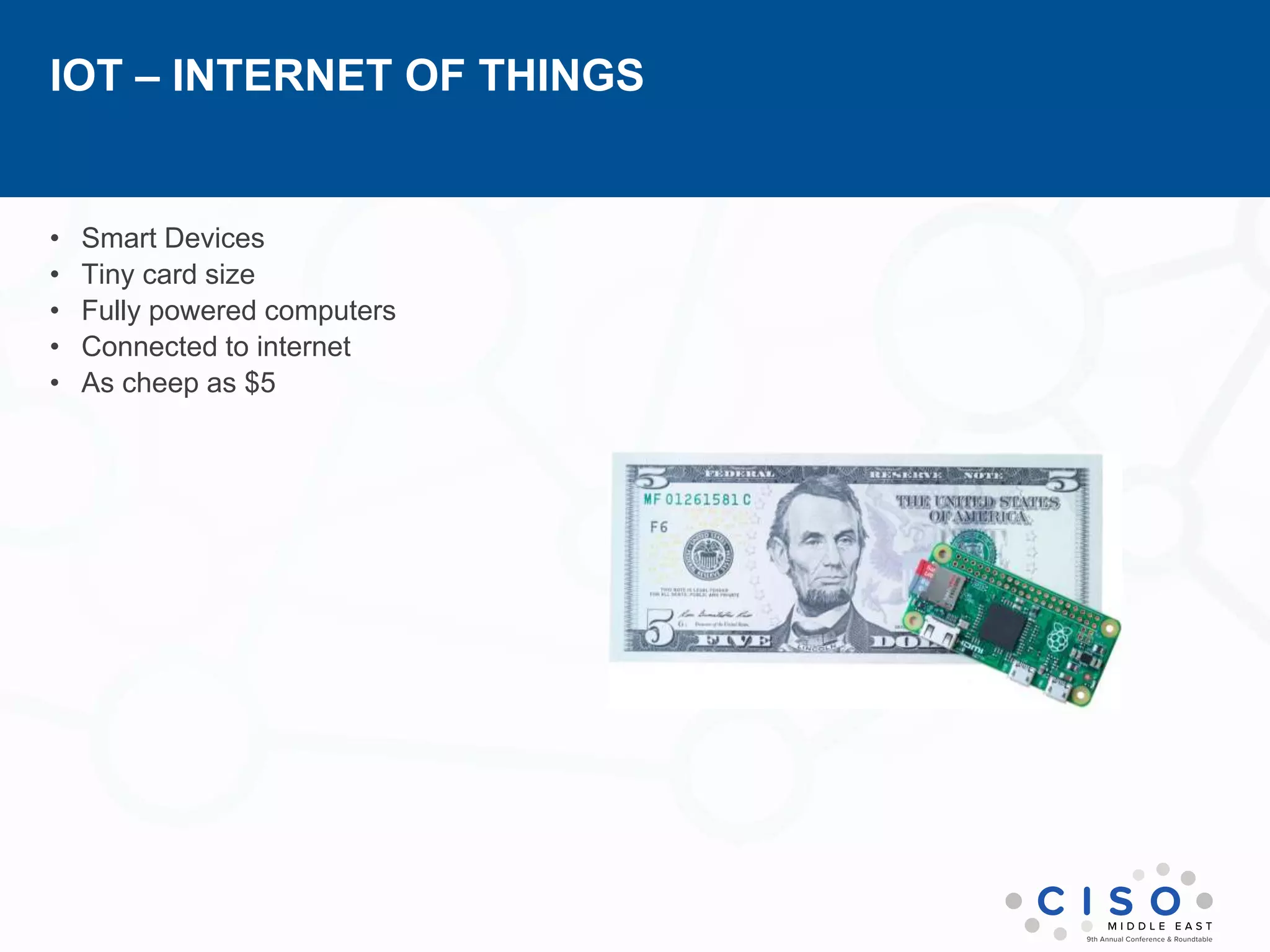
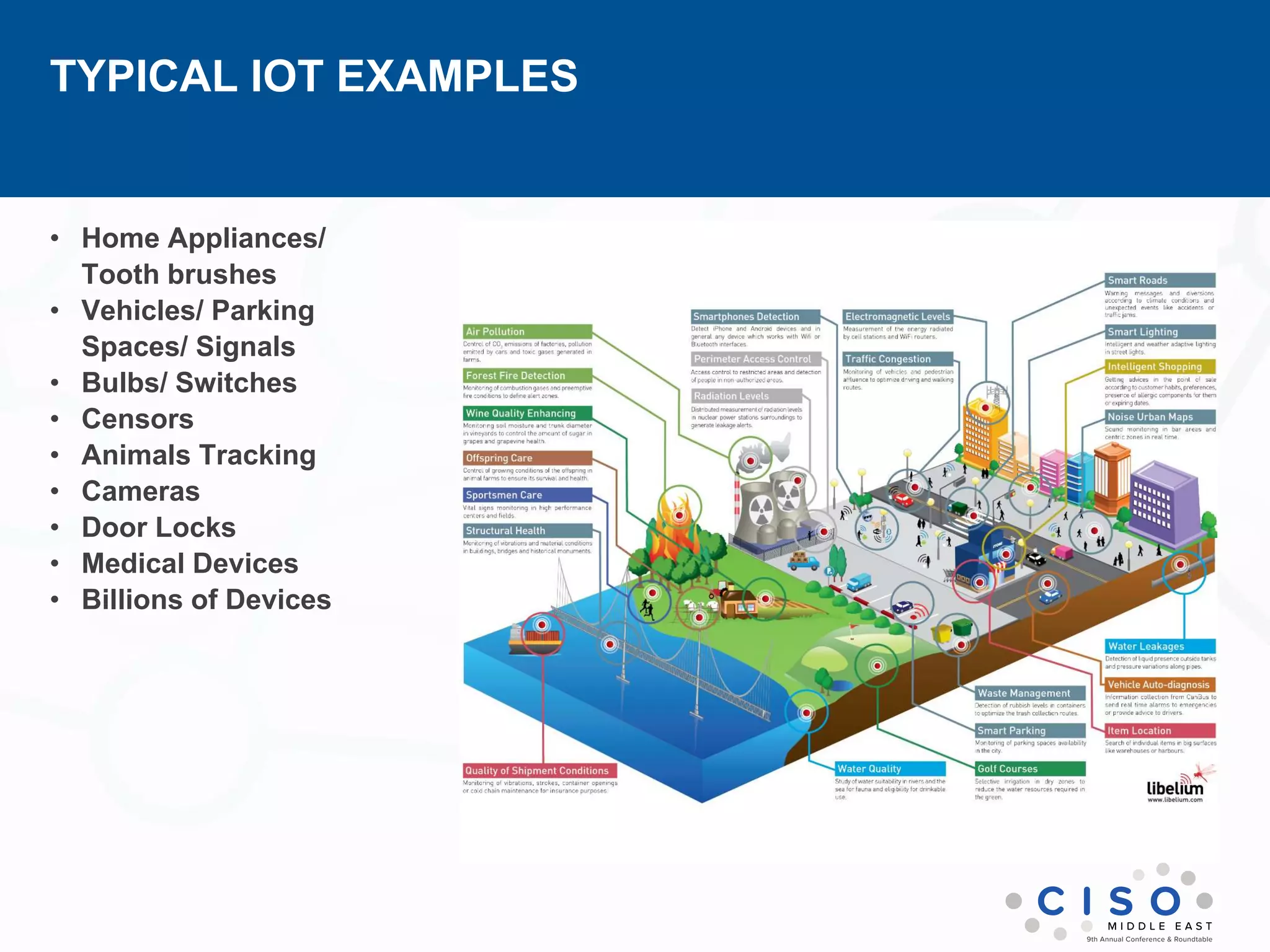
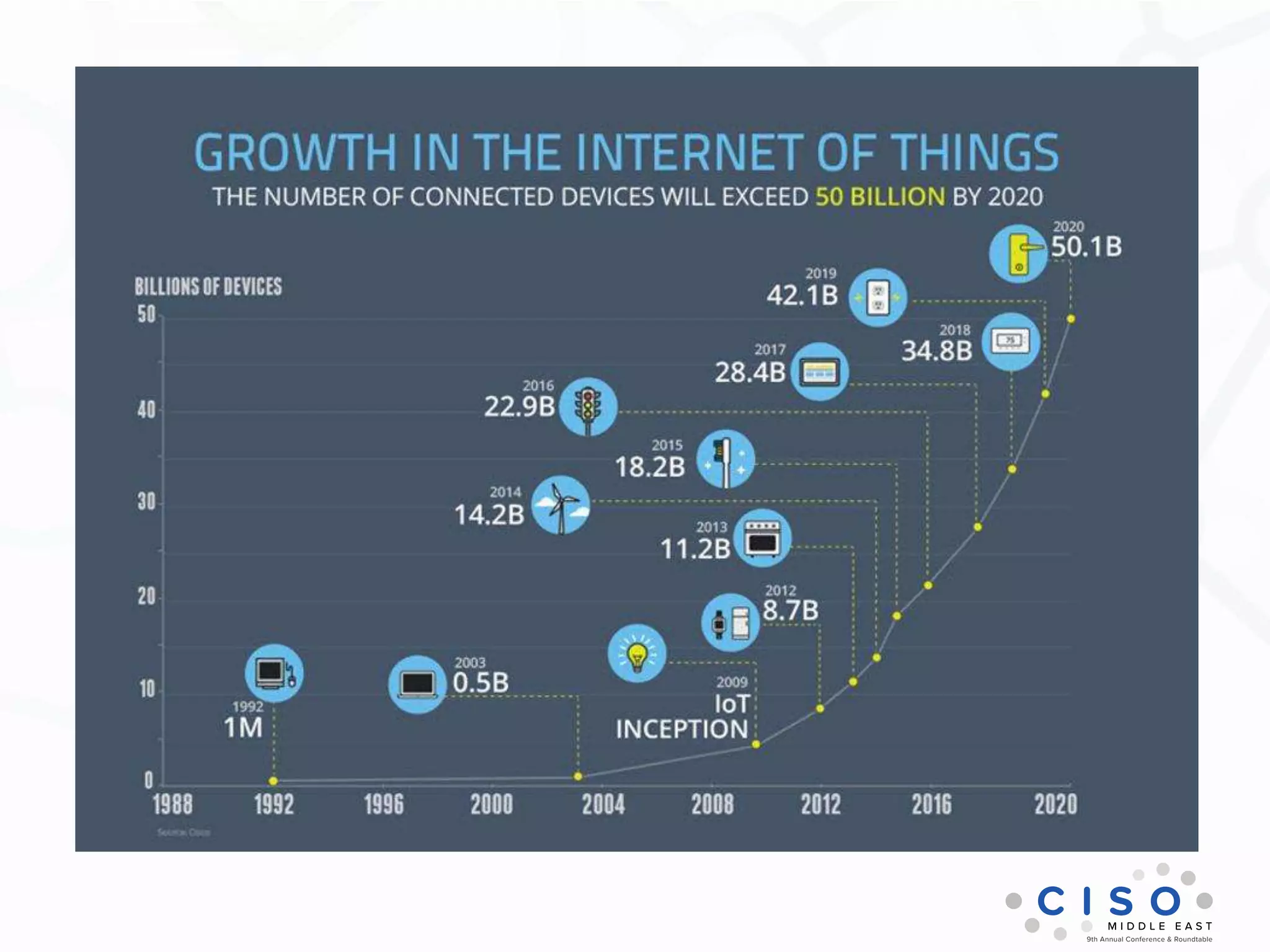
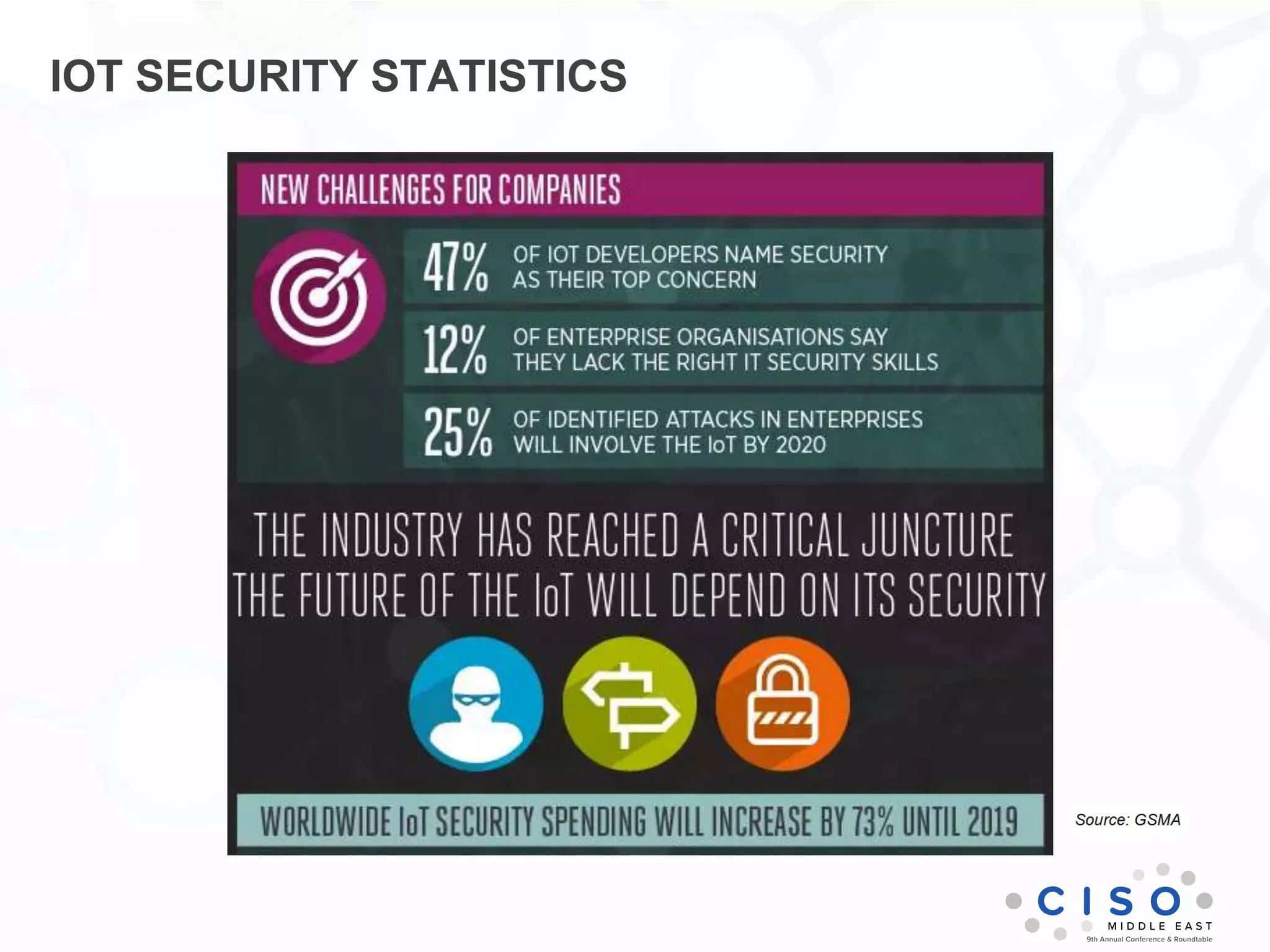
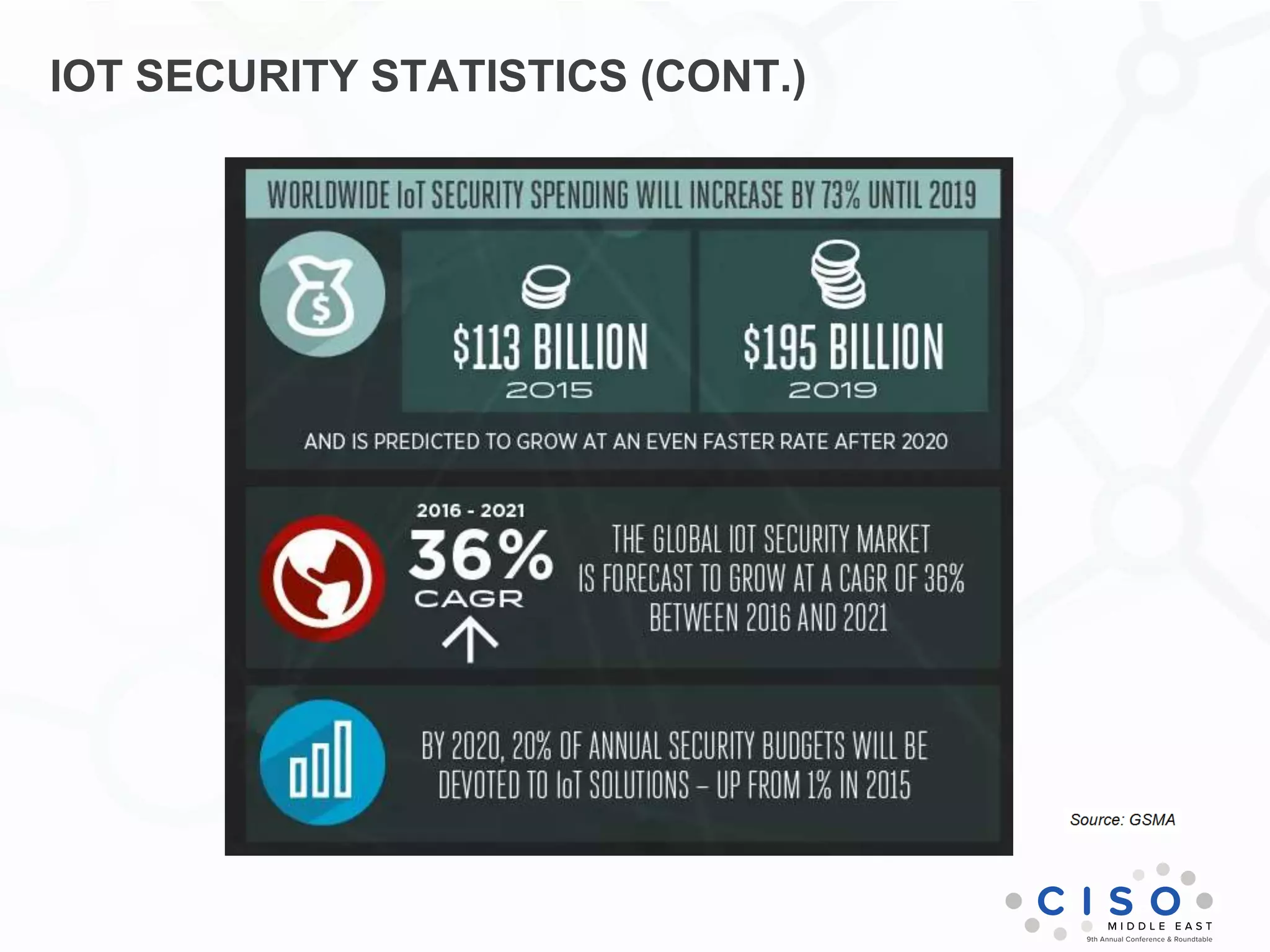
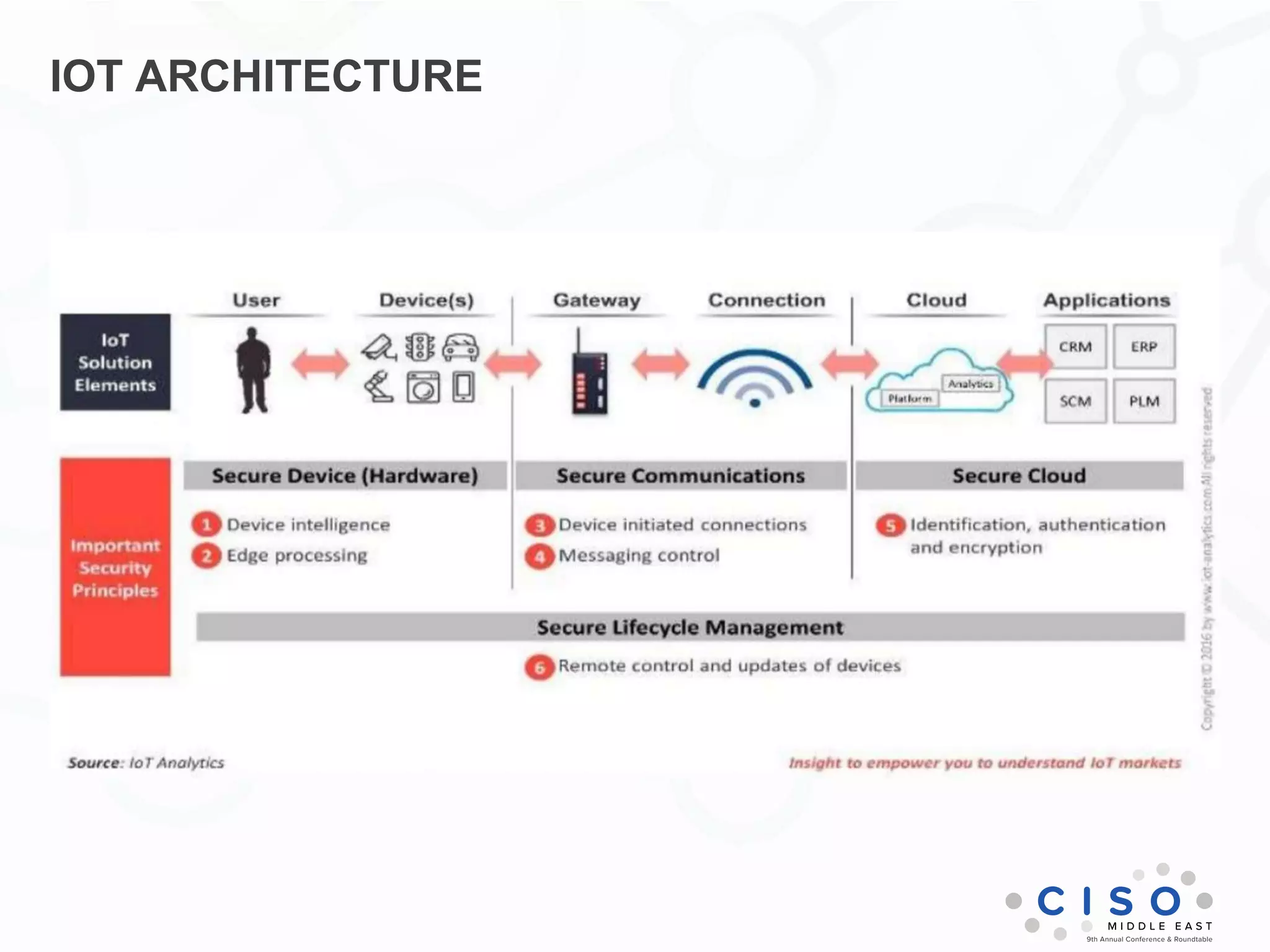
The document by Muhammad Faisal Naqvi discusses the Internet of Things (IoT) and the associated security vulnerabilities, highlighting the rise of IoT attacks such as ransomware and DDoS attacks. It outlines the primary security challenges, including poor authentication and insecure interfaces, and suggests strategies for mitigating risks like network segregation and automatic updates. The author underscores the urgent need for better standards and practices in IoT security as the number of connected devices continues to grow.