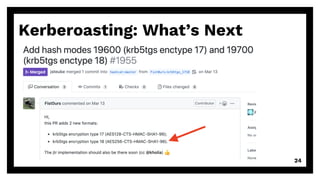
The document discusses advanced techniques for kerberoasting, a method of offline password cracking in Windows environments, highlighting the mechanisms of service tickets and service principal names (SPNs). It details current approaches, such as using tools like Rubeus and Mimikatz, and addresses security considerations like encryption types and the challenges of mitigating kerberoasting risks. The presentation emphasizes the importance of understanding these techniques to improve security postures against potential exploitation.









![msDS-
SupportedEncryptionTypes
▪ AD user/computer account property touched on by Jim
Shaver and Mitchell Hennigan in their DerbyCon 7.0
“Return From The Underworld” talk
▪ According to Microsoft’s [MS-ADA2], “The Key
Distribution Center (KDC) uses this information [msDS-
SupportedEncryptionTypes] while generating a service
ticket for this account.” 15](https://image.slidesharecdn.com/kerberoastingrevisited-190907185352/85/DerbyCon-2019-Kerberoasting-Revisited-15-320.jpg)
![msDS-
SupportedEncryptionTypes
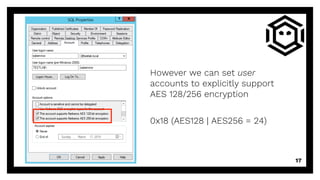
▪ According to MS-KILE 3.1.1.5 the default value for this
field is 0x1C (RC4 | AES128 | AES256 = 28) for Windows
7+ and Server 2008R2+
▪ However, this property is only set by default
on computer accounts (not user or trust accounts!)
□ If this property is not defined/set to 0, [MS-KILE] 3.3.5.7 says
default behavior is to use a value of 0x7 (RC4) 16](https://image.slidesharecdn.com/kerberoastingrevisited-190907185352/85/DerbyCon-2019-Kerberoasting-Revisited-16-320.jpg)






![Thanks!Any questions?
▪ @harmj0y
▪ will [at] harmj0y.net
Get Rubeus:
▪ https://github.com/GhostPack/Rubeus
26](https://image.slidesharecdn.com/kerberoastingrevisited-190907185352/85/DerbyCon-2019-Kerberoasting-Revisited-26-320.jpg)