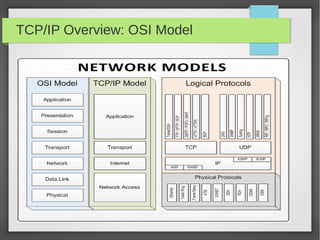
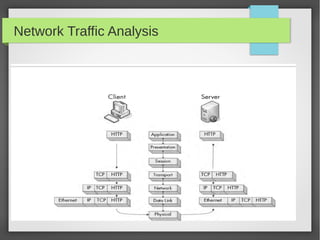
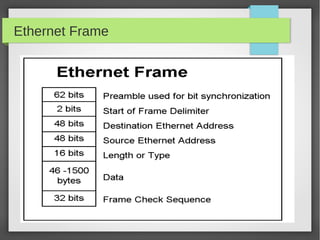
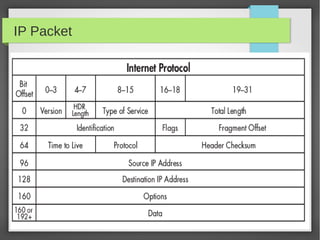
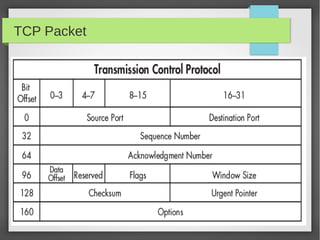
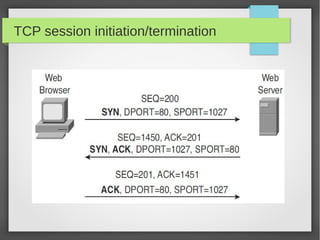
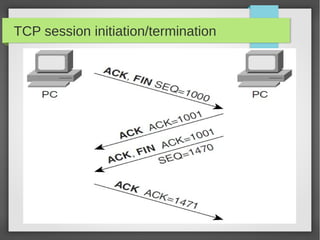
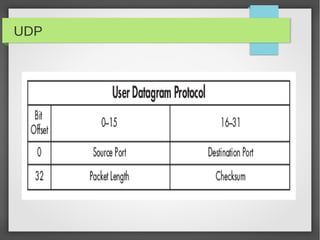
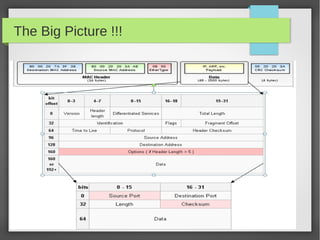
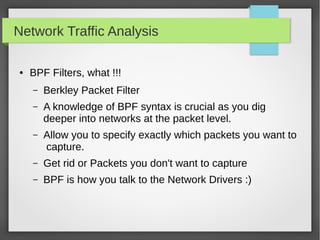
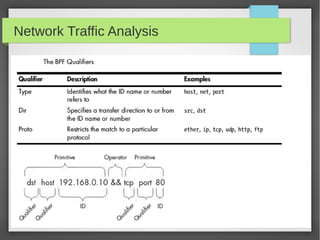
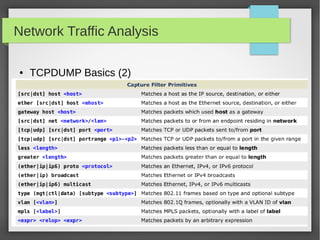
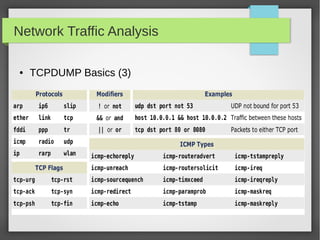
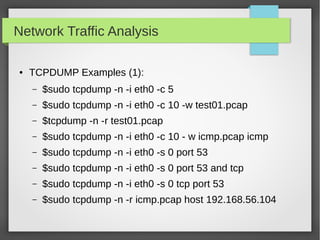
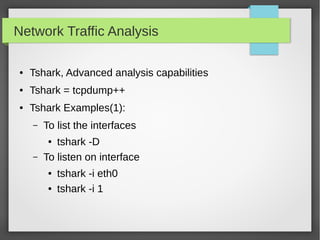
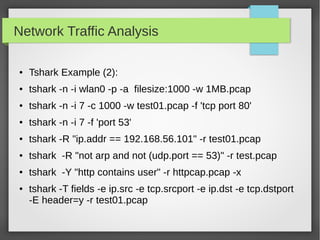
This document provides an overview of network traffic analysis. It discusses why traffic analysis is useful for gaining knowledge about a network, investigating issues, and network forensics. It also summarizes the basics of TCP/IP protocols, packet sniffing tools like Wireshark and Tcpdump, and how to analyze network traffic captures for troubleshooting and security purposes. Hands-on network forensics examples are provided to demonstrate these concepts.