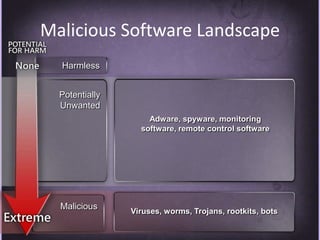
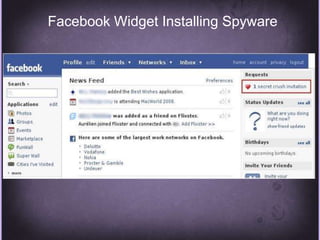
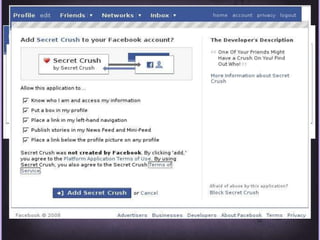
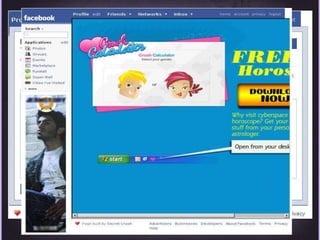
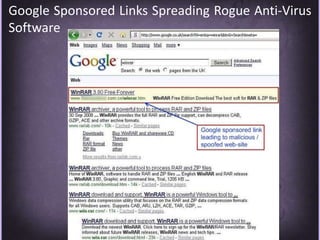
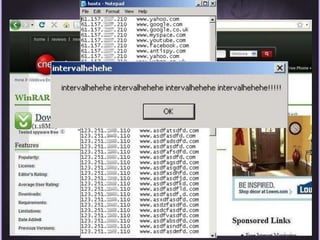
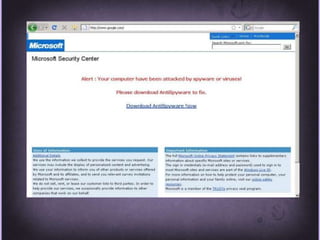
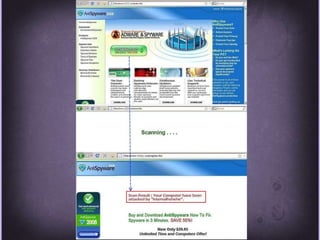
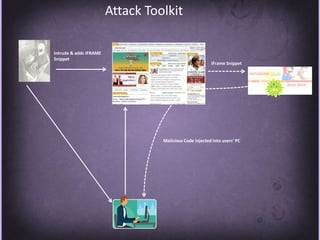
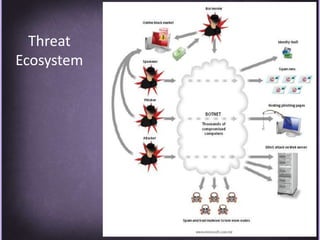
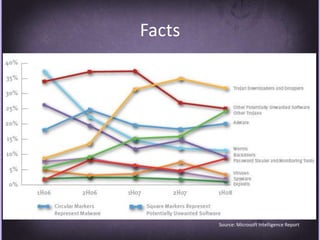
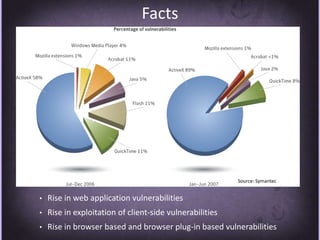
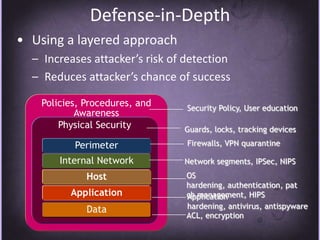
This document discusses protecting Windows networks from malware. It begins with two "immutable laws of security": if a bad actor can persuade you to run their program or alter the operating system, the computer is no longer yours. It then discusses current malware trends like compromising trusted websites and toolkits. Case studies show malware being spread through Facebook and Google. Best practices for defense include using defense-in-depth with policies, firewalls, host security, and continual patching and updates.