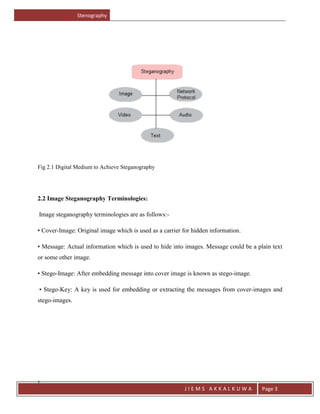
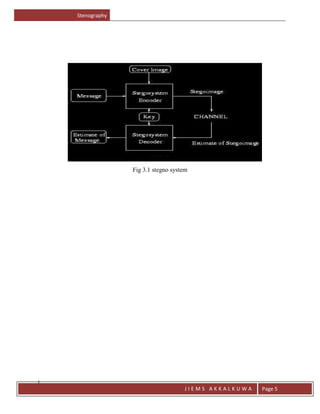
The document provides an introduction to stenography, which is the ancient art of hiding messages so they are not detectable. It discusses how stenography aims to hide the existence of a message, while cryptography scrambles it so it cannot be understood. It then reviews traditional stenography methods used before digital means, and outlines some key terms like cover image and stego image. The document proposes an edge adaptive scheme for digital image stenography and discusses advantages like messages not attracting attention. It also reviews some applications of stenography like digital watermarking and discusses the technique's future scope.