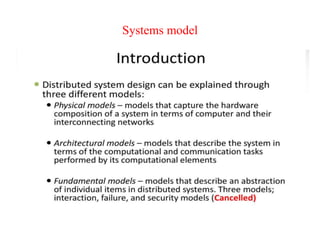
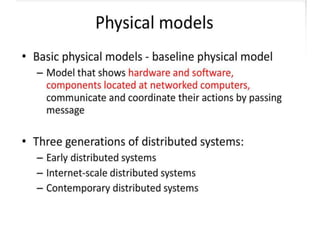
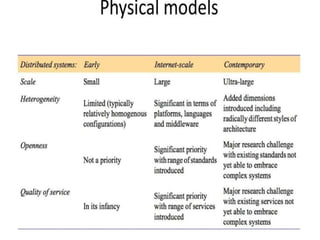
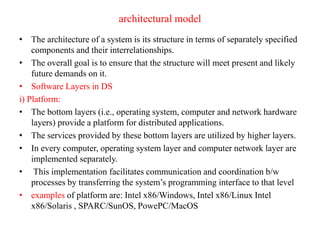
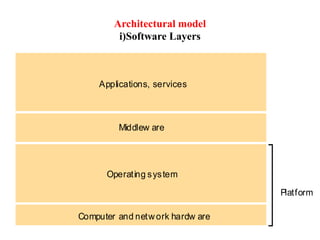
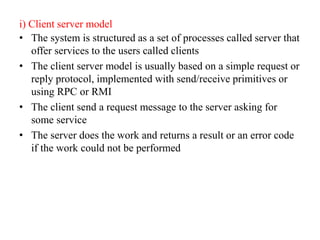
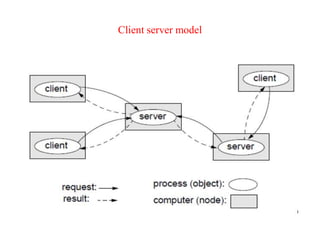
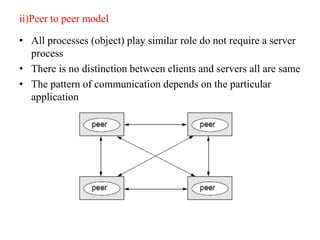
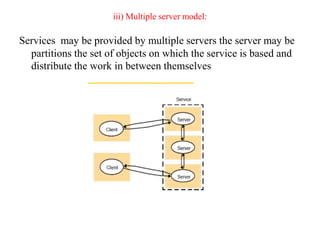
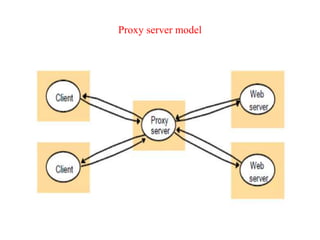
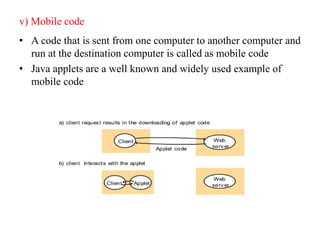
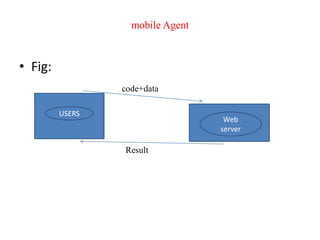
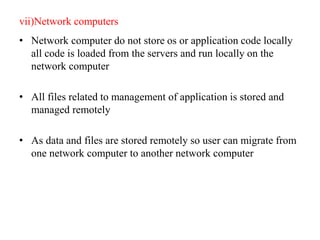
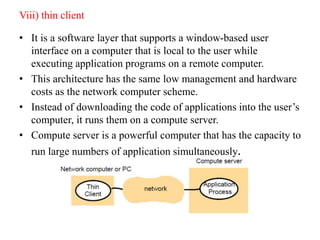
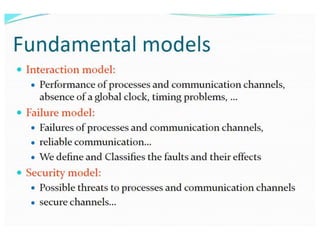
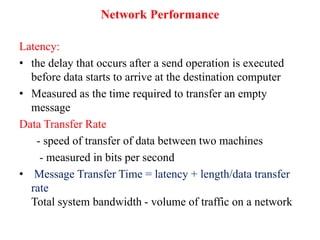
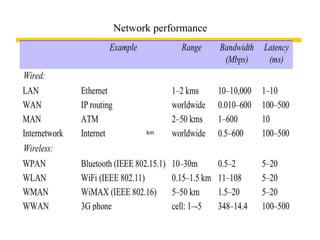
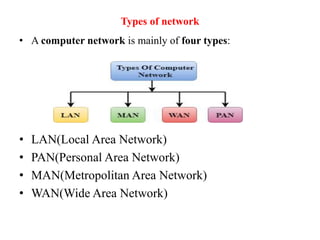
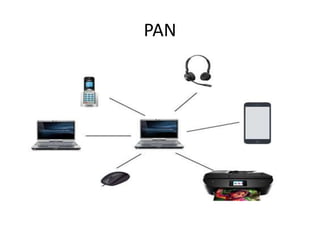
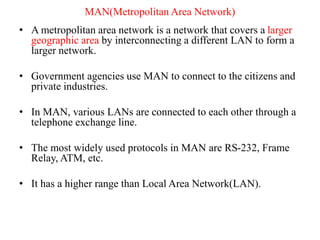
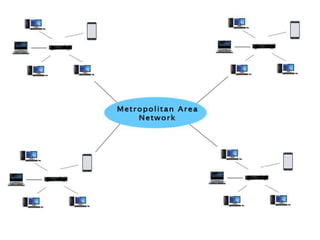
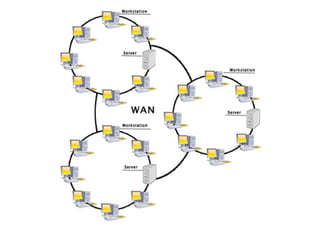
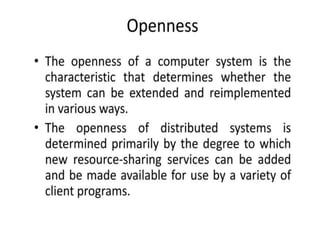
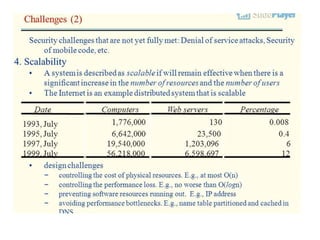
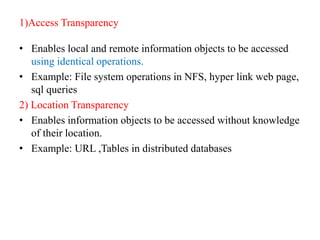
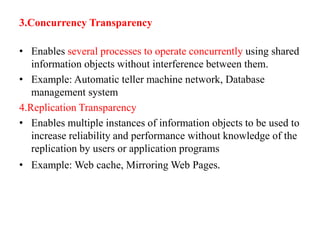
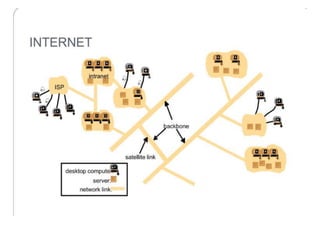
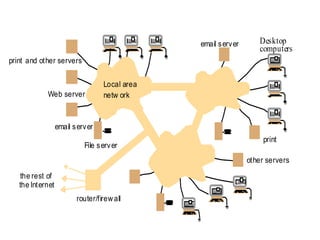
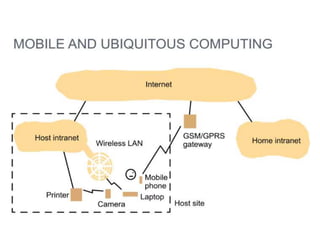
This document provides an overview of distributed systems. It discusses different types of distributed systems like client-server, n-tier, and peer-to-peer systems. It outlines advantages like performance, reliability, and scalability. Challenges include networking and security issues. Key features are discussed such as concurrency, lack of a global clock, and independent failures. Characteristics of distributed systems include heterogeneity, openness, security, scalability, failure handling, concurrency, and transparency. Examples provided are the Internet, intranets, and mobile/ubiquitous computing systems.





































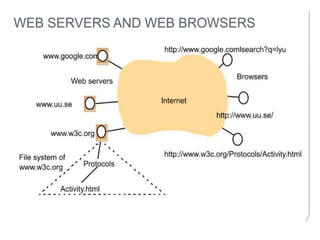
![ii) Uniform Resource Locator(URL)
URLs : The purpose of a Uniform Resource Locator [www.w3.org III] is to
identify a resource. It means, the term used in web architecture documents
is Uniform Resource Identifier (URI)
The ‘scheme’, declares which type of URL this is. URLs are required to
identify a variety of resources.
For example,
mailto:joe@anISP.net identifies a user’s email address;
ftp://ftp.downloadIt.com/software/aProg.exe identifies a file that is to be
retrieved using the File Transfer Protocol (FTP) rather than the more
commonly used protocol HTTP.
HTTP URLs are the most widely used, for accessing resources using the
standard HTTP protocol. An HTTP URL has two main jobs: to identify
which web server maintains the resource, and to identify which of the
resources at that server is required.
HTTP URLs are of the following form:
http:// servername [:port] [/pathName] [?query] [ #fragment]](https://image.slidesharecdn.com/pptsdsunit-1-240125124005-e7ef1909/85/PPTS-DS-UNIT-1-pptx-48-320.jpg)