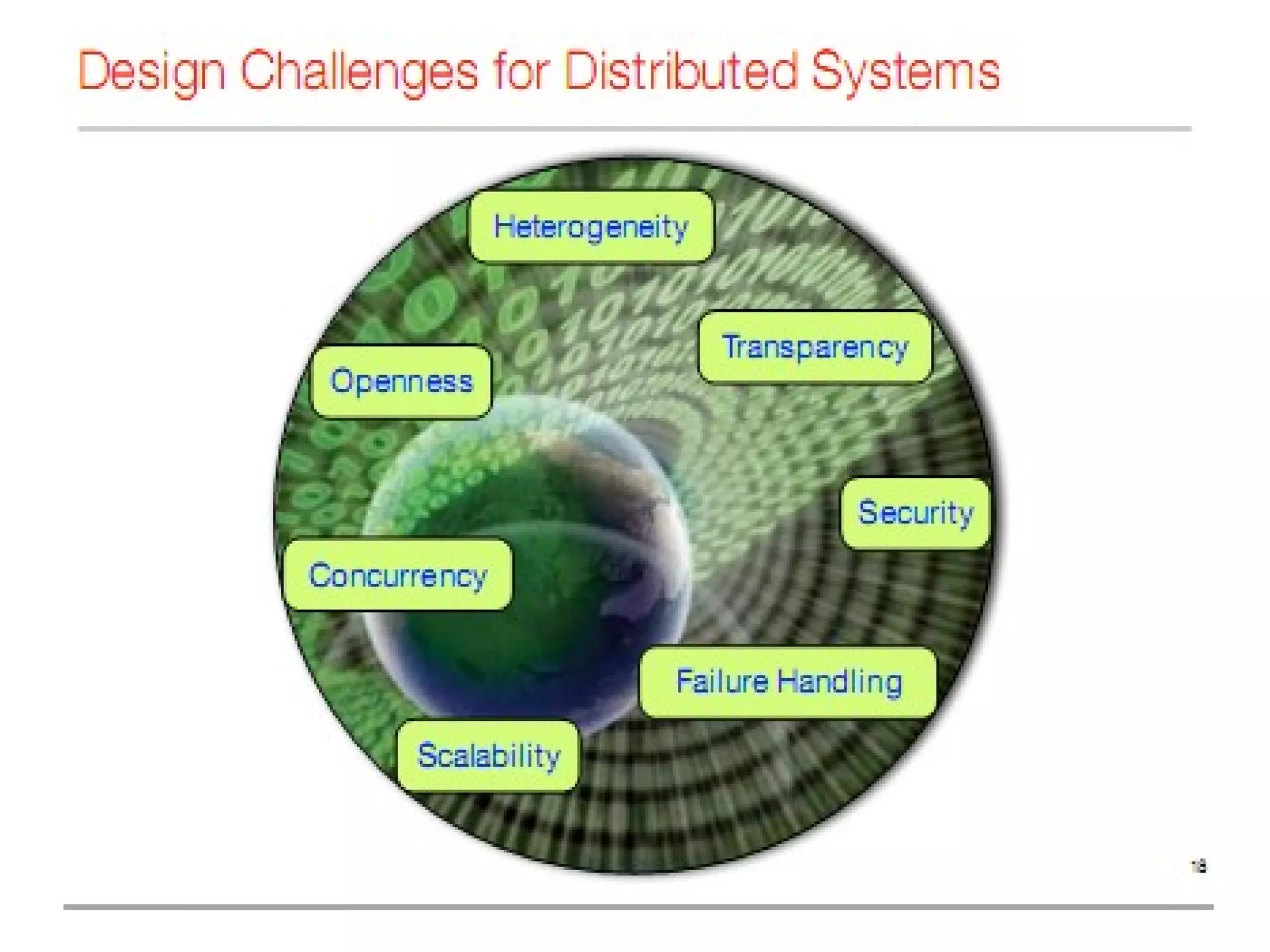
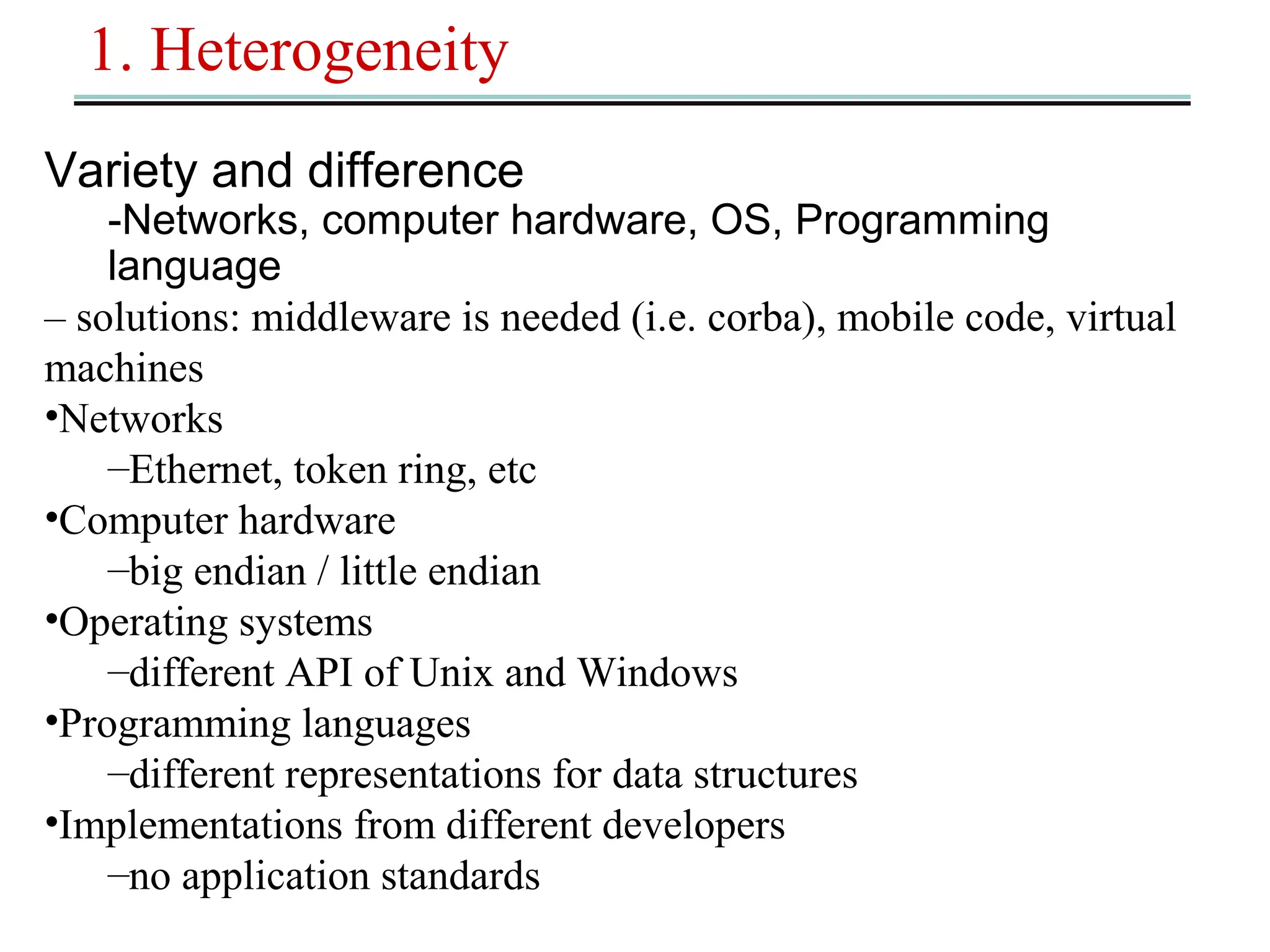
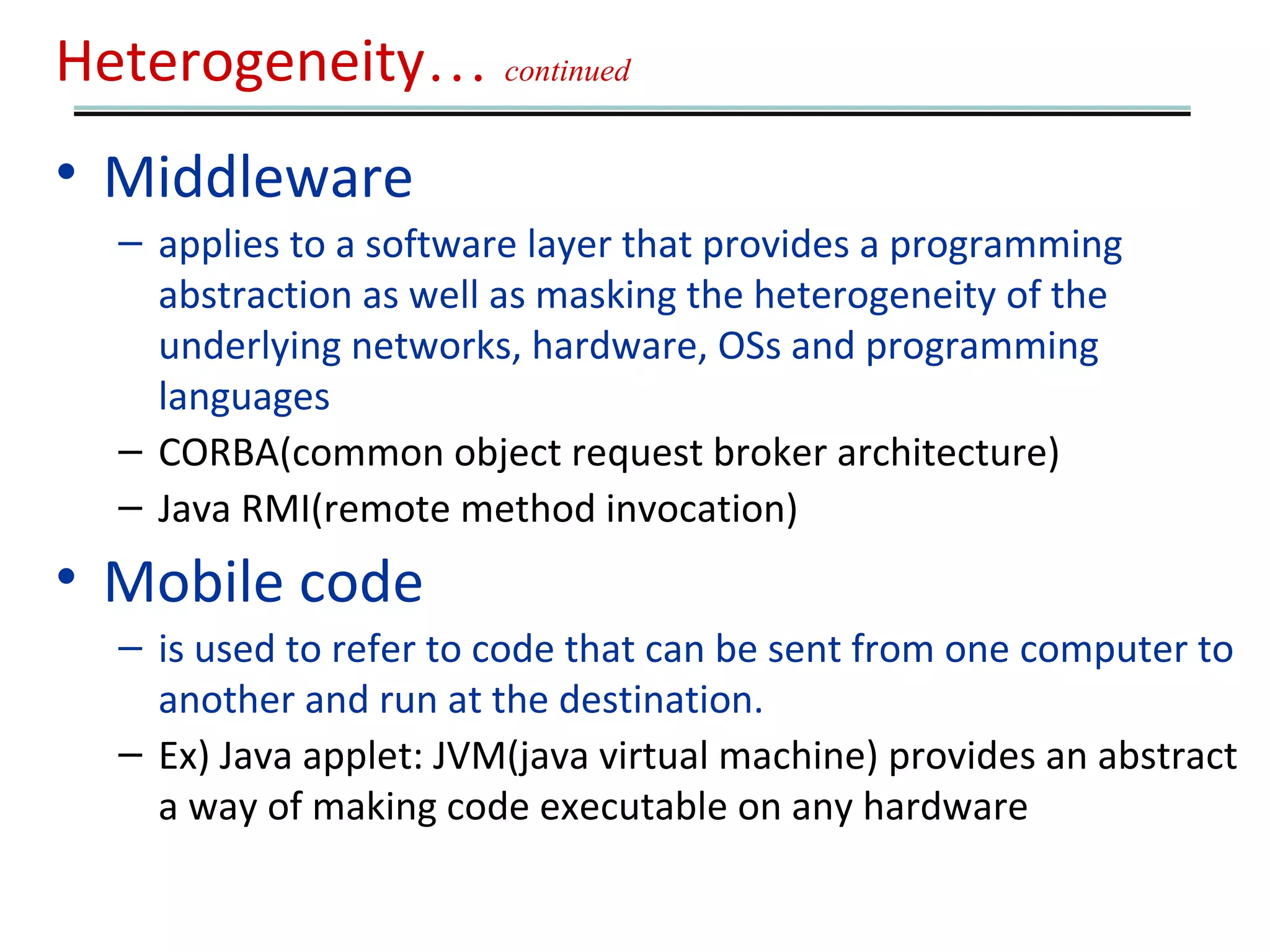
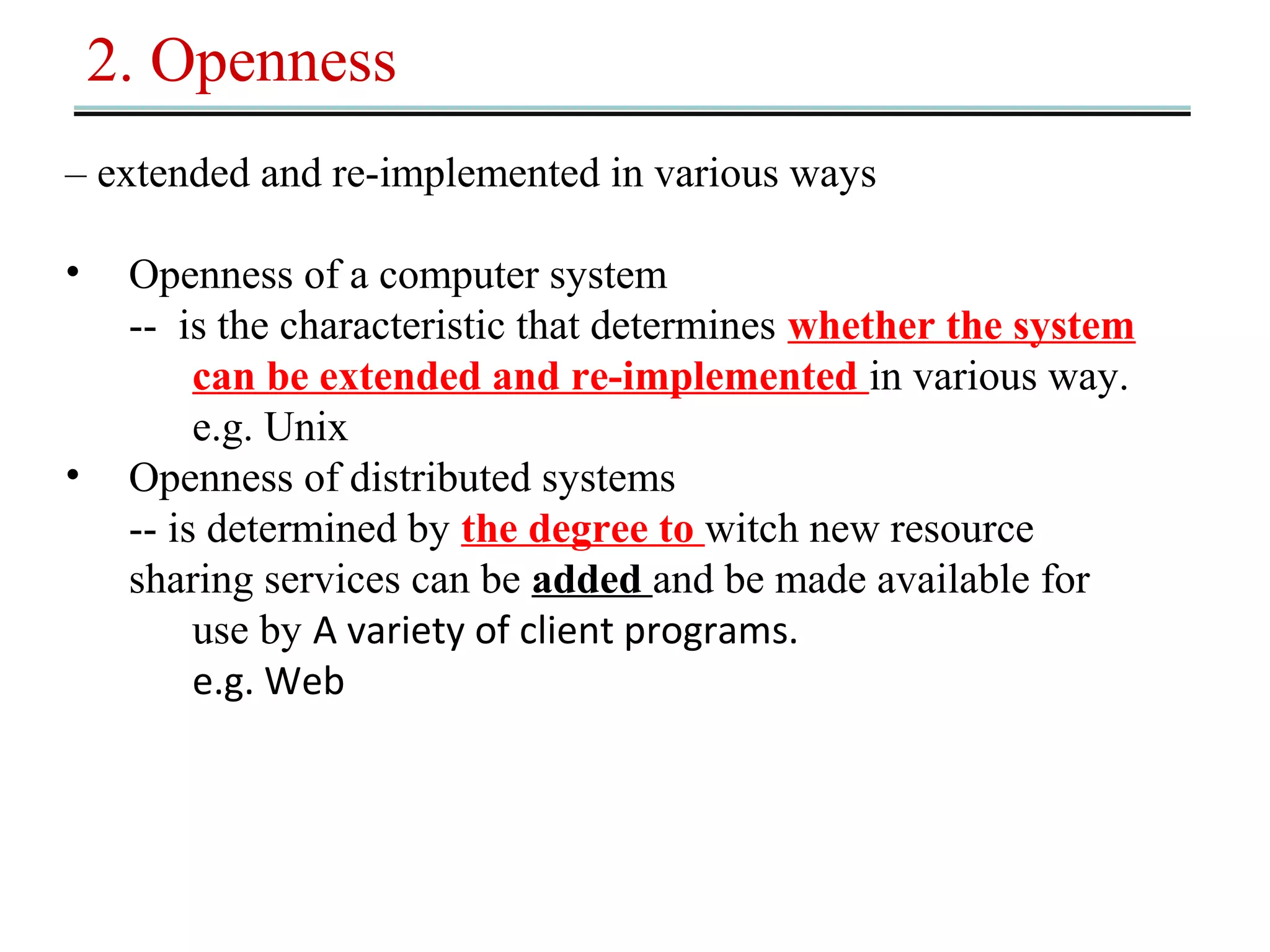
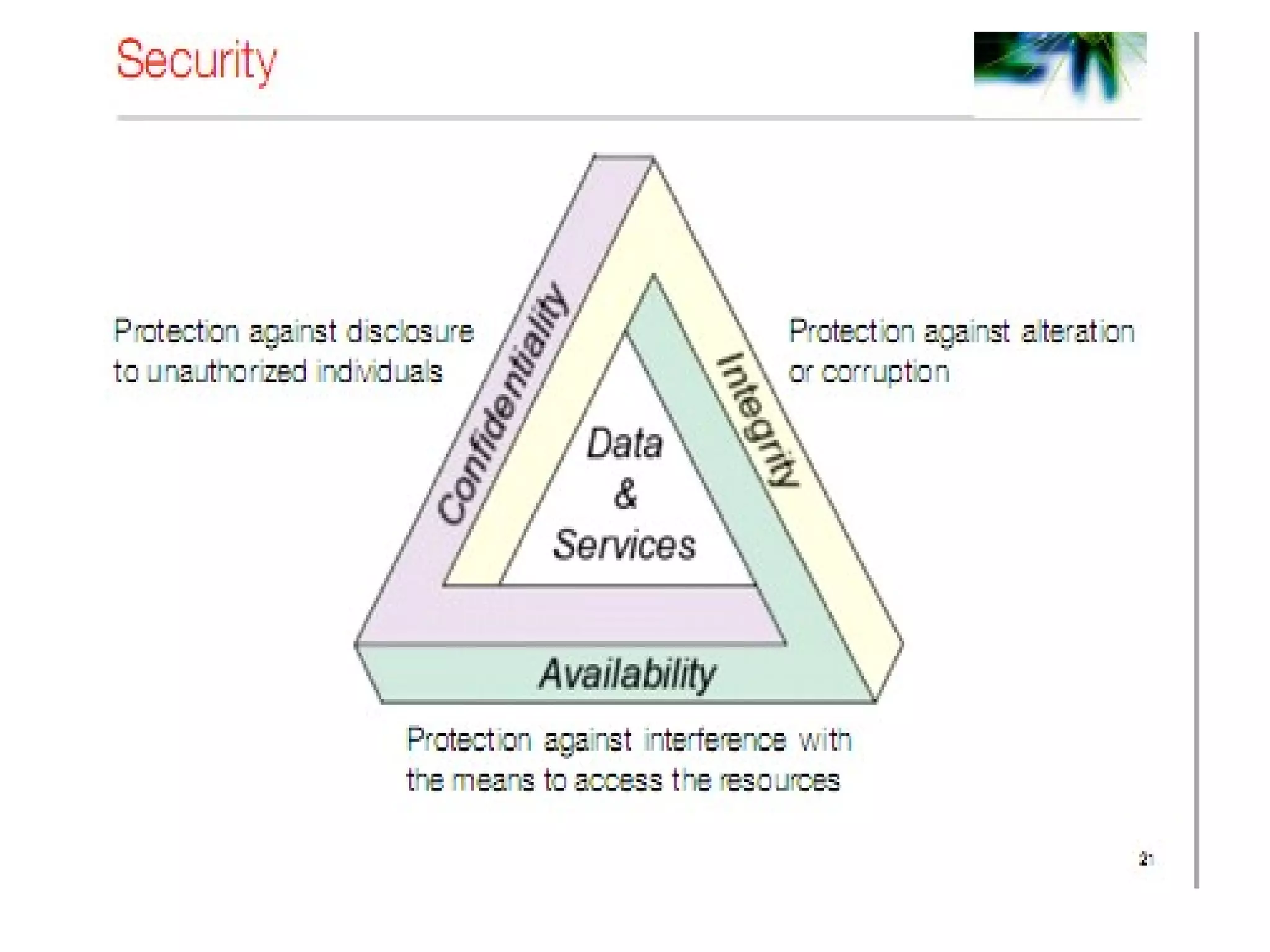
This document outlines 7 key challenges in designing distributed systems: heterogeneity, openness, security, scalability, failure handling, concurrency, and transparency. It discusses each challenge in detail, providing examples. Heterogeneity refers to differences in networks, hardware, operating systems, and programming languages that must be addressed. Openness means a system can be extended and implemented in various ways. Security concerns confidentiality, integrity, and availability of resources. Scalability means a system remains effective as resources and users increase significantly. Failure handling techniques include detecting, masking, tolerating, and recovering from failures. Concurrency ensures correct and high performance sharing of resources. Transparency aims to make distributed components appear as a single system regardless of location, access