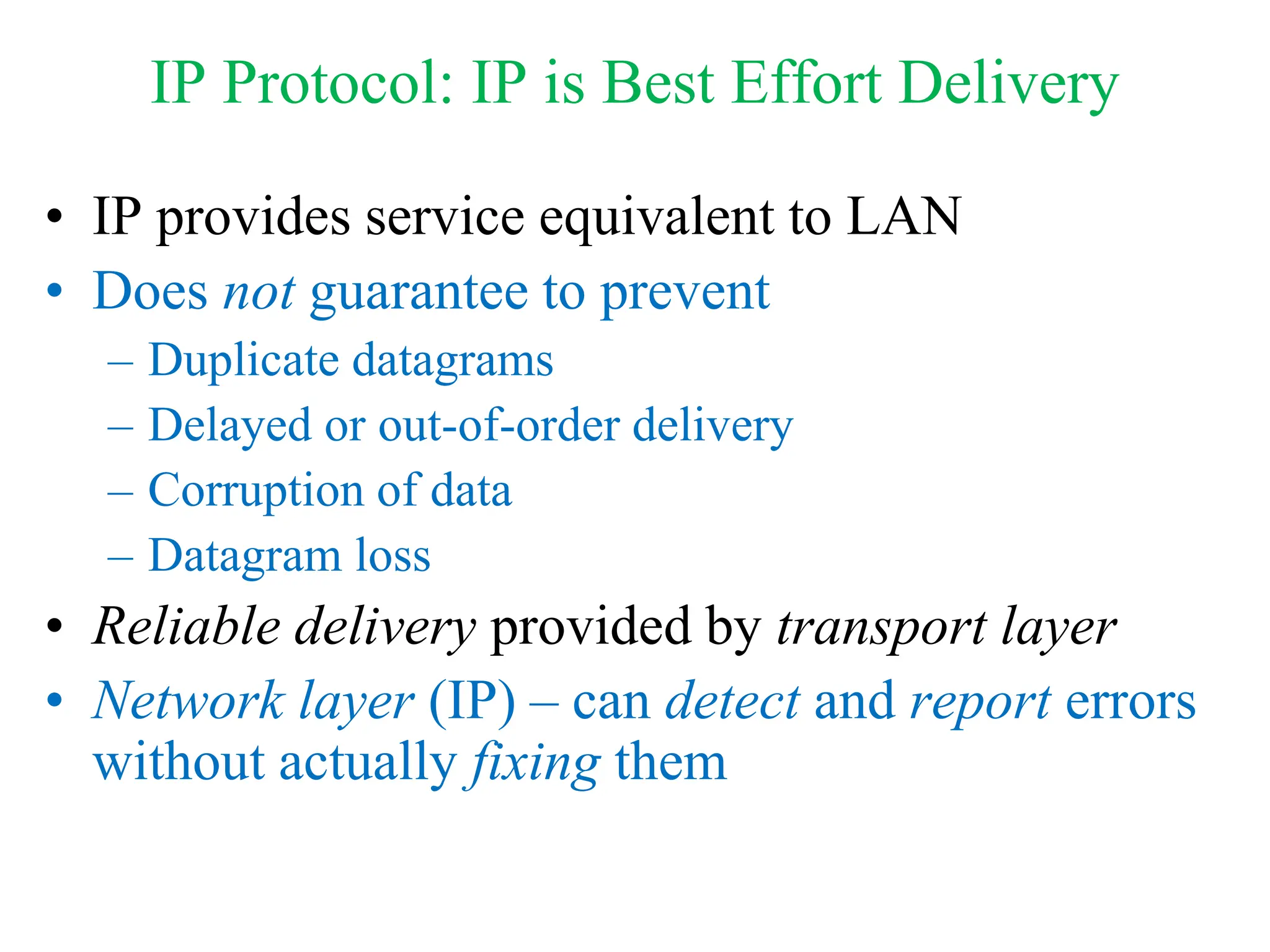
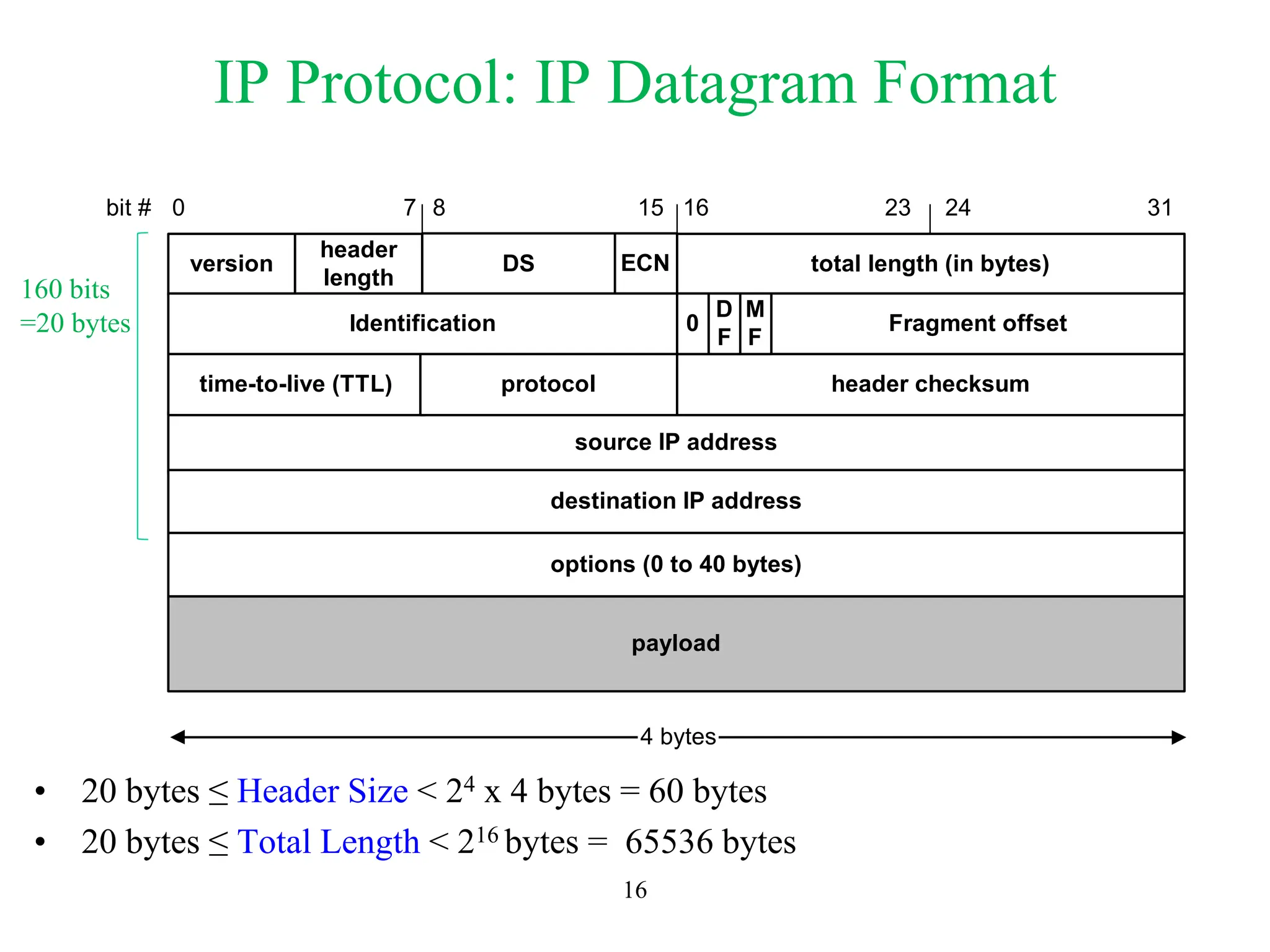
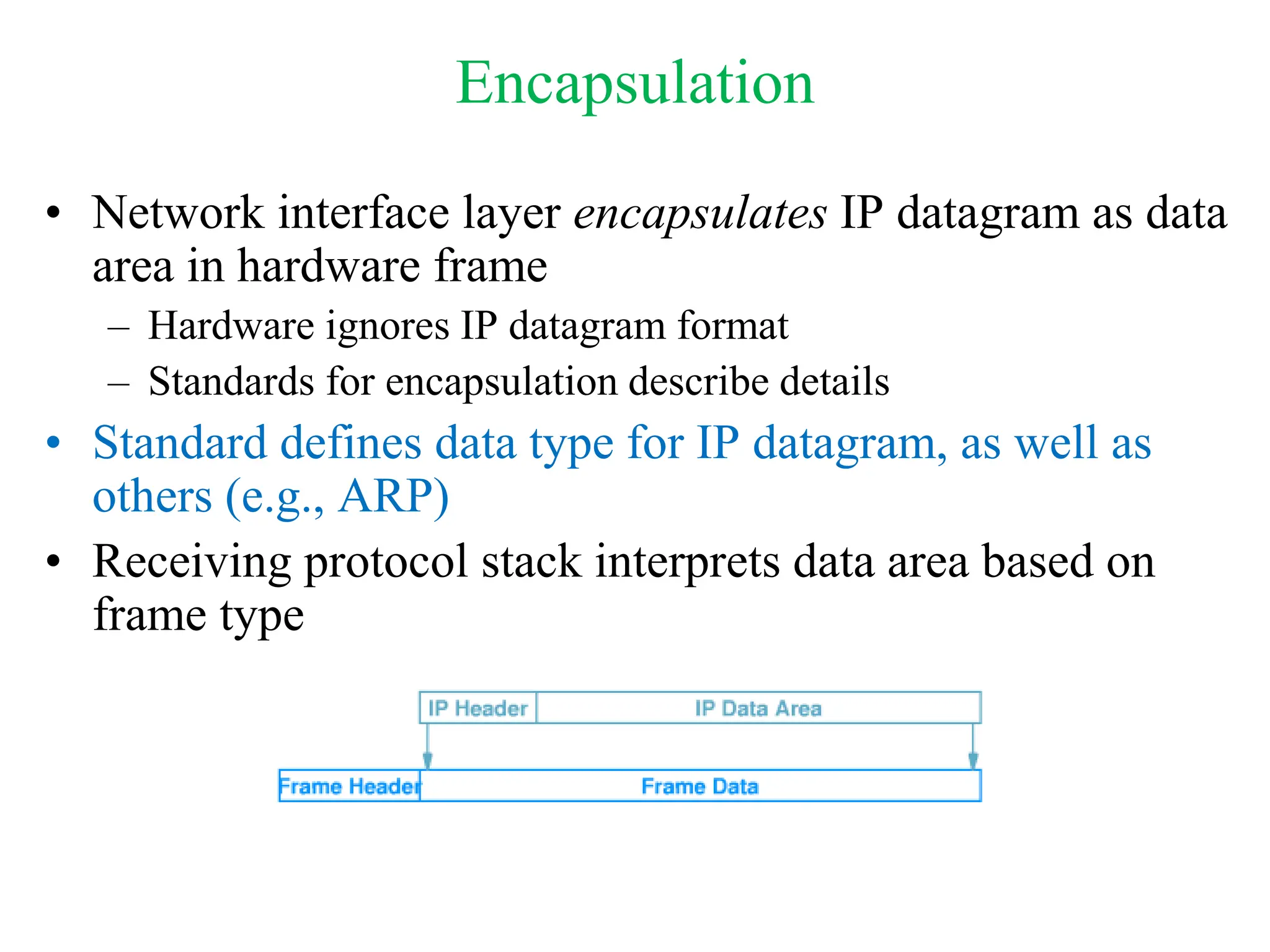
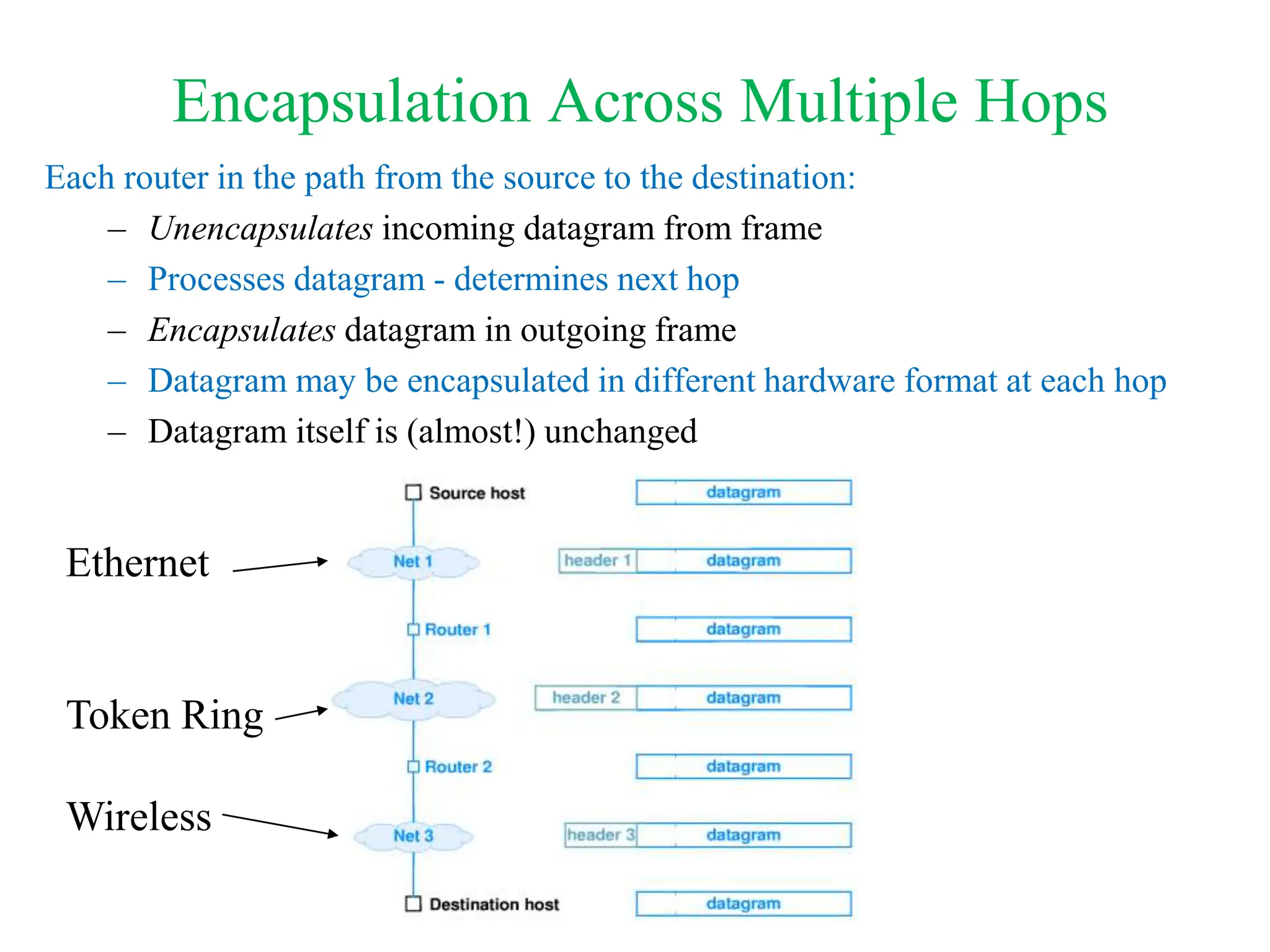
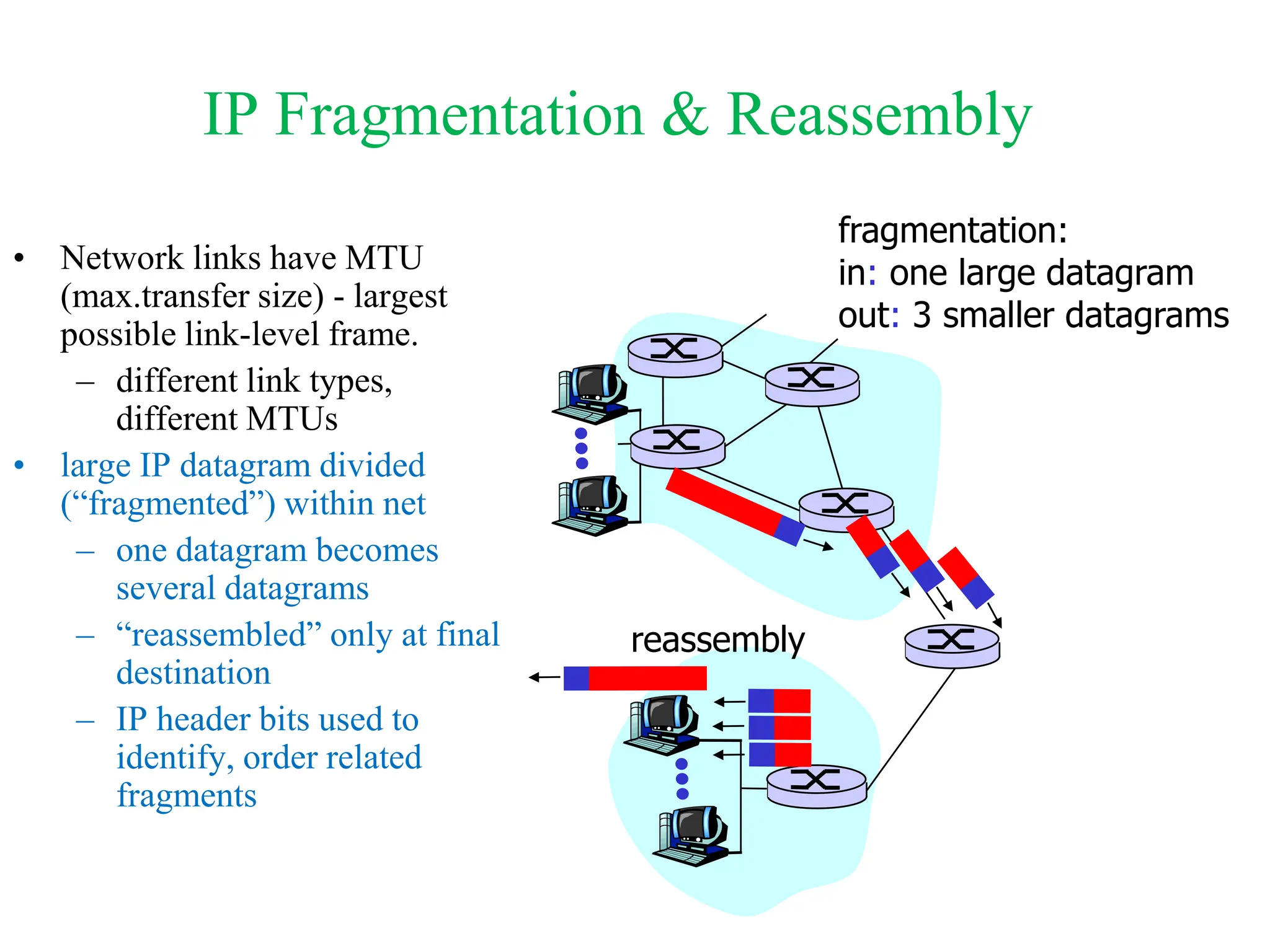
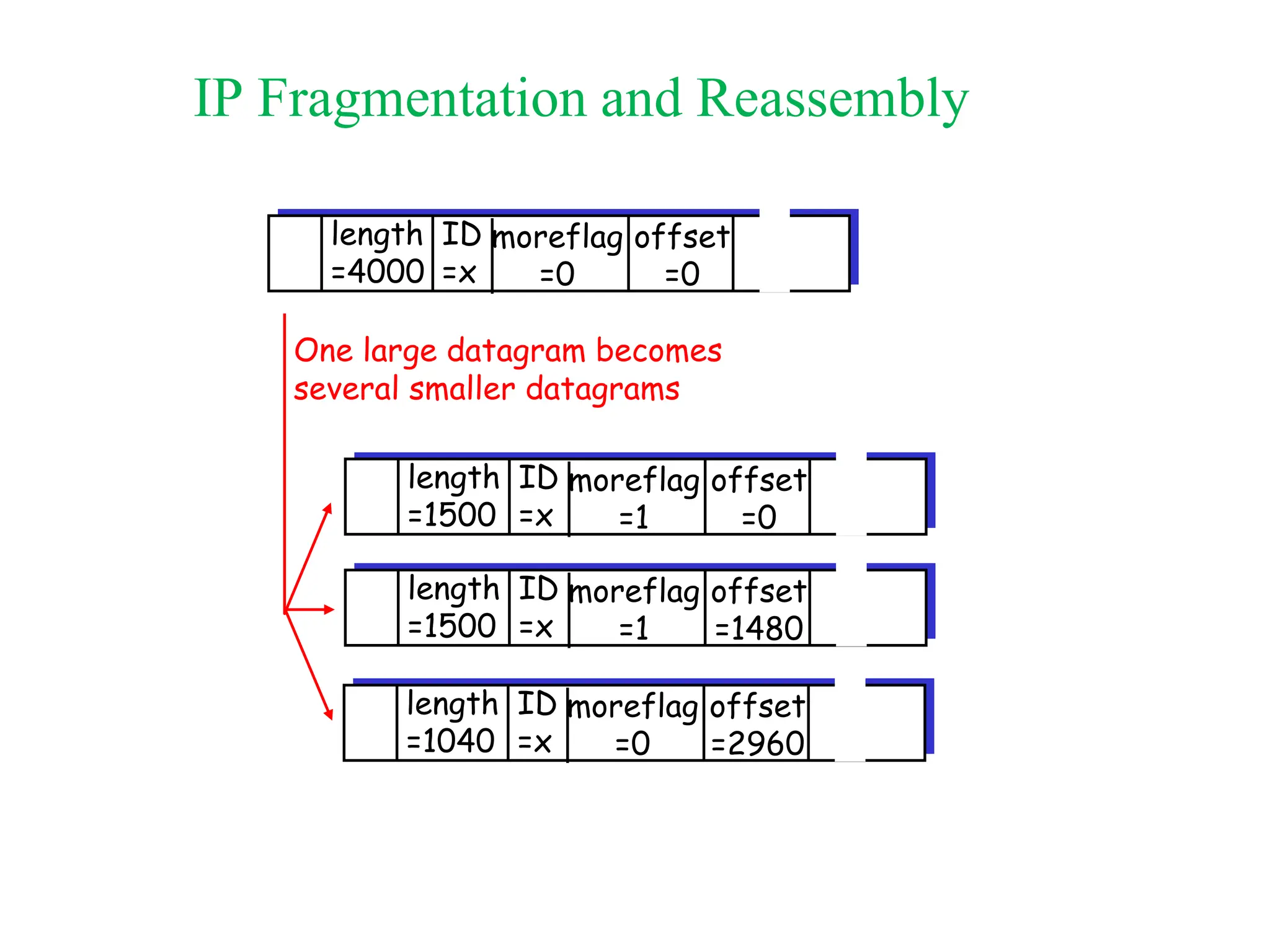
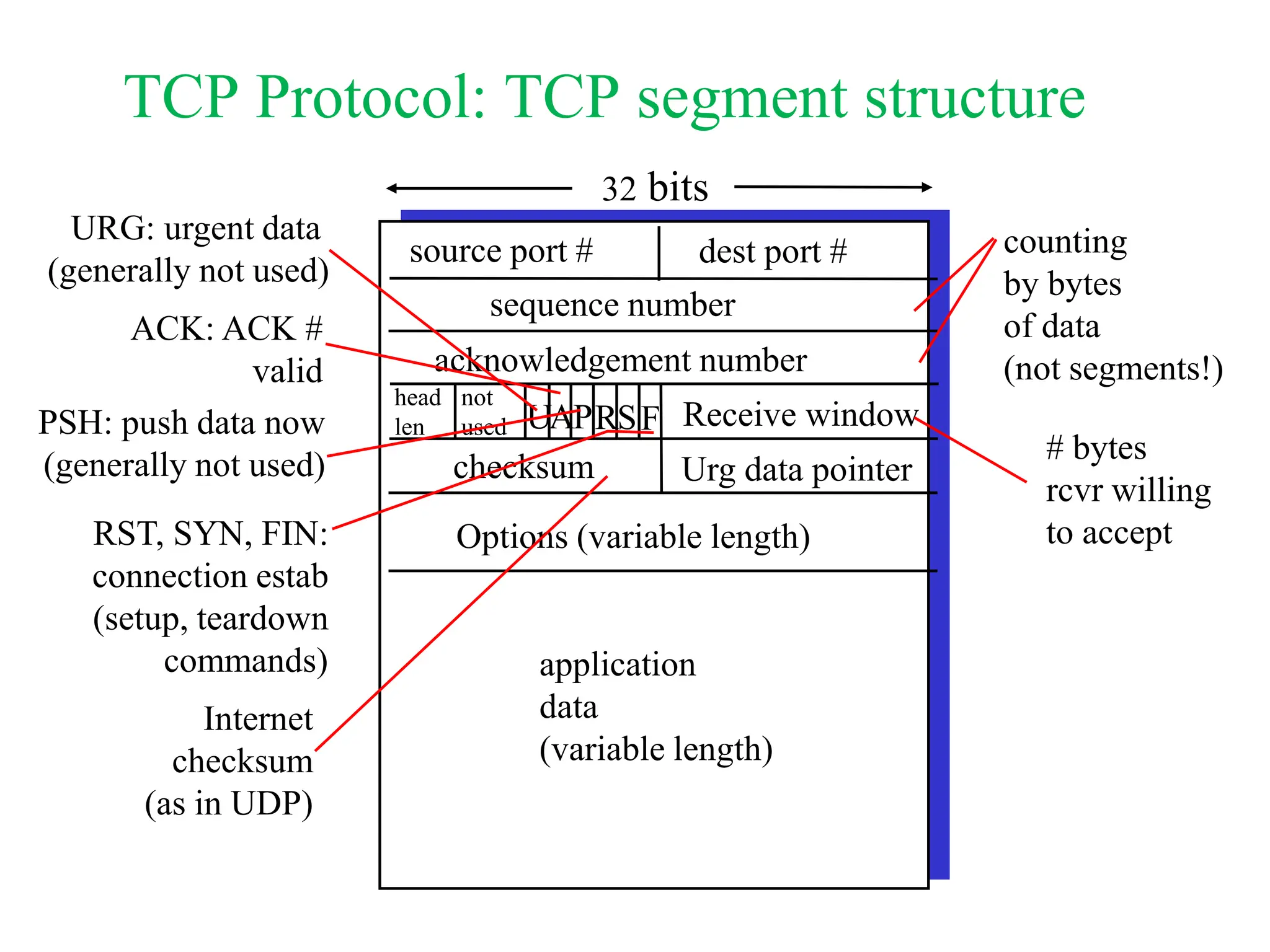
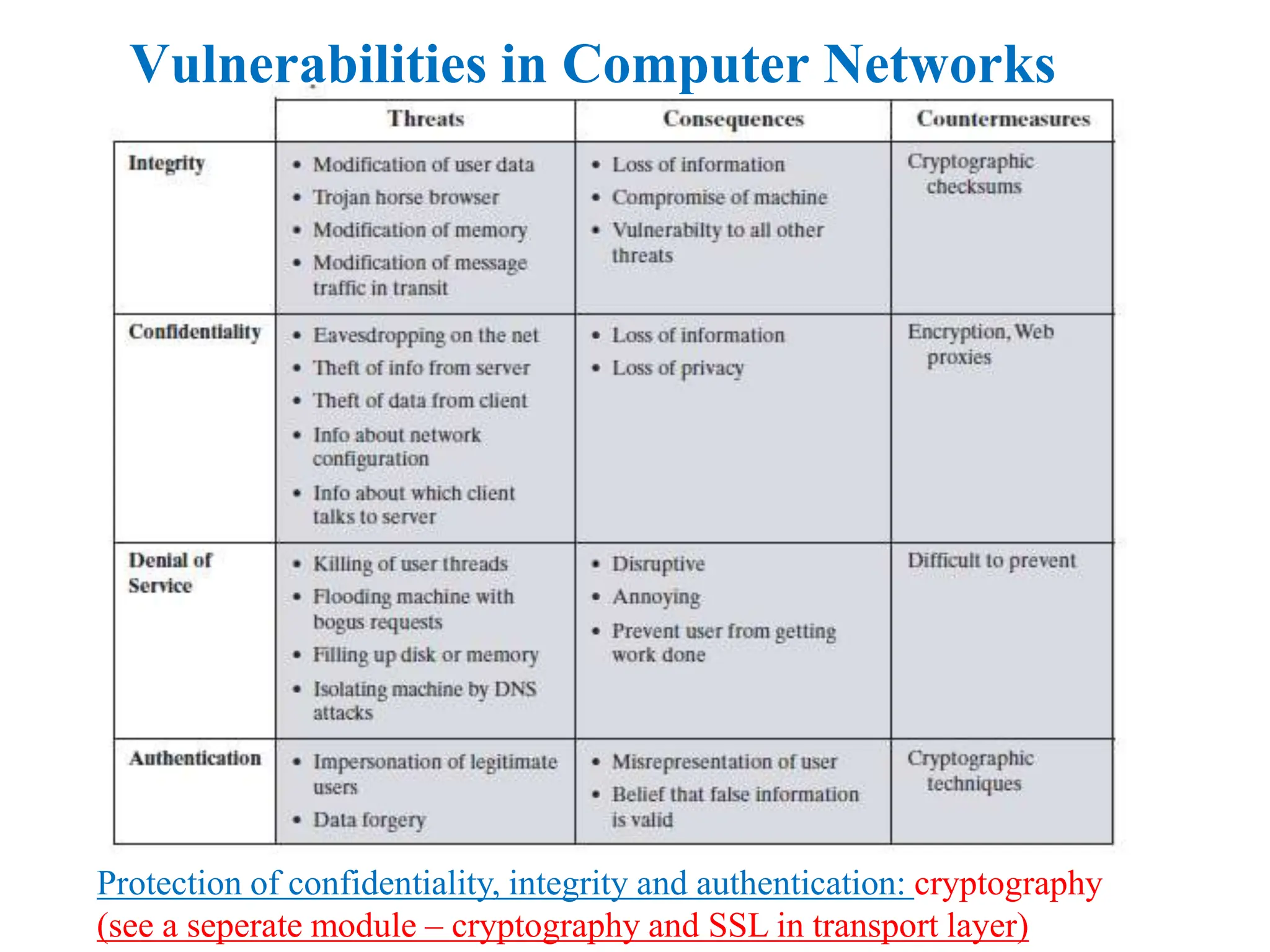
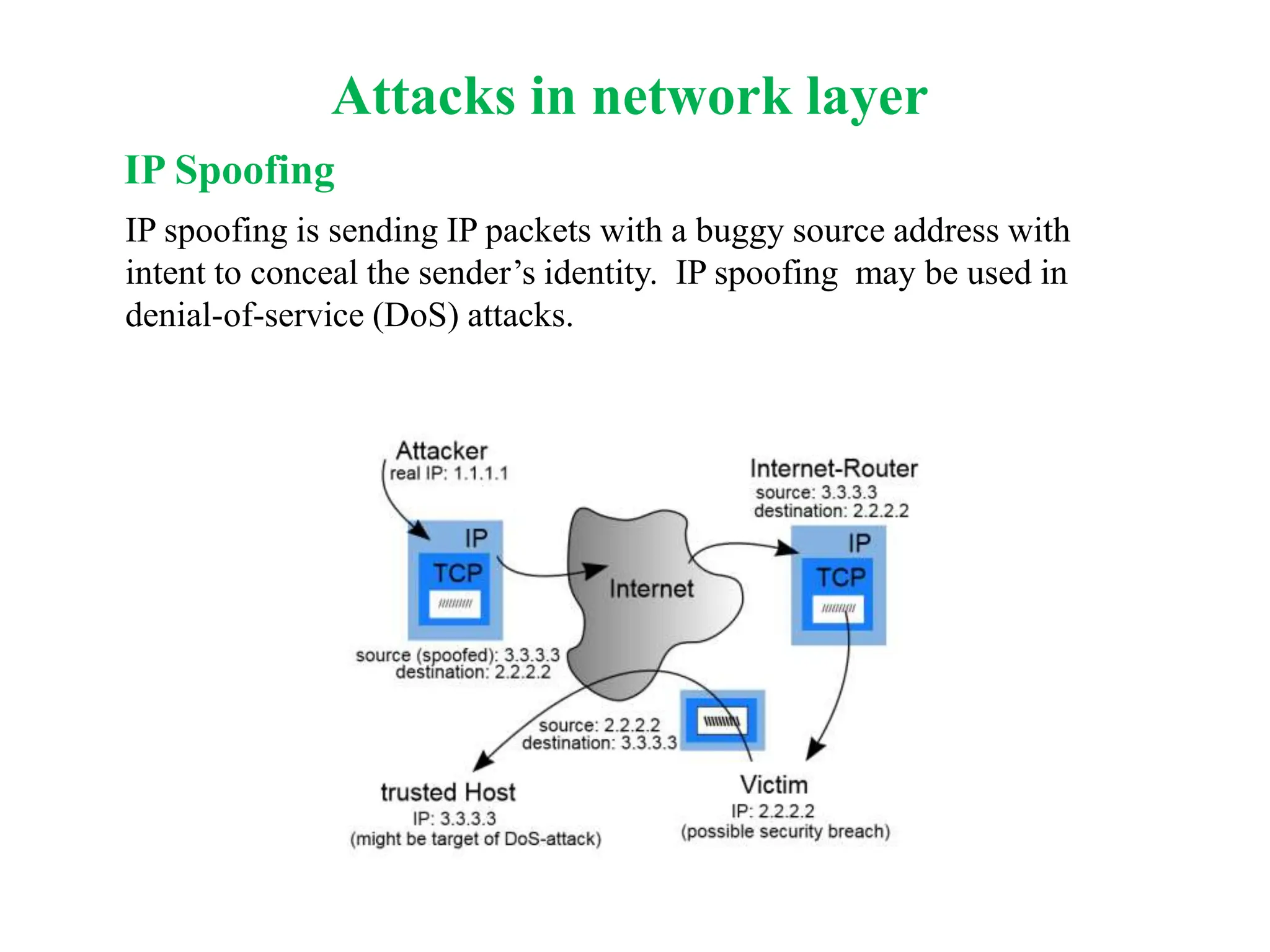
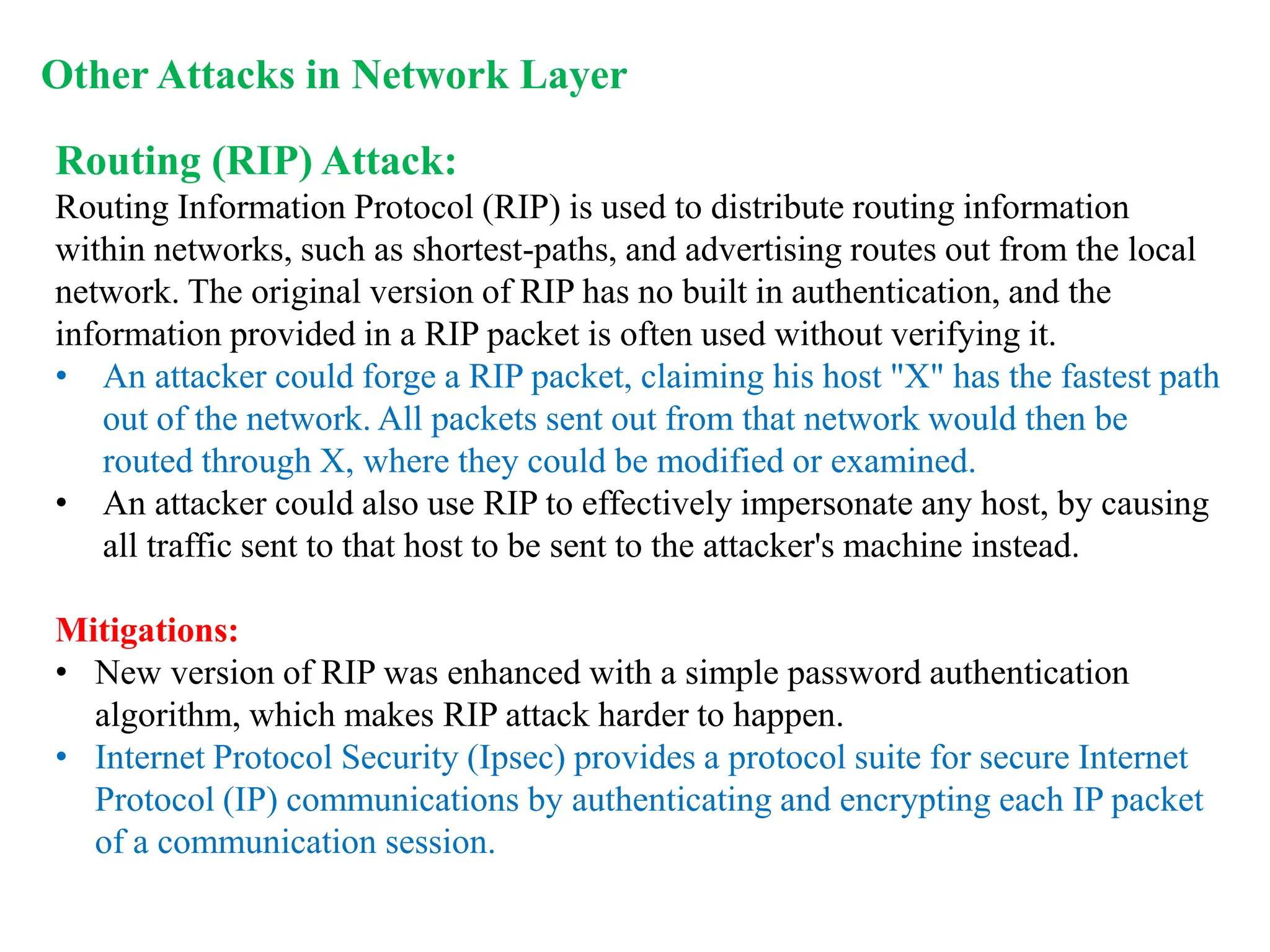
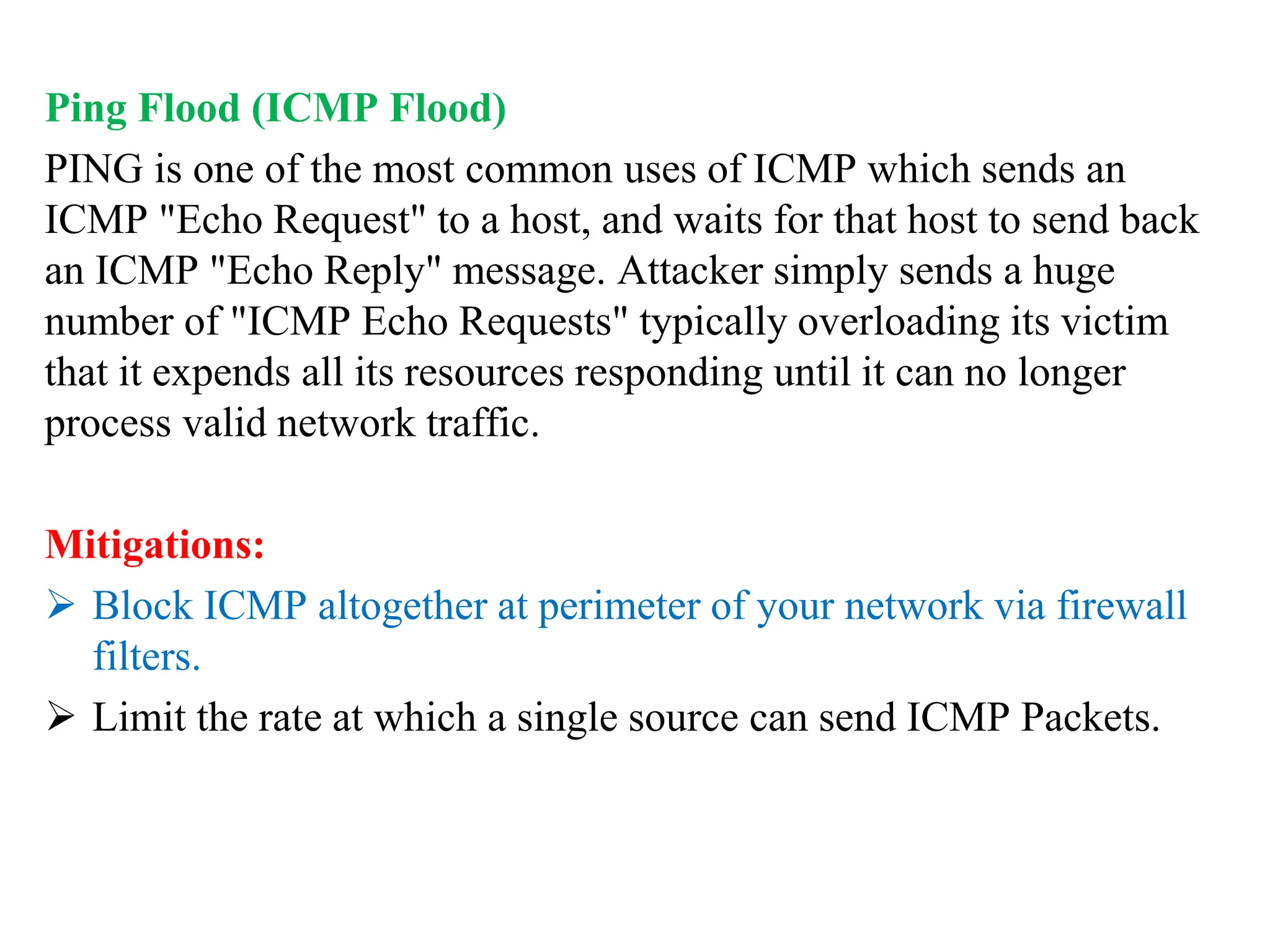
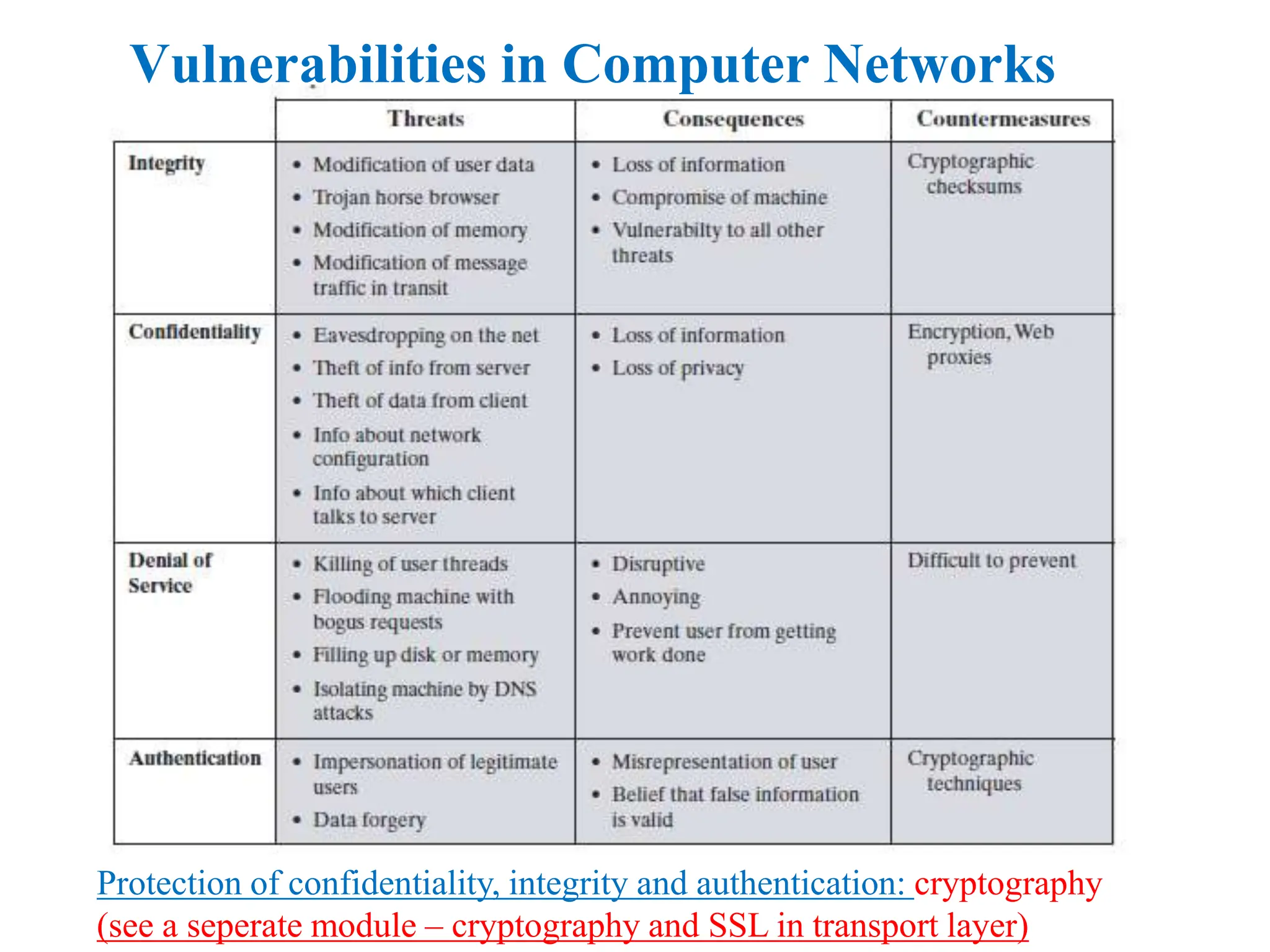
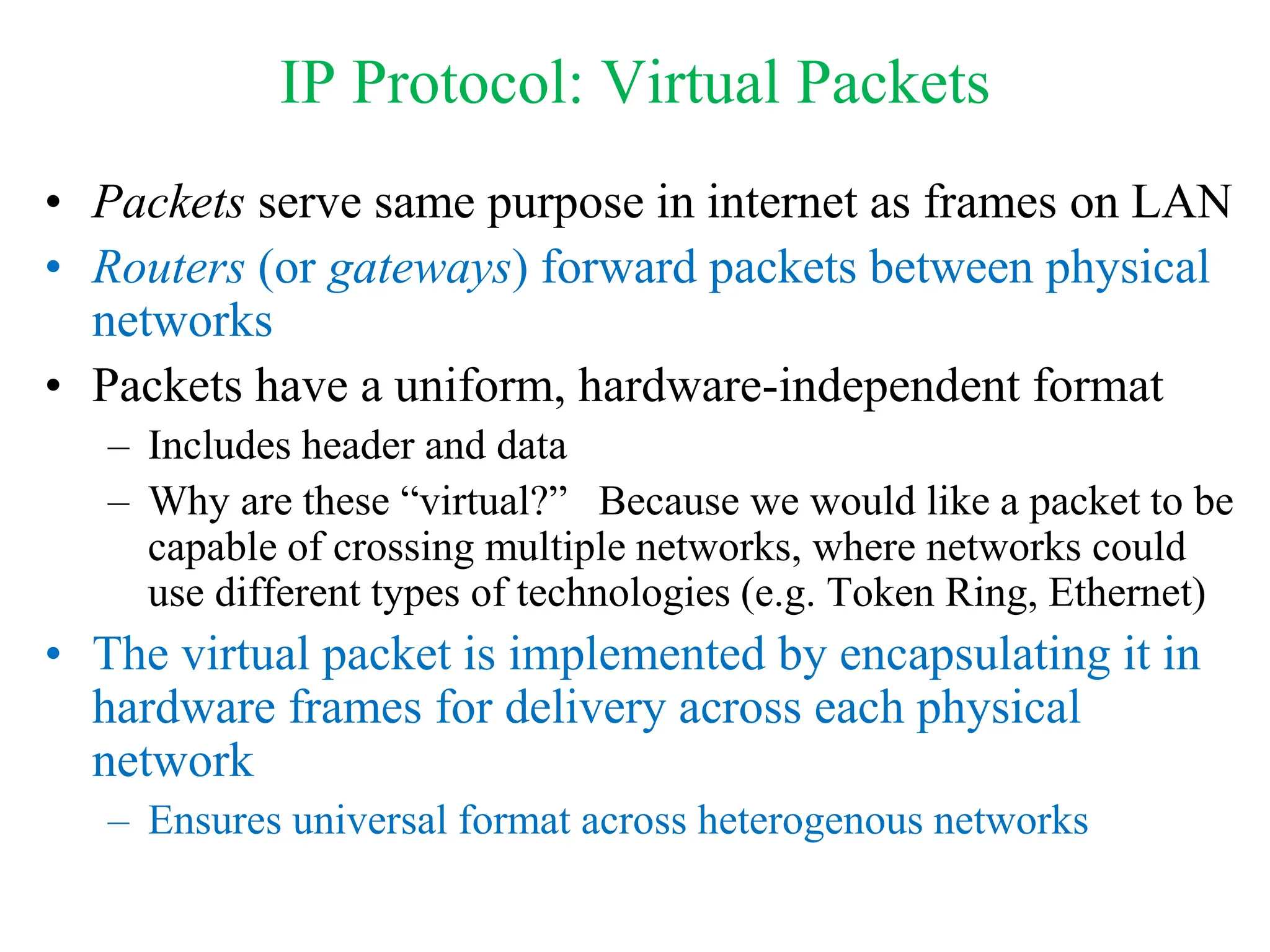
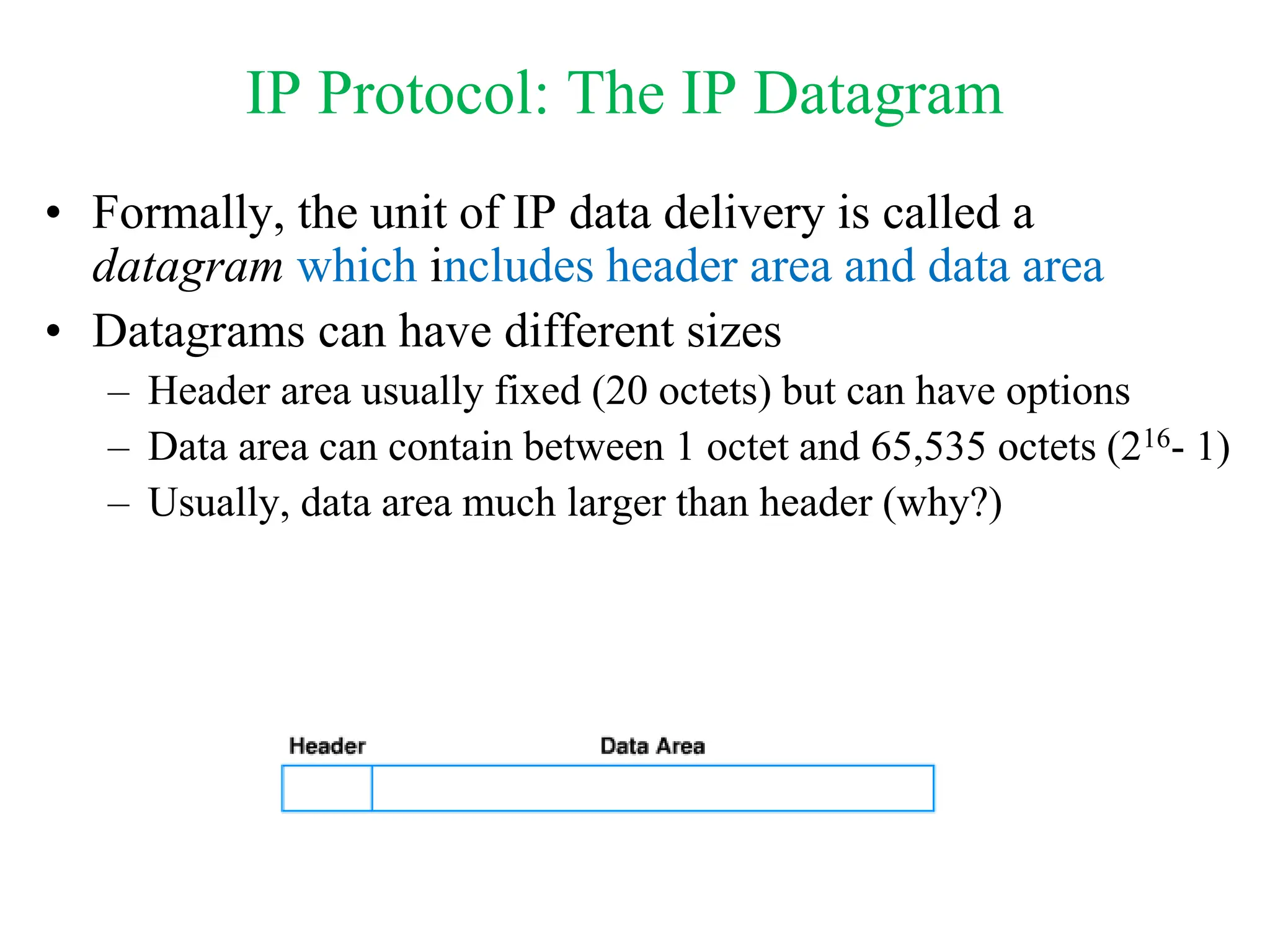
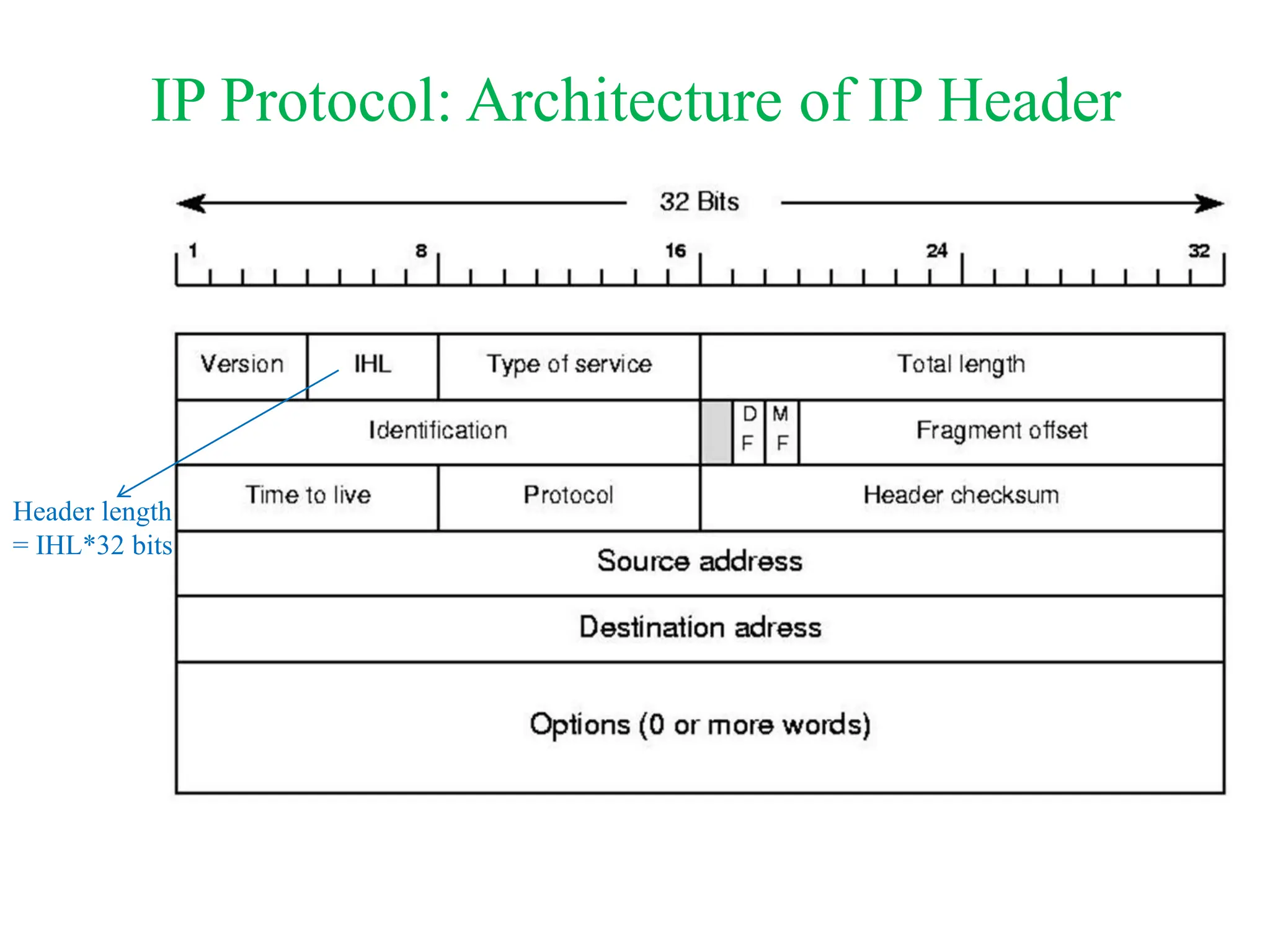
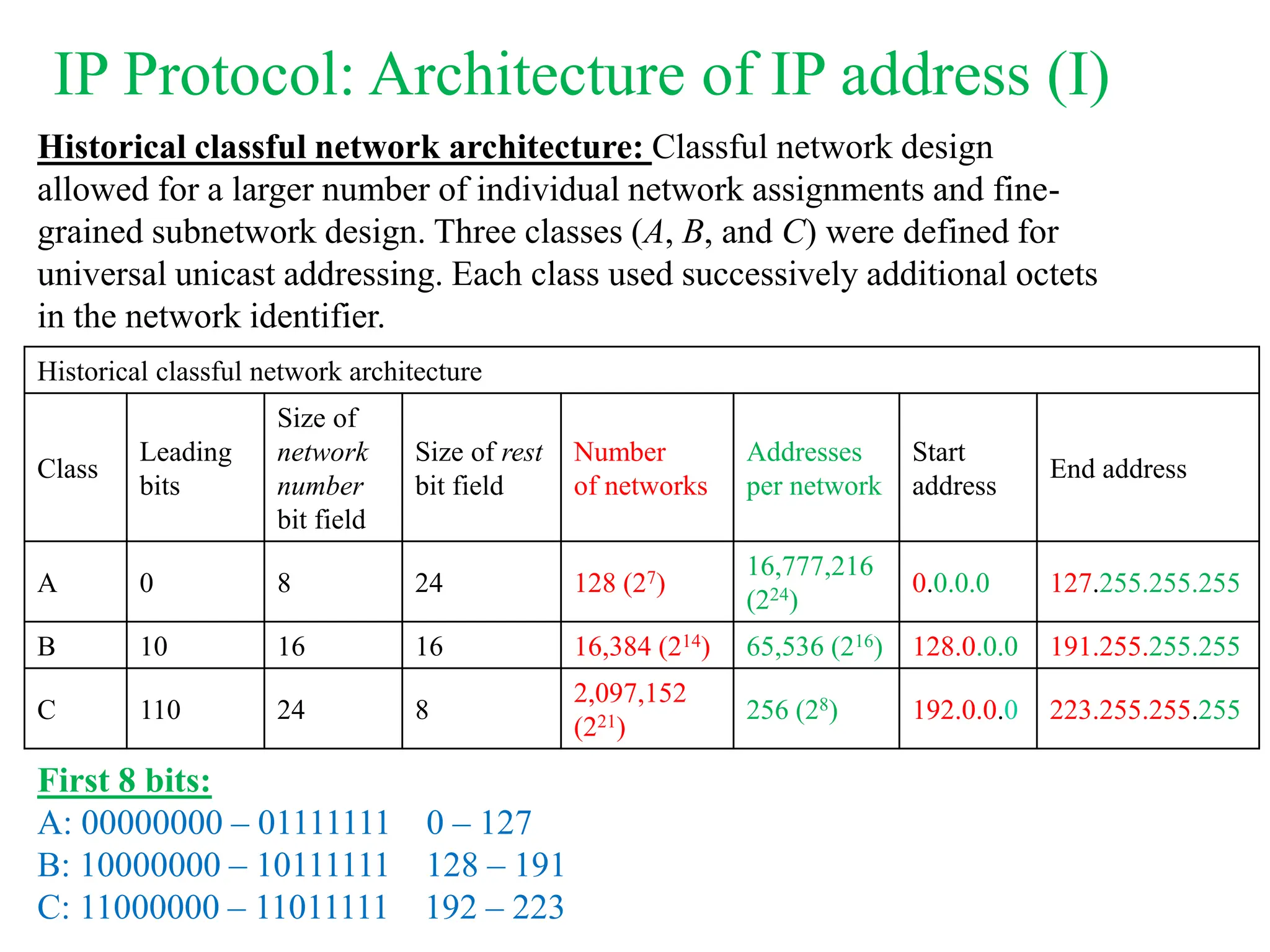
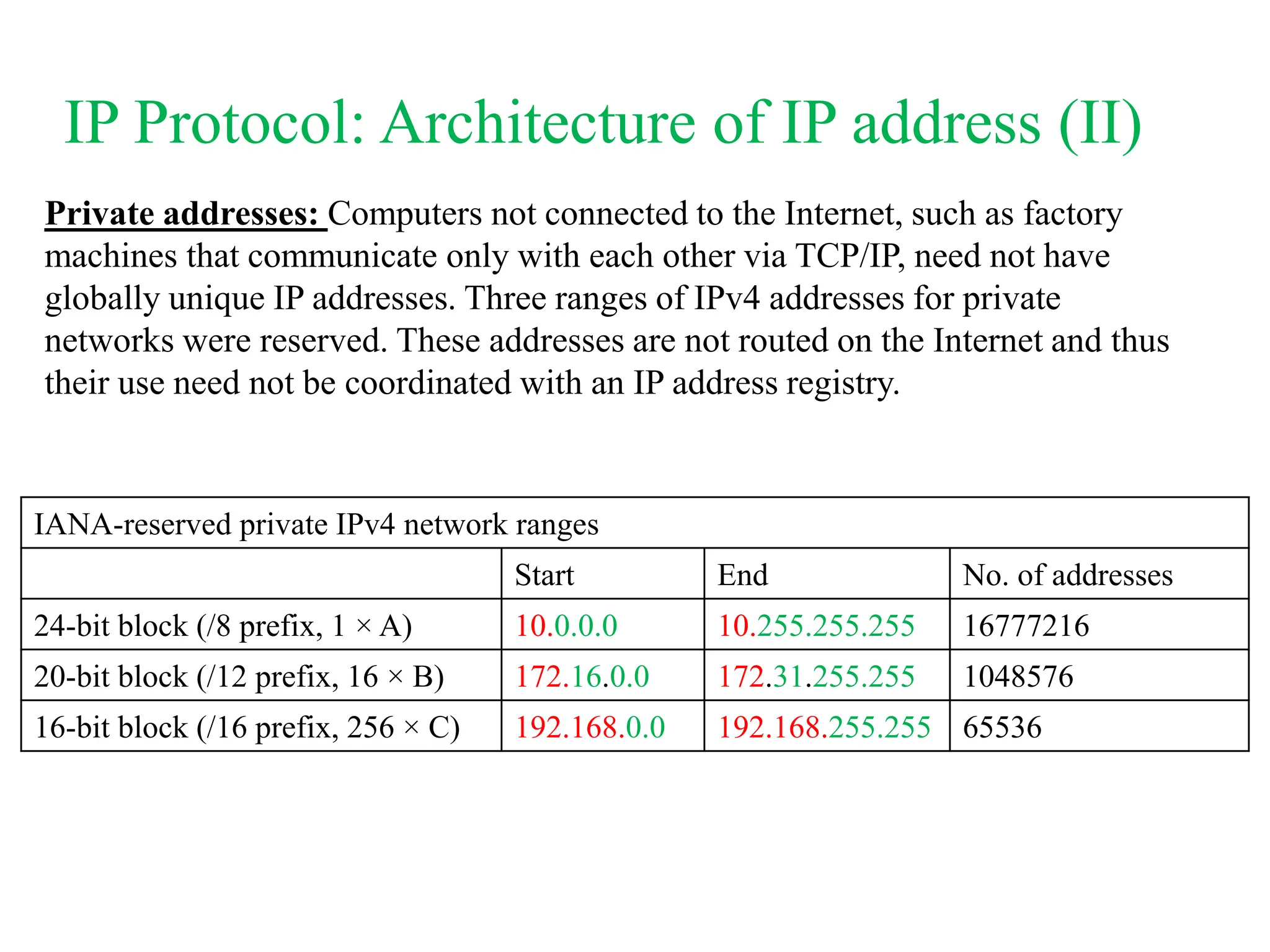
The document explores computer networks, focusing on vulnerabilities, particularly IP spoofing and Denial of Service (DoS) attacks. It covers network layer protocols, emphasizing IP architecture, transport protocols, and security measures against attacks such as routing protocol forgery and ICMP-based DoS. The document suggests various mitigation strategies, including access control lists, encryption, and proper configuration of network devices to enhance security.

![IP Protocol: Address Masks
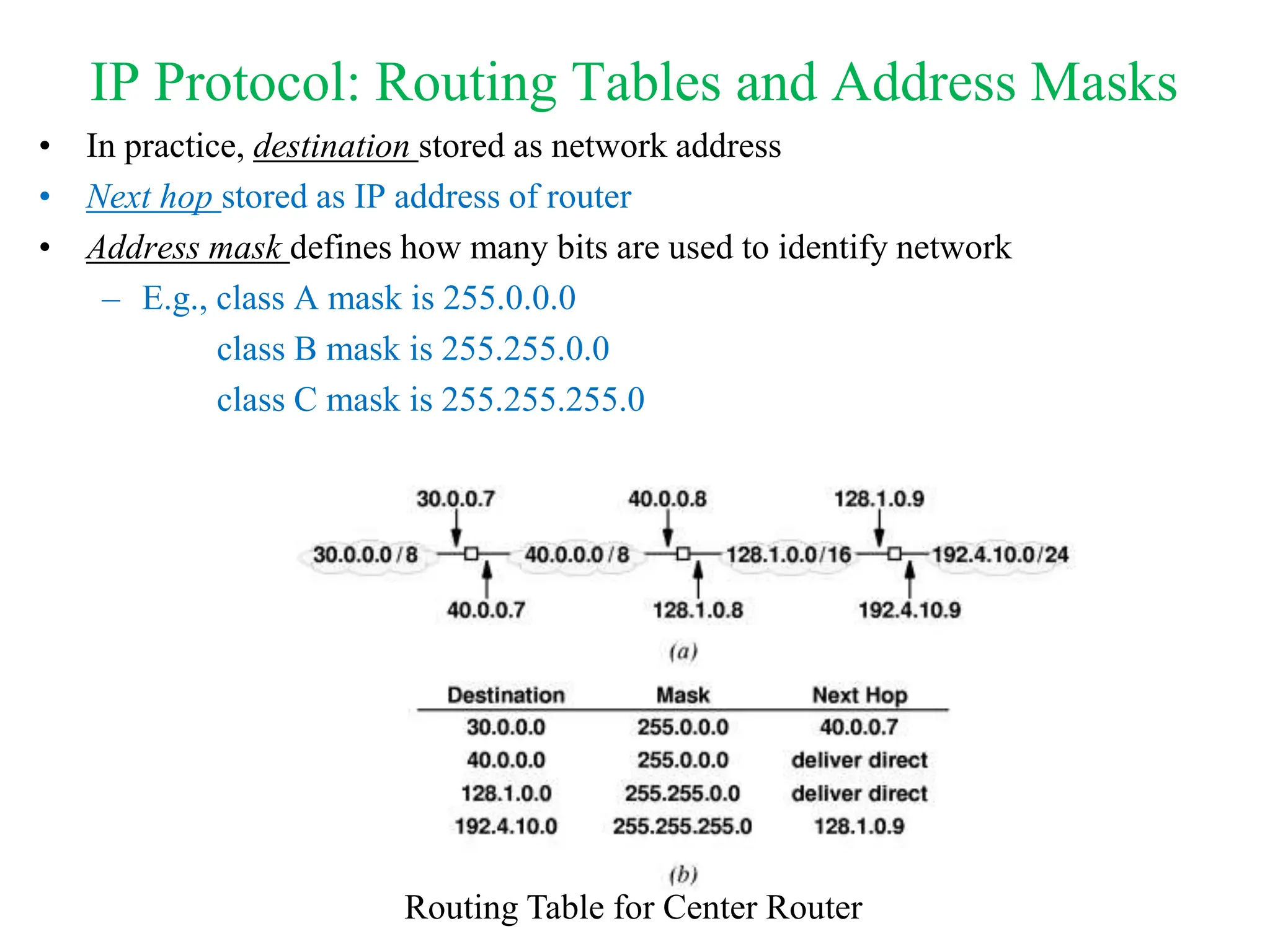
• To identify destination network, apply address mask to destination address and
compare to network address in routing table by using Boolean AND
if ((Mask[i] & D) == Dest[i]) forward to NextHop[i]
• Consider routing table at 128.1.15.26. Deliver a datagram to D = 192.4.10.9
Mask[1]&D = 255.0.0.0&192.4.10.9 = 192.0.0.0 ≠ Dest[1]
Mask[2]&D = 255.0.0.0&192.4.10.9 = 192.0.0.0 ≠ Dest[2]
Mask[3]&D = 255.255.0.0&192.4.10.9 = 192.4.0.0 ≠ Dest[3]
Mask[4]&D = 255.255.255.0&192.4.10.9 = 192.4.10.0 = Dest[4];
therefore forward the datagram to NextHop[4] (=128.1.0.9)](https://image.slidesharecdn.com/computernetworksecurity-240501043614-235a6189/75/210202021018701-suratNetworkSecurity-ppt-13-2048.jpg)