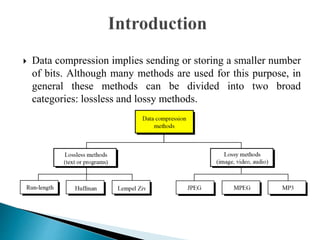
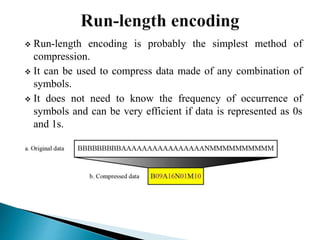
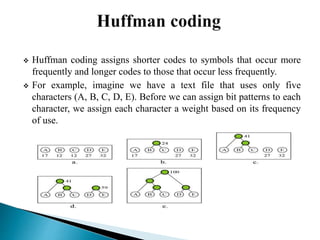
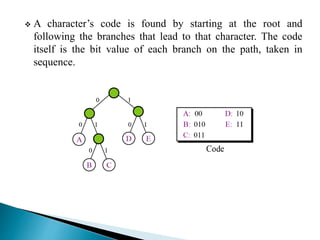
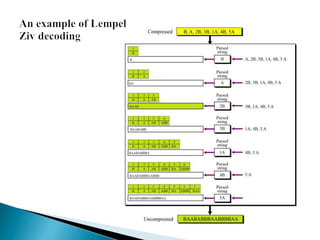
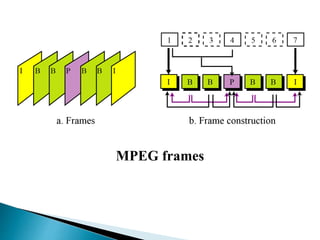
There are two categories of data compression methods: lossless and lossy. Lossless methods preserve the integrity of the data by using compression and decompression algorithms that are exact inverses, while lossy methods allow for data loss. Common lossless methods include run-length encoding and Huffman coding, while lossy methods like JPEG, MPEG, and MP3 are used to compress images, video, and audio by removing imperceptible or redundant data.