The document discusses distributed shared memory (DSM) in three paragraphs:
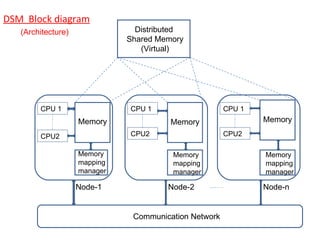
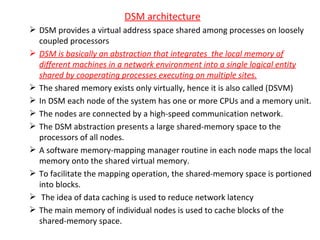
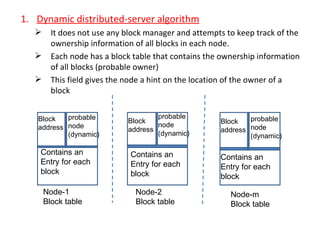
1) DSM provides a virtual shared address space across loosely coupled nodes through software memory mapping. Each node caches blocks of shared memory locally to reduce network latency.
2) When a process accesses a non-local memory block, the memory manager handles the request by migrating the block over the network if needed. Cached blocks avoid repeated network transfers.
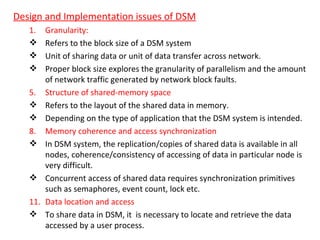
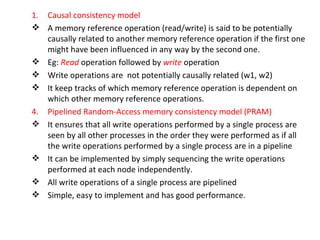
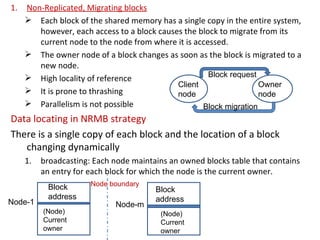
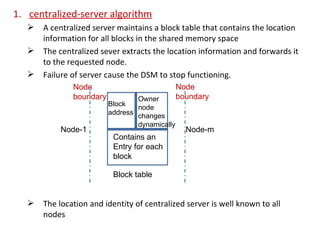
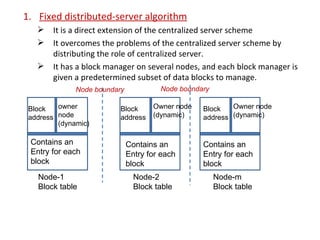
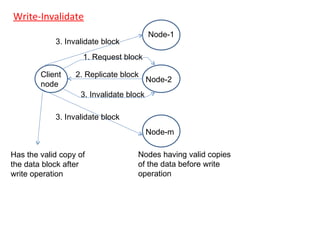
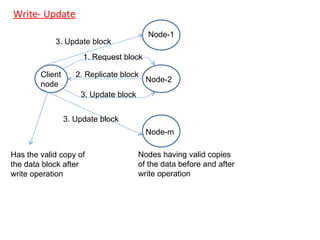
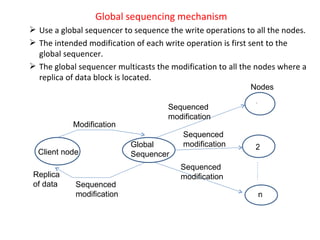
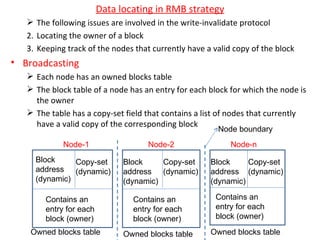
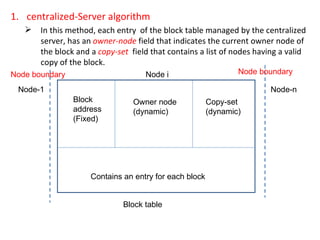
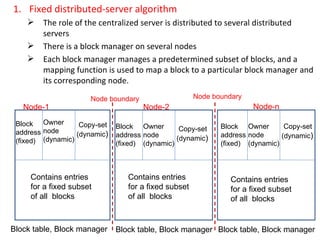
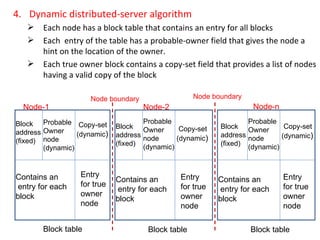
3) Key design issues include block granularity, consistency models, data location protocols, and handling replication and migration of blocks. Different protocols are used depending on whether blocks are replicated, migrating, or both.