Ansible Automation can be used to deliver a high-level introduction of Red Hat Ansible Automation. This deck contains speaker notes and can be used to start discussions with customers. It provides a technical overview but not a deep dive. Follow-on discussions would leverage Red Hat Ansible Automation technical materials.








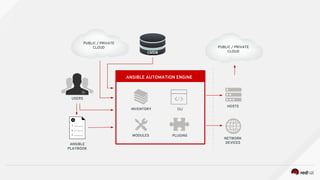
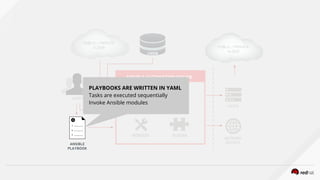
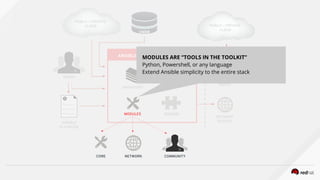
![ANSIBLE AUTOMATION ENGINE
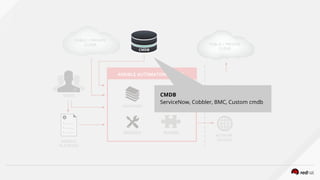
CMDB
USERS
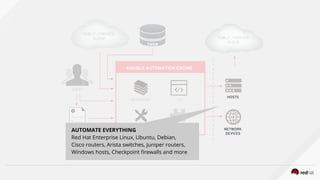
HOSTS
NETWORK
DEVICES
CLI
ANSIBLE
PLAYBOOK
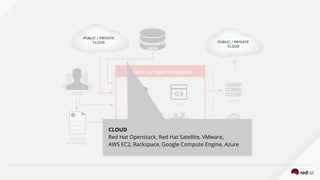
PUBLIC / PRIVATE
CLOUD
PUBLIC / PRIVATE
CLOUD
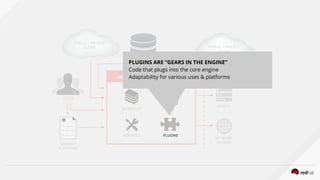
MODULES PLUGINS
INVENTORY
INVENTORY
[web]
webserver1.example.com
webserver2.example.com
[db]
dbserver1.example.com
[switches]
leaf01.internal.com
leaf02.internal.com
[firewalls]
checkpoint01.internal.com
[lb]
f5-01.internal.com](https://image.slidesharecdn.com/redhatansibleautomationtechnicaldeck-191122093155/85/Red-hat-ansible-automation-technical-deck-18-320.jpg)






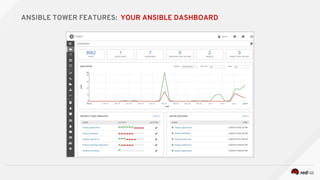
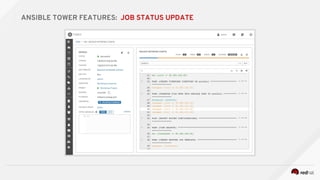
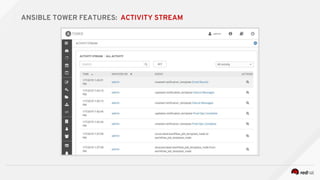
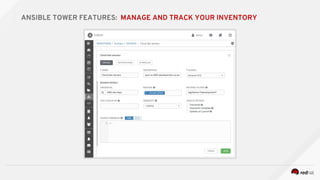
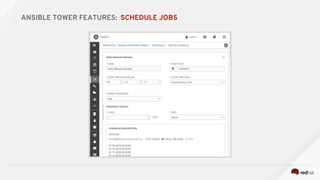
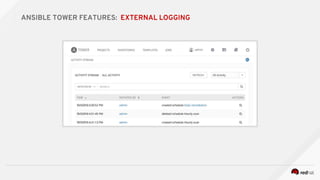

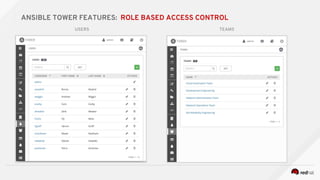
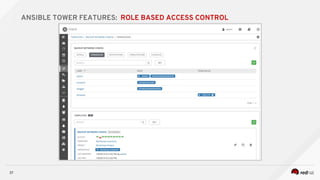
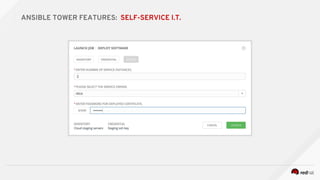
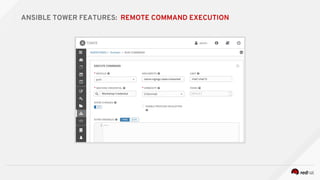

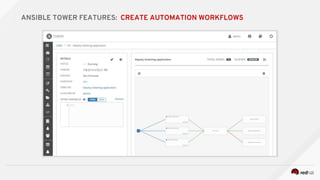



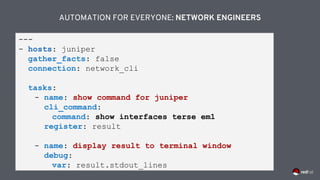
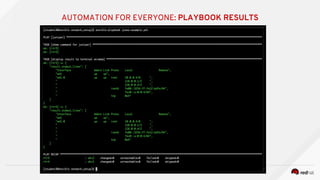


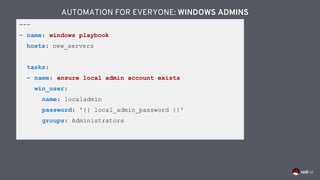
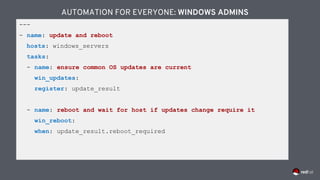
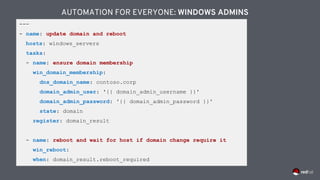
![---
- name: windows playbook
hosts: windows_machines
tasks:
- name: ensure common tools are installed
win_chocolatey:
name: '{{ item }}'
loop: ['sysinternals', 'googlechrome']
AUTOMATION FOR EVERYONE: WINDOWS ADMINS](https://image.slidesharecdn.com/redhatansibleautomationtechnicaldeck-191122093155/85/Red-hat-ansible-automation-technical-deck-58-320.jpg)