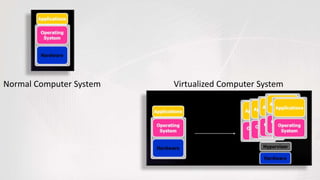
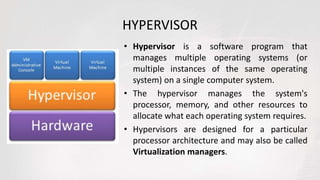
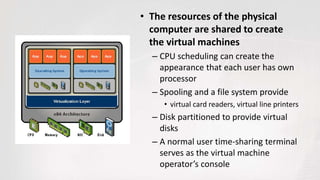
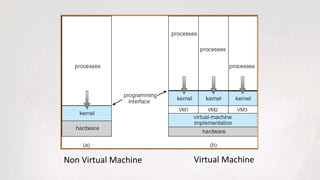
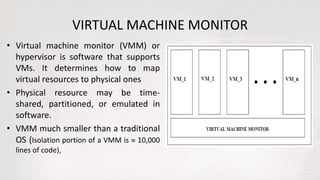
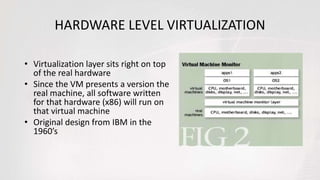
Virtual machines allow multiple operating systems to run simultaneously on the same physical hardware through virtualization. A hypervisor manages access to physical resources and allocates what each virtual machine needs, providing isolation. This allows different operating systems, applications, and workloads to be securely isolated while sharing the same underlying hardware resources.