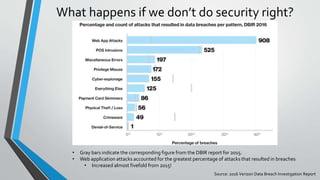
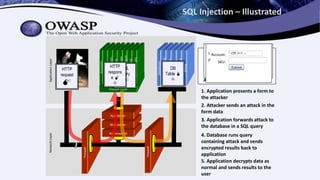
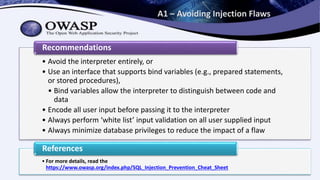
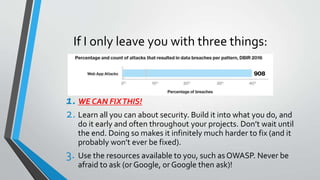
The document presents an overview of web security by Noah G. Jaehnert, emphasizing the importance of security in protecting valuable assets, particularly in a healthcare setting. Key topics include the definition of security and information security, the challenges of implementing security measures, and steps developers can take to enhance security through resources like OWASP. The document concludes with actionable advice on integrating security throughout the development process and offers various resource links for further information.