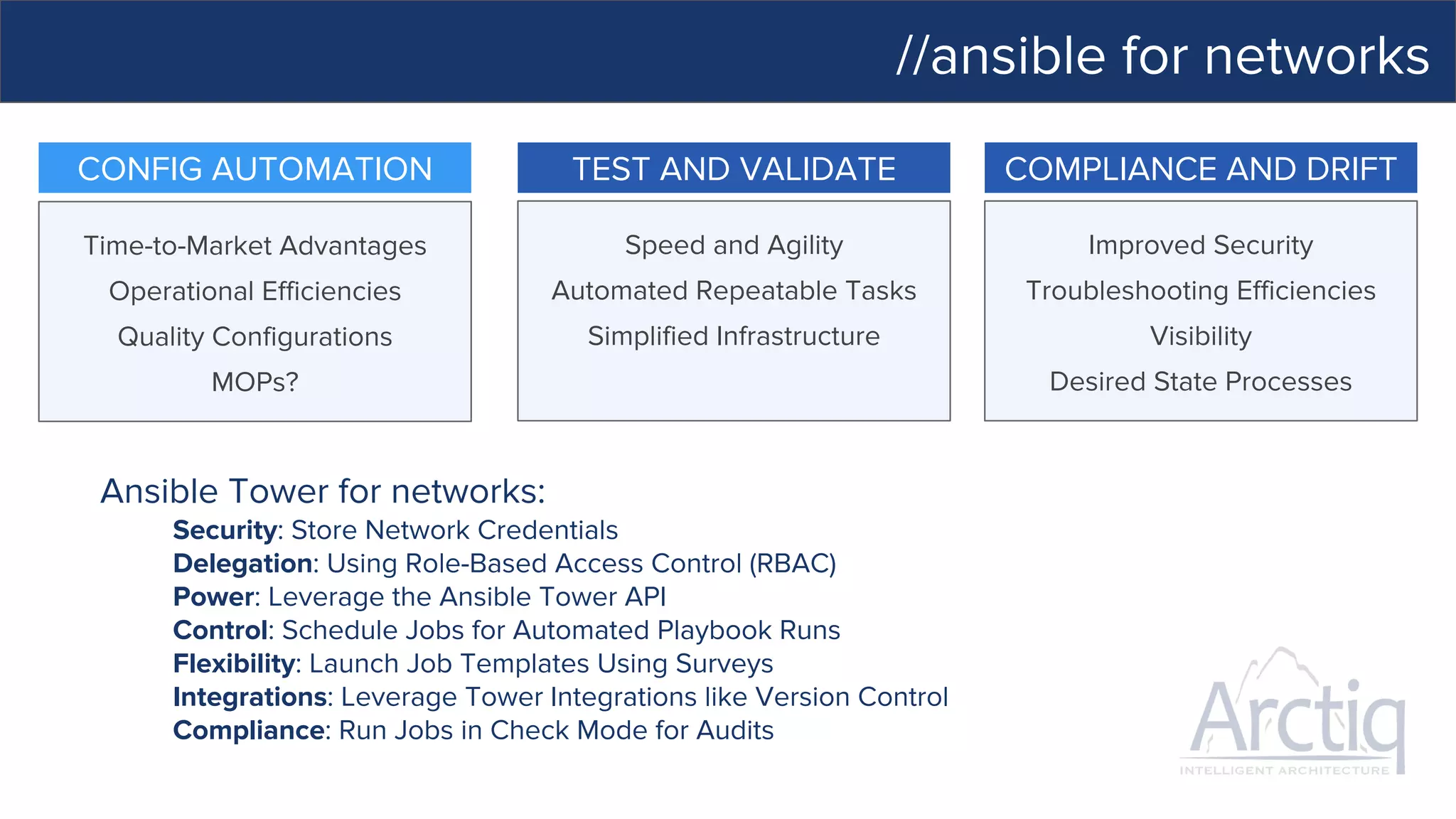
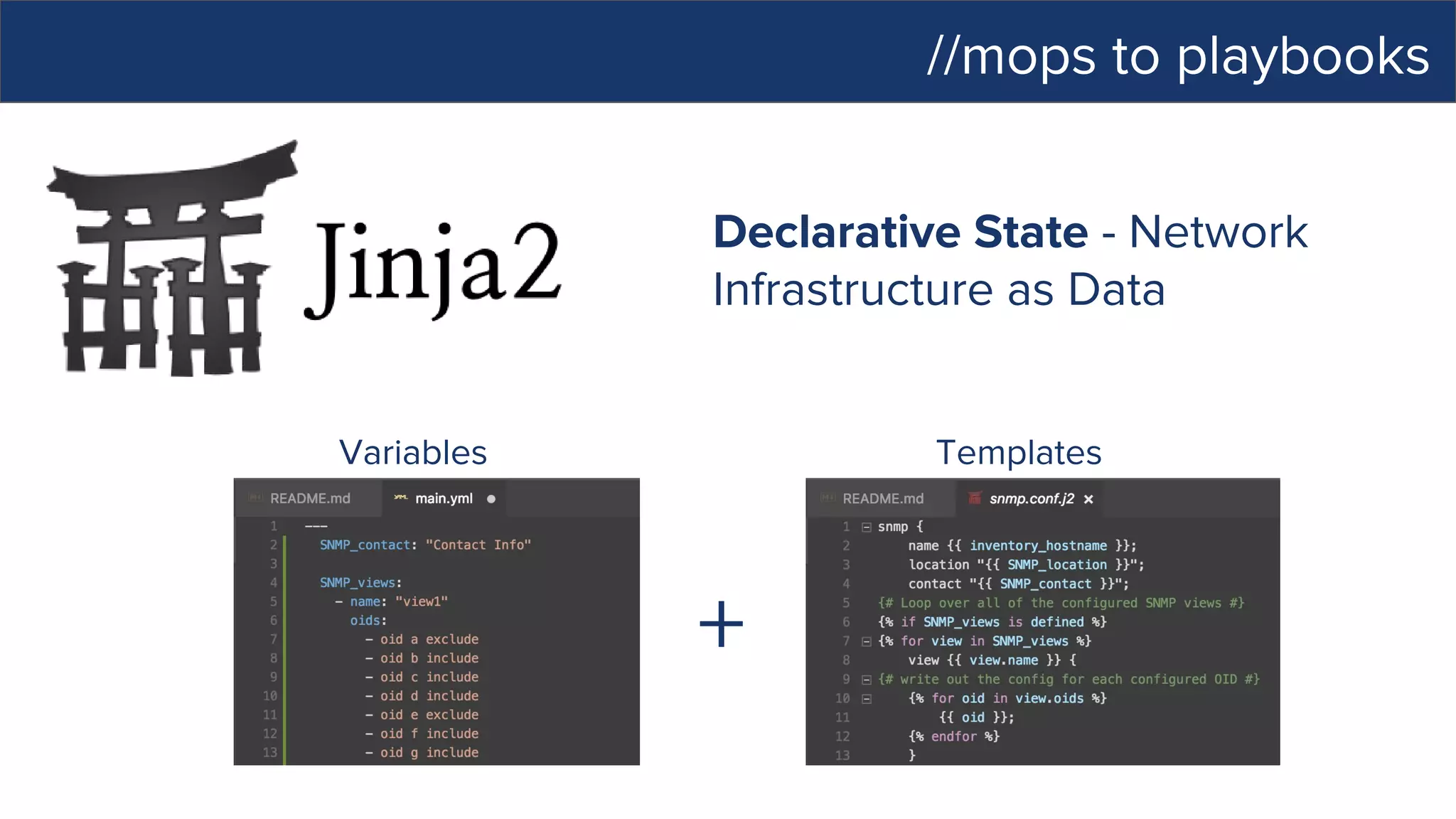
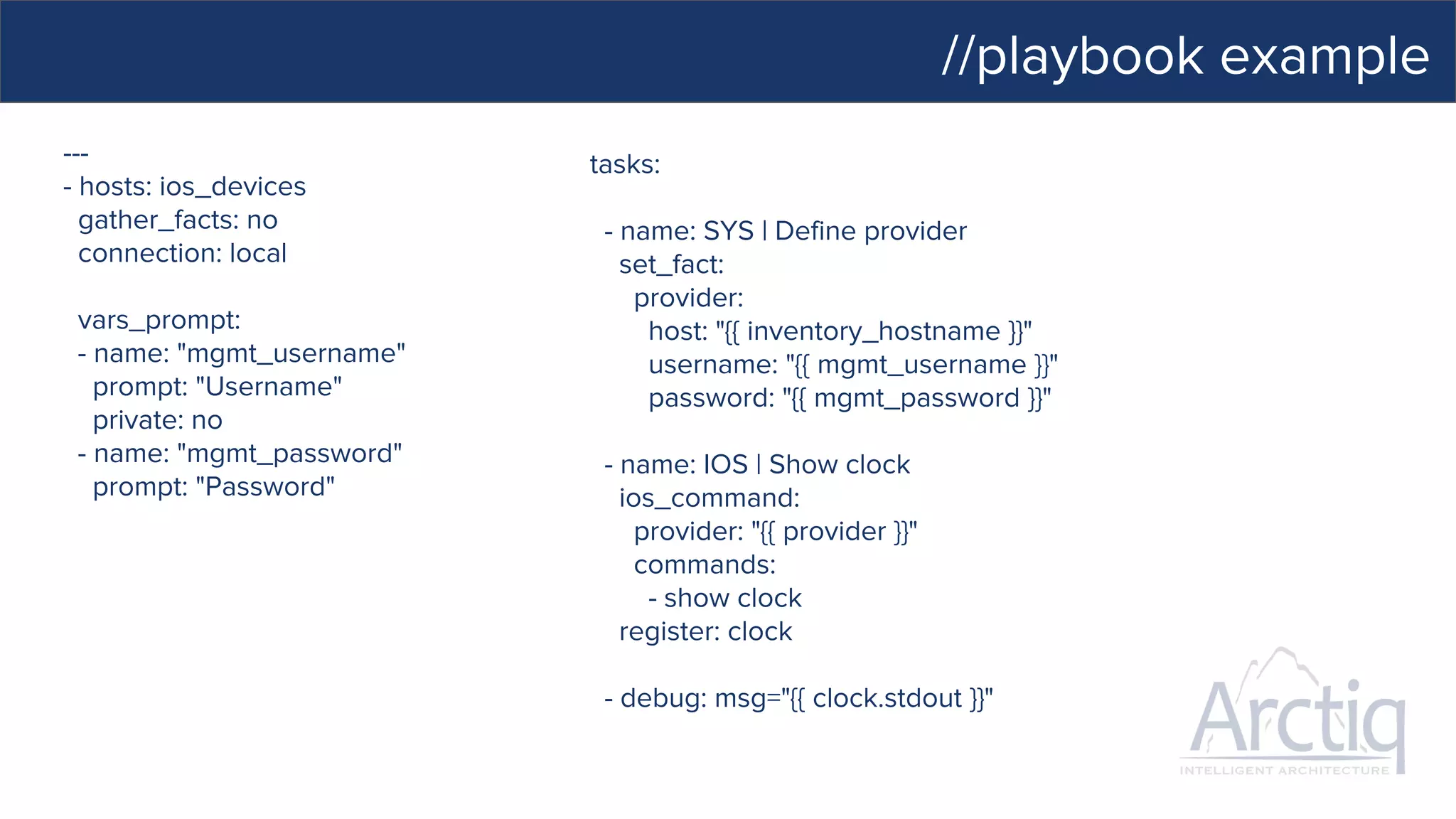
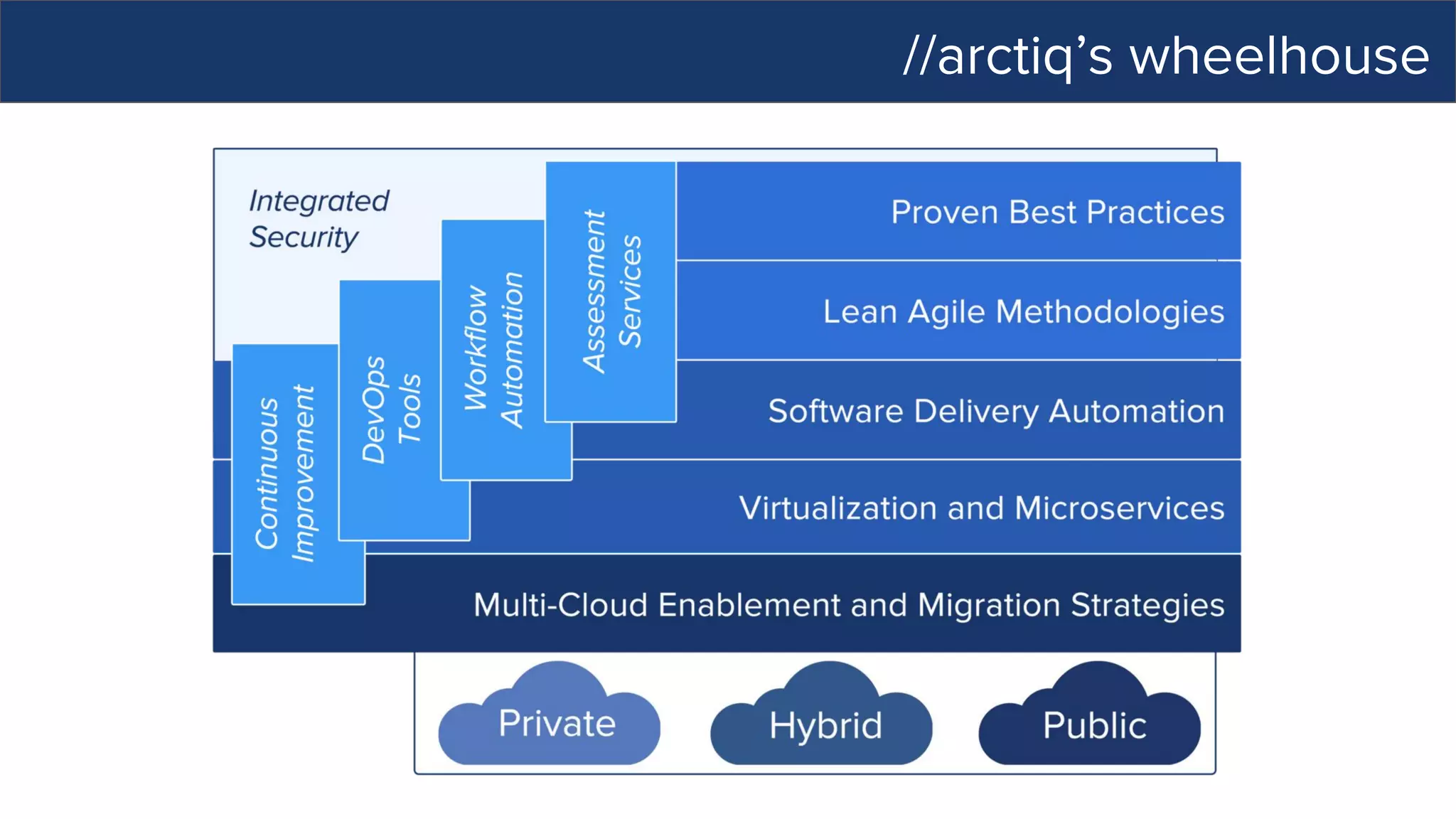
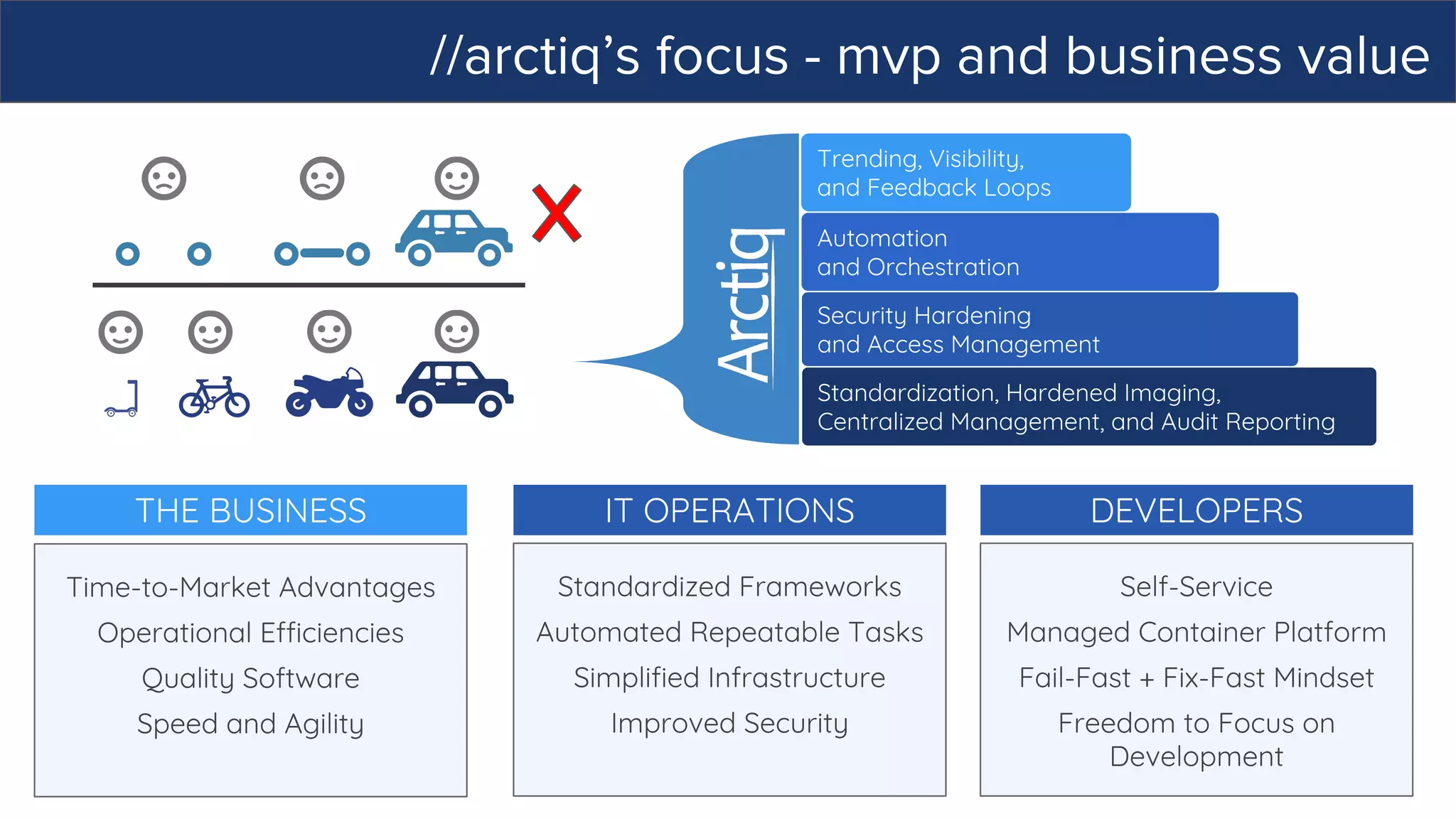
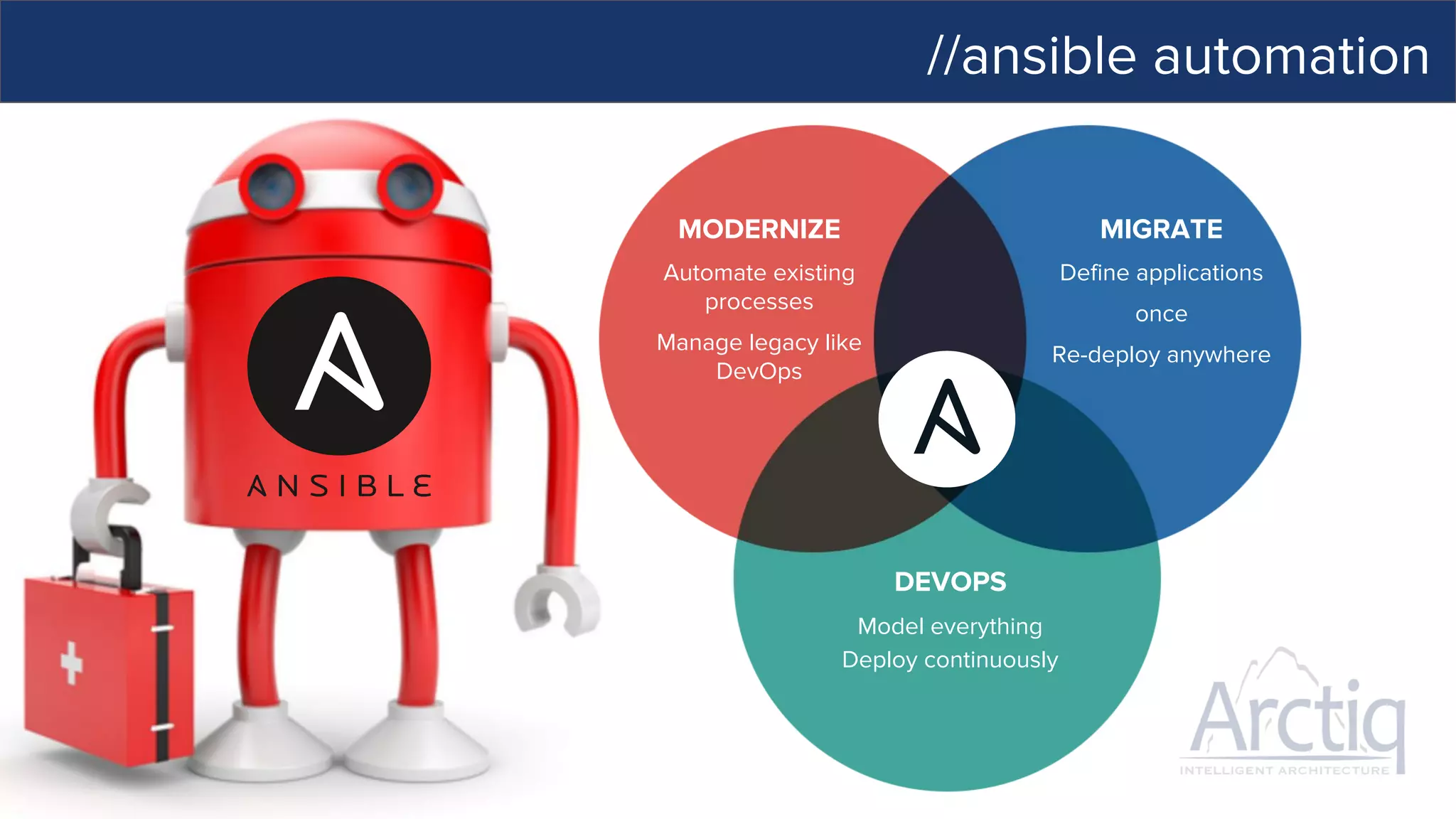
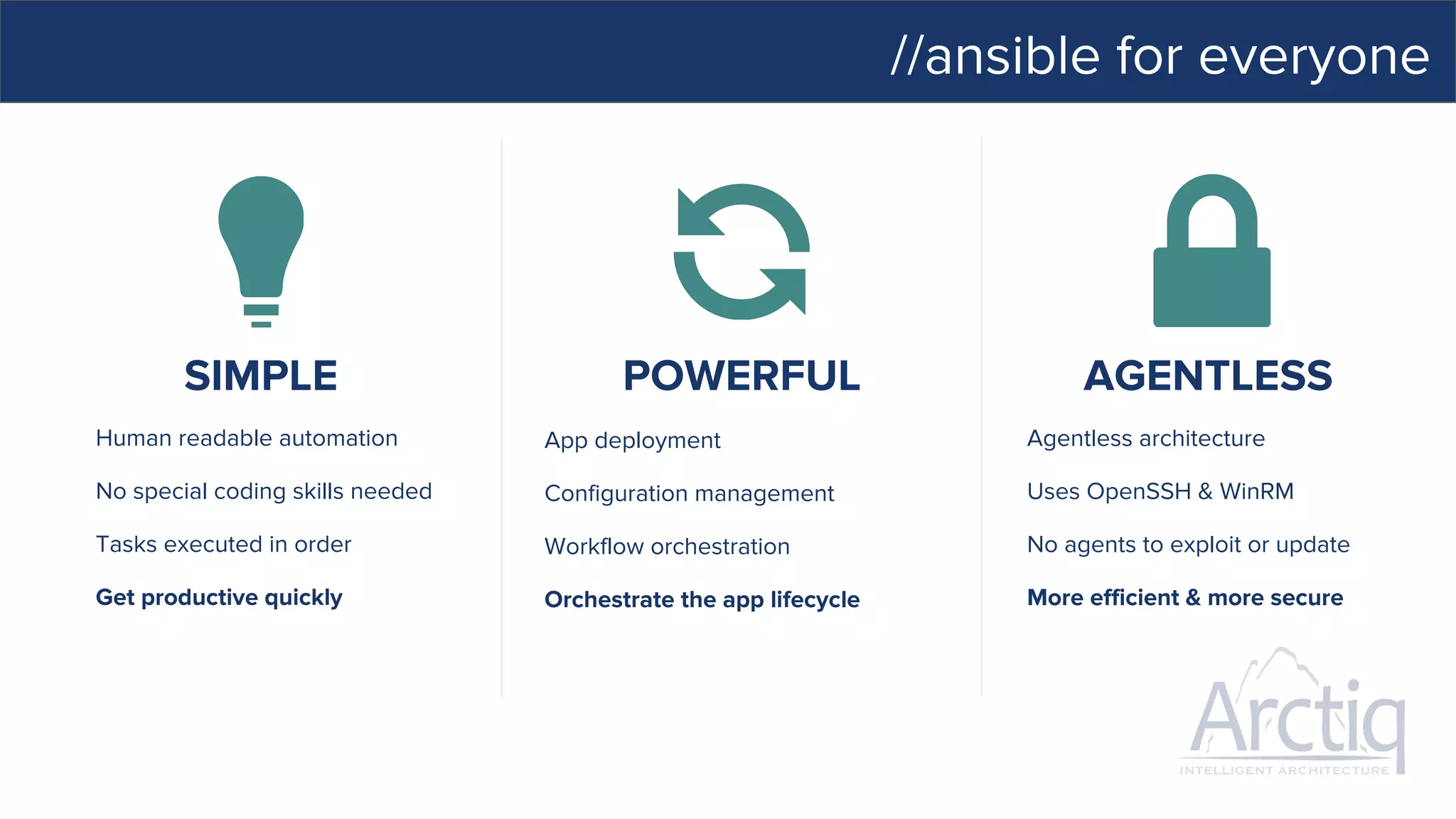
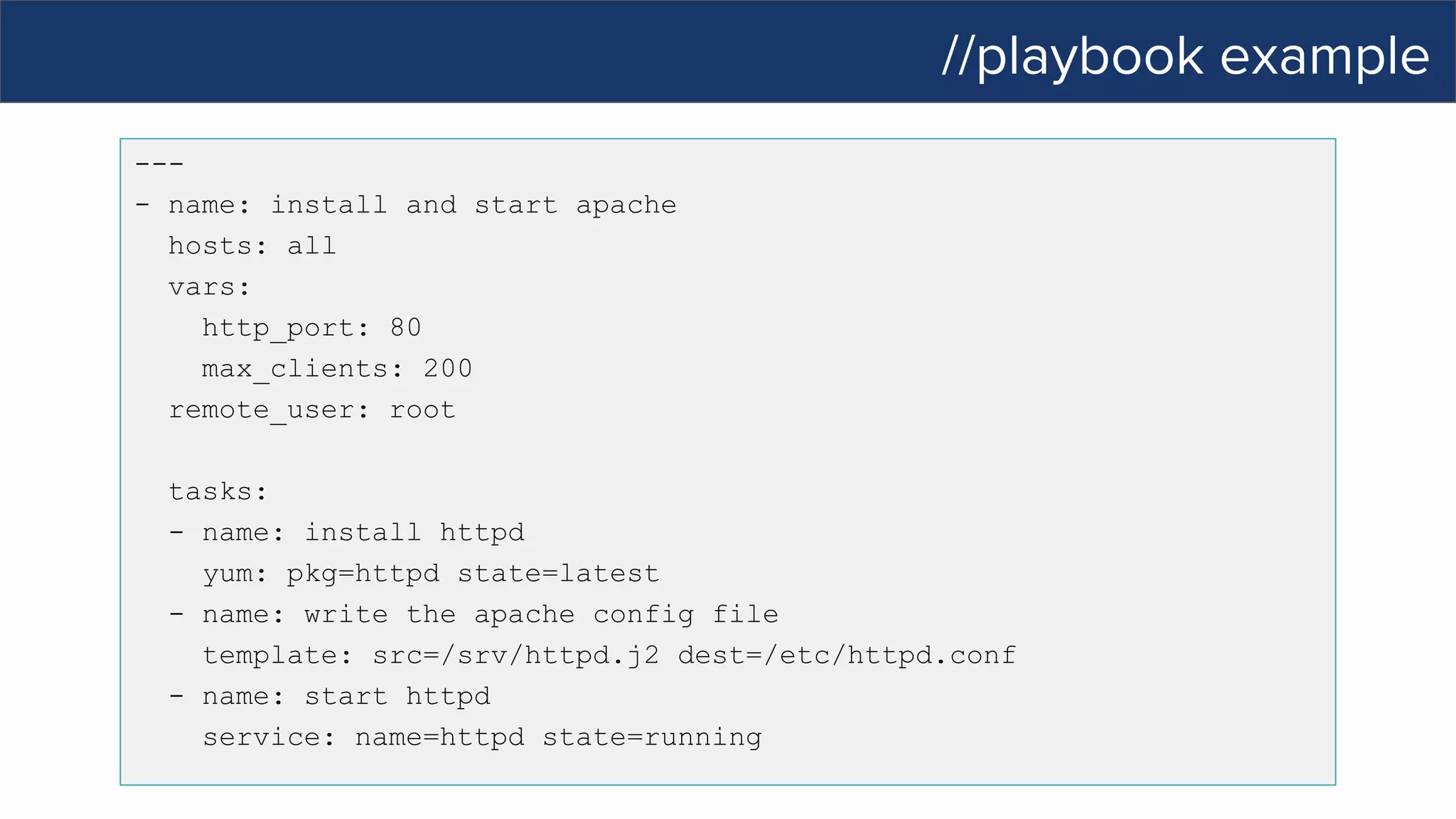
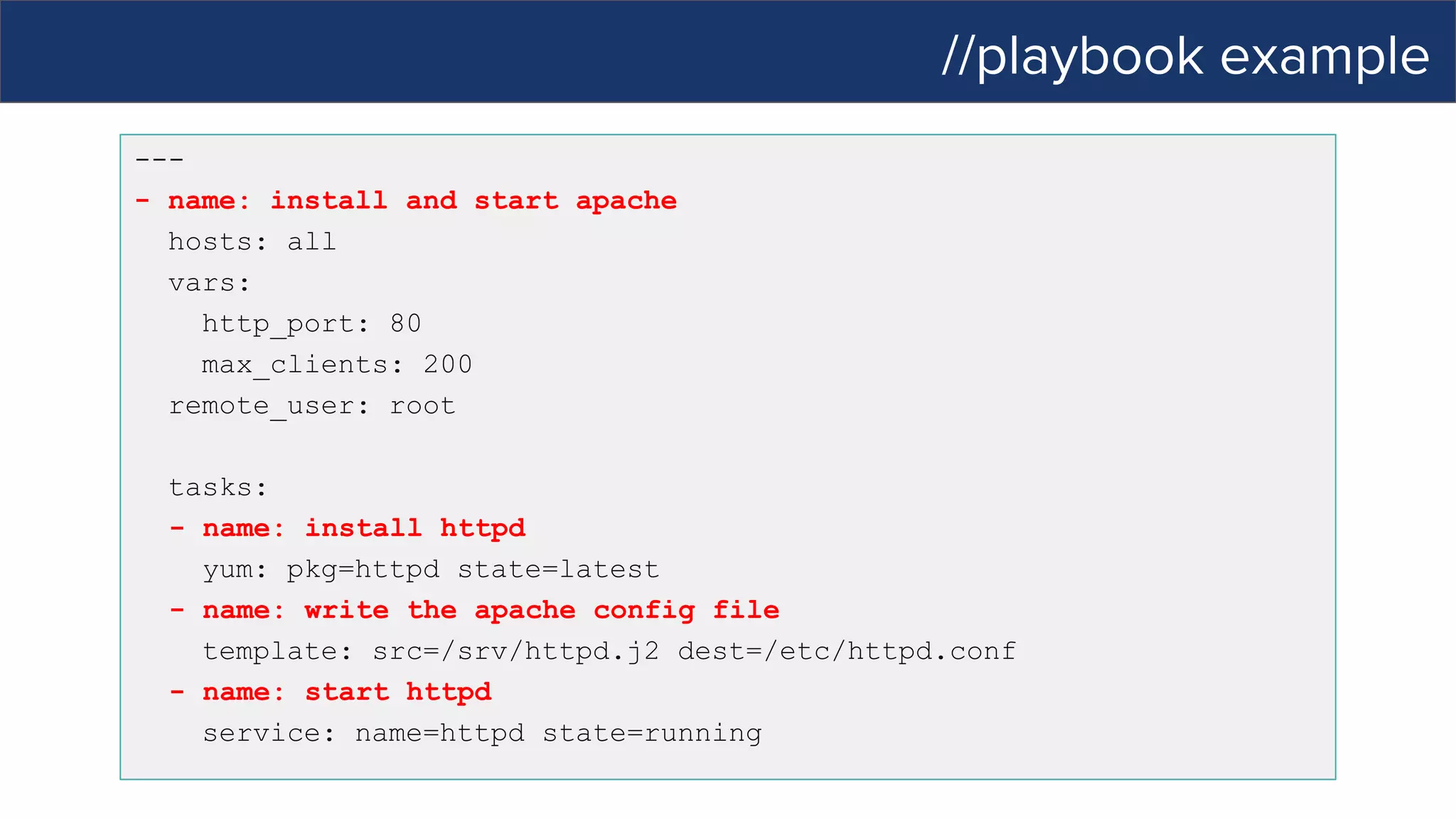
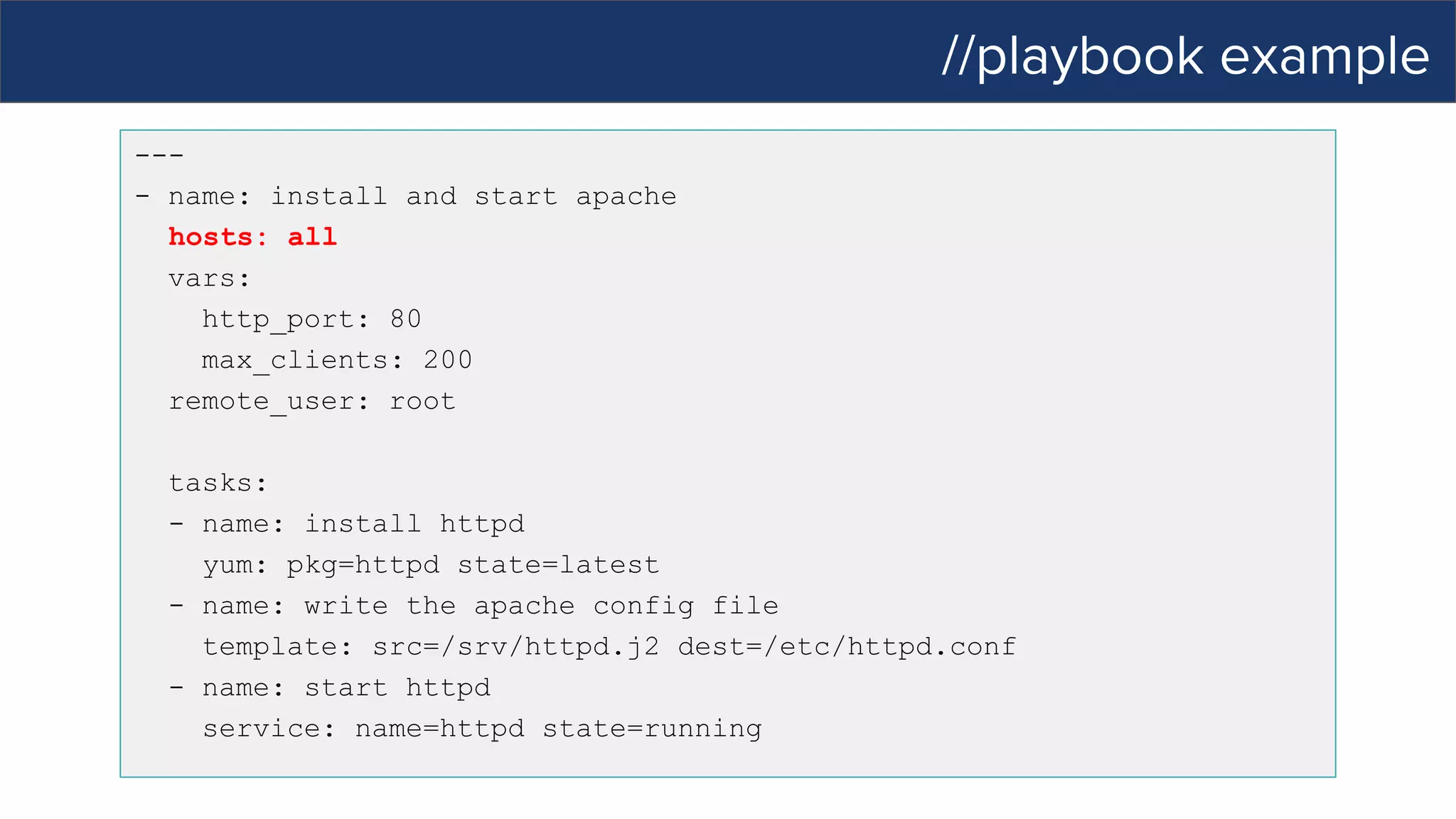
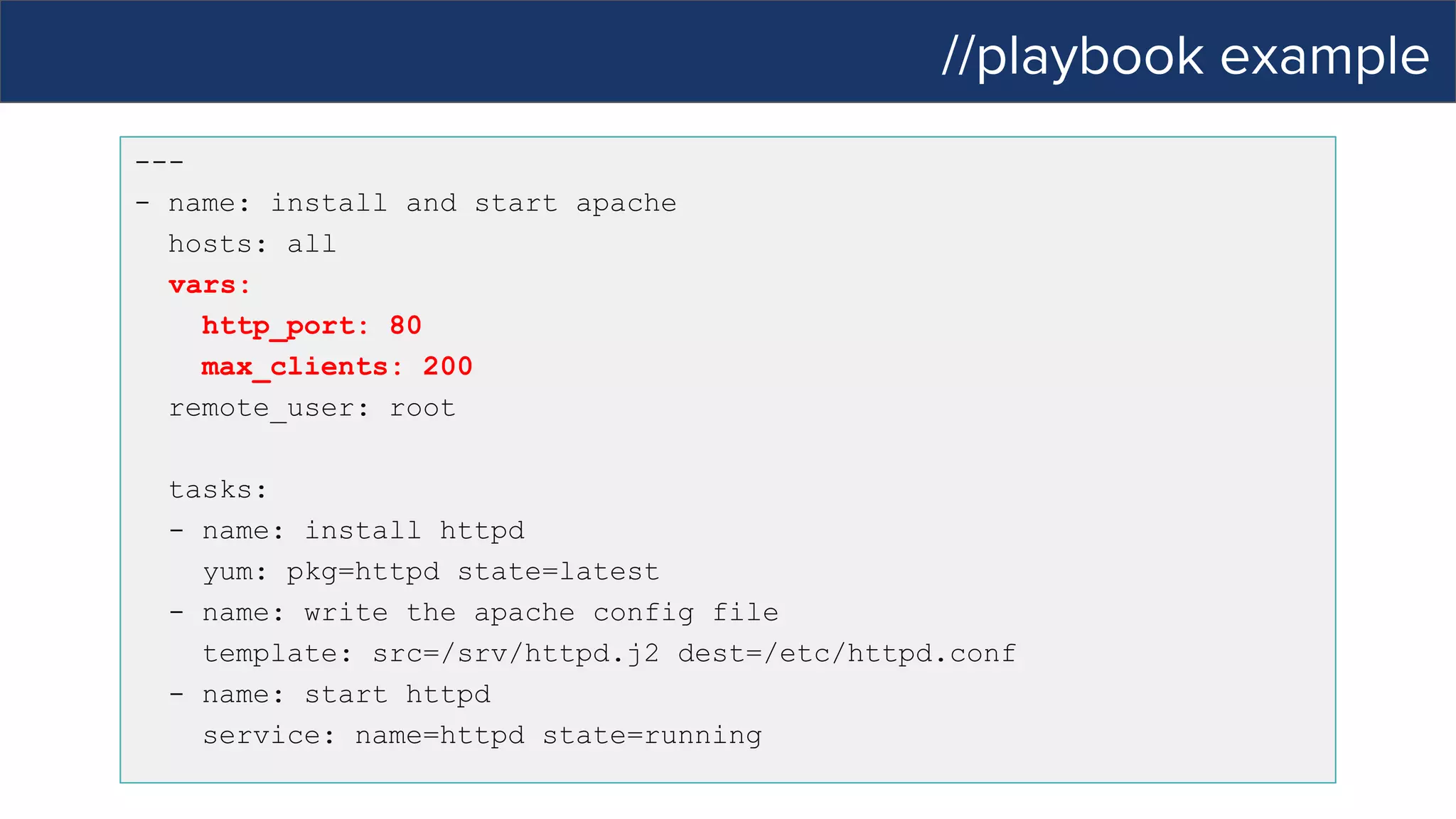
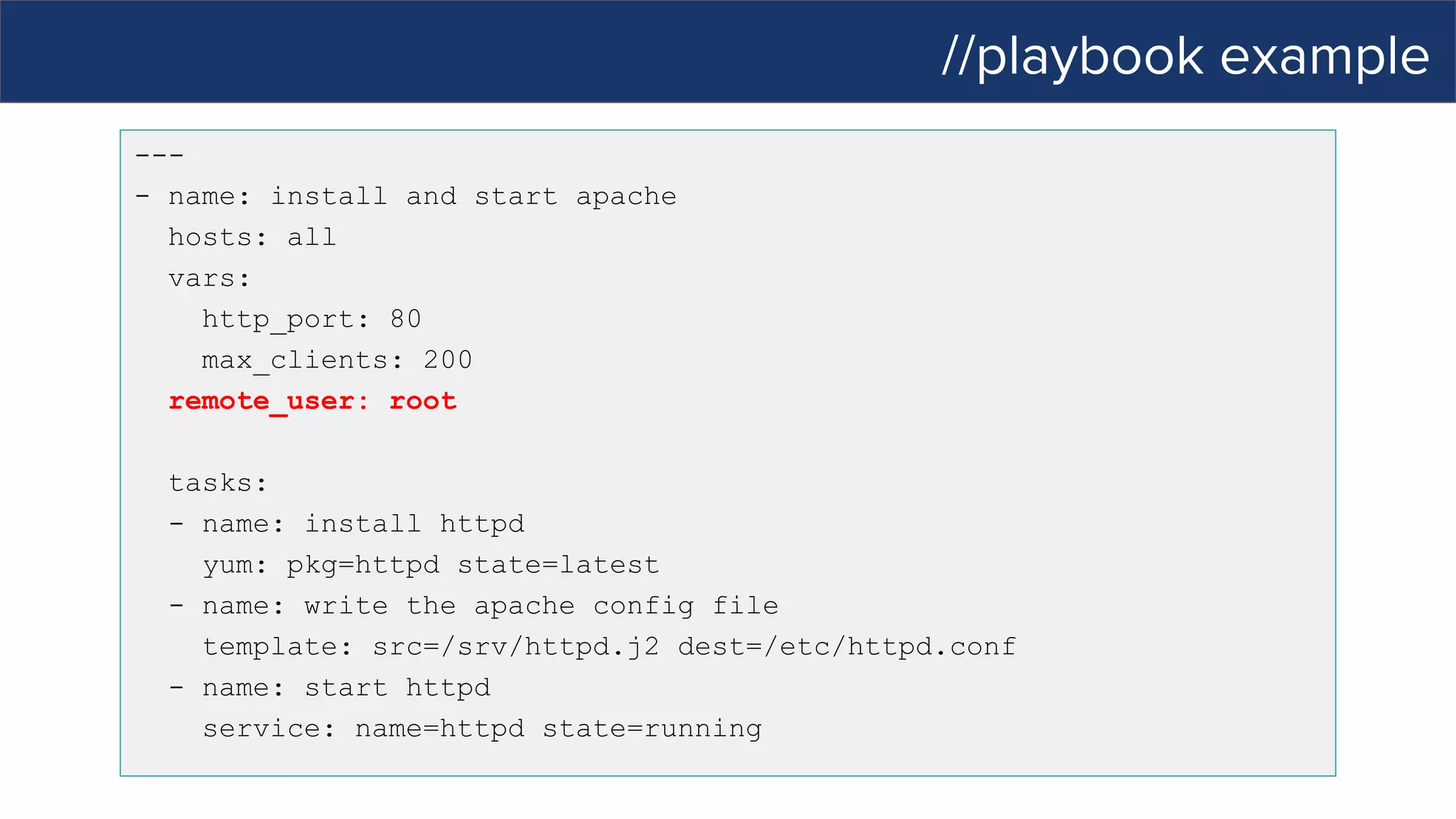
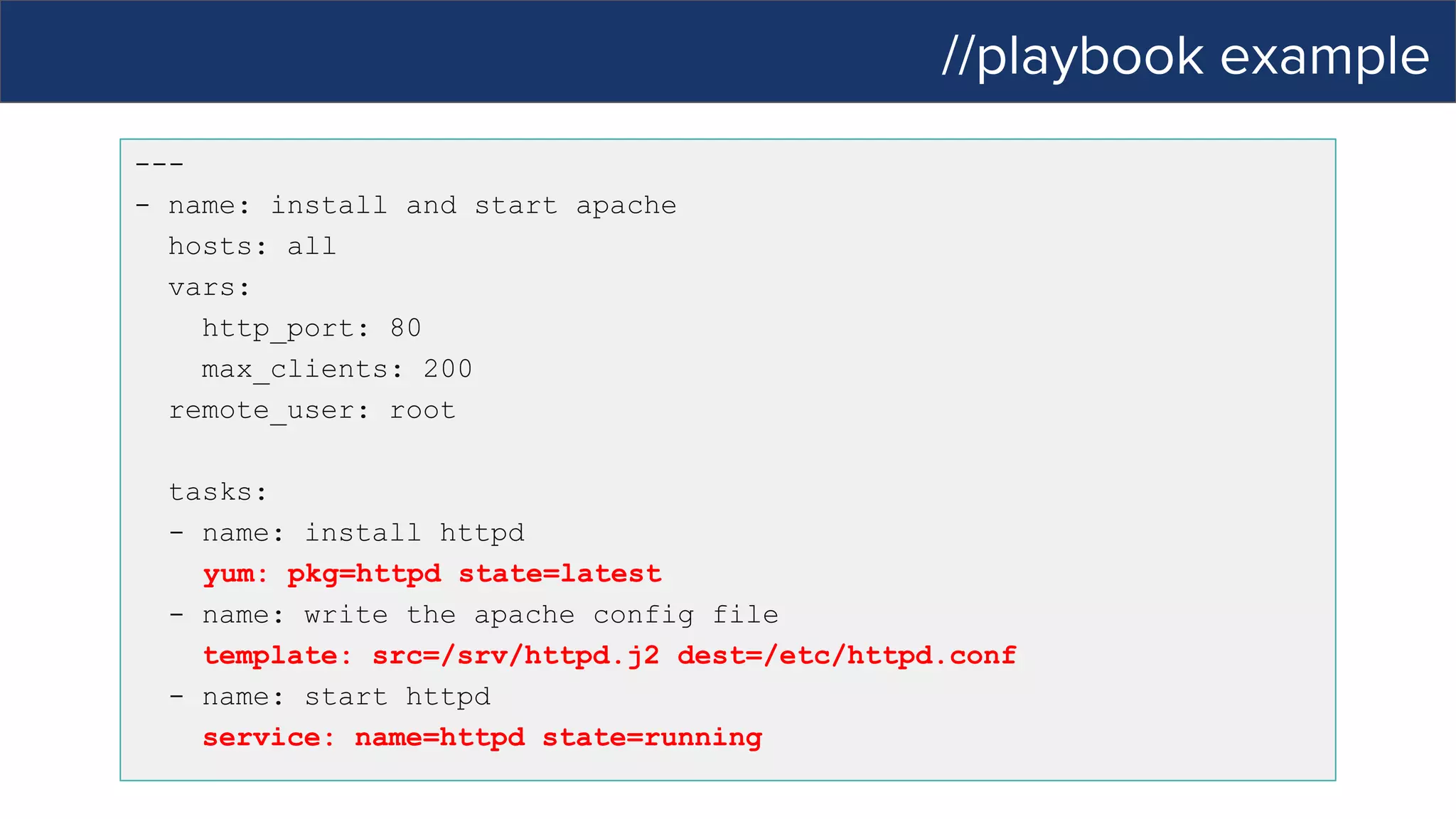
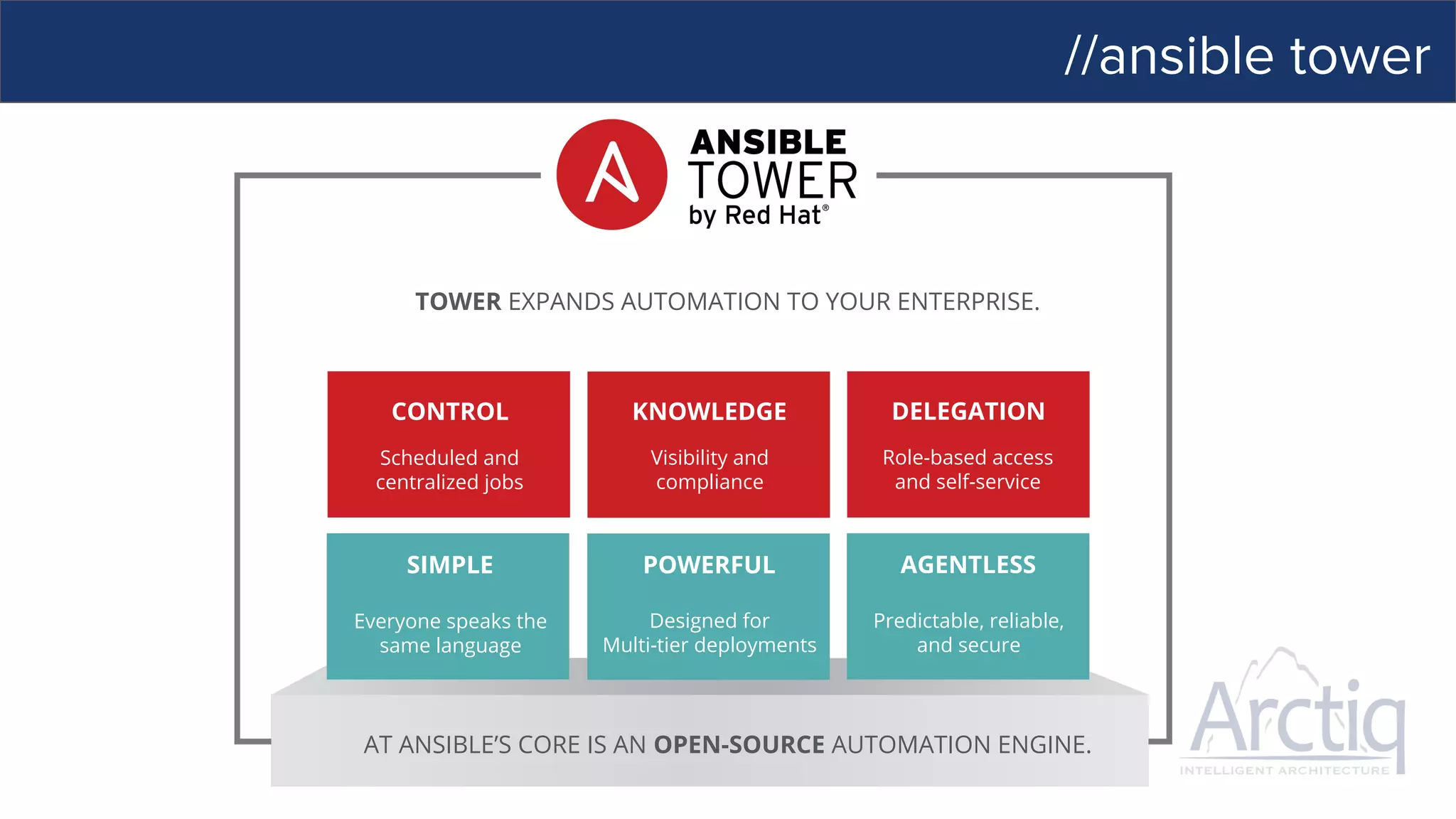
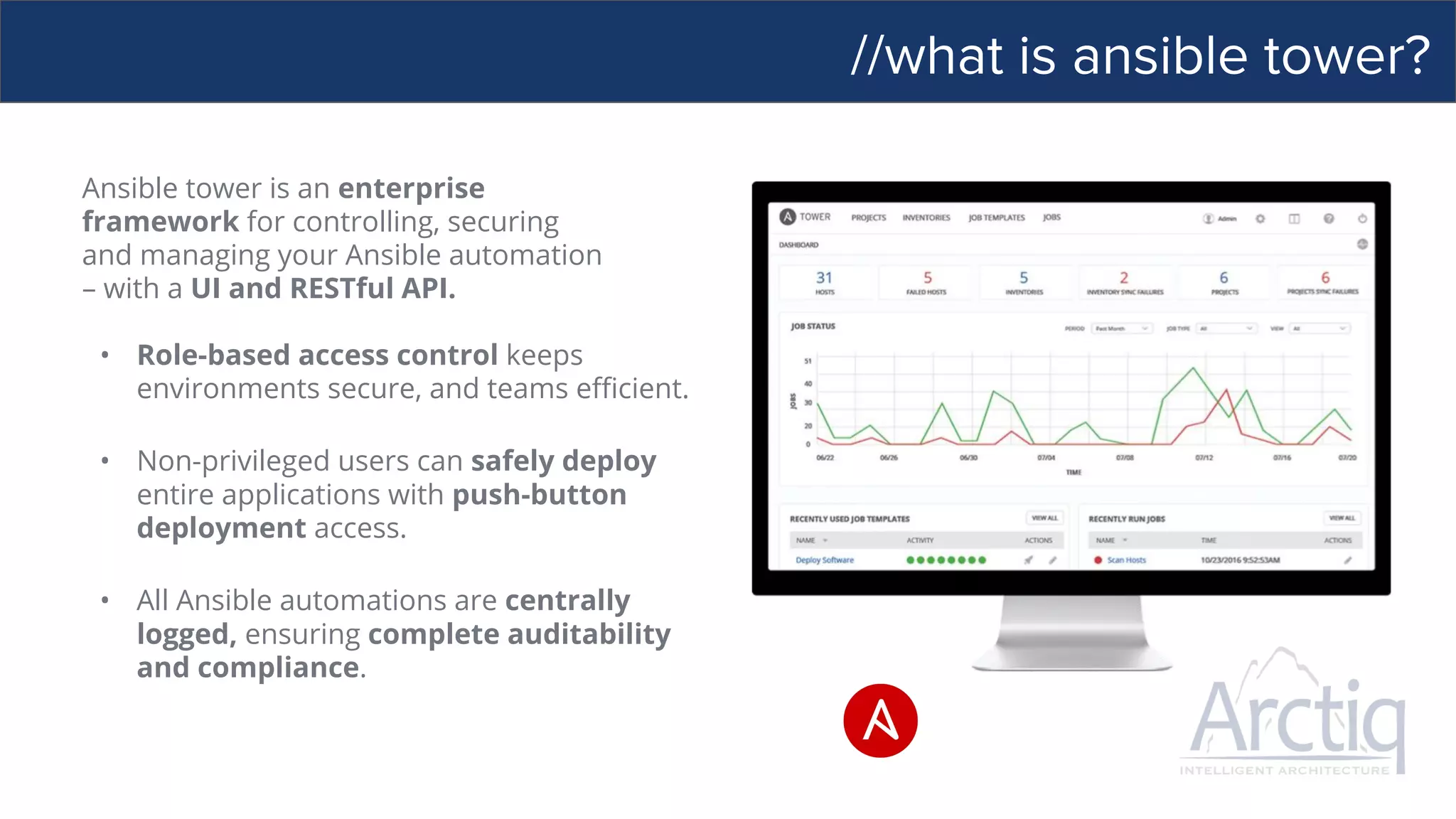
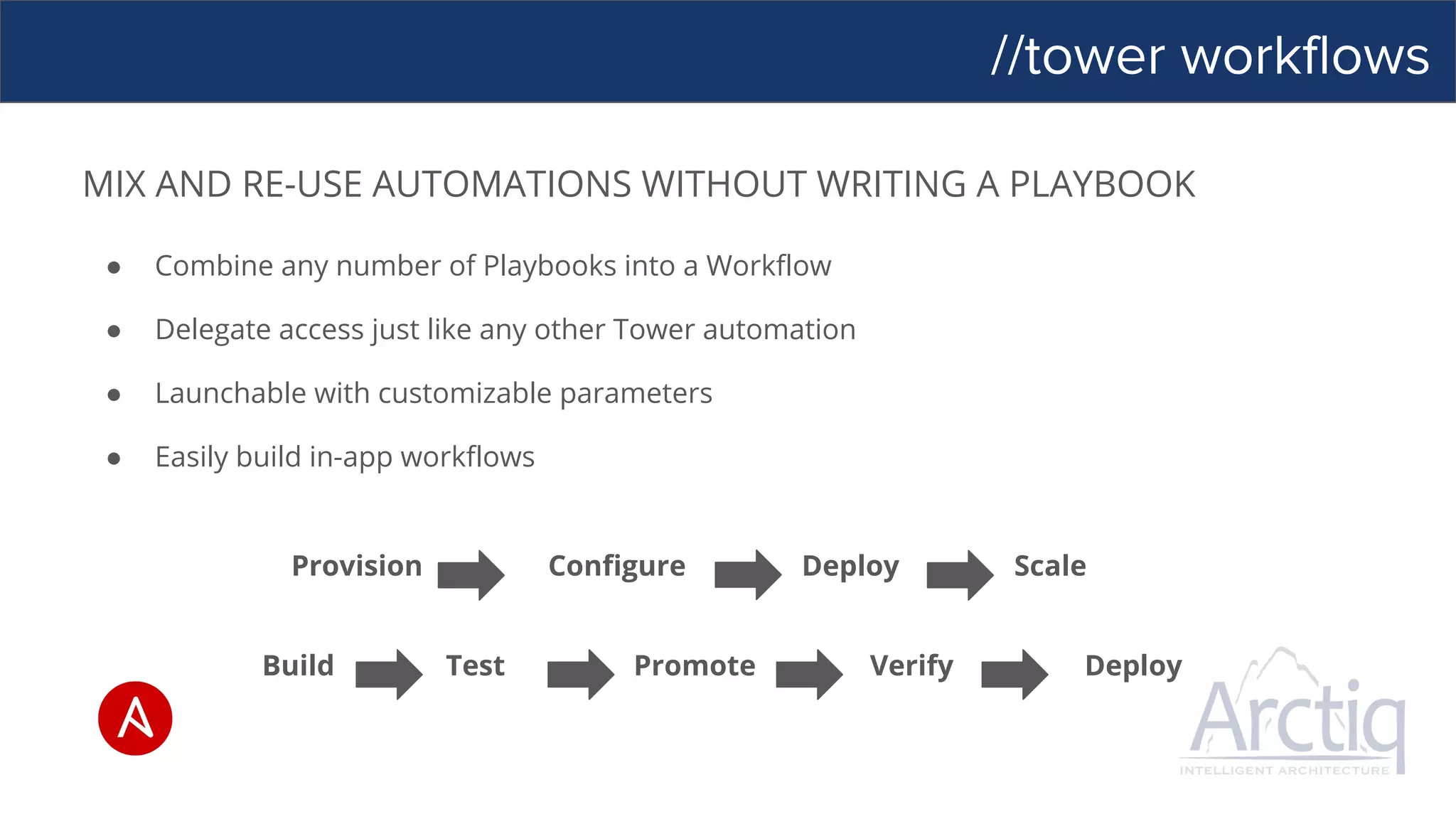
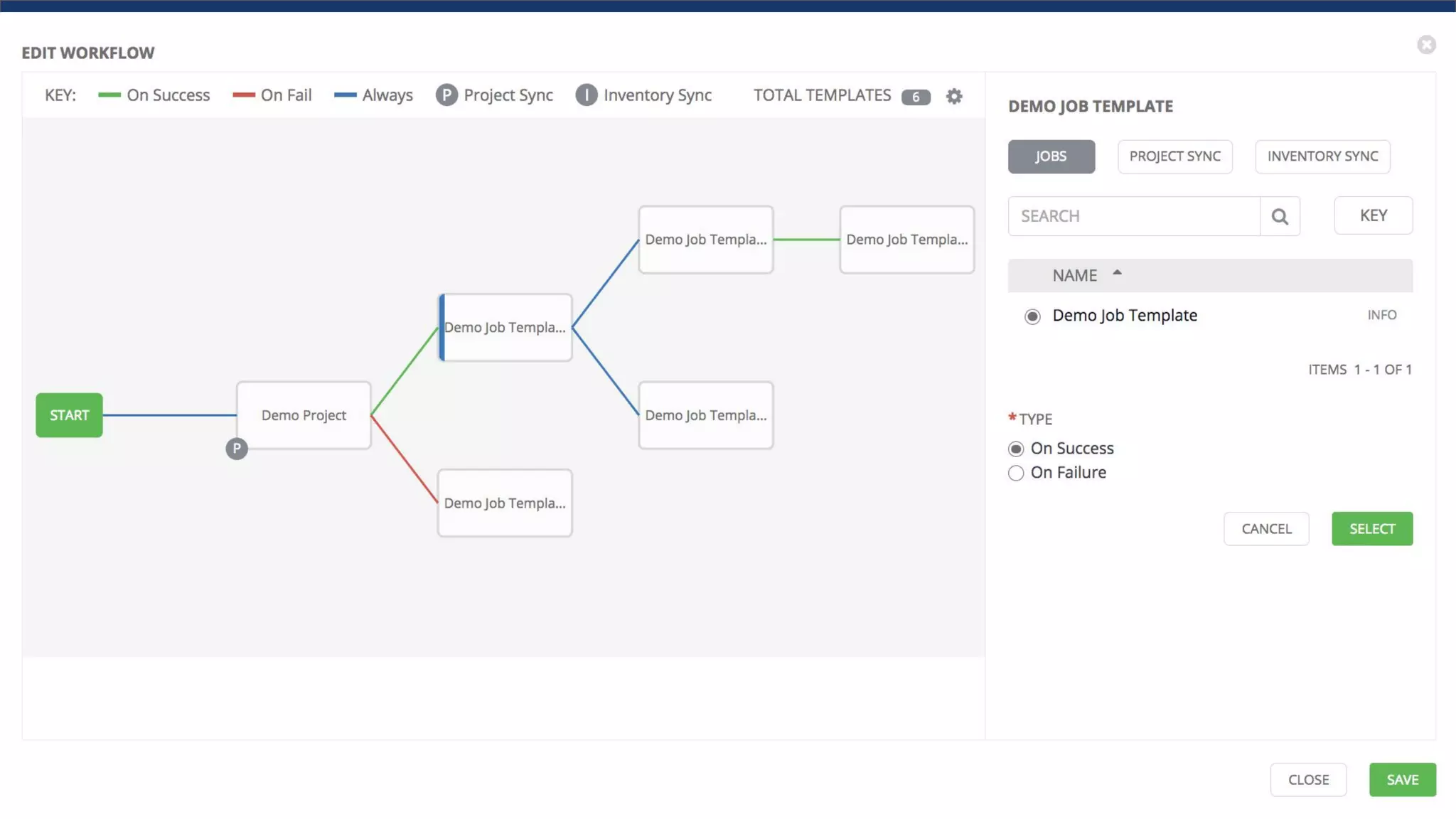
This document discusses Ansible, an open-source automation tool. It provides an overview of Ansible's capabilities including configuration management, orchestration, deployment and more. It also summarizes Ansible Tower which adds centralized control, RBAC, and other features to Ansible. Examples are given of using Ansible playbooks to automate tasks like installing and configuring Apache on Linux hosts and using Ansible modules to configure network devices.


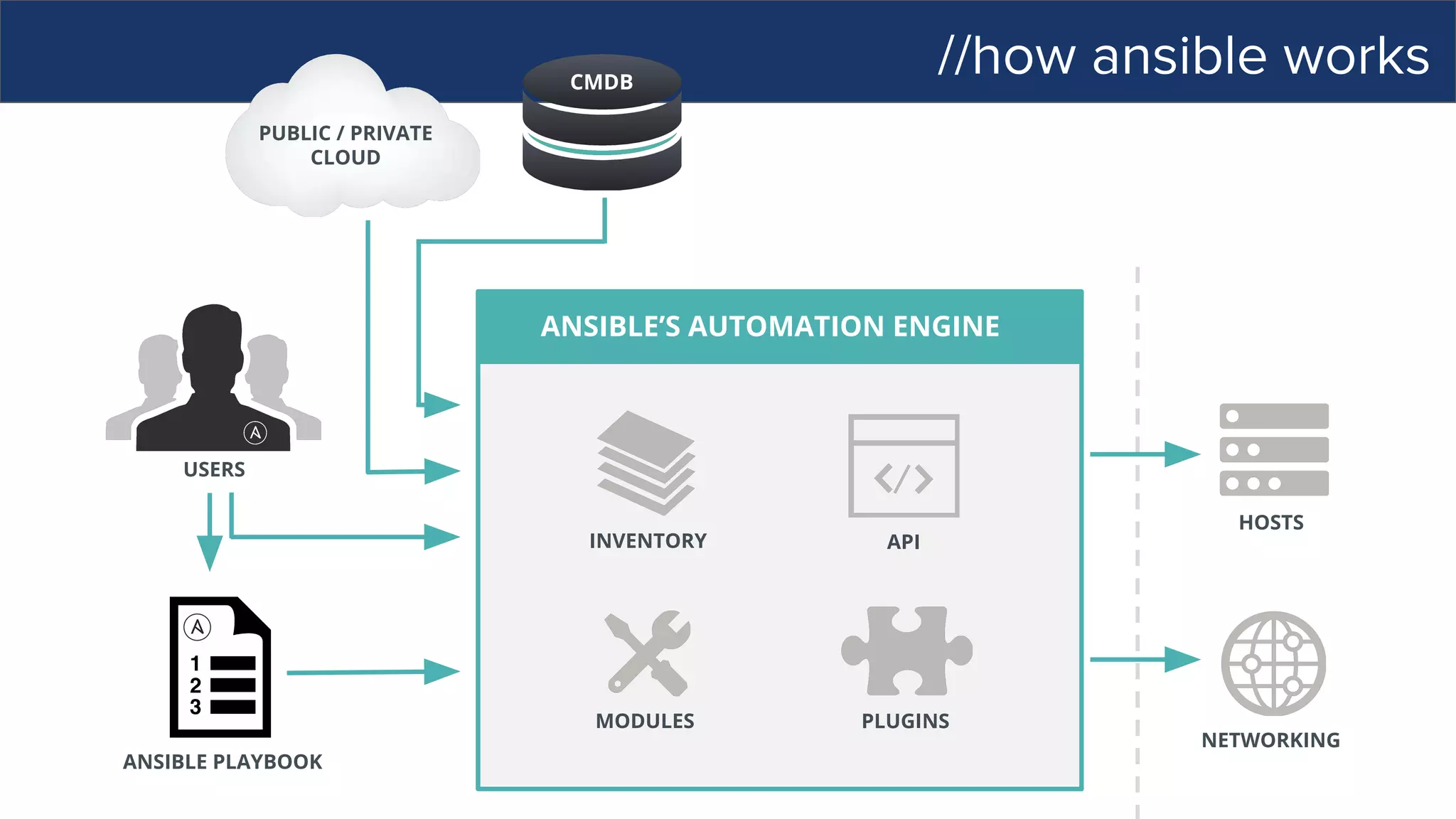
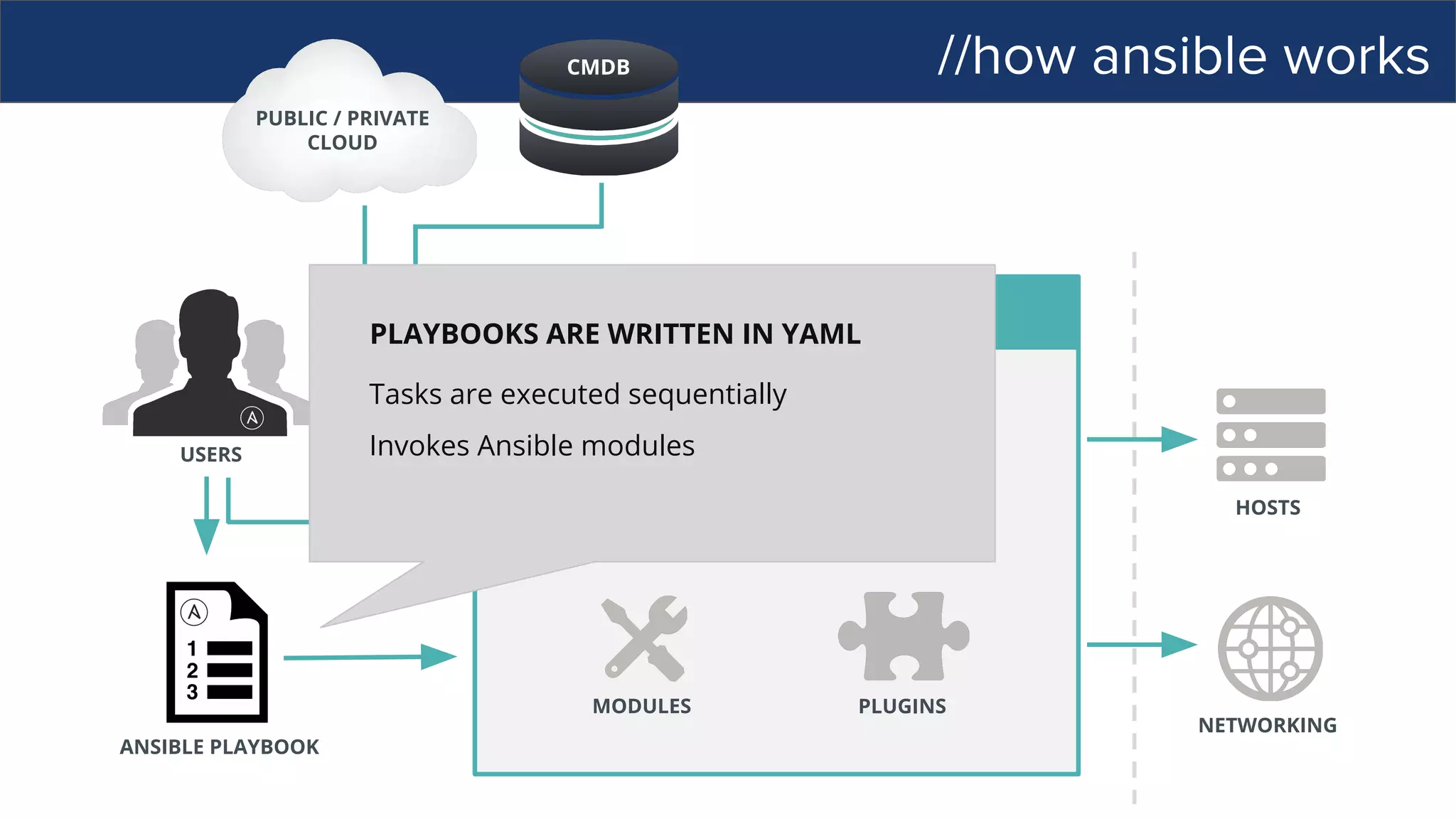
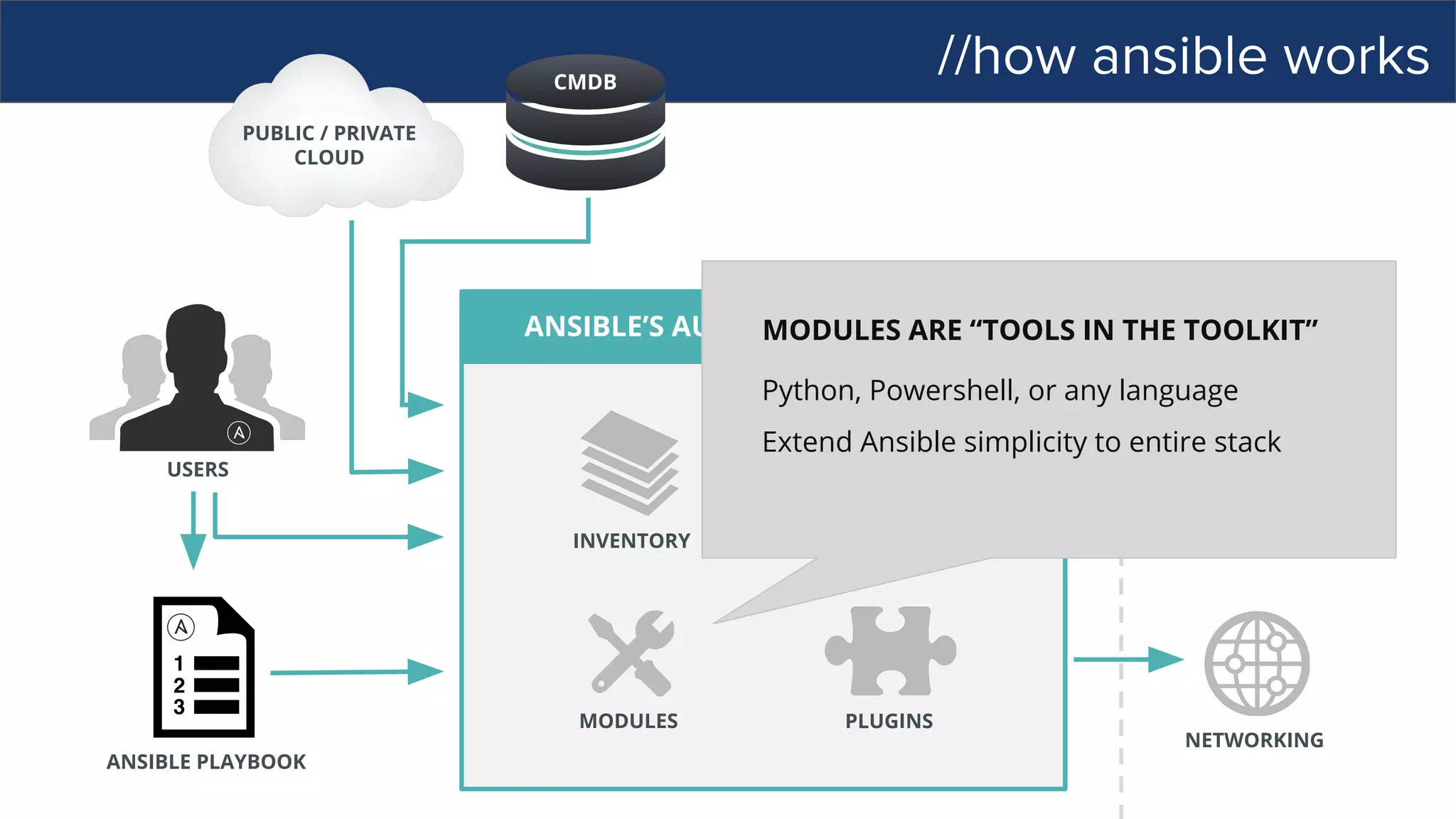
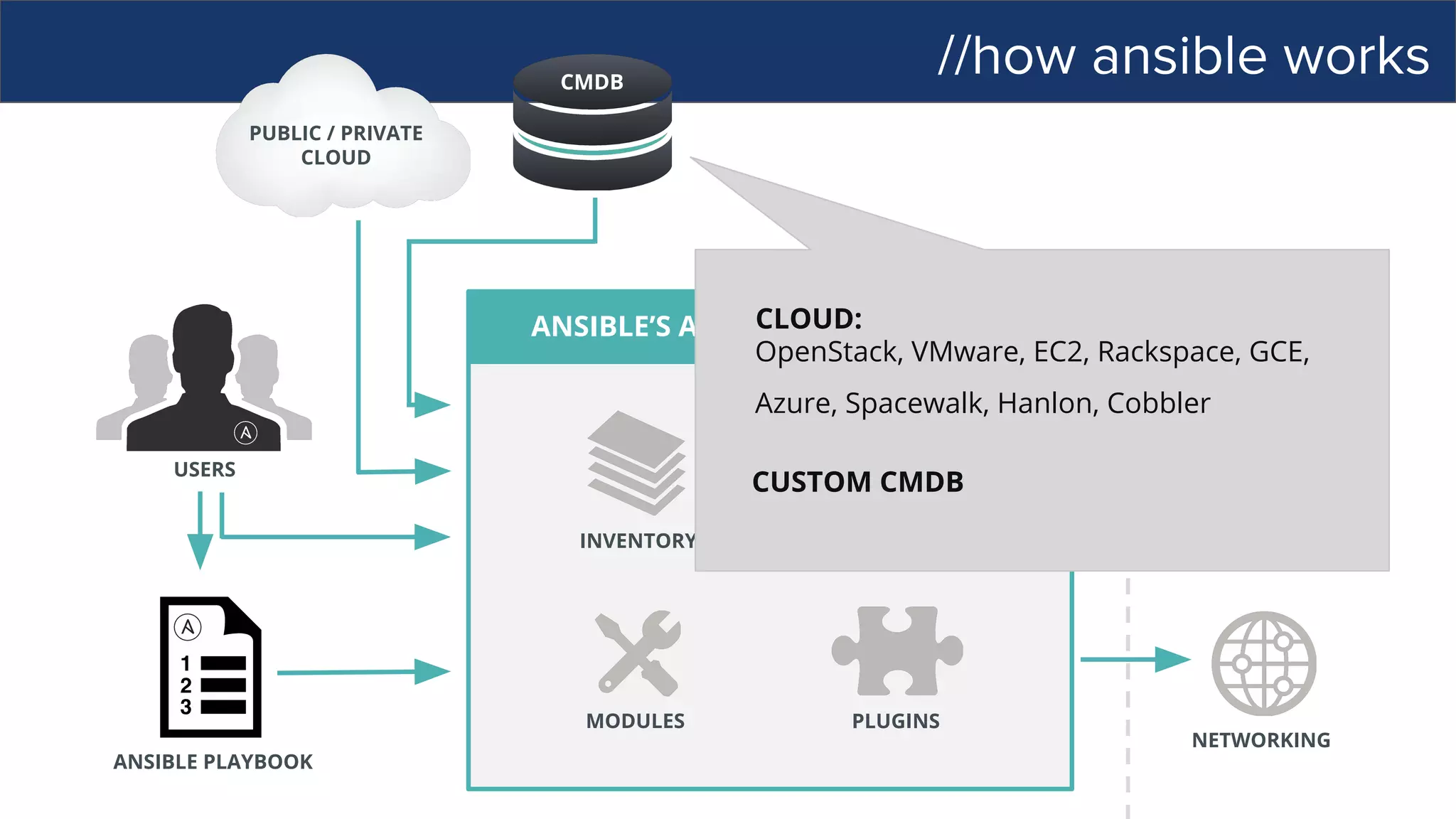
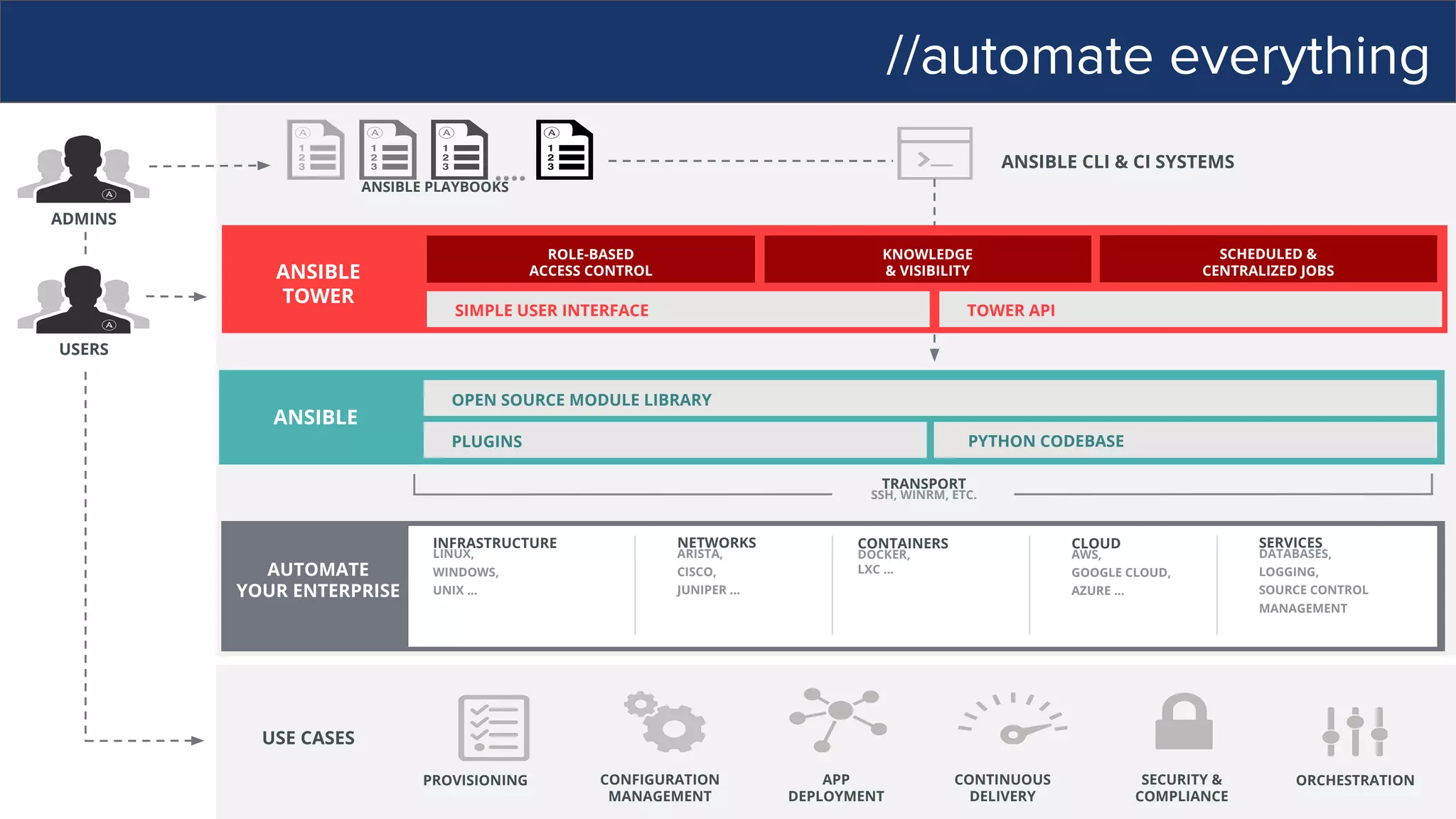
![//how ansible works
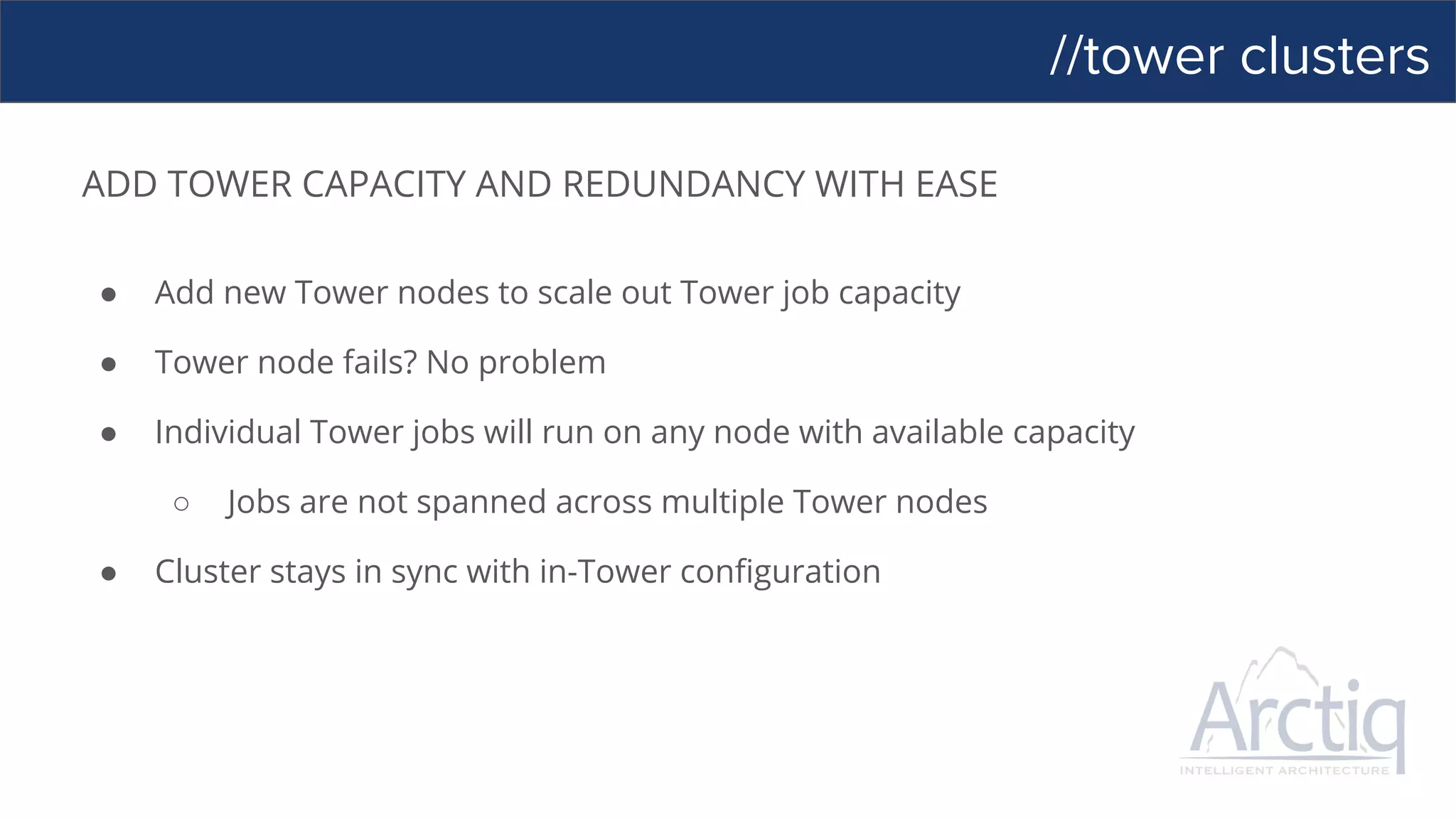
ANSIBLE’S AUTOMATION ENGINE
ANSIBLE PLAYBOOK
PUBLIC / PRIVATE
CLOUD
CMDB
USERS
HOSTS
NETWORKING
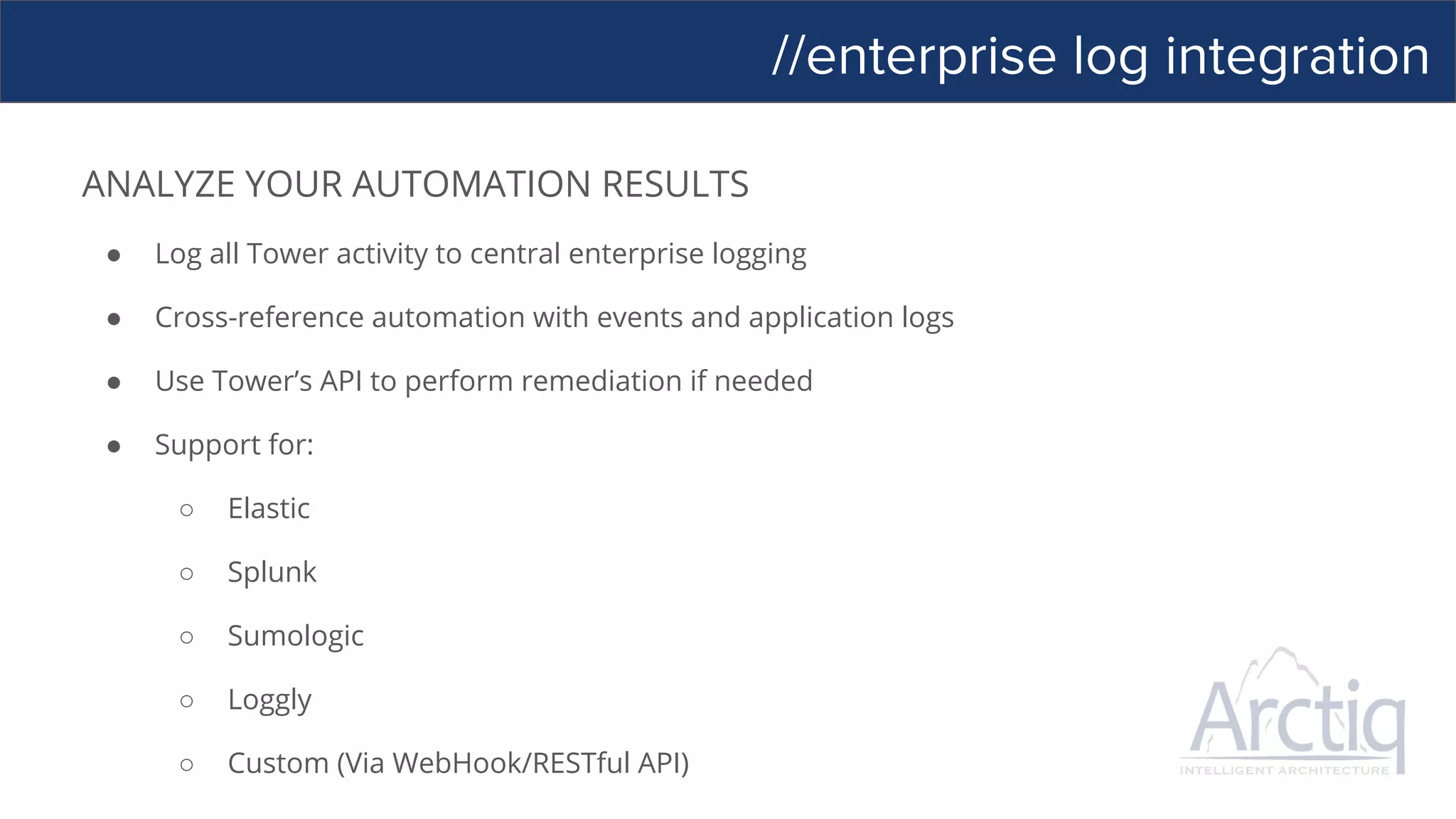
PLUGINS
API
MODULES
INVENTORY
[web]
webserver1.example.com
webserver2.example.com
[db]
dbserver1.example.com](https://image.slidesharecdn.com/ansibleautomationtorulethemall-170306163125/75/Ansible-Automation-to-Rule-Them-All-10-2048.jpg)









![● Configure Kerberos
# vi /etc/krb5.conf
[realms]
MY.DOMAIN.COM = {
kdc = domain-controller1.my.domain.com
kdc = domain-controller2.my.domain.com
}
[domain_realm]
.my.domain.com = MY.DOMAIN.COM
//authentication](https://image.slidesharecdn.com/ansibleautomationtorulethemall-170306163125/75/Ansible-Automation-to-Rule-Them-All-37-2048.jpg)