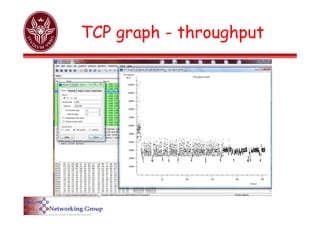
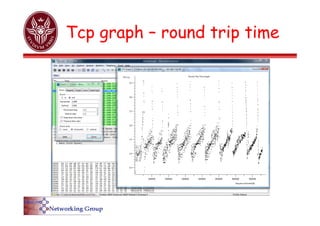
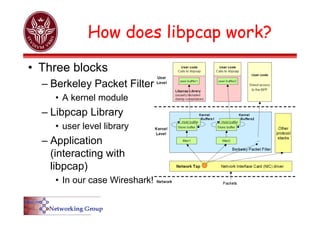
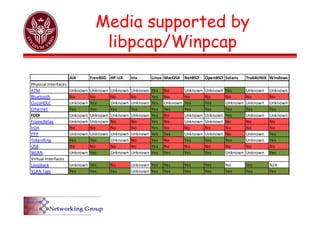
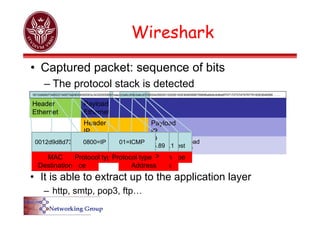
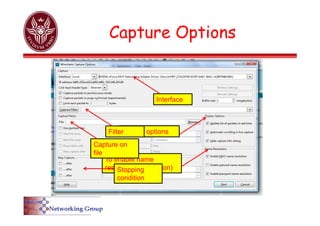
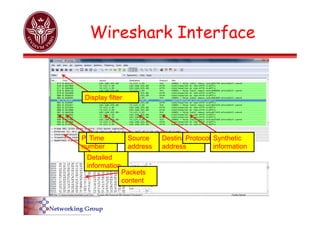
The document provides an overview of Wireshark, a popular open-source network packet analyzer, including its features, supported media, and functionality. It explains how Wireshark captures and analyzes network packets using the libpcap library, along with details on creating capture and display filters for efficient data analysis. Additionally, it includes references to documentation and user guides for further information on using Wireshark.





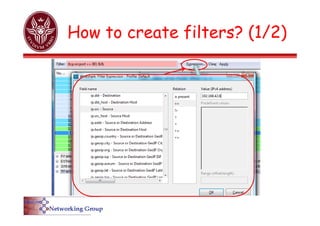
![Capture filters
• [not] primitive [and|or [not] primitive ...]
– [src|dst] host <host>
• Filter on IP address
– Source or destination is an option
– ether [src|dst] host <ehost>
• Filter on MAC address
– Source or destination is an option
– [tcp|udp] [src|dst] port <port>
• Filter on port number
– Source or destination is an option](https://image.slidesharecdn.com/5-wireshark-240717162929-dca62831/85/Ferramenta-de-analise-de-rede-para-windows-e-linux-14-320.jpg)
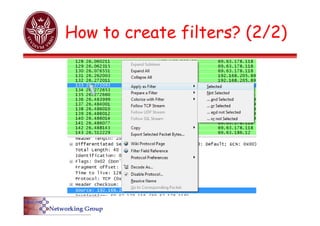
![Capture filters again….
01=ICMP
0012d9d8d734002219df27bb08004500003c343200008001eae2c0a8cd59c0a8cd0108004d56000100056162636465666768696a6b6c6d6e6f7071727374757677616263646566676869
The “icmp” filter can
be defined:
ether[0x17]==0x01
0x17
Customized filters](https://image.slidesharecdn.com/5-wireshark-240717162929-dca62831/85/Ferramenta-de-analise-de-rede-para-windows-e-linux-16-320.jpg)