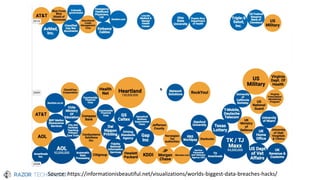
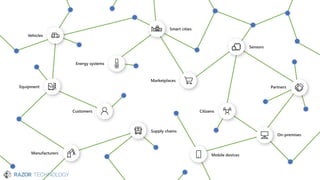
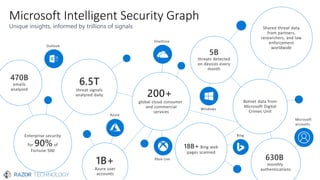
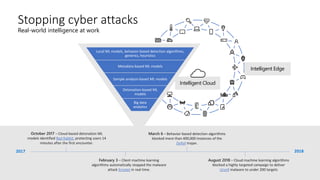
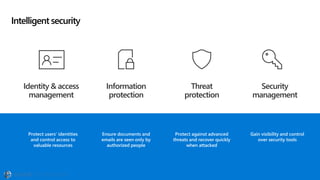
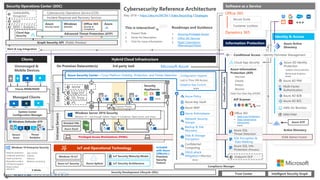
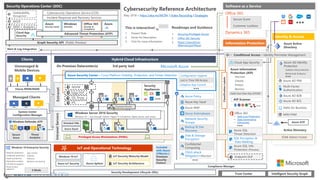
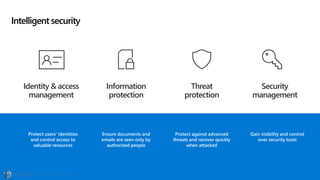
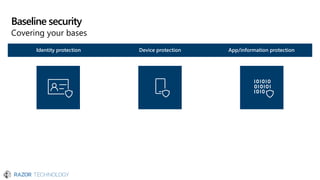
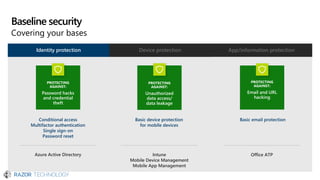
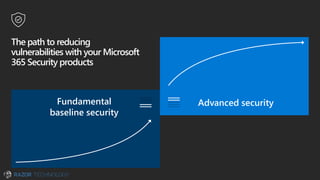
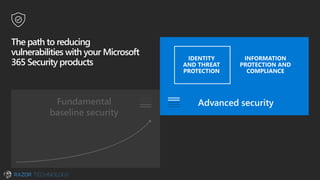
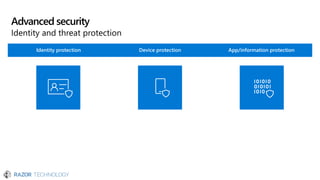
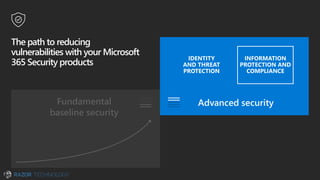
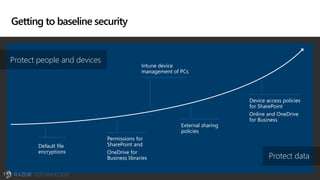
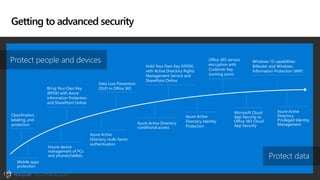
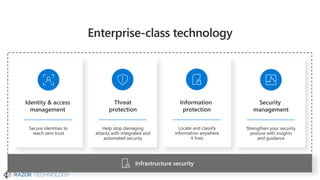
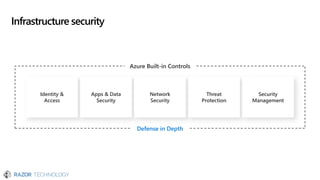
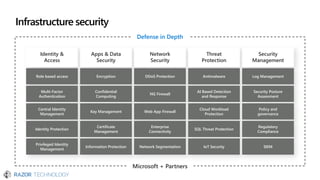
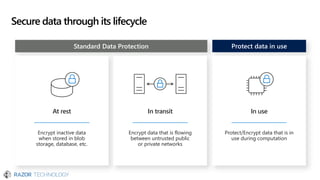
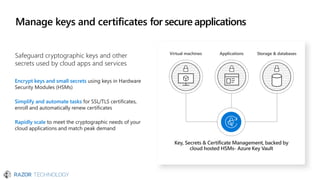
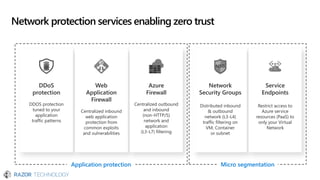
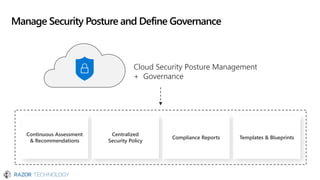
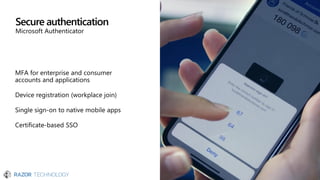
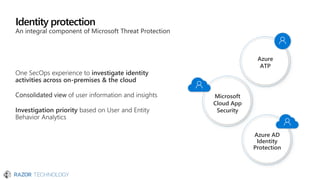
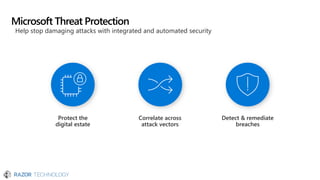
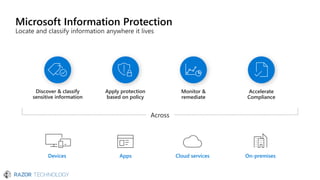
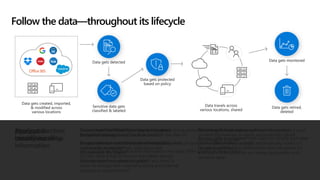
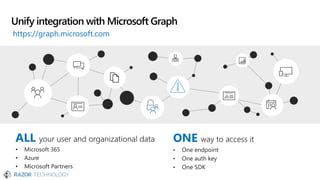
The document discusses the evolving landscape of cybersecurity, highlighting the critical shortage of security skills and the increasing reliance on advanced technologies like machine learning for threat detection and prevention. It emphasizes the importance of protecting users' identities, data management, and adopting a zero-trust security posture as a response to emerging threats in the mobile workforce. Additionally, it outlines various Microsoft security products and strategies aimed at mitigating vulnerabilities and securing organizational assets against cyberattacks.