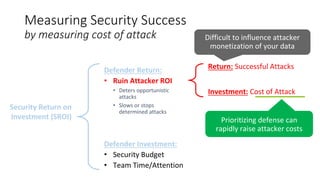
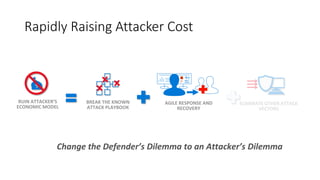
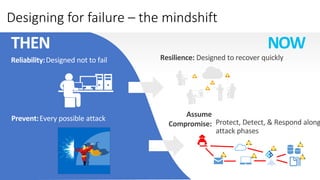
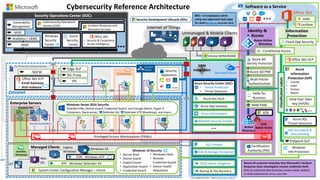
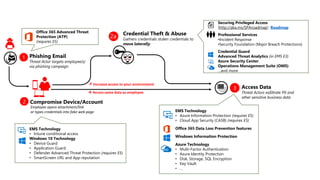
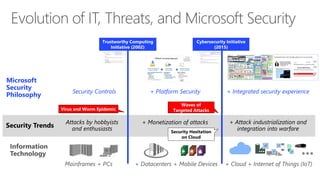
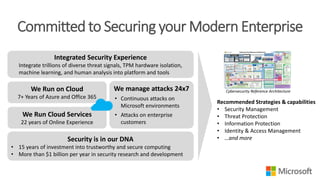
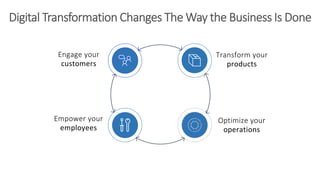
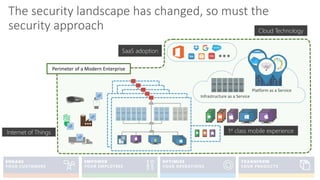
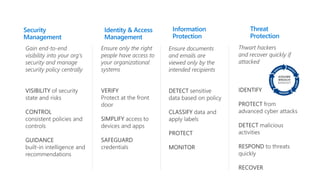
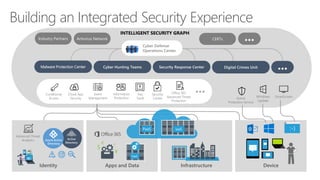
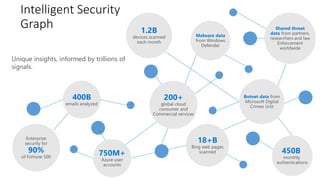
The document discusses Microsoft's approach to security and how the threat landscape is evolving. It emphasizes building an integrated security experience that combines data from across Microsoft products and services with machine learning to better detect and respond to threats. It also outlines Microsoft's strategy to make attacks more costly for threat actors by disrupting their economic models and technical playbooks through rapid response capabilities and a defense in depth approach across identity, devices, infrastructure and applications.







![Microsoft Trust Center
[ Privacy/Compliance boundary ]
{ }
PRODUCT & SERVICE TELEMETRY](https://image.slidesharecdn.com/3danielgrabskimicrosoftscommitmenttosecurity-171030091652/85/Daniel-Grabski-Microsofts-cybersecurity-story-16-320.jpg)