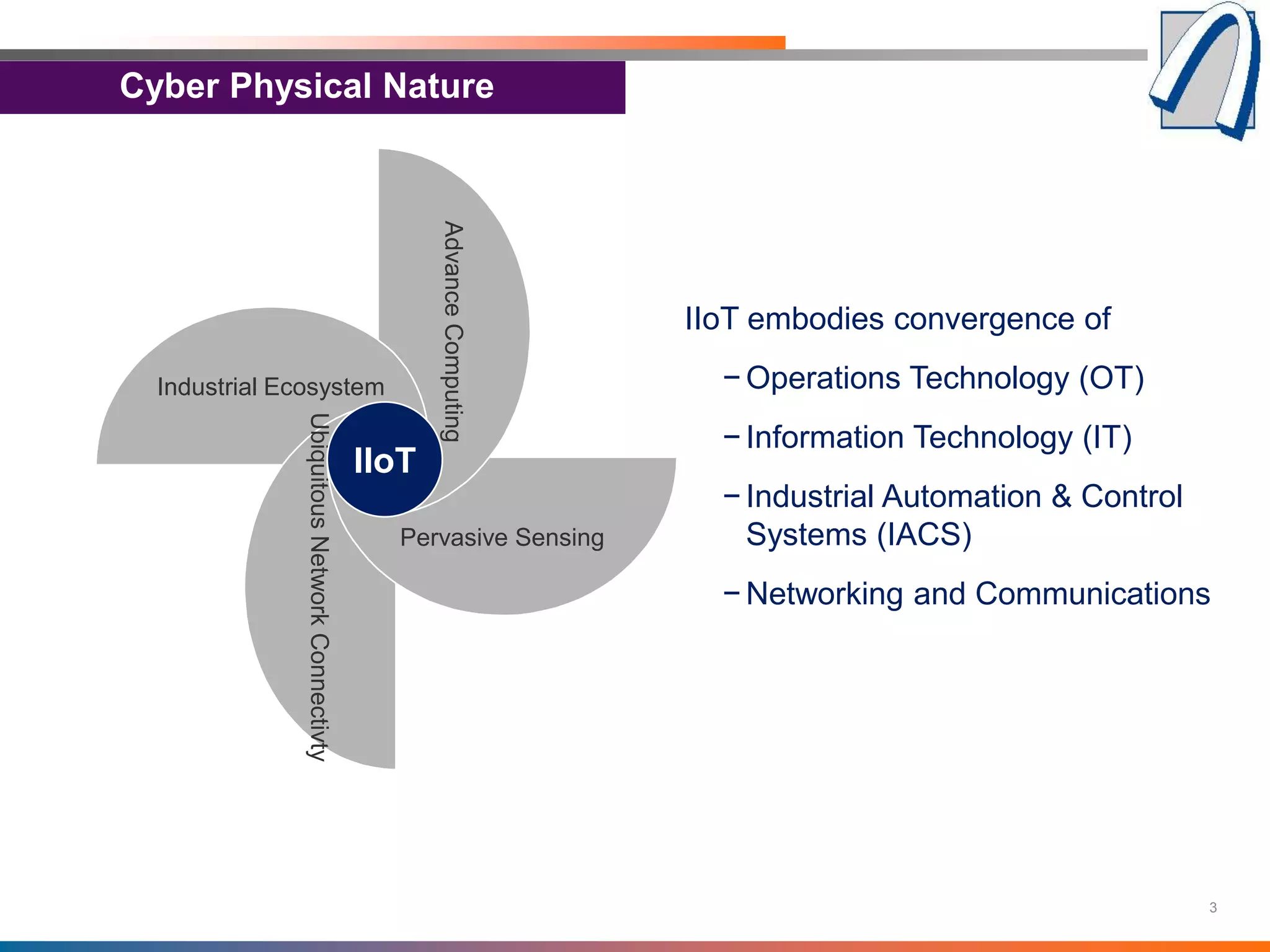
The document discusses the importance of security standards and frameworks for the Industrial Internet of Things (IIoT), highlighting the integration of operations technology, information technology, and industrial automation. It emphasizes the need for comprehensive security measures, including the CIA triad and additional requirements for reliability and safety, to protect against risks in a connected industrial environment. Various standards like ISA/IEC 62443 and the Industrial Internet Security Framework (IISF) are referenced as vital resources for establishing effective security practices in IIoT systems.