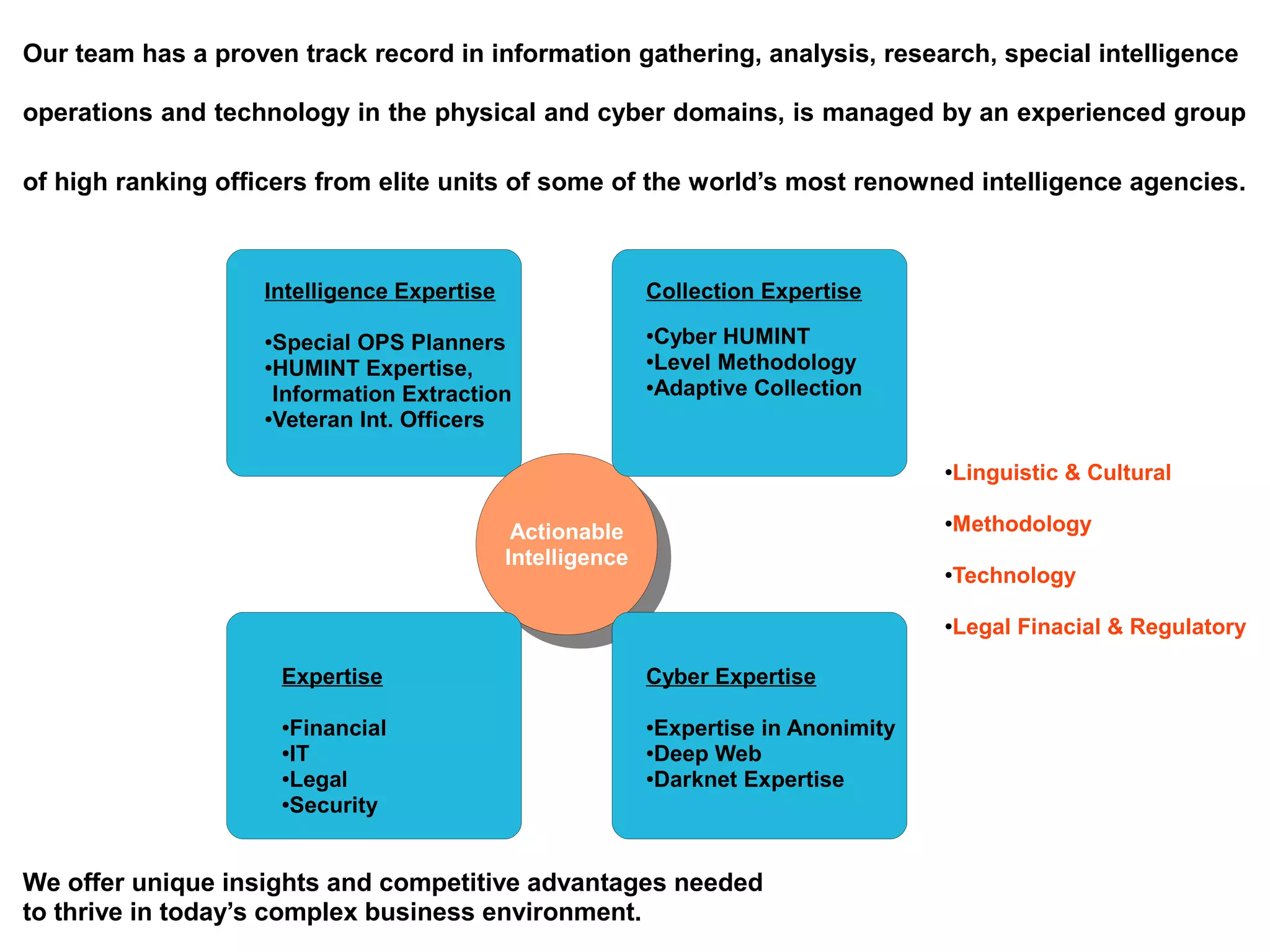
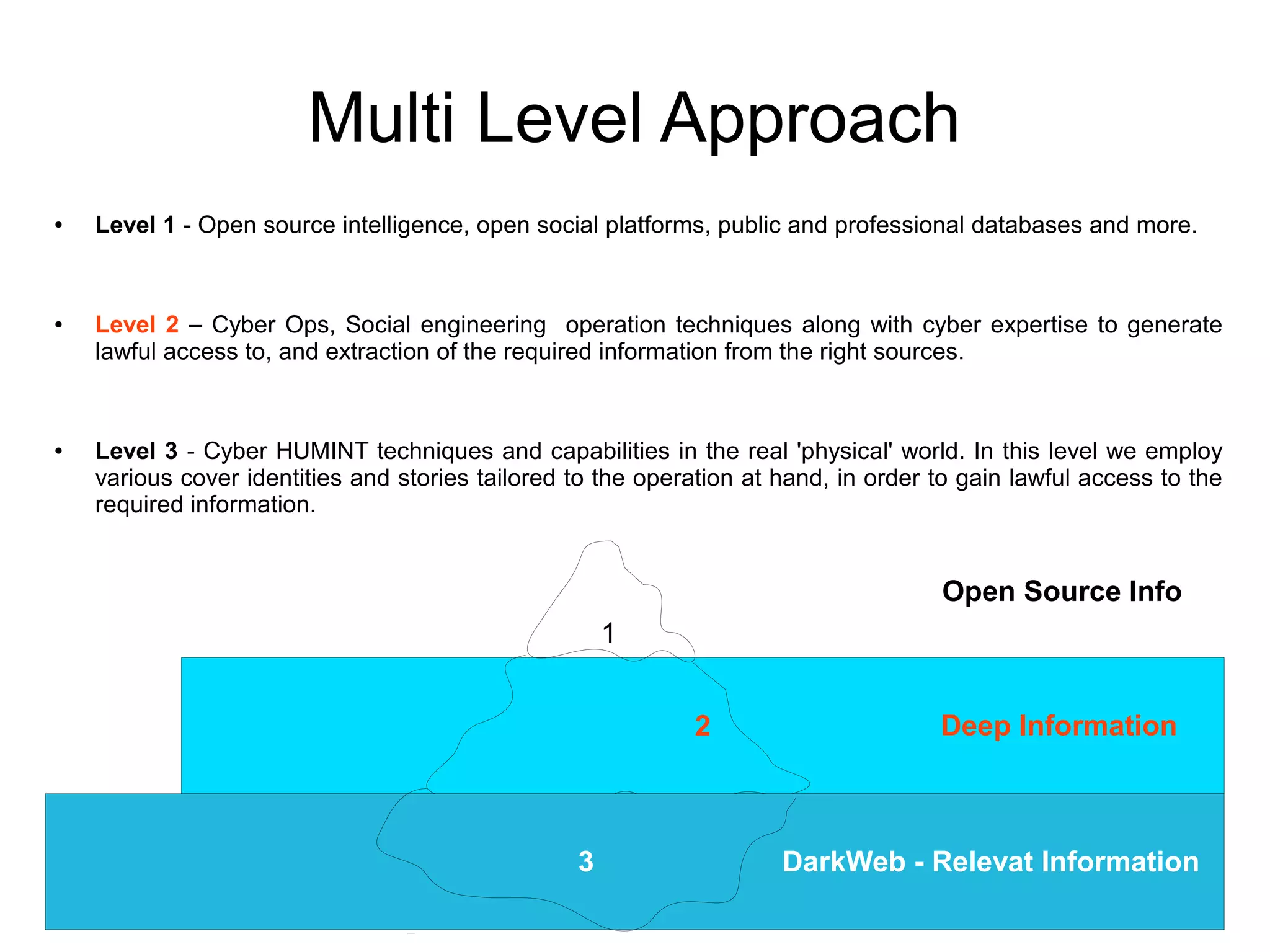
The document outlines the services provided by a cyber intelligence and security firm, including cyber threat intelligence, vulnerability assessments, and actionable intelligence collection strategies. The team comprises experienced officers from elite intelligence agencies, offering insights to help clients mitigate risks related to competition, fraud, and cyber threats. Their capabilities cover various levels of intelligence gathering and analysis, emphasizing a comprehensive approach to enhancing cybersecurity for diverse clients.