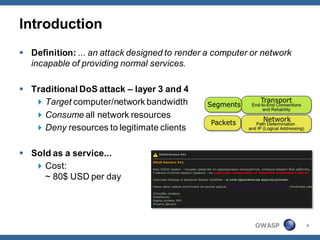
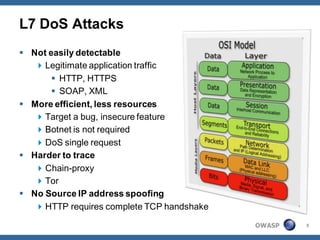
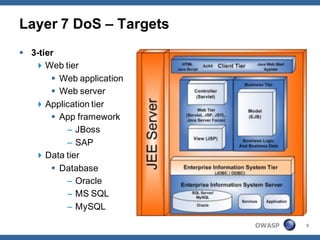
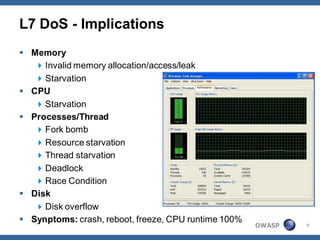
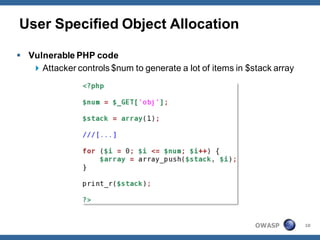
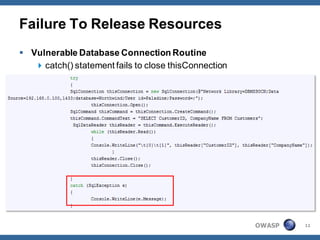
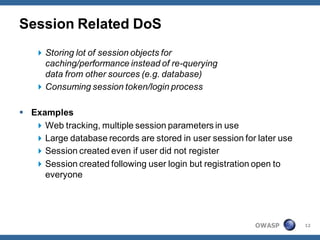
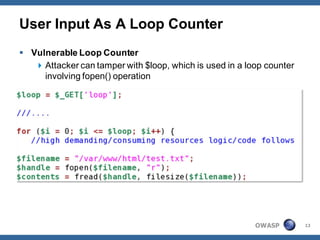
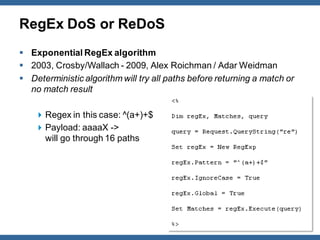
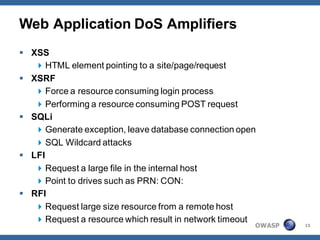
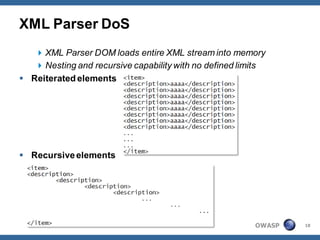
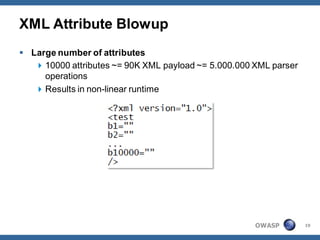
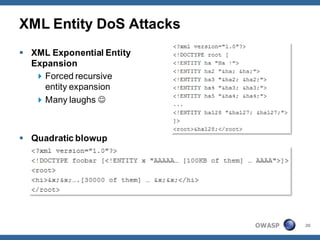
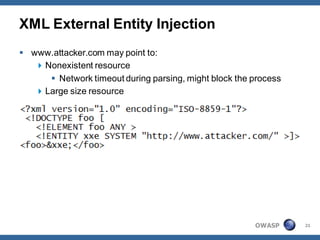
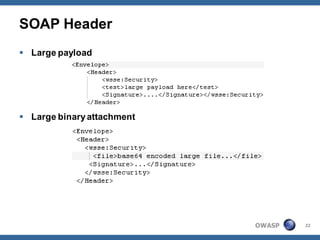
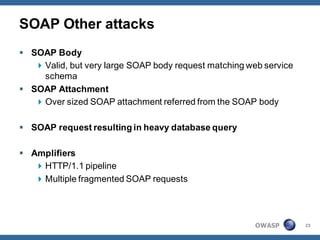
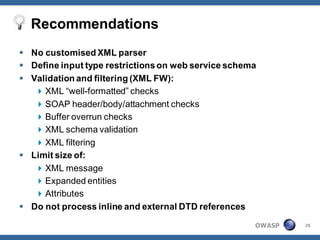
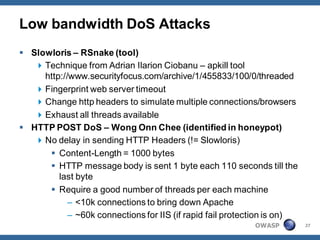
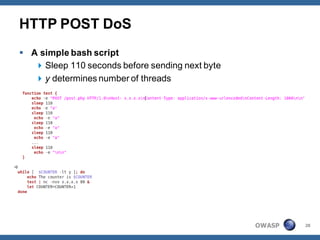
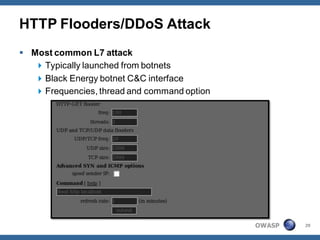
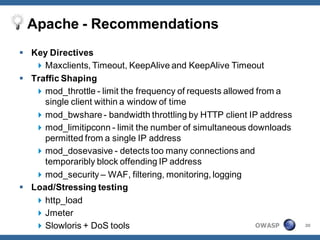
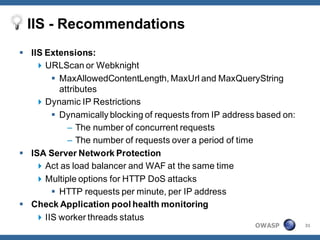
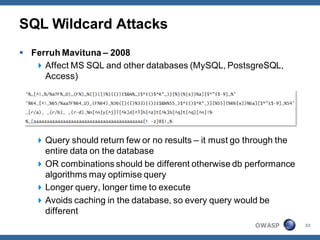
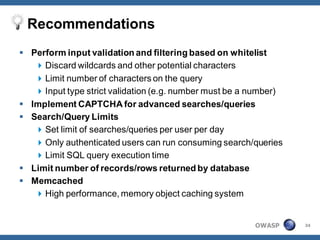
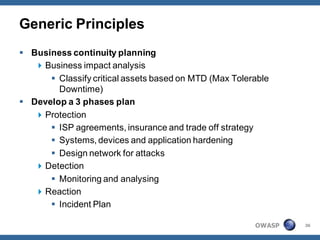
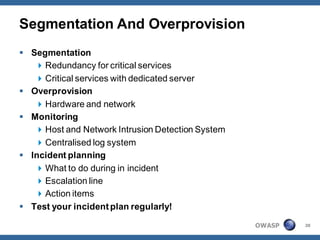
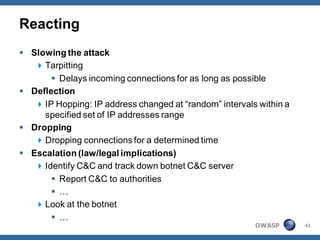
The document outlines strategies for defending against application layer Denial of Service (DoS) attacks, detailing various attack methods, implications, and root causes. It discusses different layers such as web applications, web servers, and databases, and provides recommendations for prevention and mitigation measures. Additionally, it emphasizes the importance of continuous monitoring, proper resource management, and security testing to safeguard against these attacks.