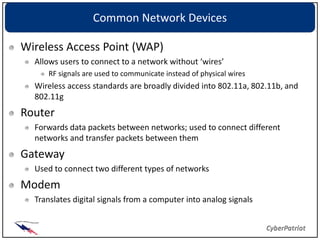
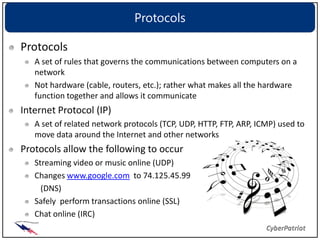
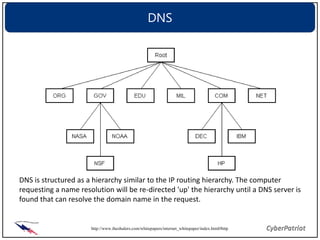
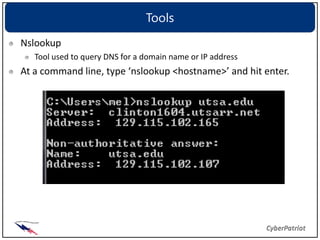
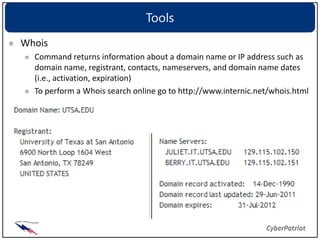
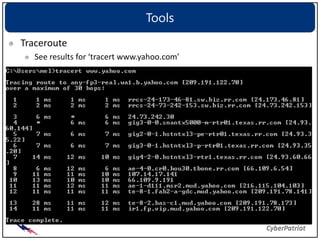
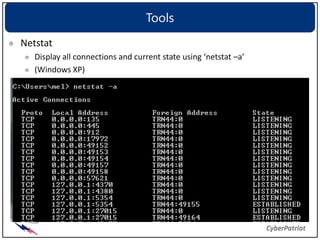
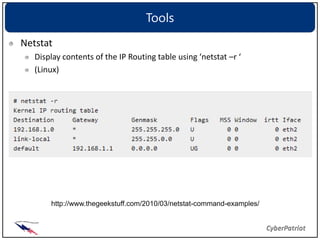
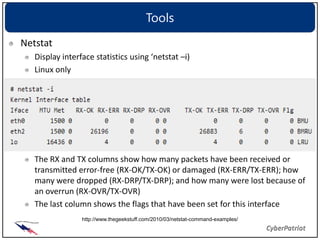
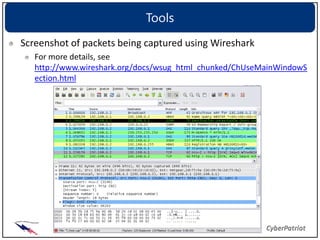
The document provides an overview of common network devices, protocols, DNS fundamentals, and network configuration tools. It defines devices like switches, routers, and wireless access points. It explains protocols including TCP, IP, UDP, and DNS. It also introduces tools for looking up domain information, tracing network routes, checking connections and interfaces, and analyzing packets.