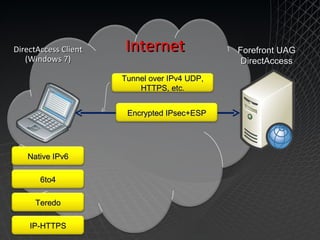
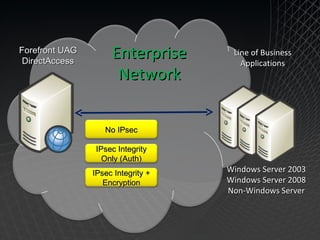
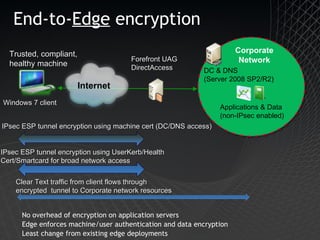
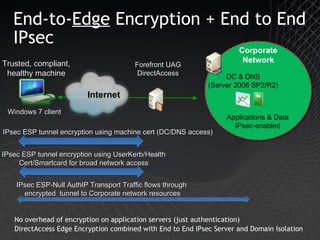
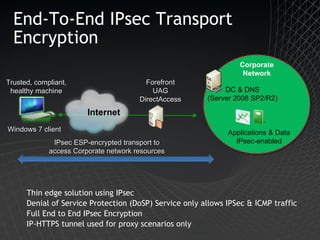
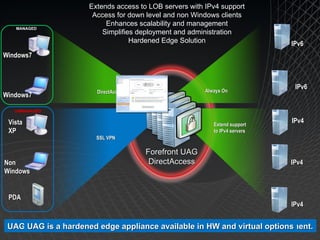
Microsoft Windows 7 provides enhanced security features such as AppLocker and Internet Explorer 8 to control applications and protect users. It also improves data protection with BitLocker and BitLocker To Go to encrypt data on devices and removable drives. Windows 7 builds on the security foundation of Windows Vista with features such as User Account Control and the Security Development Lifecycle.