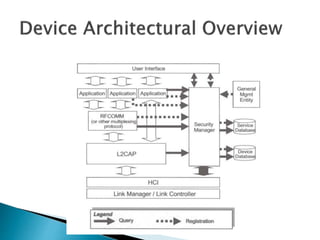
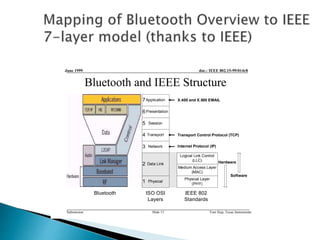
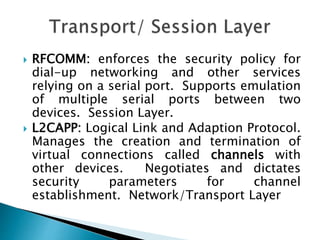
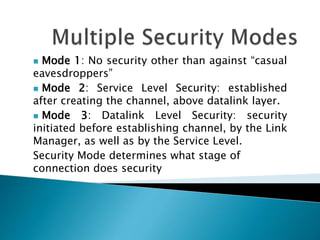
1) The document discusses security threats and mechanisms in wireless networks and Bluetooth technology. It describes authentication, authorization, and different security modes in Bluetooth.
2) It explains pairing and encryption processes between Bluetooth devices and how different trust levels impact service access. Security is implemented through symmetric keys and challenge-response.
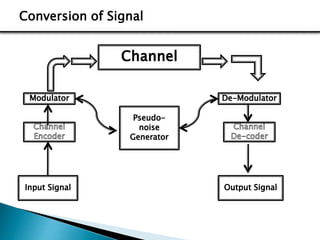
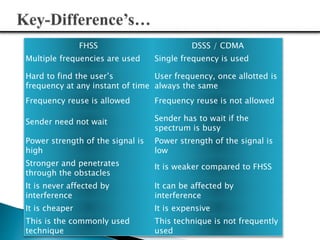
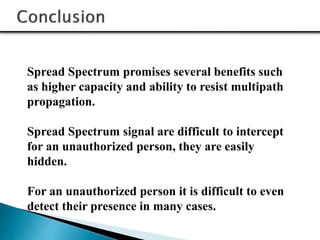
3) The document compares FHSS and DSSS/CDMA signaling techniques, noting advantages of FHSS like reduced interference, better voice quality, inherent security, and resistance to jamming.