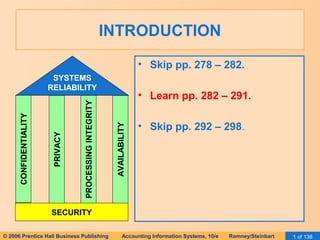
This document discusses processing integrity controls for accounting information systems. It describes five categories of controls: source data controls, data entry controls, processing controls, data transmission controls, and output controls. Within each category, specific controls are defined, such as forms design and pre-numbered forms for source data controls, and field checks and limit checks for data entry controls. Examples are provided of how these controls would be implemented in batch processing and online processing systems.