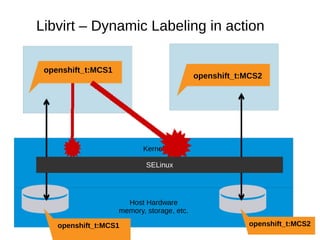
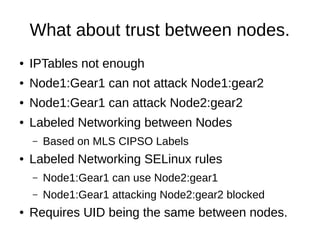
This document discusses the integration of SELinux with OpenShift, focusing on the labeling system, type enforcement, and multi-category security (MCS). It outlines the various SELinux labels used by OpenShift and the issues regarding security, node separation, and network access. Additionally, it highlights the challenges of running containers securely under SELinux and the importance of using Linux namespaces for resource management.















![Libvirt-lxc
● Boot “init” binary
● SELinux Types + MCS
● Firewall ebtables/ip[6]tables
● Host FS passthrough bind mounts
● CGroups resource control
● Available in RHEL6.4
– But your on your own...](https://image.slidesharecdn.com/openshift-130414195303-phpapp01/85/OpenShift-SELinux-with-Dan-Walsh-rhatdan-19-320.jpg)

