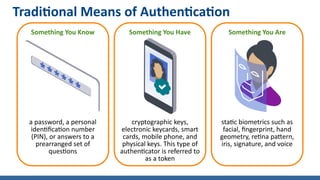
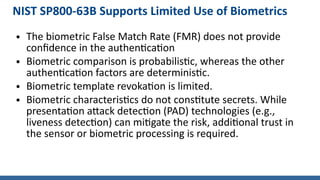
- NIST guidelines support limited use of biometrics for authentication and recommend it only be used as part of multi-factor authentication along with a physical authenticator. Biometrics have limitations including probabilistic matching and inability to easily revoke templates.
- When biometrics are used, NIST requires a false match rate of 1 in 1000 or better, implementation of liveness detection, and preference for local rather than central matching to mitigate attacks.
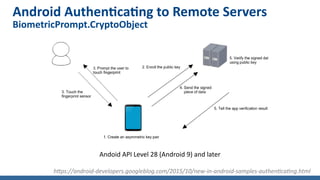
- For AAL2 authentication on mobile, NIST recommends using multi-factor cryptographic software authenticators activated by a second factor like biometrics. Examples include FIDO protocols and Android's CryptoObject for authenticating to remote servers.
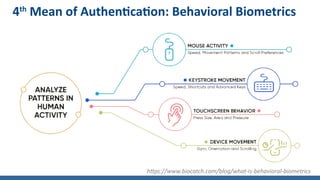
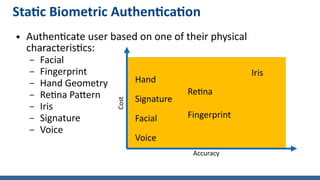
- Behavioral biometrics analyzing user







![NIST SP800-63B Biometric Requirement & Guideline
● Used only as part of multi-factor authentication with a
physical authenticator (something you have).
● Operate with an FMR (False Match Rate) [ISO/IEC 2382-37] of
1 in 1000 or better.
● Implement presentation attack detection (PAD) as defined in
[ISO/IEC 30107-1].
● Biometric comparison can be performed locally on claimant’s
device or at a central verifier. Since the potential for attacks
on a larger scale is greater at central verifiers, local
comparison is preferred.](https://image.slidesharecdn.com/biometricauthentication-230615110351-071e45b2/85/Biometric-Authentication-pdf-14-320.jpg)