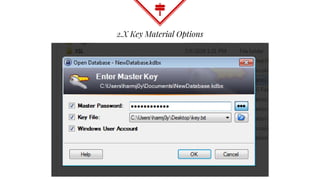
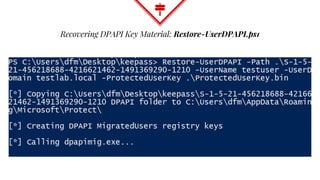
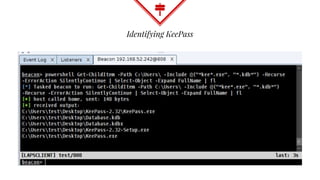
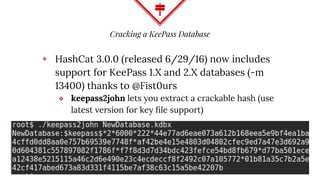
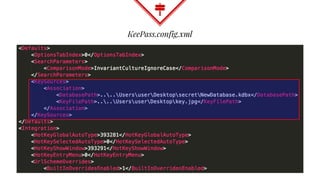
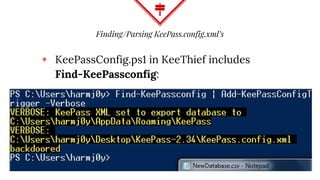
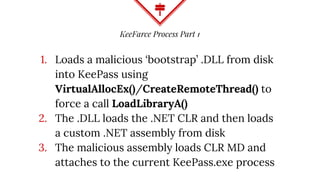
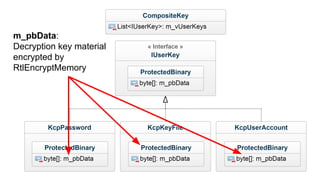
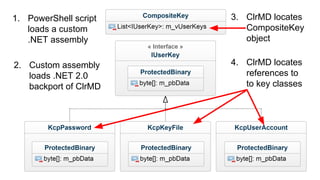
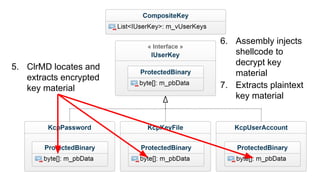
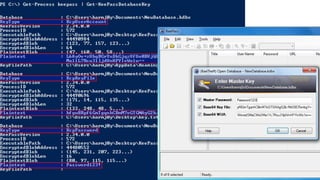
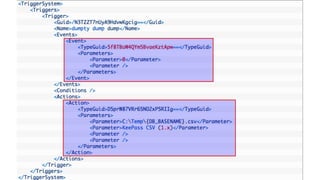
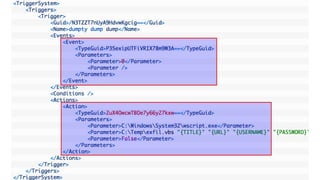
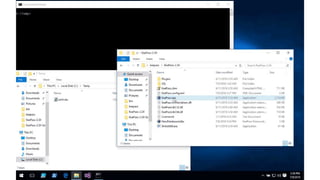
This document summarizes techniques for attacking the KeePass password manager program. It provides an overview of KeePass, discusses existing work like KeeFarce that exports unlocked databases, and introduces the author's tool KeeThief which extracts decryption keys from memory. The document also explores using KeePass' trigger system to automatically exfiltrate databases when they are opened or passwords copied. Mitigations like monitoring for suspicious processes interacting with KeePass are suggested.