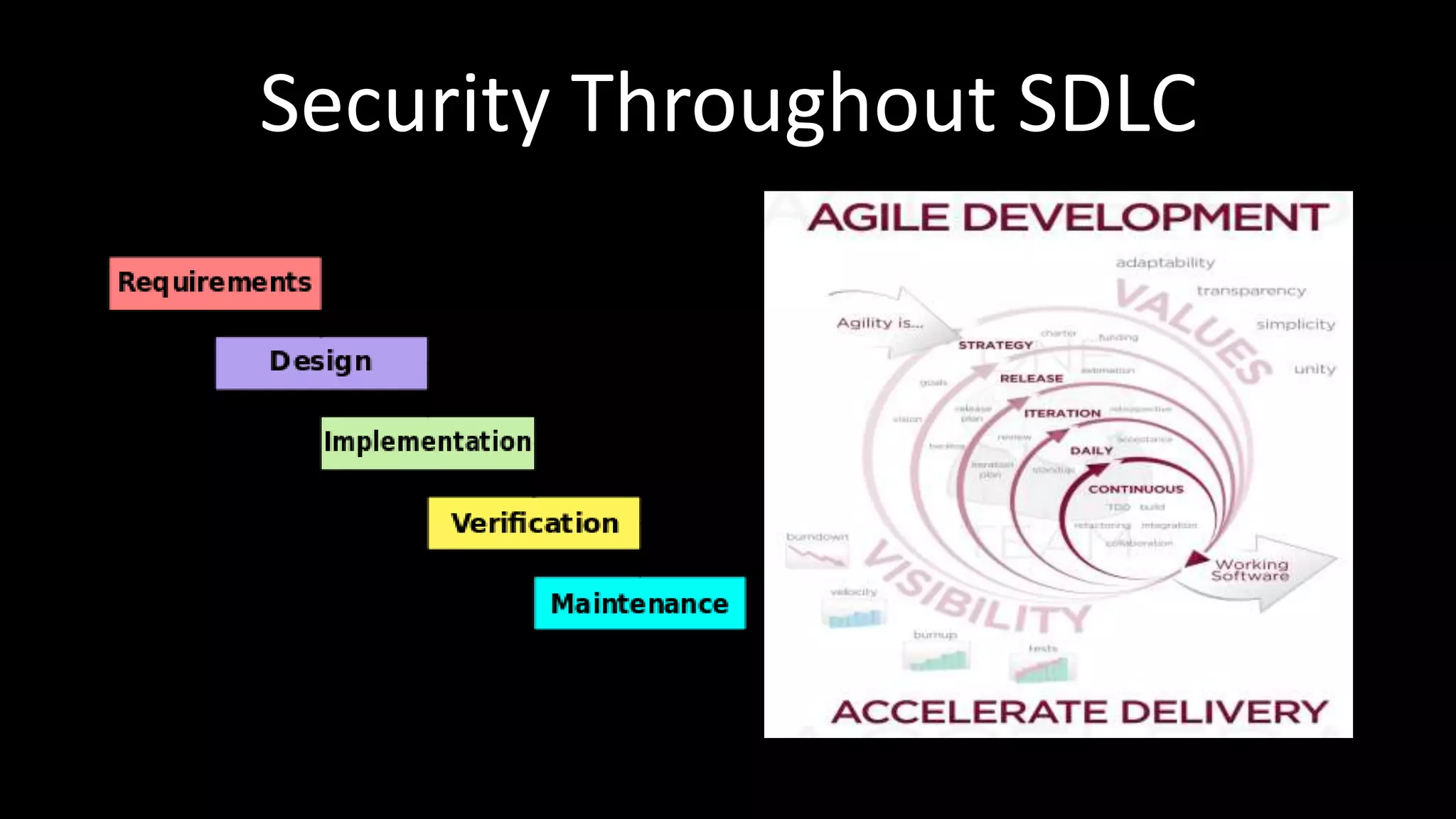
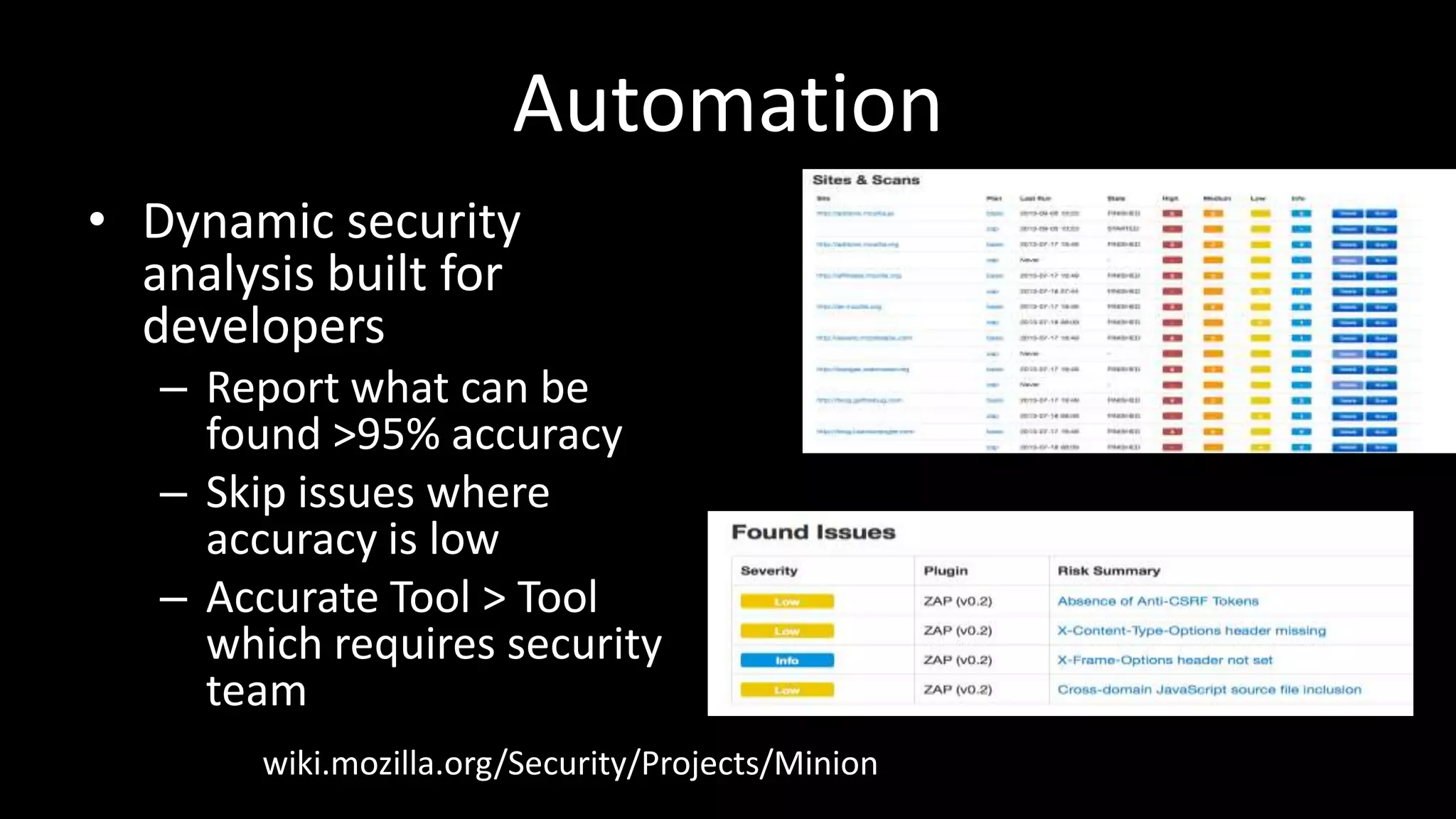
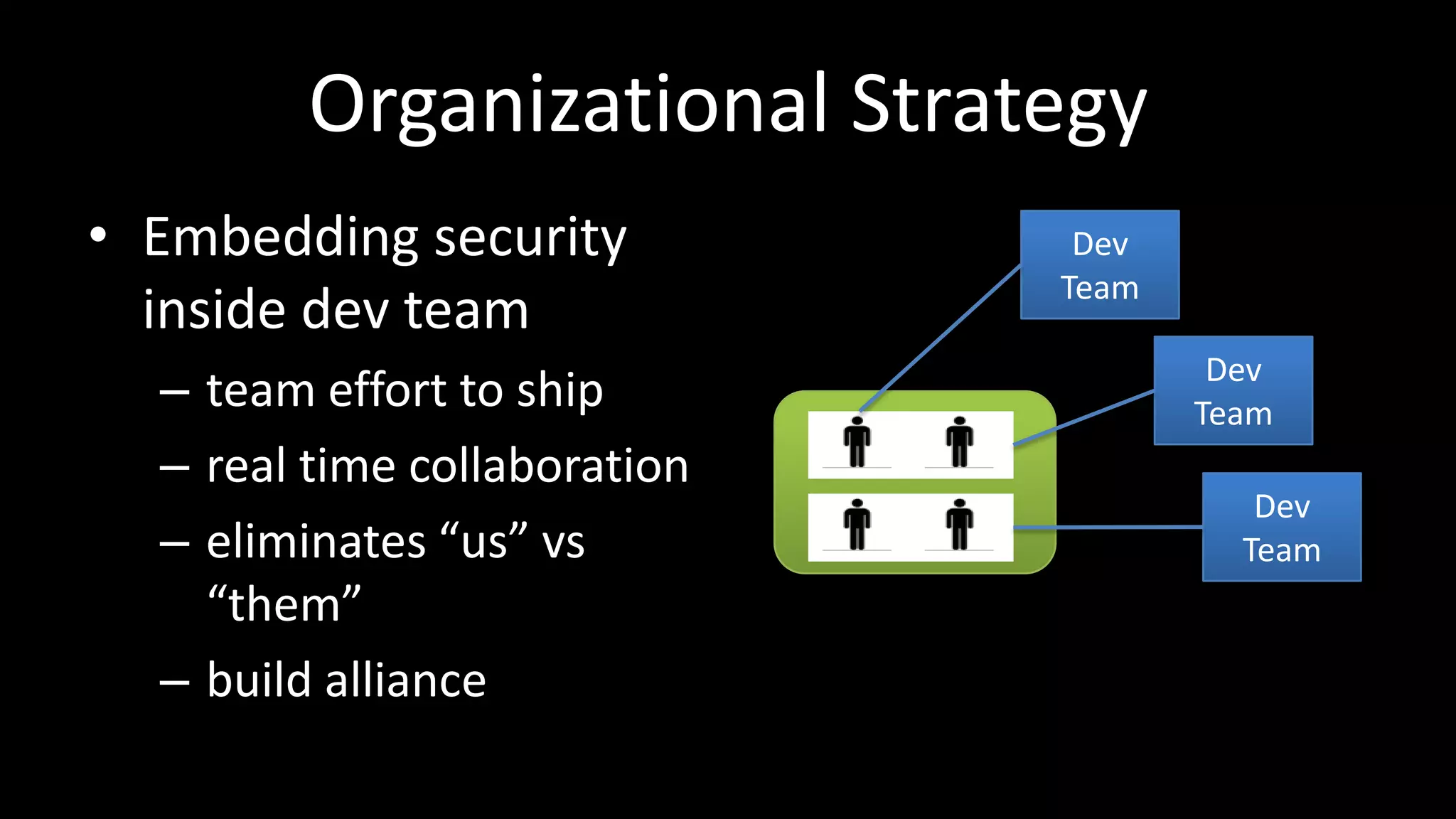
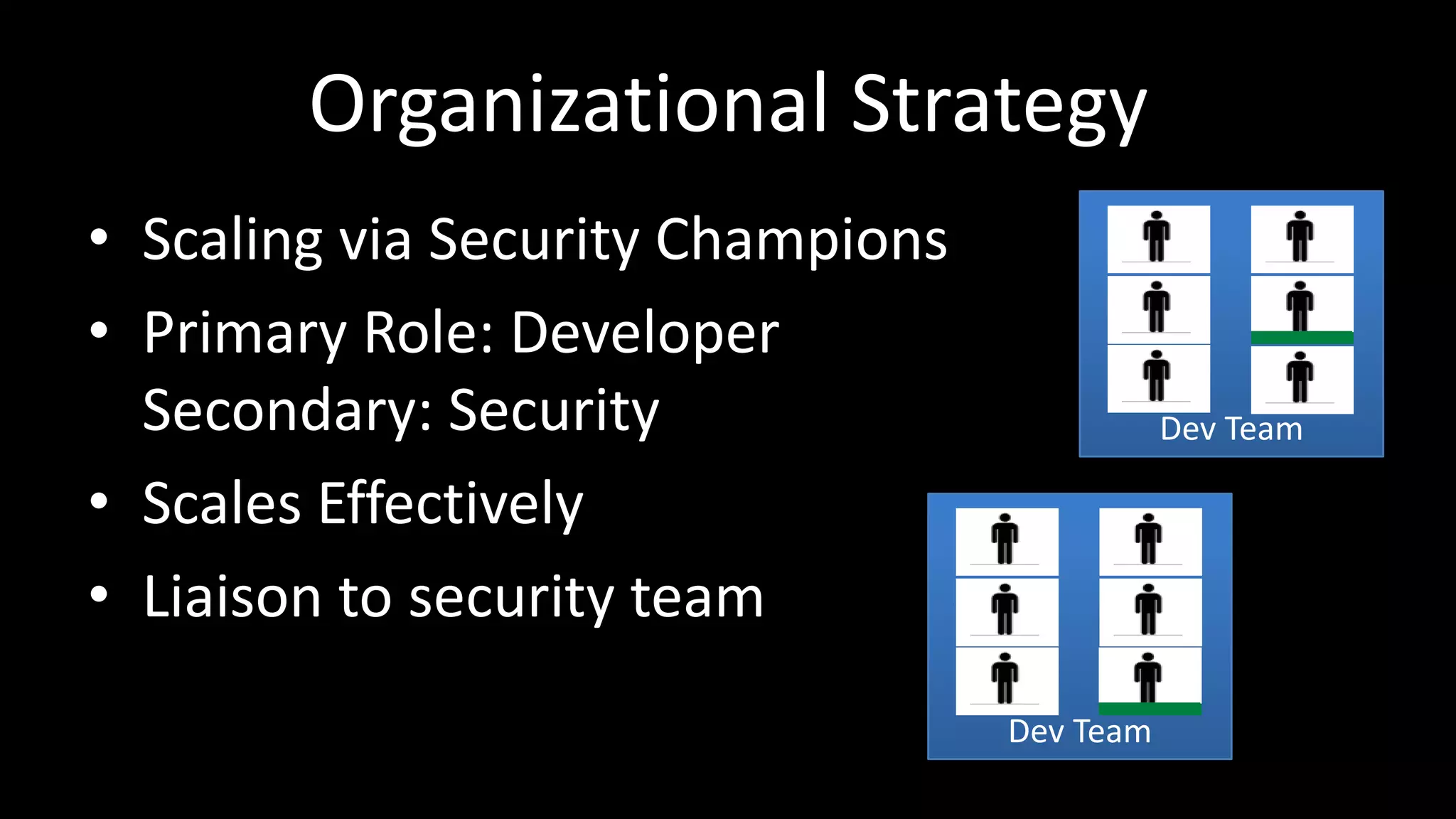
This document discusses how to scale web security programs to enable security at large organizations. It argues that relying solely on security professionals is not scalable, and that security must be embedded throughout the entire software development lifecycle (SDLC). It recommends automating as many security tasks as possible, such training developers, conducting static/dynamic analysis, and defending applications post-release. Security experts should focus on strategic tasks like risk management, architecture design, and tackling new problems. The key is gaining incremental security wins at each stage and building everything with scaling in mind.