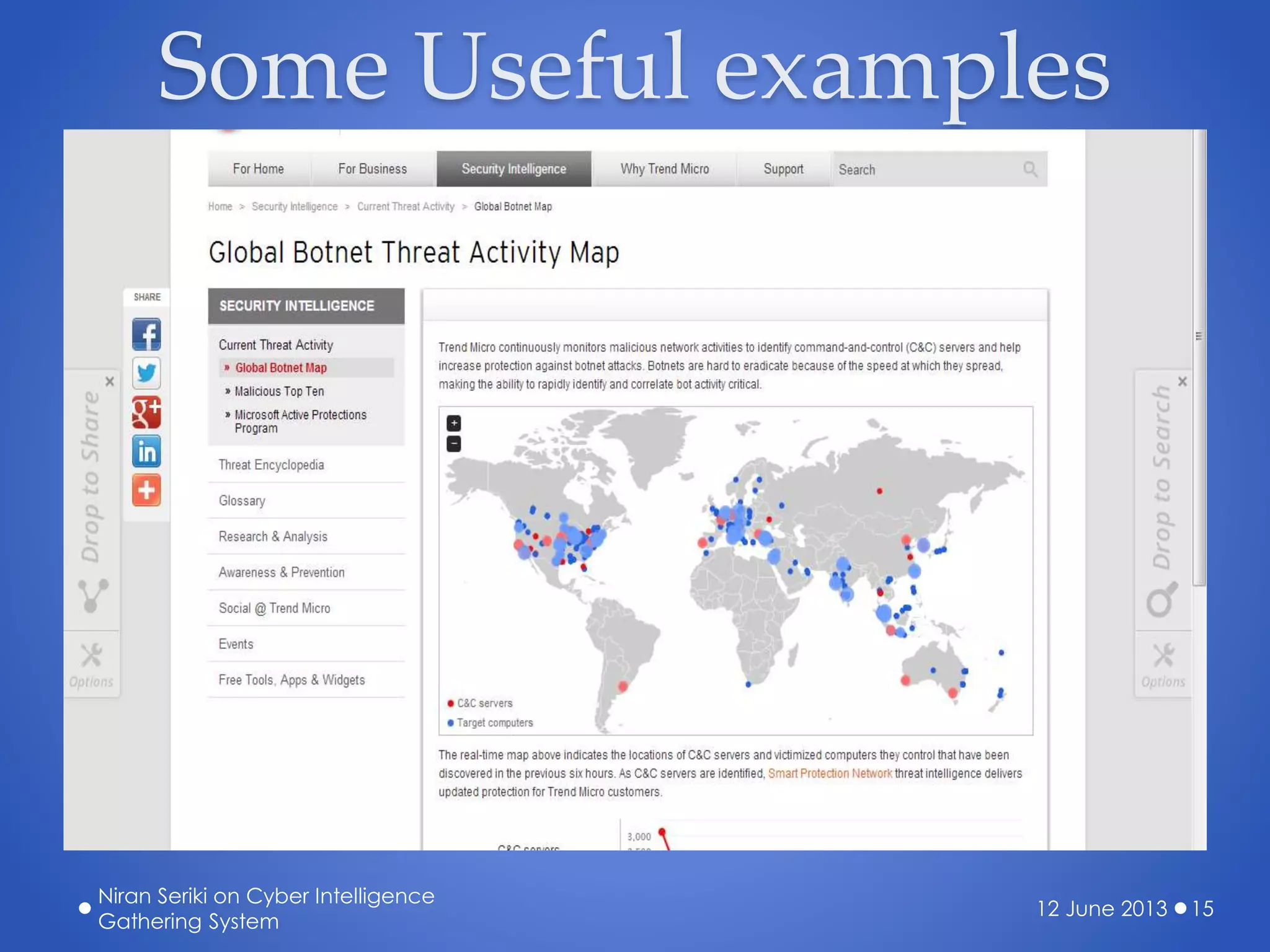
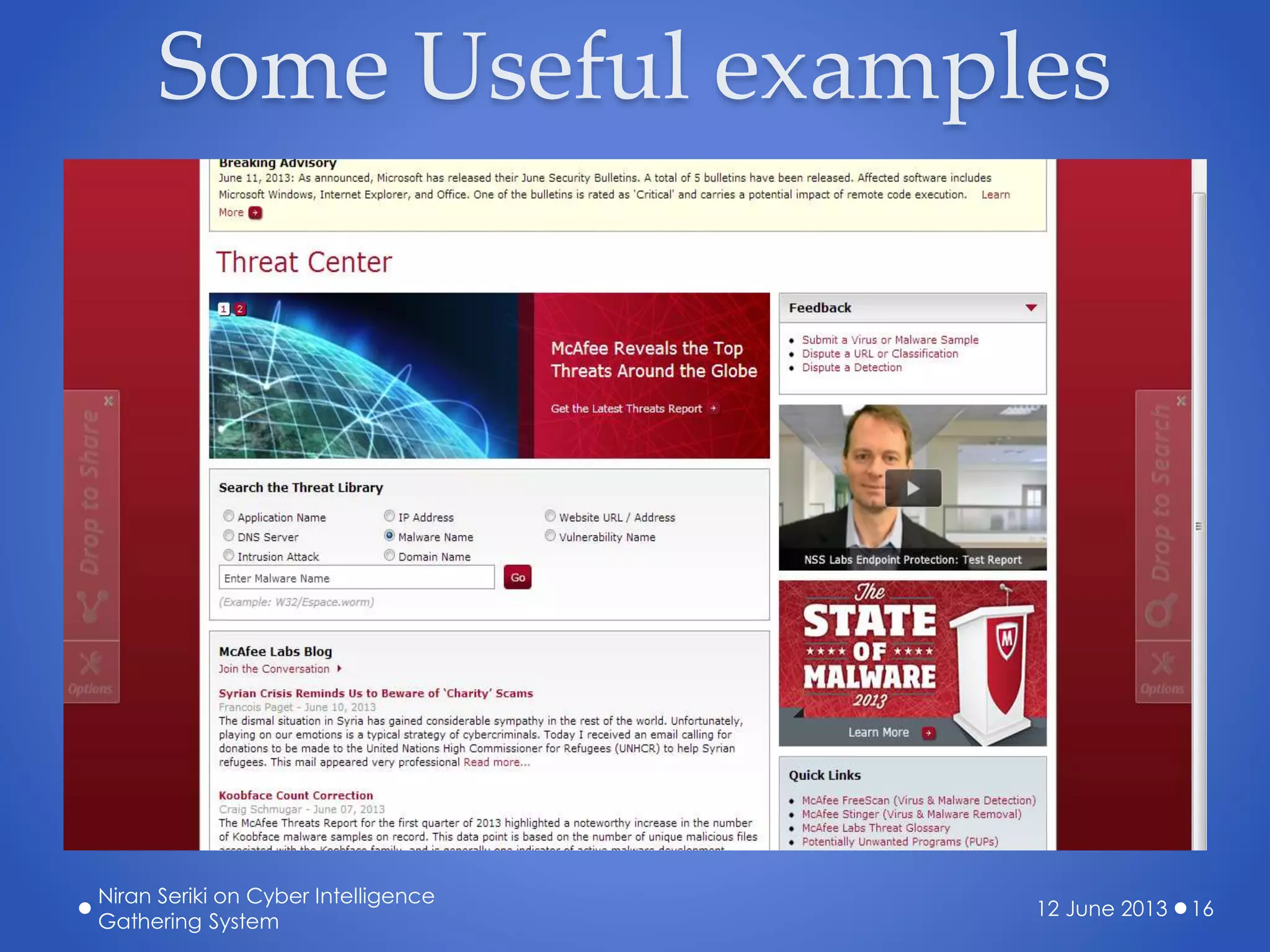
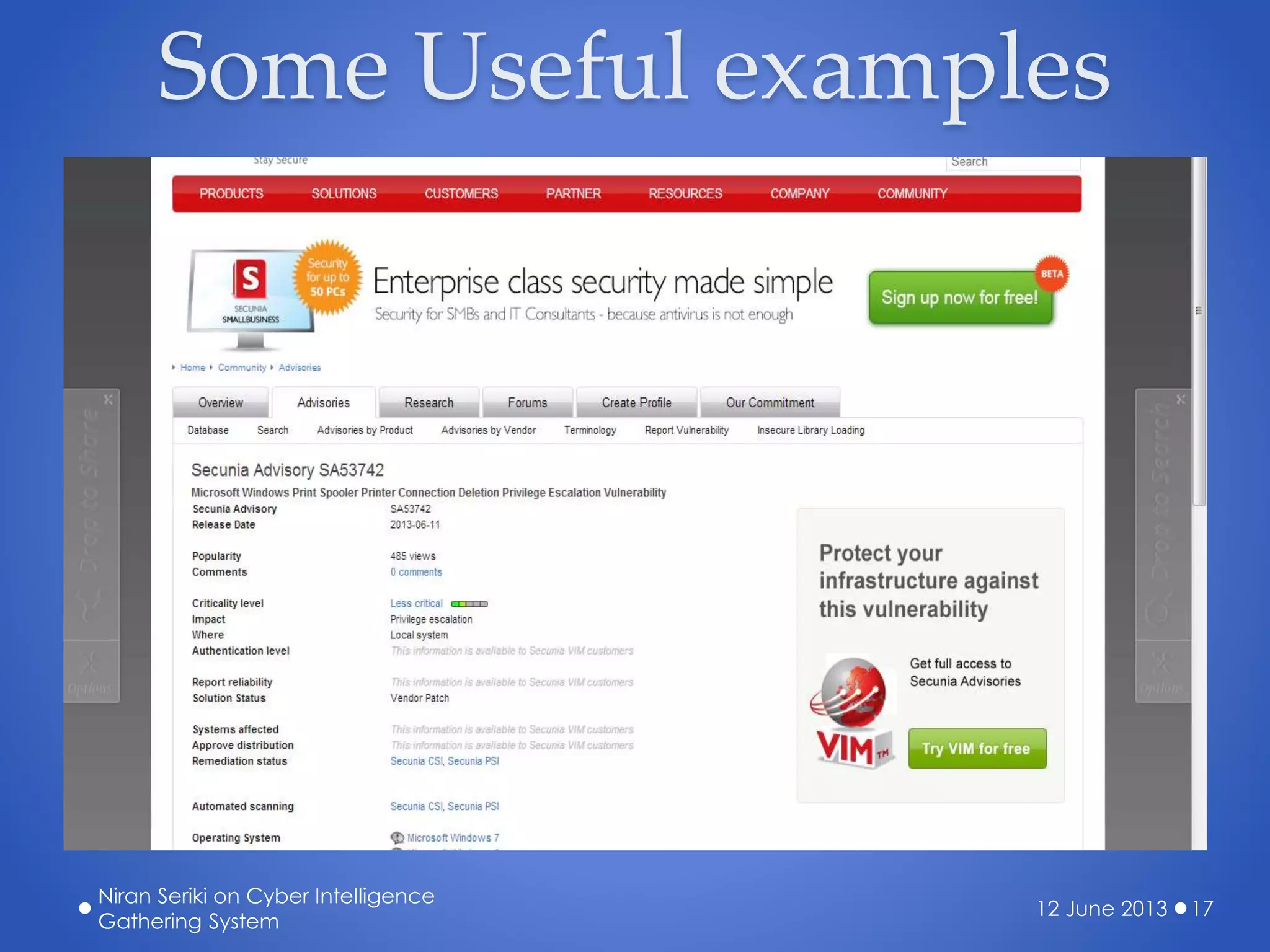
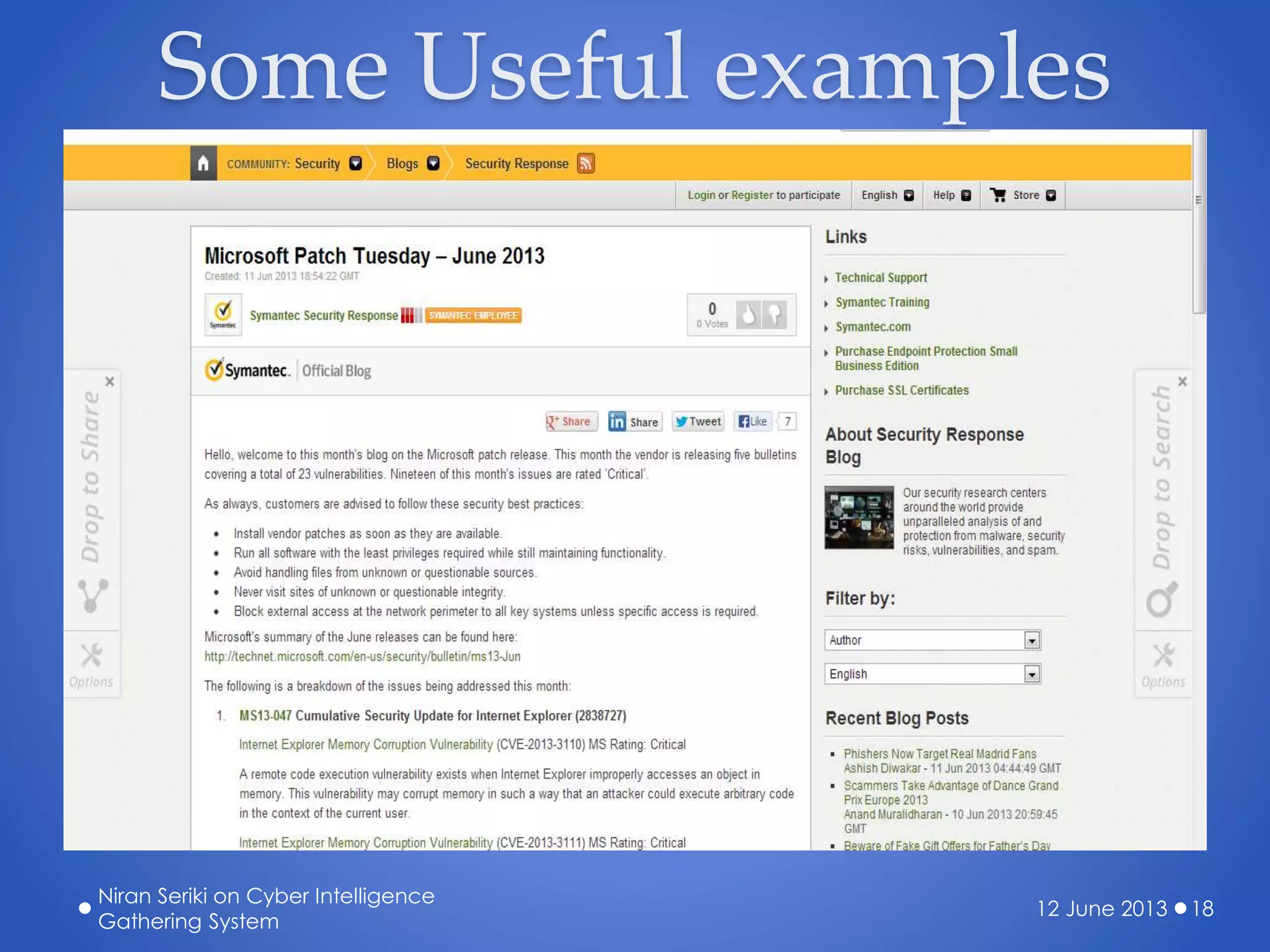
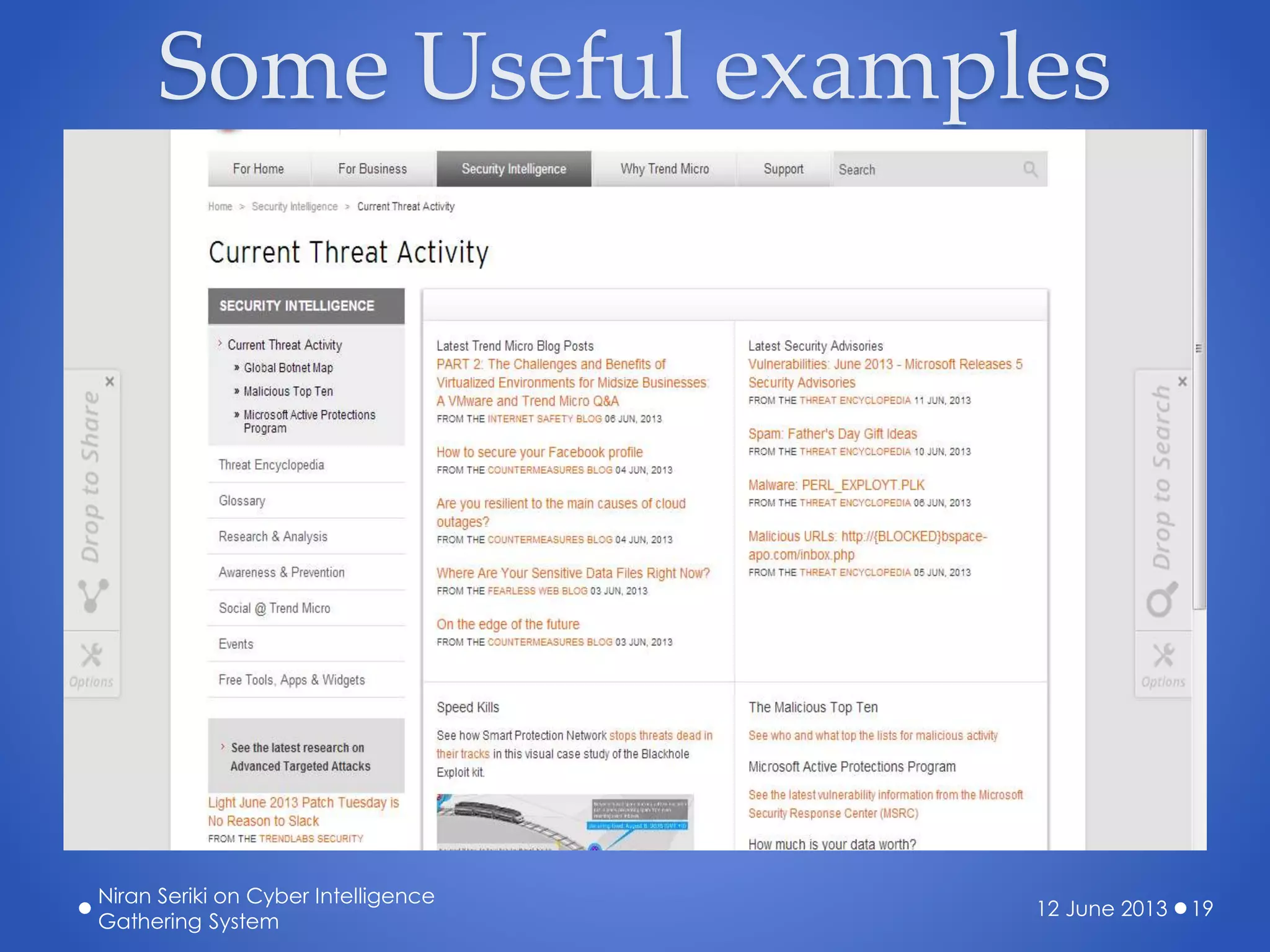
The document discusses the creation of a cyber threat intelligence gathering system leveraging open-source information, emphasizing that even individuals with limited technical knowledge can build such a system. It covers various aspects including threat monitoring, creating alerts, intelligence sorting, and sharing within organizations to enhance cybersecurity preparedness. The presentation aims to encourage proactive measures against cyber threats rather than reactive responses.