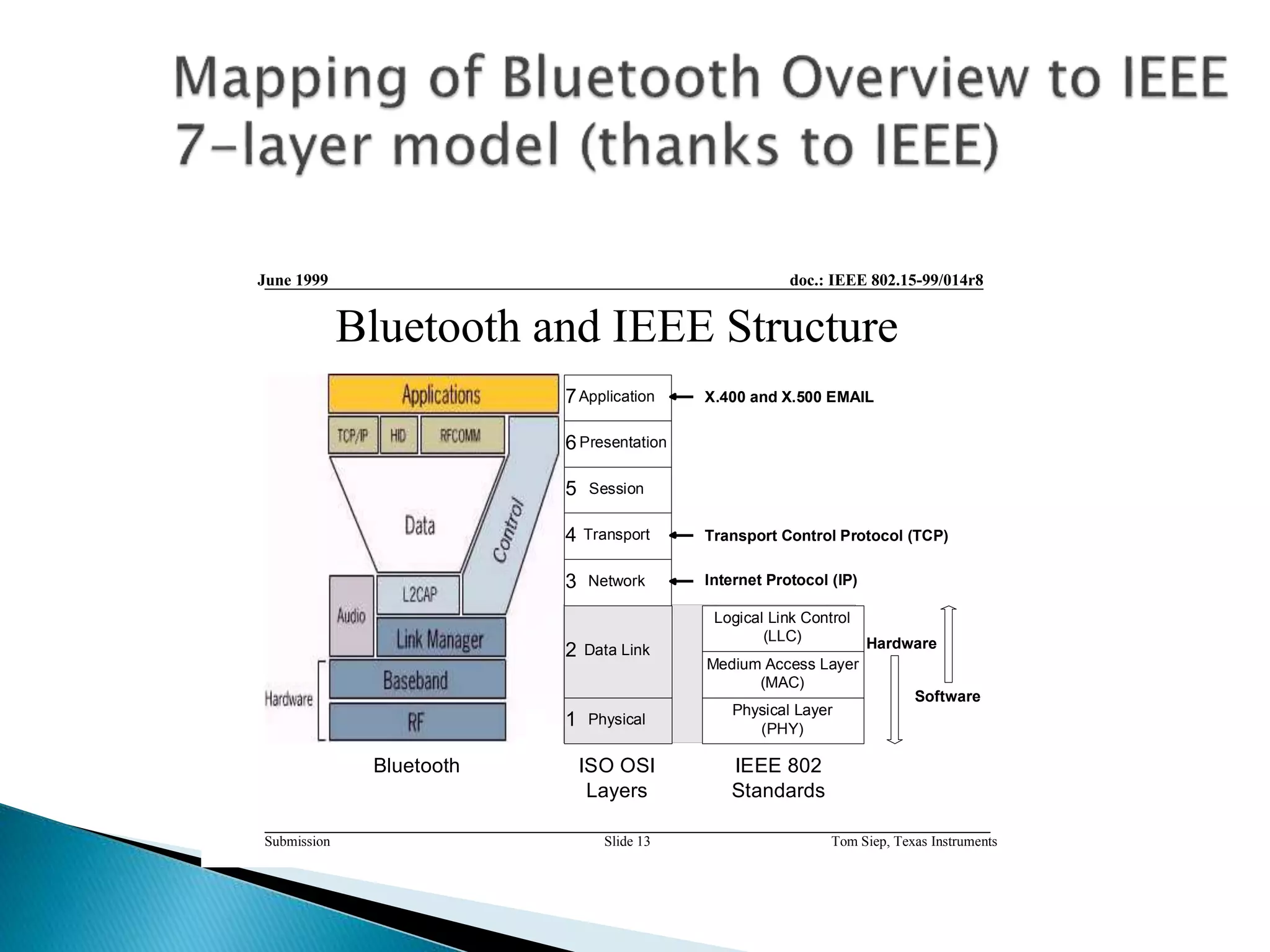
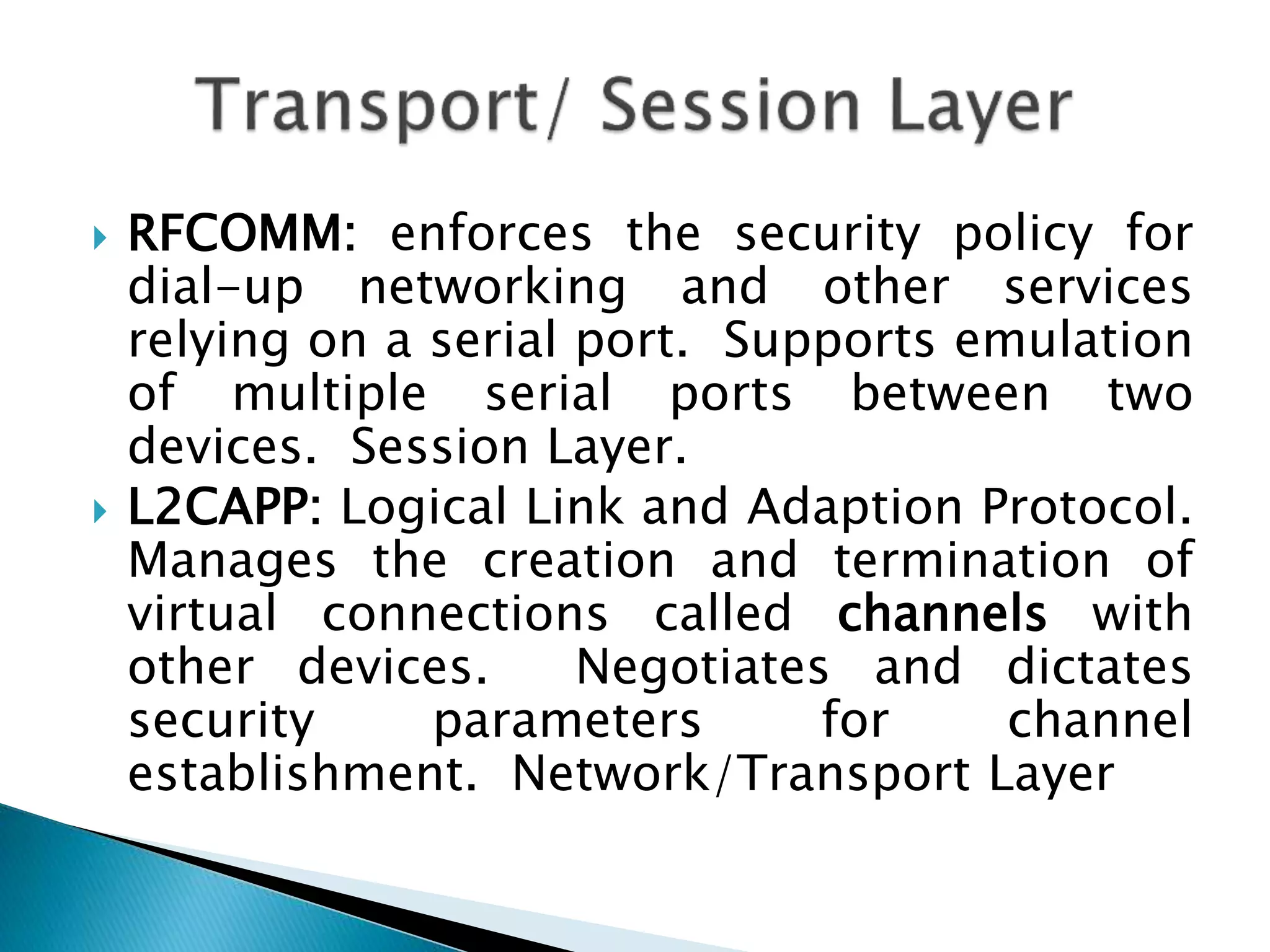
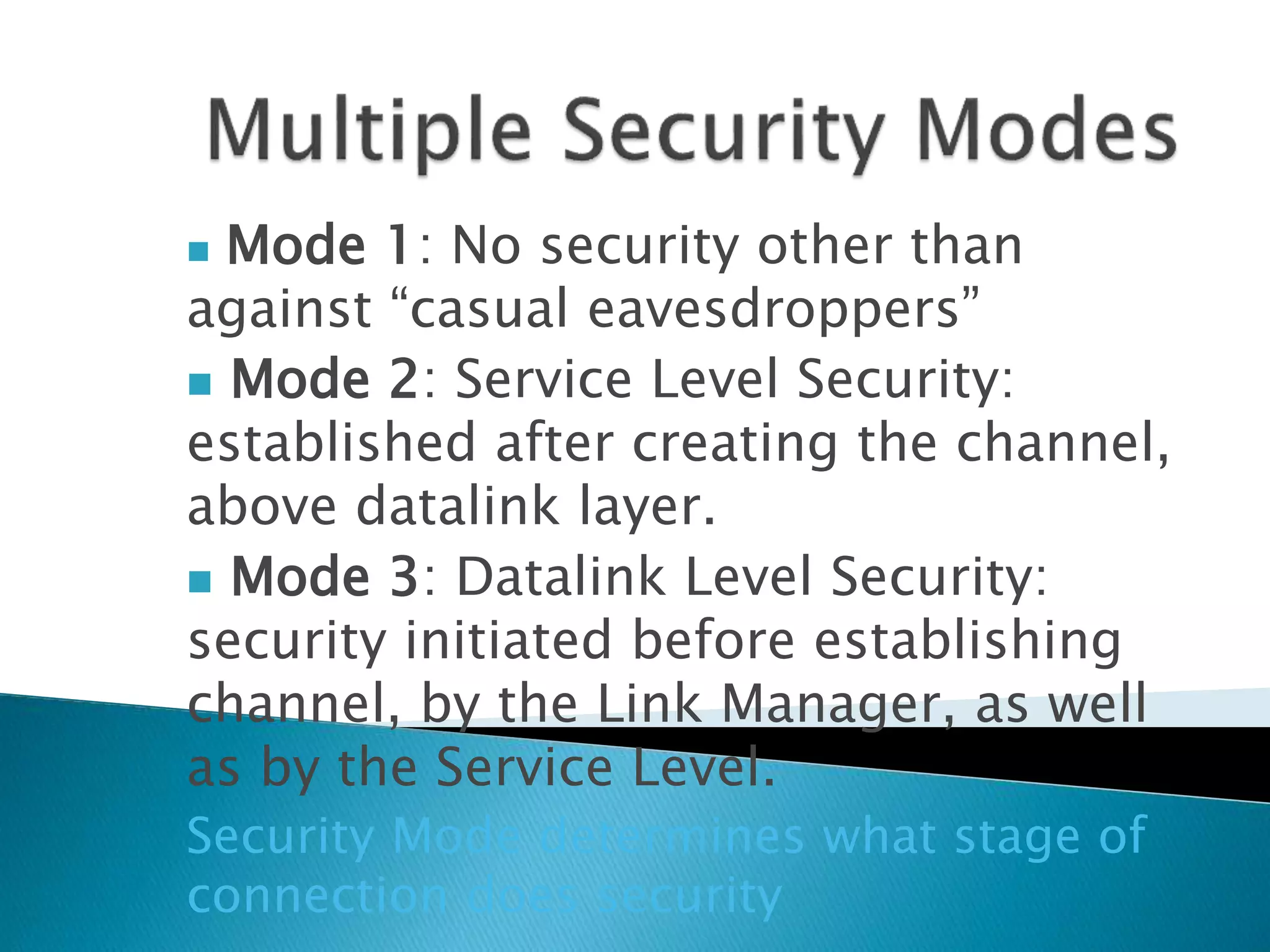
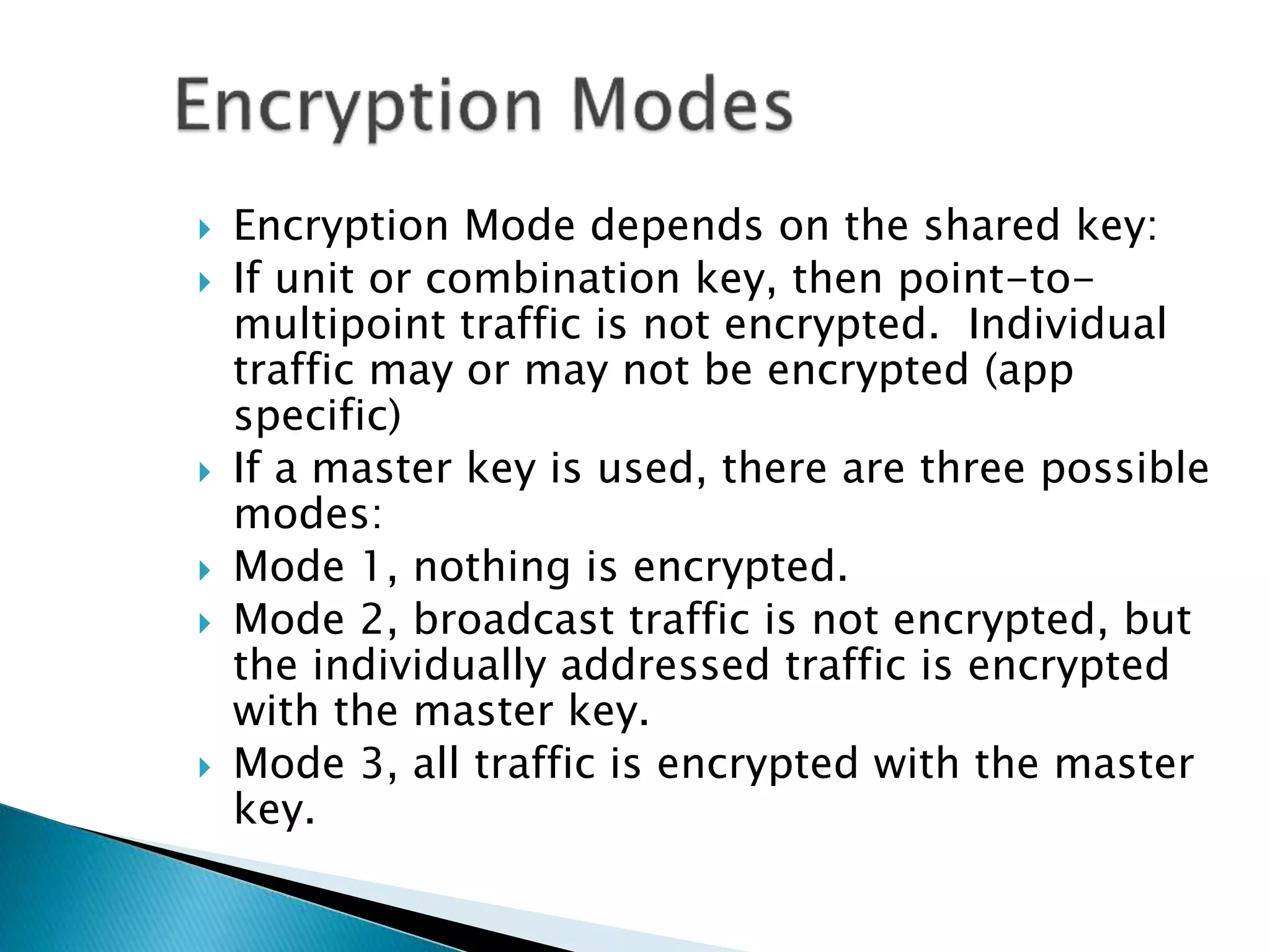
This document discusses Bluetooth security from the physical layer up to application layer. It describes how Bluetooth implements security through pairing, authentication, and encryption. Pairing involves generating initialization keys, authentication through challenge-response, and establishing shared link and encryption keys. Authentication and encryption can occur at the data link layer or above, depending on the security mode. Trust levels and access control are managed by a service database. The document also notes some potential security issues with Bluetooth and ways applications can provide additional security.