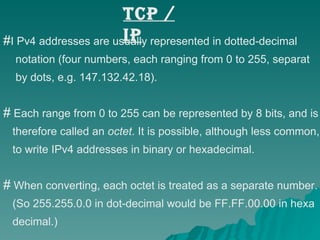
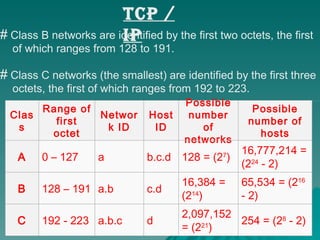
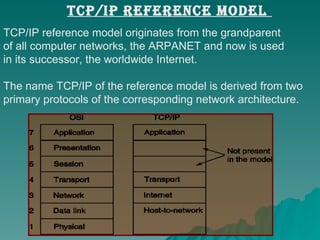
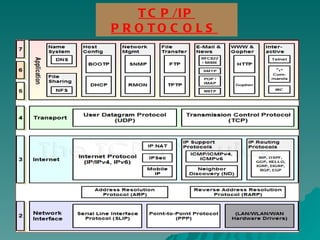
TCP/IP is a set of communication protocols developed in the 1970s to connect dissimilar networks. It includes the two main protocols TCP and IP. TCP functions at the transport layer to provide reliable data transmission through connections. IP functions at the network layer to route packets by addressing each device with a unique IP address. TCP/IP is commonly used today and supports communication over the internet through protocols like HTTP, FTP, and SMTP.