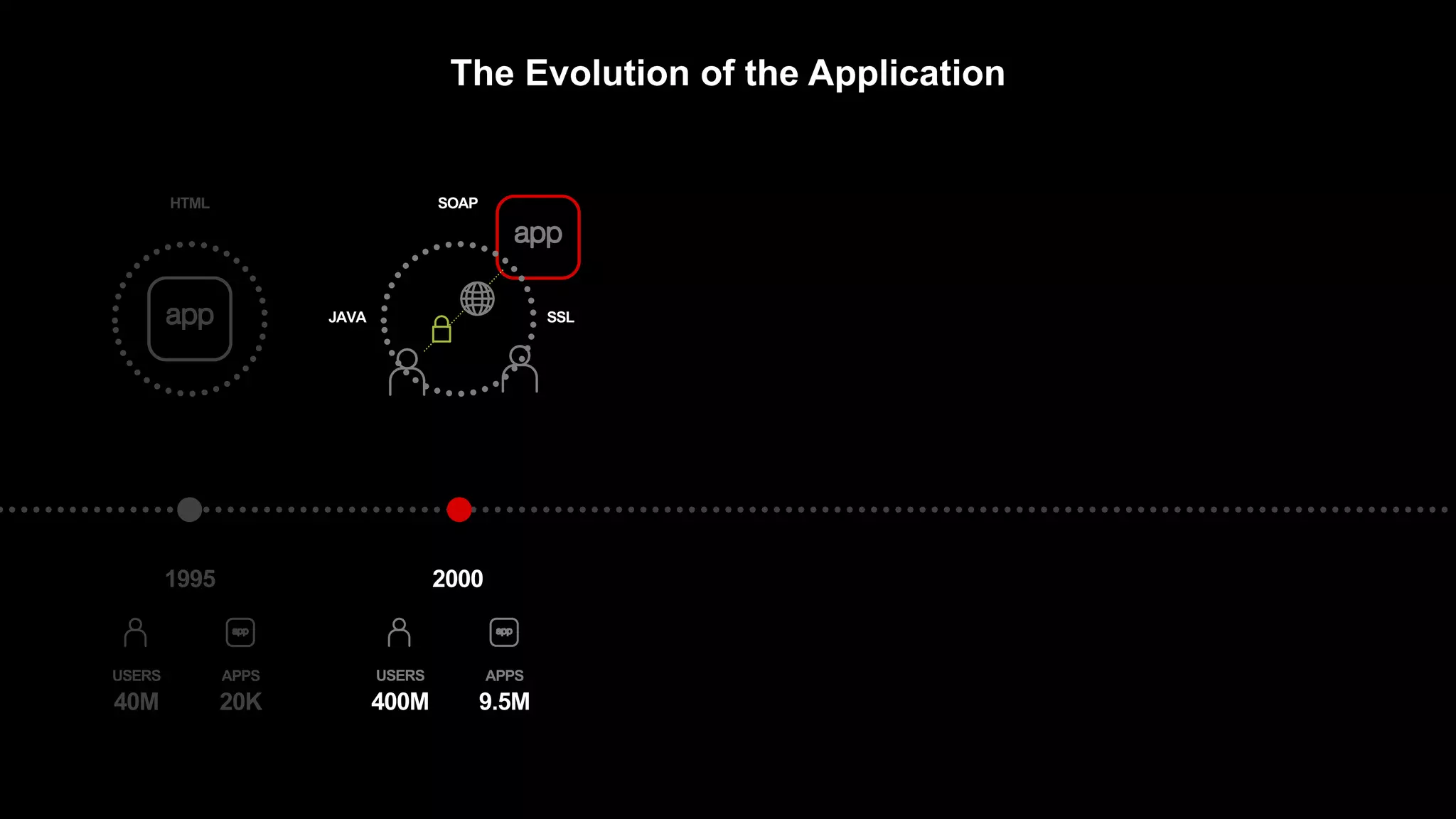
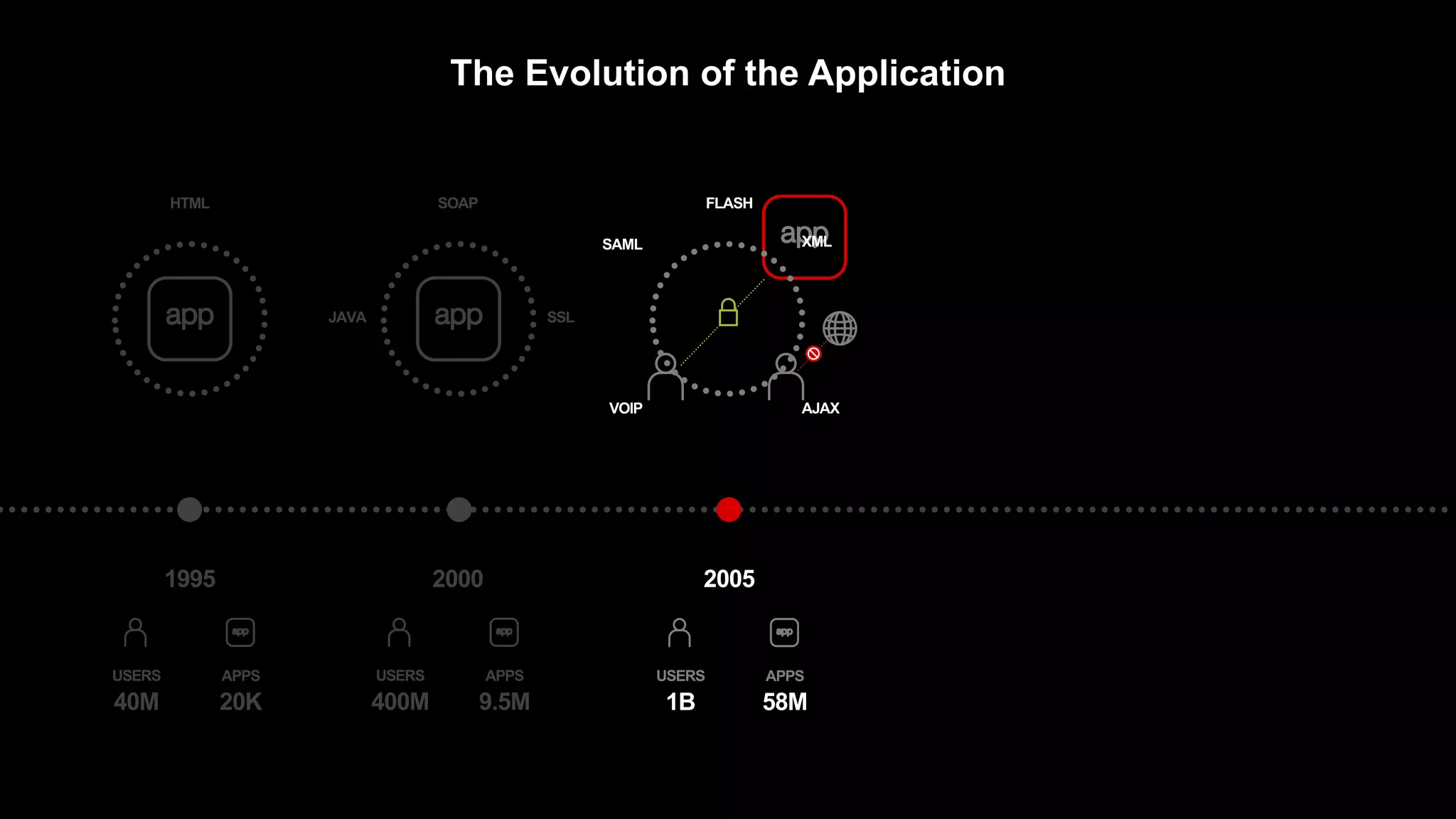
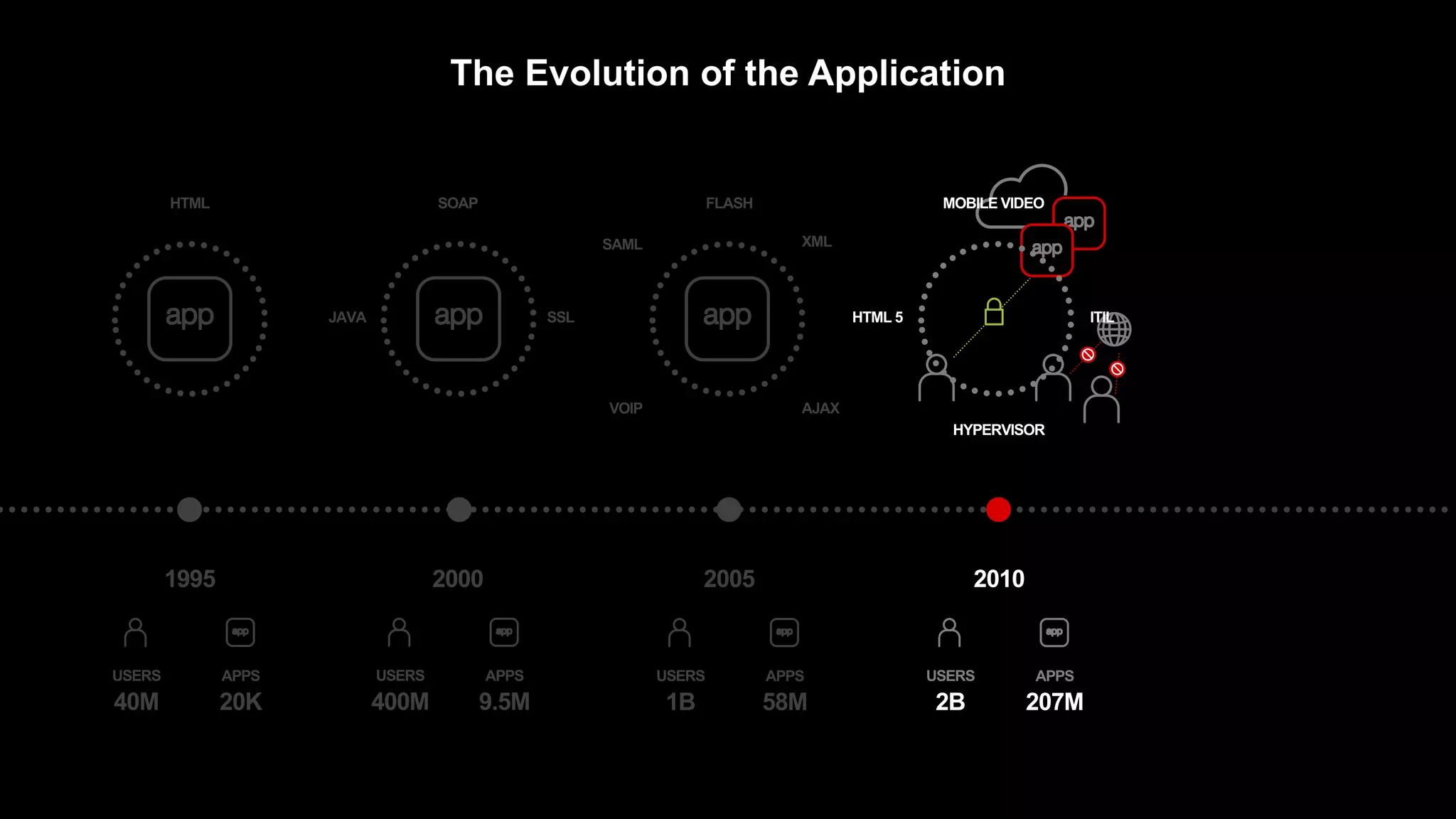
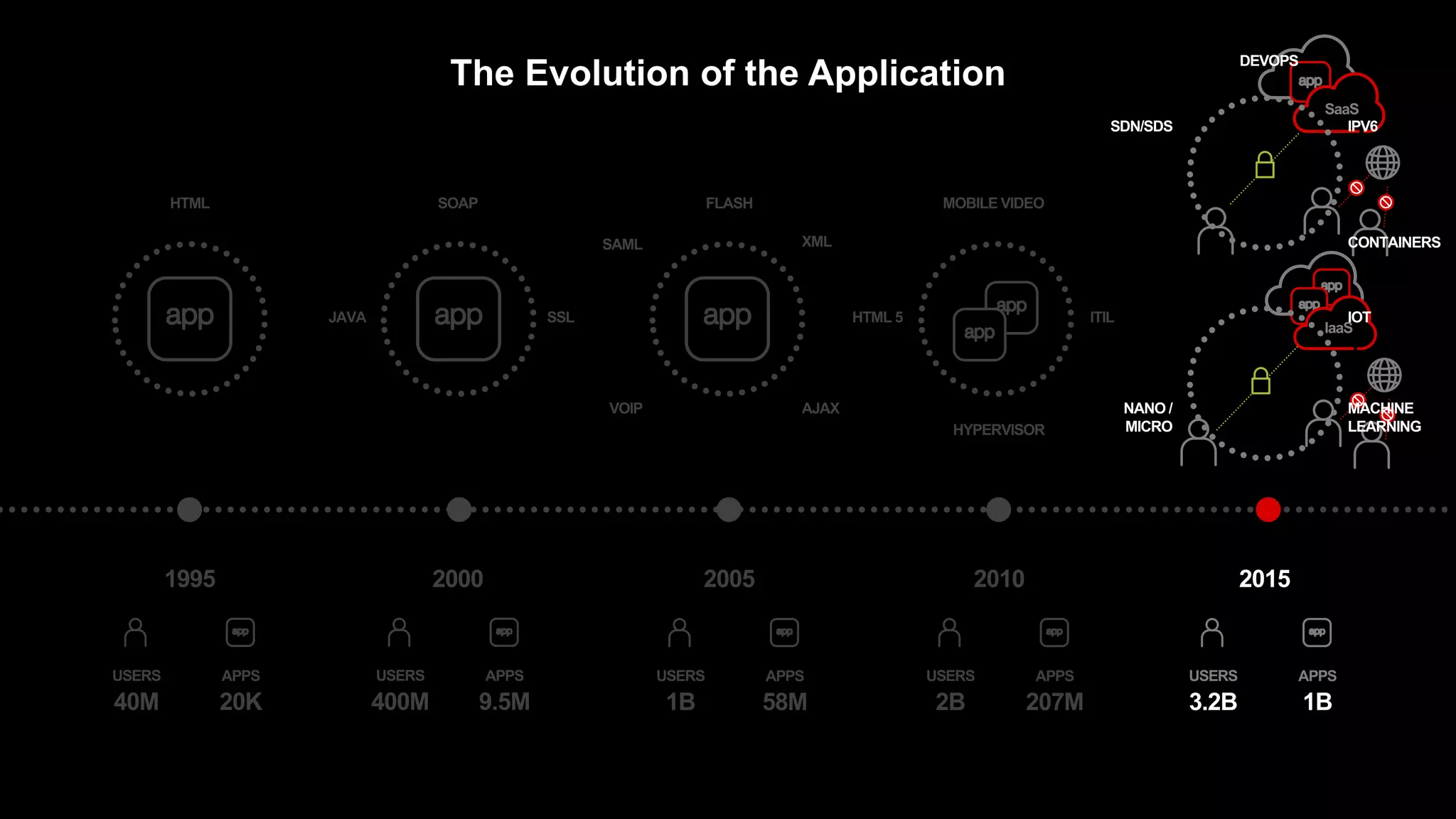
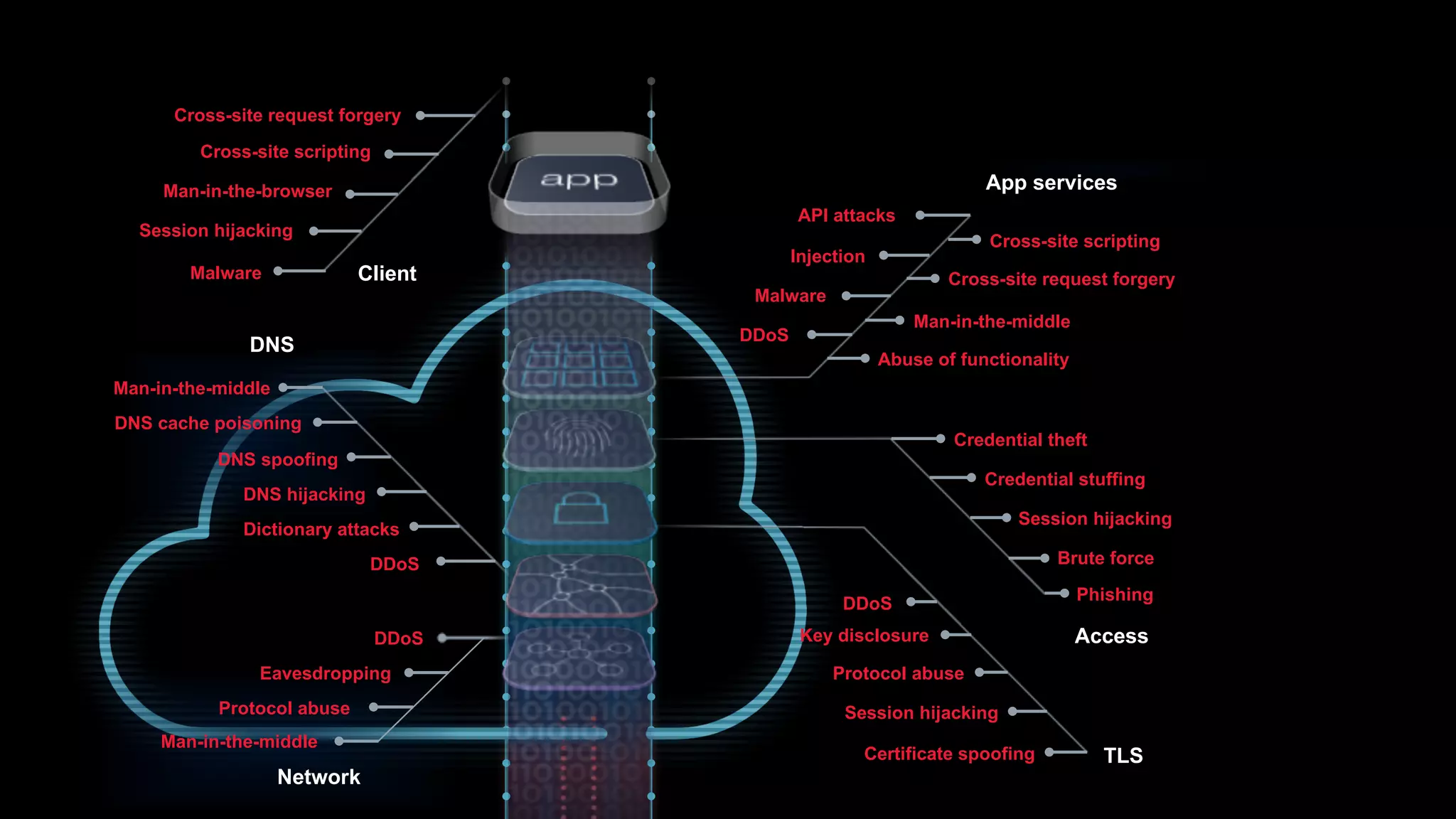
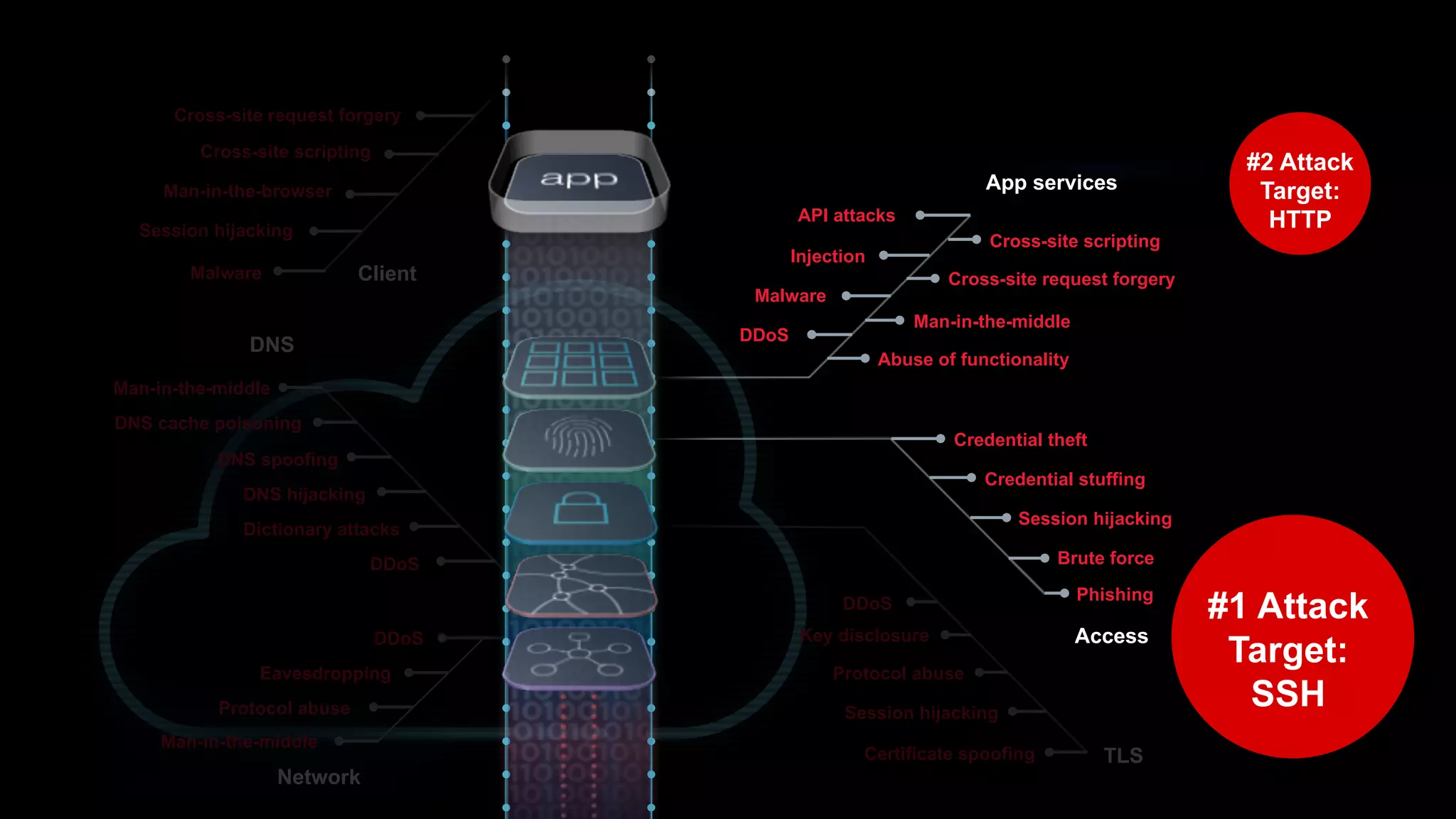
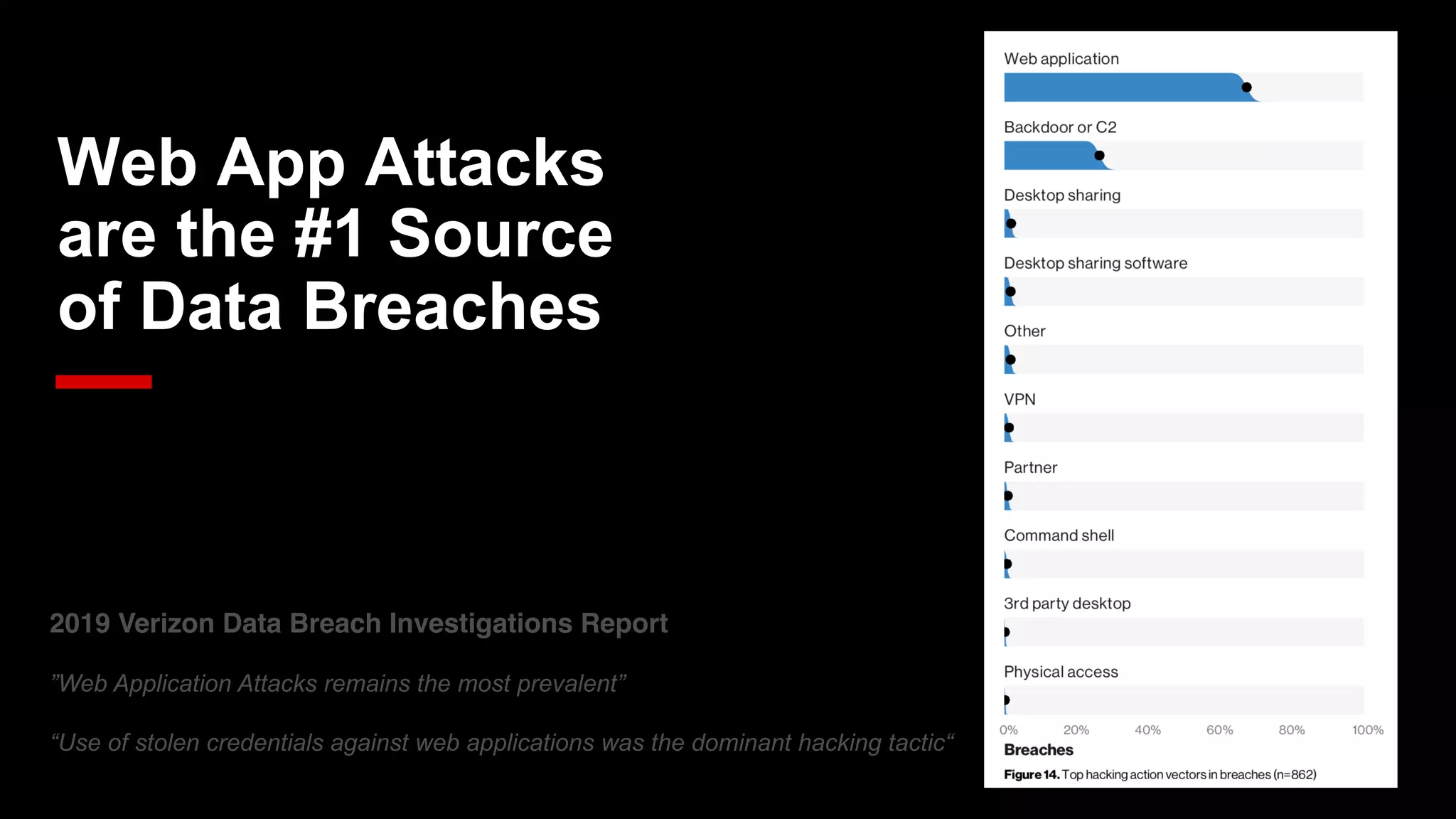
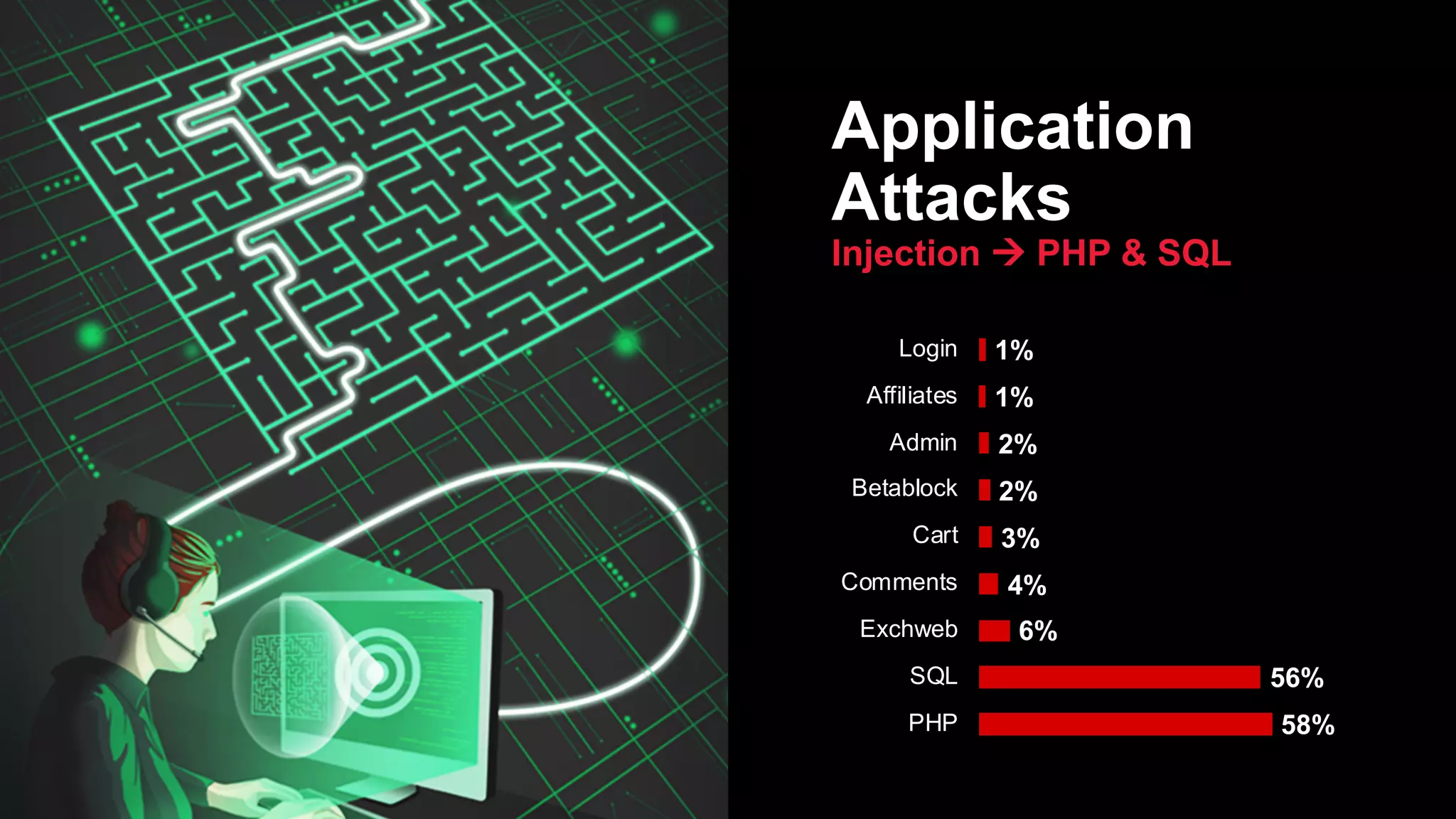
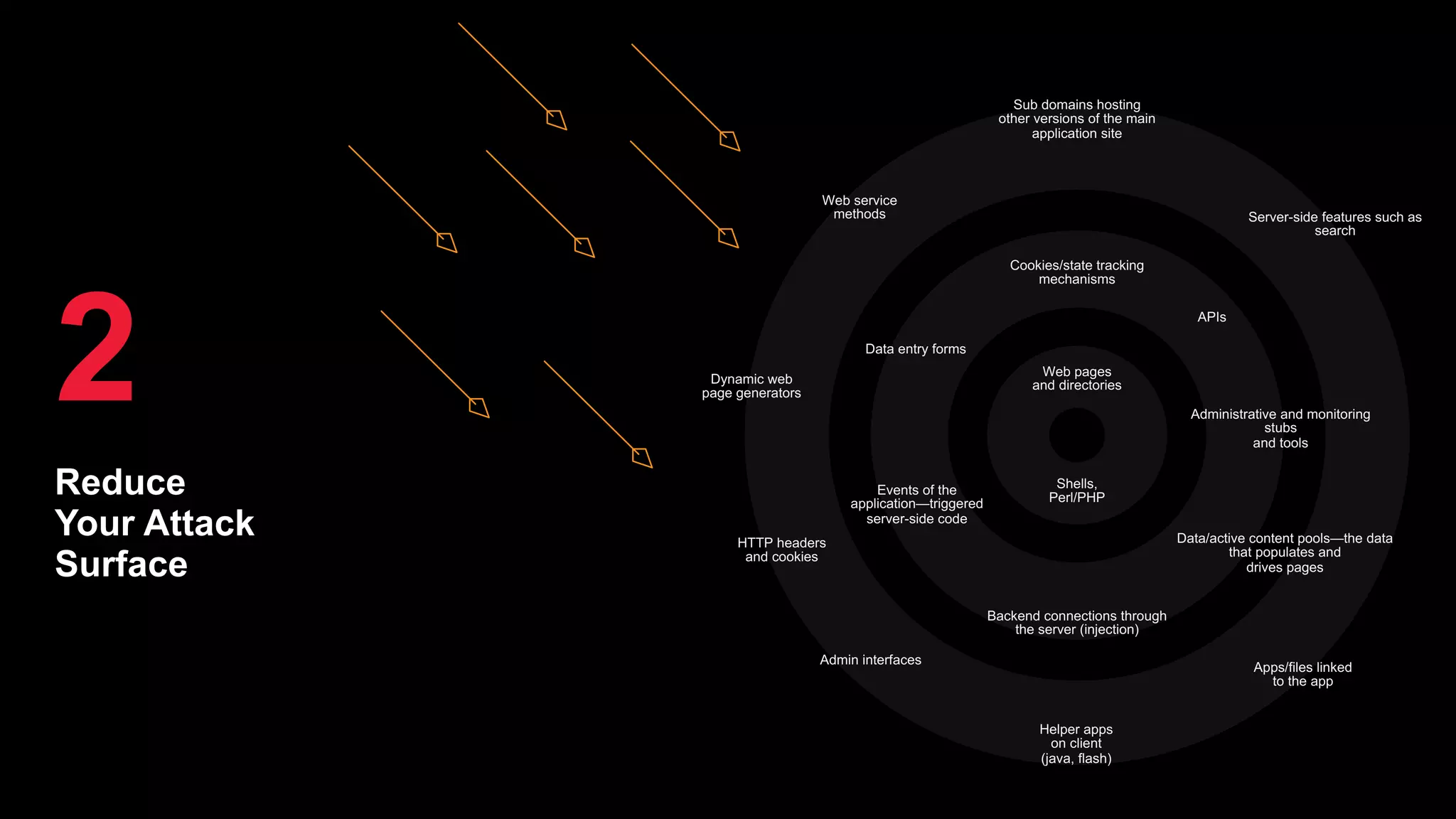
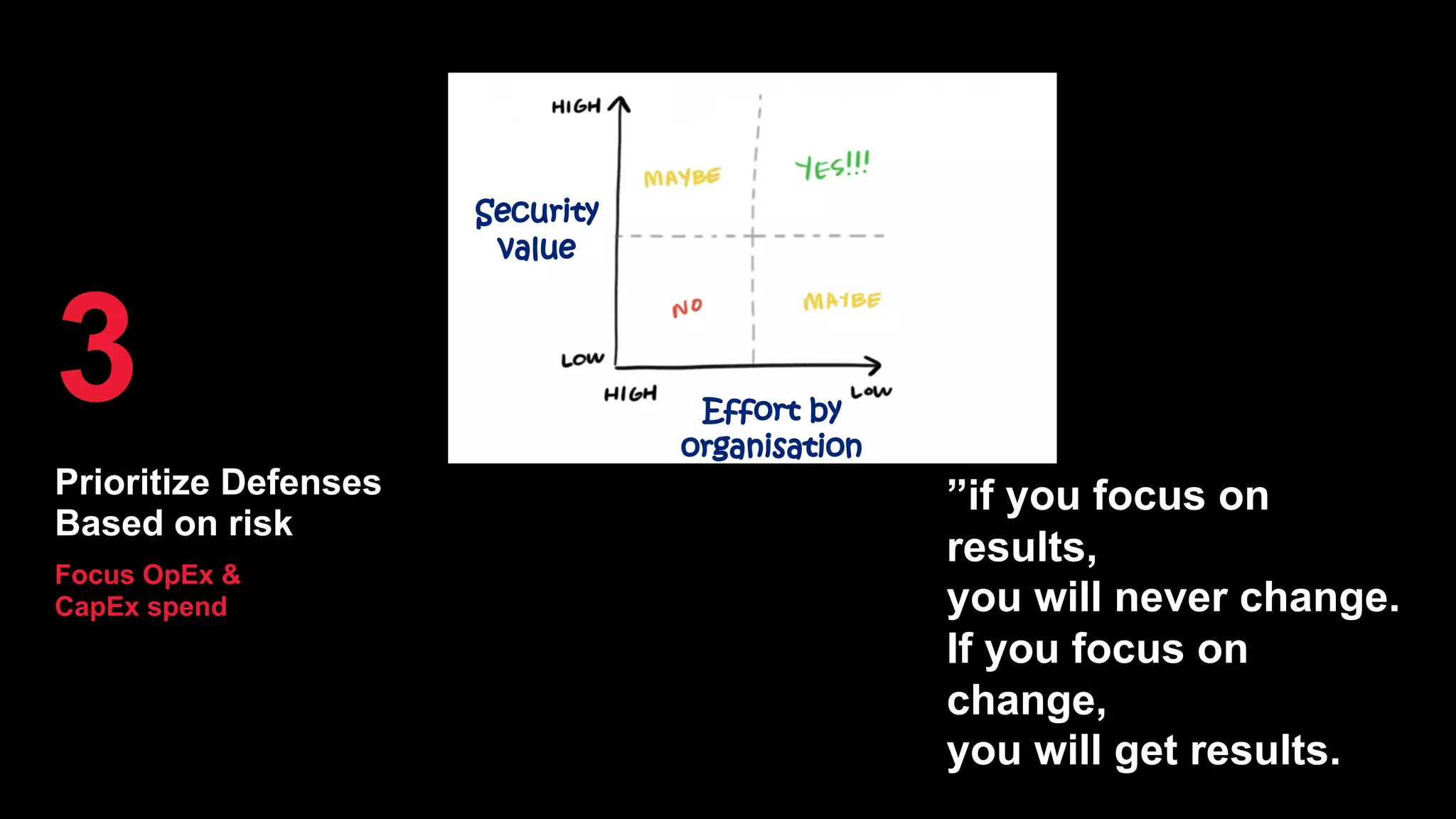
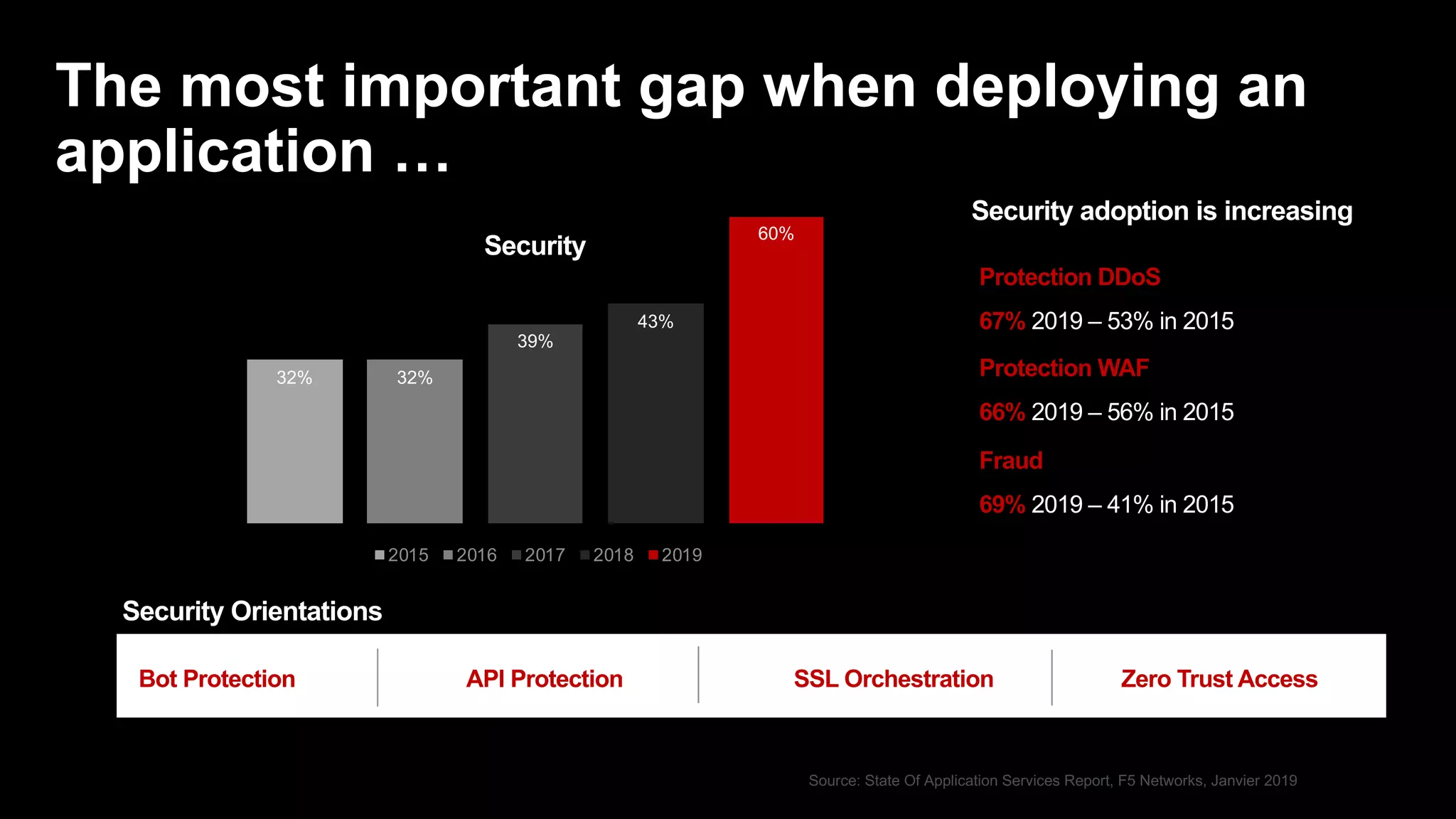
The document discusses the increasing threats to application security, highlighting that 86% of cyber threats target applications and application identities. It emphasizes the need for enhanced visibility and orchestration in managing application portfolios, while also addressing various types of attacks such as DDoS, credential theft, and injection attacks. The report advocates for a proactive approach to security, ensuring applications are protected against a diverse range of vulnerabilities.