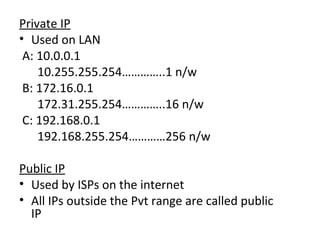
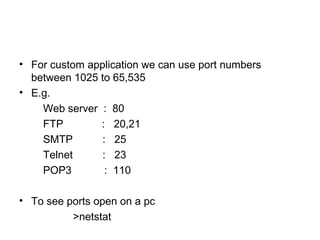
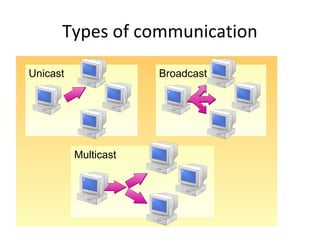
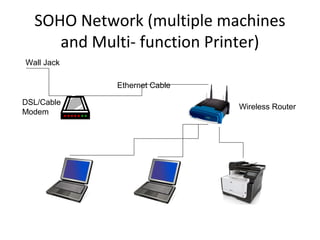
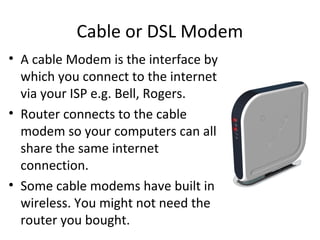
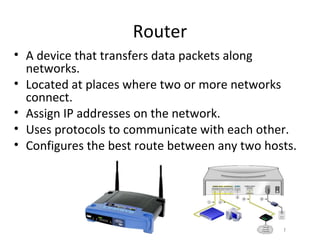
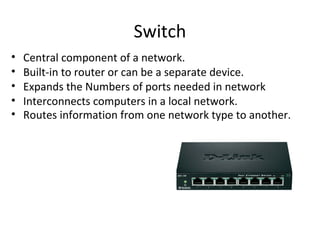
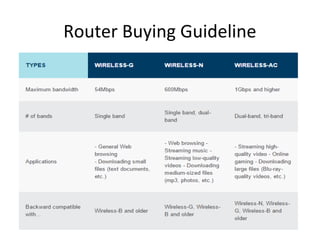
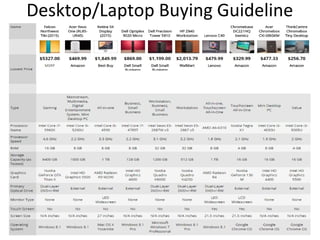
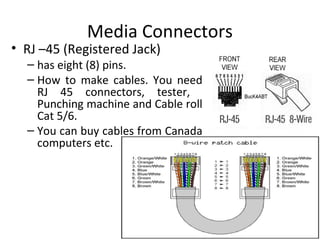
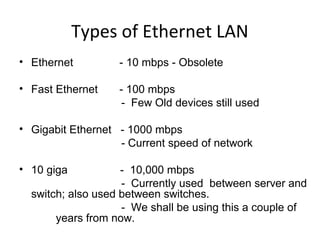
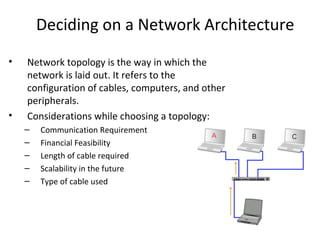
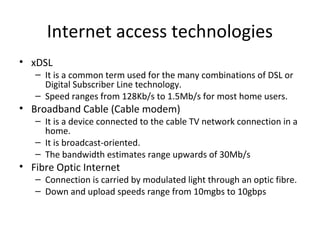
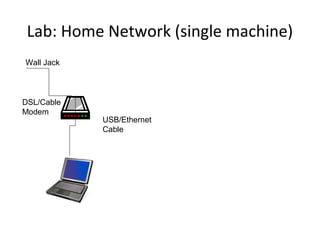
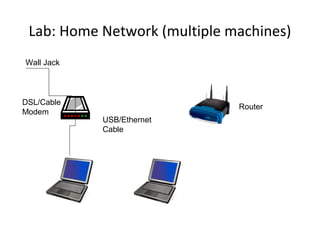
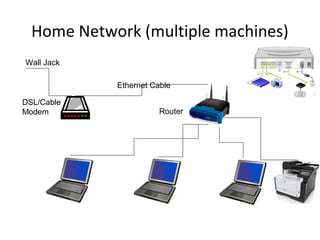
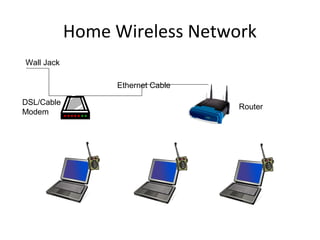
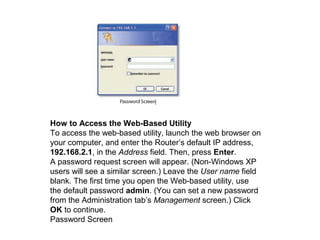
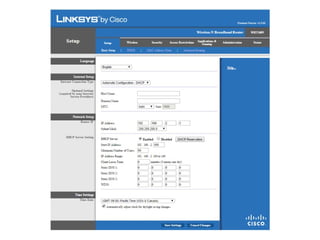
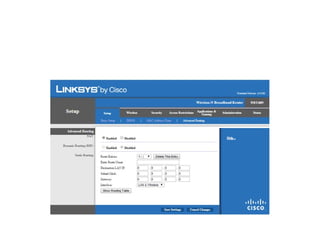
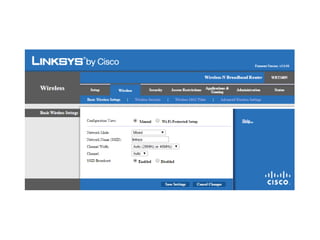
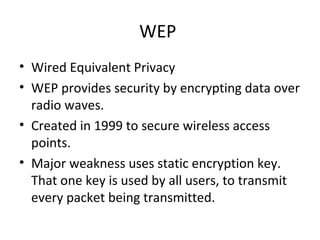
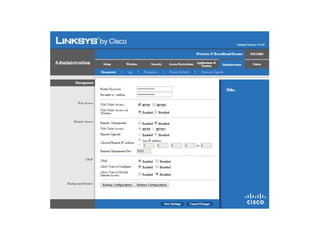
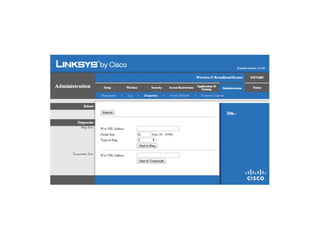
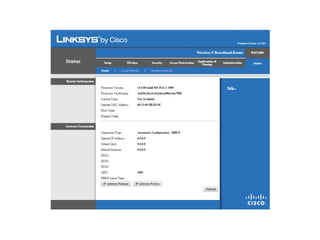
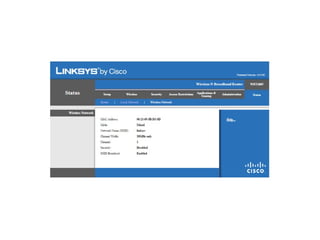
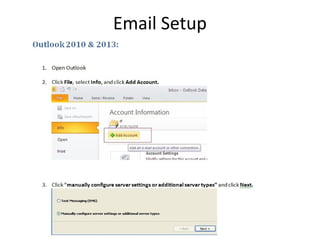
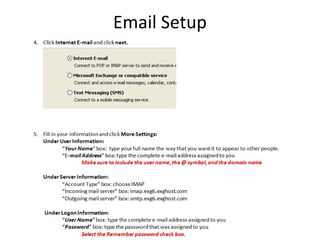
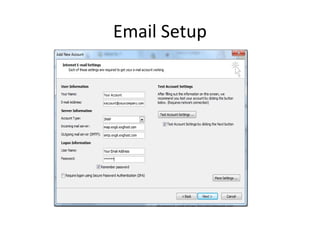
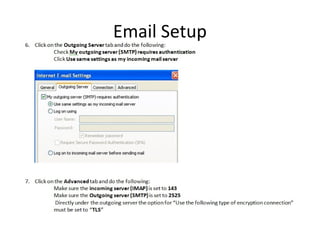
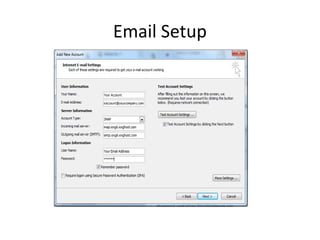
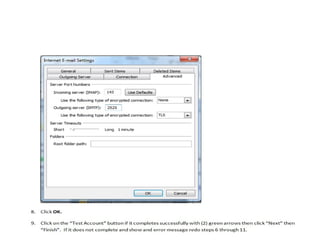
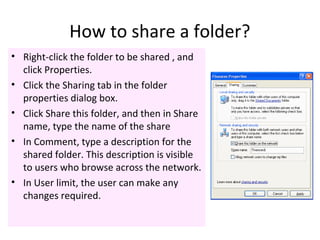
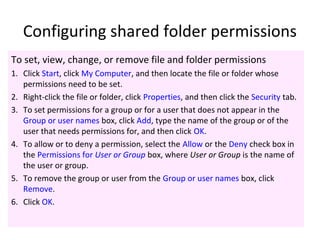
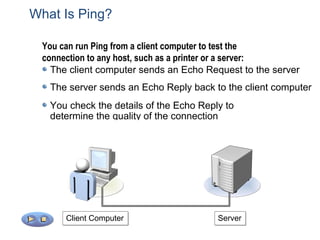
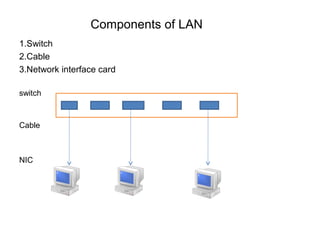
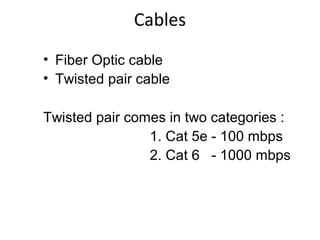
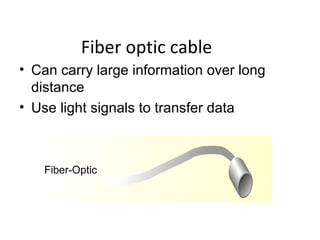
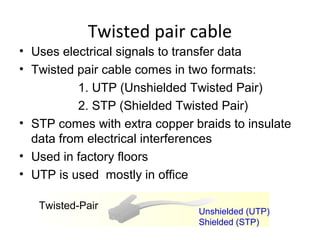
The document outlines the course content for a Small Office Home Office (SOHO) IT Network Setup course. The course covers topics such as network components, configurations, email and file sharing setup. It includes chapters on understanding networks, network components, terminologies, a SOHO network lab, and advanced Google search operators. Network abbreviations and concepts such as IP addressing, static versus dynamic IP, and private versus public IP are also defined.












![Network Interface Card(NIC)
• Each NIC has an address called mac (media access
control) address burnt into the chip at the time of
manufacture
• Also called hardware address because it cannot be
changed
• Each mac address is unique in the world & in
hexadecimal format [0-9, A-F]
• E.g.
1A.2B.CC.2A.FF.3C
vendor vendor
ID defined](https://image.slidesharecdn.com/sohonetworksetup-171031153455/85/SOHO-Network-Setup-Tutorial-20-320.jpg)